This article surveys the differences in various anomaly detection methods and their applicability to the security protection of the Industrial Internet of Things (IIoT). It analyzes papers published from 2000 to 2021 on network anomaly detection, summarizes the security threats faced by IIoT, and categorizes 9 types of network anomaly detection methods and their characteristics. A longitudinal comparison of the advantages and disadvantages of different methods is provided, as well as statistical analysis and comparison of commonly used datasets. The article also looks ahead to future development trends from four perspectives. The analysis results can guide the selection of appropriate methods based on application scenarios, identify key issues to be solved, and provide direction for subsequent research.
0 Introduction
With the rapid development of 5G communication technology and the increasing computational and storage capabilities of embedded devices such as sensors and processors, the application of these network communications and embedded devices in industrial systems has become increasingly common. The Industrial Internet of Things (IIoT) is a large network composed of applications, software systems, and physical devices, which communicate and share intelligence with the external environment and humans [1]. According to Accenture’s forecast, by 2030, the value of the IIoT in the United States will reach $7.1 trillion, and in Europe, it will exceed $1.2 trillion [2].
In this wave of industrial development, IoT security is one of the important factors affecting the widespread use of IIoT. In fact, the security of IoT devices is often poor, making them easy targets for attackers. Attackers can use these devices to conduct devastating network attacks, such as Distributed Denial of Service (DDoS) [3-4]. Traditional industrial environments have been under attack in the past, some of which have resulted in catastrophic consequences (e.g., Stuxnet virus [5] or failure overdrive/industrial destroyers [6]). Therefore, without security, IIoT will never be able to realize its full potential. Furthermore, industrial systems have strict requirements for performance and availability; even when the system is under a network attack, maintaining uninterrupted and secure system operation is often a priority.
Anomaly detection is crucial in defending systems and networks from malicious activities. In recent years, research on anomaly detection in IIoT has rapidly increased to mitigate network attacks, with many detection mechanisms proposed. On the other hand, researchers have conducted some surveys on anomaly detection from technical means, application scenarios, etc., such as references [7-10], but few have conducted in-depth analyses specifically targeting the characteristics and applicability of IIoT. In the past two years, although review articles on IIoT anomaly detection have emerged, they have not been comprehensive enough. For example, reference [2] only introduces detection methods based on system rules and modeling the physical state of the system, while reference [4] only covers statistical and machine learning-based detection methods. In addition to the detection methods mentioned in references [2, 4], there are many novel detection techniques.
Therefore, this article organizes anomaly detection technologies based on system invariance and physical state modeling, statistical learning, feature selection, machine learning, graphs, edge/fog computing, fingerprints, and biological immunity, and analyzes the advantages and disadvantages of each technology in detail. Due to the complexity and diversity of datasets used in industrial anomaly detection research, this article summarizes the characteristics and usage frequency of commonly used datasets to facilitate comparison and selection by readers. In addition, this article investigates and reviews the network threats and anomaly detection methods for typical scenarios in IIoT, introduces the application of edge/fog computing methods in anomaly detection, and adds research on the latest papers from 2021, providing an in-depth analysis of the characteristics and applicable scenarios of different detection methods.
1 Security Threats Faced by IIoT
Industry 4.0 applies information and communication technology to industrial manufacturing and automation, greatly enhancing productivity and efficiency. However, this advancement comes at the cost of expanding the attack surface of industrial systems. Attacks on IIoT can be classified into passive and active attacks. Passive attacks are covert and usually undetectable, such as eavesdropping and traffic analysis. Active attacks include packet loss, injection, and interference with the normal operation of the network. Active attacks such as malware infection, Denial of Service (DoS), unauthorized access, and false packet injection are typically detectable [9]. Below is a brief summary of the characteristics and targets of several active attacks.
Malicious packet injection attacks involve replaying captured packets and sending forged or tampered messages to disrupt or damage system operations.
DoS attacks consume system or network resources, rendering them unavailable.
Unauthorized access attacks probe computers or networks to discover vulnerabilities; sniff or intercept packets to gather information.
In addition, there have emerged some threats targeting typical scenarios of IIoT.
Physical attacks, for example, target physical transportation IoT devices, causing physical damage to traffic equipment nodes, such as power outages or moving node locations, resulting in information loss or leakage.
