Traditional industrial control systems differ from the open systems of the Internet, being individual and closed. However, with the application of industrial internet platforms, more and more devices are connected to enterprise networks, leading to an increasing number of cybersecurity issues. Traditional methods based on network traffic have encountered difficulties in anomaly detection, challenges in detecting dynamic threats like APTs, and inaccuracies in detection results. This article enumerates numerous manufacturers and research scholars both domestically and internationally regarding the research and application of anomaly detection methods in industrial control systems, analyzing their advantages and disadvantages, thereby providing a basis for the selection of automatic anomaly detection methods in industrial control systems.
The Purdue model of a typical Industrial Control System (ICS) architecture is shown in Figure 1.
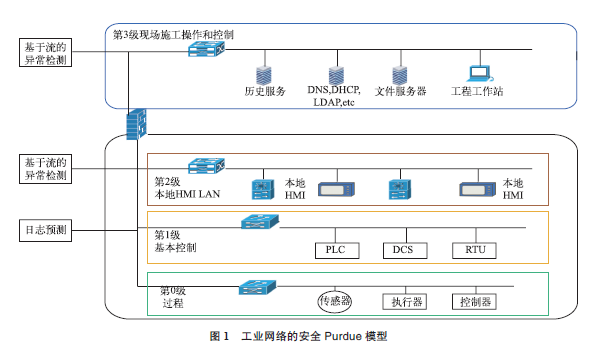
This architectural model provides six levels for interconnecting Information Technology (IT) and Operational Technology (OT) devices in the industrial internet platform: Level 0, field devices such as sensors and actuators; Level 1, local controllers such as Programmable Logic Controllers (PLCs); Level 2, Supervisory Control and Data Acquisition (SCADA) components and Distributed Control Systems (DCSs); Level 3, control centers and processing local area networks; Levels 4 and 5, enterprise zones. Level 2 SCADA systems are used for advanced monitoring and management of critical infrastructure. DCS is a control device in a distributed network, which is part of one or more industrial processes. PLCs are early control systems that interact with physical devices, managing ongoing processes locally through feedback control devices (such as sensors and actuators).
With the development of industrial internet technology, more ICS devices are connecting to traditional company information networks, facilitating remote access and overall planning for users. However, this exposes industrial control systems to the Internet, making them susceptible to cyberattacks. Research shows that the number of recorded attacks on industrial control infrastructure has sharply increased in recent years, leading to growing user concerns about the security of industrial control systems. Advanced attacks on ICS can jeopardize industrial infrastructure, and malicious activities in industrial devices may be reflected in various data sources of control systems, such as network traffic (captured from Ethernet-based components) and device logs.
Current Status of ICS Network Detection
Monitoring all data sources in the ICS network helps security analysts detect attacks early, preventing irreparable losses. However, most of the anomaly detection methods proposed in recent years are based on localized analysis of industrial control system structures, and such detection methods are not suitable for large-scale and multi-level industrial control networks with different types of data sources. Consequently, many scholars and enterprises have begun to research detection methods for global and multi-dimensional control networks, such as component analysis methods. However, much of this research focuses on anomaly detection for a single type of data source, optimizing different algorithms to enhance the accuracy of anomaly detection in control devices.
Furthermore, detecting anomalies caused by APT attacks in IT and ICS networks is also a research hotspot for automatic anomaly detection methods in industrial control systems. APT attacks exhibit dynamic behavioral characteristics and possess a certain randomness, following different attack techniques and strategies to achieve their goals. Anomaly detection methods based on attack characteristics are specifically designed for detecting APT attacks. However, it has been verified that this detection method is ineffective against zero-day vulnerabilities. In such cases, a detection method that combines coupling correlation analysis and causal analysis is adopted for anomaly detection. This method requires network slicing, with anomaly detection strategies pre-stored in each network layer. Although these methods aim to detect APT attacks, most studies assume that intrusion detection strategies are already pre-existing in each layer of the network, associating security and non-security logs over time to visualize the attacker’s path and predict future actions.

Common Methods for Anomaly Detection in ICS Security
Currently, domestic and international methods for anomaly detection in industrial control systems can be broadly categorized into three types: the first type is anomaly detection methods based on deep learning algorithms, which combine the temporal characteristics of industrial control networks, with the most commonly used being the unsupervised learning nonlinear time series “ARIMA+GARCH” hybrid model; the second method is based on multi-layer network traffic anomaly detection methods, which layer the industrial control system’s industrial processes and analyze based on payload and packet header data; the third is a multi-layer network traffic anomaly detection method coupled with deep learning algorithms. As deep learning algorithms continue to be optimized, the industrial internet facilitates multi-source fusion of industrial control data, and these methods are bound to become the primary methods for anomaly detection in industrial control systems.
