1. Introduction
2. Overview of CAN Bus
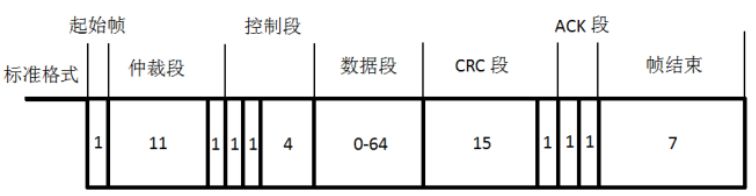
Figure 1 Standard CAN Frame Format
3. Security Challenges of CAN
4. Overview of Anomaly Detection Technology
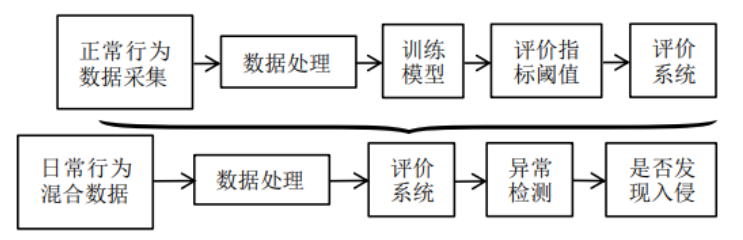
Figure 2 Anomaly Detection Model Diagram
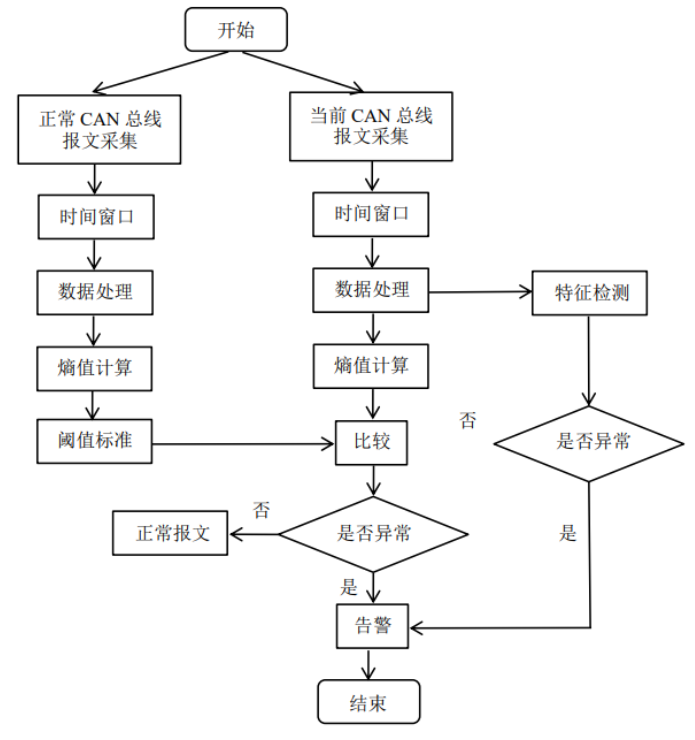
Figure 3 Anomaly Detection Model Based on Features and Information Entropy
5. Conclusion
References
[1] Navet N, Song Y, Simonot-Lion F, et al. Trends in Automotive Communication Systems[J]. Proceedings of the IEEE, 2005, 93(6):1204-1223.
[2] Qayyum A, Islam M H, Jamil M. Taxonomy of statistical based anomaly detection techniques for intrusion detection[C]. Emerging Technologies, 2005. Proceedings of the IEEE Symposium on. 2005:270 – 276.
[3] NAVAZ A S S, SANGEETHA V, PRABHADEVI C. Entropy based anomaly detection system to prevent DDoS attacks in cloud[J]. arXiv Preprint, arXiv:1308.6745, 2013.
[4] STUDNIA I, ALATA E, NICOMETTE V, et al. A language based intrusion detection approach for automotive embedded networks[J]. International Journal of Embedded Systems, 2018, 10(1):1-12.
[5] TIAN M Q, JIANG R B, XING C Q, et al. Exploiting temperature-varied ECU fingerprints for source identification in in-vehicle network intrusion detection[C]. 2019 IEEE 38th International Performance Computing and Communications Conference (IPCCC). Piscataway: IEEE Press, 2019:1-8.
[6] ZHAO Y L, XUN Y J, LIU J J. ClockIDS: a real-time vehicle intrusion detection system based on clock skew[J]. IEEE Internet of Things Journal. 2022, 9(17):15593-15606.
[7] MARCHETTI M, STABILI D, GUIDO A, et al. Evaluation of anomaly detection for in-vehicle networks through information theoretic algorithms[C]. IEEE International Forum on Research and Technologies for Society and Industry Leveraging a Better Tomorrow. Piscataway: IEEE Press, 2016:1-6
[8] ISLAM R, REFAT R U D, YERRAM S M, et al. Graph-Based intrusion detection system for controller area networks[J]. IEEE Transactions on Intelligent Transportation System, 2022, 23(3):1727-1736.
[9] LEVI M, ALLOUCHE Y, KONTOROVICH A. Advanced analytics for connected car cybersecurity[J]. IEEE 87th Vehicular Technology Conference, Piscataway: IEEE Press. 2018:1-7
[10] DING D F, ZHU L, XIE J Y, et al. In-vehicle network intrusion detection system based on BiLSTM[C]. 2022 7th International Conference on Intelligent Computing and Signal Processing (ICSP). Piscataway: IEEE Press, 2022:580-583.
[11] SEO E, SONG H M, KIM H K, et al. GIDS: GAN based intrusion detection system for in-vehicle network[C]. Annual Conference on Privacy, Security and Trust, Piscataway: IEEE Press, 2018:1-6.
[12] SONG H M, WOO J Y, KIM H K, et al. In-vehicle network intrusion detection using deep convolutional neural network[J]. Vehicular Communications, 2020, 21:100198.
China Association for Confidentiality
Scientific and Technological Branch
Scan the code to follow us

Author: Zhang Jianrong, Institute of Information Engineering, Chinese Academy of Sciences
Editor: Yan Jie
Top 5 Articles of 2023 Review
Using Sound Masking to Protect Audio Privacy in Mobile Calls
Overview of Integrated Sensing and Communication Technology (ISAC)
Overview of Electromagnetic Fingerprinting Technology
Introduction to Electromagnetic Metamaterials
Overview of Network Attack Traffic Detection Technology
Recent Highlights Review
Overview of RF Fingerprint Recognition Technology
Overview of Virtual Mobile Network Security
Anomaly-Based Intrusion Detection Methods
Towards 6G—Security Issues of Integrated Sensing and Communication (ISAC)
Covert Channel Attacks Under Air-gap Systems