Perception data corruption involves unauthorized addition, deletion, modification, or destruction of perception data, such as tampering with power production data in renewable energy generation plants.
Control command forgery attacks involve sending forged control commands to disrupt or maliciously utilize the system, such as forging control commands for CNC machine tool IoT.
To protect industrial systems from network attacks, various security measures have emerged, such as encrypting communication data, data integrity checks, and access control methods, which can protect systems from multiple types of attacks. However, even with these security measures in place, attackers can still successfully launch attacks on systems, such as malicious packet injection and DDoS attacks. Therefore, it is necessary to conduct anomaly detection on networks to further ensure the security of industrial systems.
2 Anomaly Detection in IIoT
This section first introduces the types of anomalies present in IIoT, and then analyzes and organizes existing anomaly detection methods for different types of anomalies and application scenarios.
2.1 Types of Anomalies
Network attacks aim to compromise the confidentiality, integrity, and availability of system information and resources, often causing network operations to deviate from normal, exhibiting abnormal behavior. Therefore, anomalies can be identified by discovering patterns in data that do not conform to expected behavior. Currently, there are mainly 3 types of anomalies in IIoT [8].
Point anomalies are individual data instances that are abnormal compared to the rest of the data. For example, if the predefined range for water temperature sensor values is 30℃ to 40℃, then values outside this range will be considered an anomaly point.
Contextual anomalies are data instances that exhibit abnormal behavior only in specific contexts. These anomalies are often found in spatial or temporal data.
Collective anomalies refer to a set of related data instances that are abnormal compared to the entire dataset. Individual data instances in a collective anomaly may not be abnormal by themselves, but when they appear together as a set, they are considered abnormal. For example, a single TCP connection request is normal, but receiving multiple such requests consecutively from the same source may indicate a DoS attack, which is an anomaly.
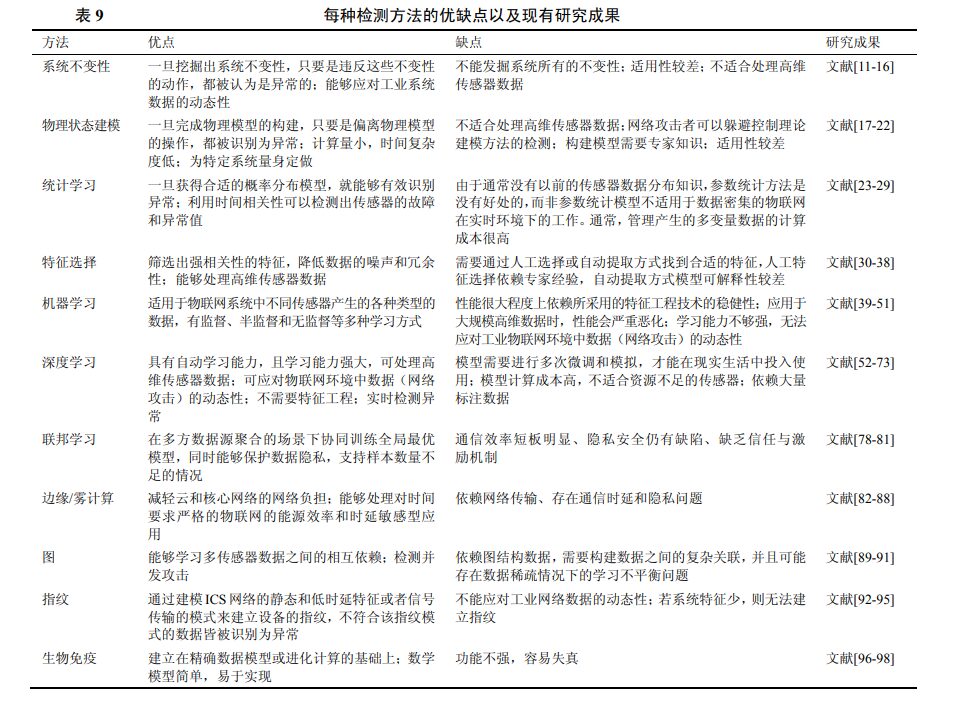
Network anomaly detection refers to the detection of anomalies in network traffic data, utilizing devices or software applications to monitor and analyze network traffic to detect malicious activities. Existing anomaly detection methods for IIoT can be categorized into detection methods based on system invariance, physical state modeling, statistical learning, feature selection, machine learning, edge/fog computing, graphs, fingerprints, and biological immunity. The following sections will introduce and analyze the technical principles, existing research results, advantages and disadvantages, and applicable application scenarios of each detection method in detail.
2.2 Detection Methods Based on System Invariance
System invariance refers to a condition in the “physical” or “chemical” characteristics of the system’s operation that must be satisfied whenever the system is in a given state. Detecting anomalies by analyzing physical invariance has been applied in many Cyber-Physical Systems (CPS) [11-14]. Reference [11] expresses the stability and correctness constraints of all components in the form of logical invariance, and system actions can only be executed if they do not violate these invariance. For the invariance of various CPS modules, reference [12] proposes unified invariance and develops a common semantics that spans various levels of the system. However, references [11-12] generate physical invariance manually, which is costly and prone to errors. To address this issue, reference [13] proposes using association rule mining algorithms to automatically identify system invariance, which can uncover invariance hidden in design layouts and avoid the tediousness of manual searching. However, this technique is only applicable to pairs of sensors and actuators, whereas in real CPS, all sensors and actuators work collaboratively across multiple processes. There are also studies that use machine learning algorithms to mine CPS physical invariance. For example, Momtazpour et al. [14] use externally discovered latent variable autoregressive models to identify invariance between wireless sensor data over multiple time steps. Chen et al. [15] use code mutation programs to generate anomalous data trajectories and then use Support Vector Machine (SVM) classifiers and statistical model checks to discover invariance between sensor data in a safe water treatment experimental platform. Reference [16] employs a combination of various machine learning and data mining techniques to systematically generate invariance from the operating logs of Industrial Control Systems (ICS) and the status information of actuators.
2.3 Detection Methods Based on Physical State Modeling
The underlying processes of CPS are generally controlled by their working principles; therefore, their process states are predictable. Anomaly detection methods based on physical models model normal physical operations based on physical states, allowing for the detection of network attacks from abnormal states that deviate from the physical operation model.
2.4 Detection Methods Based on Statistical Learning
Statistical anomaly detection methods create a distribution model for the dataset and match it with the target data objects. Normal data is assumed to fall within high-probability intervals, while abnormal data falls into low-probability intervals; anomalies are determined based on the probability of data in the target dataset fitting into the model. Rajasegarar et al. [23-24] established two types of anomaly detection models: statistical detection models and non-parametric detection models. These two models can be applied to different scenarios, with the former suitable for applications where data type and sampling period are predetermined, while the latter identifies anomalies by comparing current data with adjacent data without prior knowledge. Fei Huan et al. [25] proposed a multi-source data anomaly detection method, mainly applied in platform space, which determines the relationship between two nodes based on their two-dimensional coordinates. Similarly, reference [26] proposed a density-based model to discover anomalous behavior in solar power generation systems by analyzing electrical data.
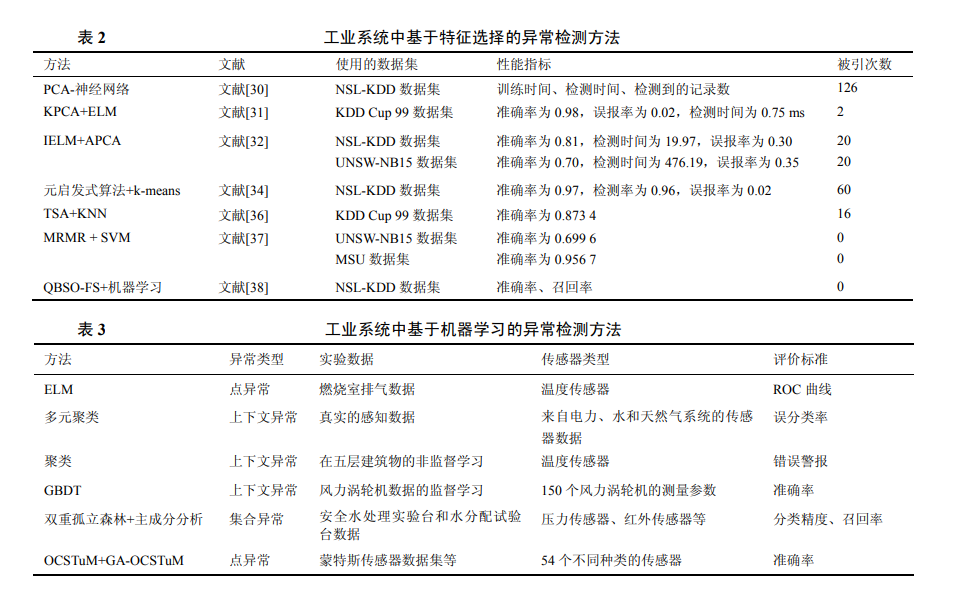
2.5 Detection Methods Based on Feature Selection
The data processed for anomaly detection is extracted manually from complex network systems. These data typically exhibit characteristics such as high dimensionality, strong redundancy, and low correlation. Using raw data directly can lead to poor performance of detection algorithms. Feature selection serves to select useful features from raw data; selected features exhibit stronger correlation, non-redundancy, and less noise. These features can help relevant algorithms differentiate, detect, and classify different targets more efficiently and quickly. Therefore, many researchers have applied it in the design of Intrusion Detection Systems (IDS) to improve detection accuracy and reduce detection time.

However, the aforementioned methods share a common drawback: the selected features possess a certain degree of randomness and uncertainty, making them inapplicable for subsequent selections. To overcome this issue and clarify the impact of different features on anomaly detection, reference [37] conducted a series of experiments based on the maximum relevance minimum redundancy feature selection algorithm and SVM classification method. Additionally, to further select effective features, reference [38] proposed a feature selection model called QBSO-FS, which combines swarm intelligence algorithms and reinforcement learning; experimental results indicate that this model outperforms traditional feature selection algorithms. The methods for anomaly detection based on feature selection in industrial systems are compared in Table 2.
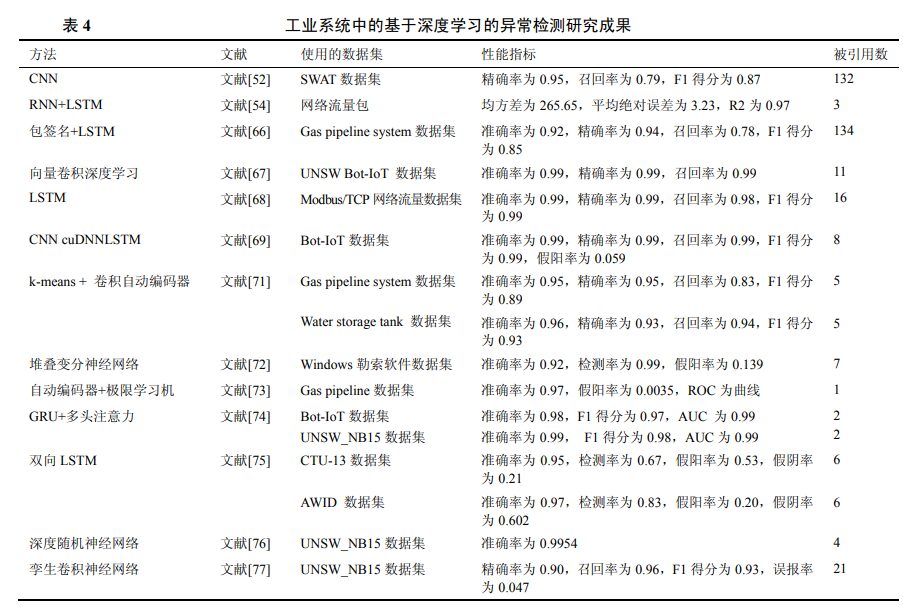
2.6 Detection Methods Based on Machine Learning
In industrial systems, machine learning methods (such as Bayesian networks, k-means, ELM [39], SVM, regression, etc.) have been successfully used to identify and detect anomalous behavior in IIoT [10]. Additionally, algorithms such as clustering [40-42], random forests [43], isolation forests [44], and hidden Markov models [45] have also achieved good results. Table 3 summarizes the machine learning-based anomaly detection methods in industrial systems.
One-Class Support Vector Machine (OCSVM) is a well-known anomaly detection algorithm applied in many fields; it learns the boundary of visible data and identifies all events or data points outside the boundary as anomalous behavior of the system [43, 46-47]. To further enhance the performance of OCSVM, reference [48] employed cloud gray wolf optimization algorithms to optimize OCSVM parameters. Experimental results indicate that this algorithm indeed improves the model’s detection accuracy to some extent. Unlike the work of reference [48], reference [49] proposed two anomaly detection algorithms that extend OCSVM to tensor space, namely single-class support tensor machine and genetic single-class support tensor machine based on tensor decomposition and genetic algorithms. Both are unsupervised anomaly detection methods for large sensor data, preserving data structure information while improving detection accuracy and efficiency.
Clustering methods group similar objects together in an unsupervised manner. After this automatic grouping, if a new data point cannot be placed into a predefined cluster (group), the system will classify that data point as an anomaly and generate an alert [40-42]. Gradient boosting trees are an ensemble learning classifier; reference [50] used them to detect early anomalies in wind turbine bolt fracture issues. This algorithm first generates multiple decision trees and then aggregates the results of all trees to make a final decision. However, gradient boosting trees have a significant drawback: they cannot handle massive data. To address this issue, reference [51] proposed a method that combines lightweight gradient boosting machines and Bayesian optimization to detect anomalies in industrial network traffic. This method improves detection efficiency and accuracy while reducing manual involvement in model training.
However, machine learning methods have the following three limitations: 1) performance largely depends on the robustness of the feature engineering techniques used, limiting stability; 2) performance severely deteriorates when applied to large-scale high-dimensional data; 3) learning ability is insufficient to cope with the dynamics of data (network attacks) in IIoT environments.
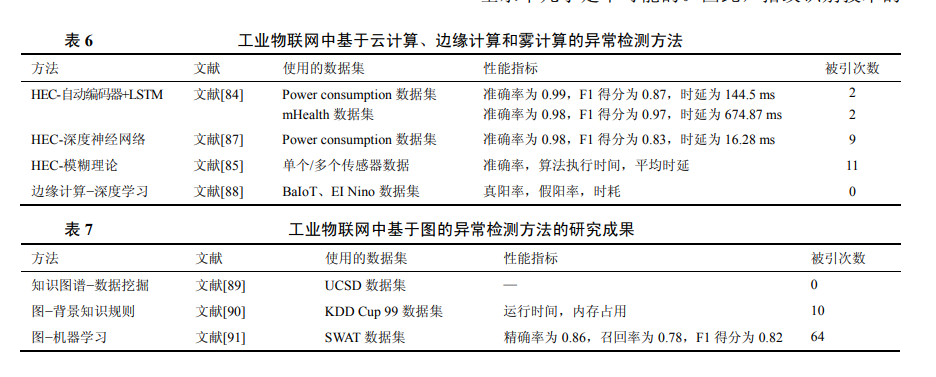
2.7 Detection Methods Based on Edge/Fog Computing
The advancements of deep neural networks greatly support the real-time detection of anomalous IoT data. However, due to limited computational power and energy supply, IoT devices can hardly afford complex deep neural network models. While it is possible to shift the anomaly detection task to the cloud, when thousands of IoT devices simultaneously transmit data to the cloud, it can cause delays and network congestion.
An emerging architecture—fog (edge) computing—addresses this issue. This architecture aims to alleviate the network burden on the cloud and core network by transferring resource-intensive functions such as computation, communication, storage, and analysis to end users. Fog computing systems can handle time-sensitive and energy-efficient applications of IoT, such as fire alarm systems in factories and underground mining environments, which require quick anomaly detection.
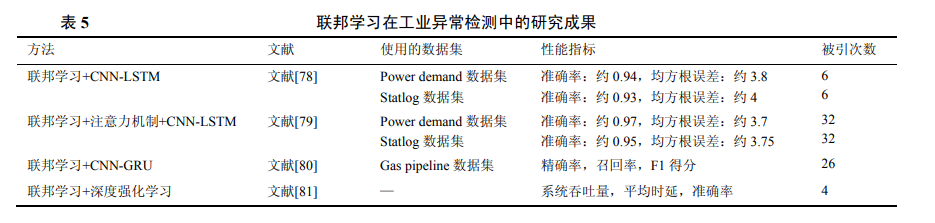
2.8 Detection Methods Based on Graphs
2.9 Detection Methods Based on Fingerprints
Convenient access to professional knowledge
Convenient download, please followSpecial Knowledge public account (click the above blue Special Knowledge to follow)
Reply “IOTAD” in the background to obtain《Latest 2022 Research Review on Industrial IoT Anomaly Detection Technology》 download link