3.1 Anomaly Detection Methods Based on Deep Learning Algorithms
Supervised learning is the most common type of deep learning algorithm and corresponds to the most algorithm models. Although supervised learning methods in anomaly detection can provide higher detection accuracy, the data labeling process for these methods is very tedious and time-consuming, making them impractical for complex industrial control systems with multi-source heterogeneous data in the real world. Therefore, unsupervised methods are generally adopted for automatic anomaly detection in industrial control systems. For example, in Oliveira et al.’s multi-layer industrial control system anomaly detection method, the first layer is an unsupervised clustering method for identifying malicious network flow records; the second layer is based on the behavioral pattern analysis of physical devices. The algorithm model used, ARIMA/GARCH, is employed to create a normal behavior model and predict future values. Any deviation between the actual and predicted values in their model is considered an anomaly, indicating that the current industrial control system is under attack.
In practice, most anomaly detection methods based on deep learning algorithms use the nonlinear time series “ARIMA+GARCH” model to predict the expected future values of PLC logs from correlated variables. This model effectively couples the linear characteristics of the ARIMA model with the nonlinear characteristics of the GARCH model. When correlations exist between values over different time periods, the ARIMA model can be used for time series forecasting. The GARCH model better describes the nonlinear characteristics of time series, including more volatility information, and allows conditional variance to depend on previous values. The “ARIMA+GARCH” hybrid model is a combination of the ARIMA model and the GARCH model, which can significantly improve the prediction accuracy of anomaly detection.
In the actual detection process, ICS device logs follow a predictable model of expected behavior. Manual tuning is generally used to discover this behavior model, and this process requires coupling ICS and its related industrial processes. Therefore, it can detect deviations from the expected behavior model and send alerts for anomalous behavior. PLC logs can be stored on the device or through HMI storage, with HMI communicating with PLCs based on commands and logs. Wireshark is a common network traffic analyzer that can be installed on the HMI of factory automation datasets to capture PLC logs.
3.2 Anomaly Detection Methods Based on Multi-Layer Network Traffic
Network traffic analysis is divided into payload-based analysis and packet header-based analysis. Anomaly detection based on payload in ICS environments is a well-researched area. Analyzing network traffic can be used to detect network attacks that affect network traffic. This method can detect attacks such as port scanning, DNS poisoning, DoS, and DDoS attacks. The lack of payload analysis makes NetFlow-based methods scalable, fast, and cost-effective for anomaly detection. Therefore, NetFlow-based analysis can detect them in the early stages before flood attacks affect the entire network. This method can serve as a complementary approach to payload-based anomaly detection methods.
NetFlow is a proprietary protocol from Cisco that can be enabled on router devices to provide NetFlow logs. Network flow records are defined as a set of packets with some common features that pass through a monitoring point within a specific time interval. Compared to payload-based methods, network flow analysis methods significantly reduce the amount of traffic to be processed. For example, in the IT network at Twente University, the ratio of traffic output by NetFlow to packets on the network is 0.1. Dong et al. have utilized this network traffic-based anomaly detection method, proposing an intrusion detection method based on mapping periodic traffic features to hash summaries using discrete cosine transform and singular value decomposition, which has shown superior detection performance. Markman et al. proposed a proxy-based traffic model, in which the communication cycle between PLC and HMI/engineering workstations can be modeled as a deterministic finite automaton pattern, improving the accuracy of network traffic detection methods.
3.3 Anomaly Detection Methods Coupled with Deep Learning Algorithms for Multi-Layer Network Traffic
Conventional network traffic-based anomaly detection methods can monitor distributed ICS data sources, including NetFlow data. Since network flow detection methods are based solely on packet header data, they significantly reduce the workload of data analysis, and the encryption of payloads does not affect their results. Furthermore, network devices (such as routers and switches) can easily generate and collect network flow data, making it relatively easy to produce large amounts of analyzable detection data. By using network flow analysis and log analysis, anomaly detection methods coupled with deep learning for network traffic perform significantly better than those based solely on network packets or device logs.
The main difference between traditional information systems and industrial control systems is that the latter are integrated into physical devices. This integration introduces new types of vulnerabilities and increases the complexity of anomaly detection. For example, for multi-layer integrated circuit networks, it is necessary to adopt anomaly detection methods for multi-layer network traffic coupled with deep learning algorithms.
Although network traffic-based methods can be used for anomaly detection in ICS networks, the inherent problem with network traffic-based anomaly detection algorithms is that they cannot identify abnormal behaviors of compromised workstations at the supervisory control layer. For instance, attackers can access operator credentials and use them to send commands that disrupt physical processes. To address this challenge, researchers have proposed anomaly detection algorithms based on physical processes. This method can identify attacks from compromised workstations. However, this algorithm is inefficient in detecting DoS and DDoS attacks that affect the top layer of ICS network traffic. DDoS or DoS attacks on ICS can be effectively detected at the network layer before they impact physical processes.

Traditional industrial control systems are different from the open systems of the Internet, being individual and closed. However, with the application of industrial internet platforms, more and more devices are connected to enterprise networks, leading to an increasing number of cybersecurity issues. Industrial control networks themselves possess distributed characteristics, and with the implementation of policies like the industrial internet, the boundaries of industrial control networks are becoming increasingly blurred, showing a higher correlation with industrial process workflows, and the strong temporal characteristics of industrial processes are becoming more evident. Traditional methods based on network traffic have encountered difficulties in anomaly detection, challenges in detecting dynamic threats like APTs, and inaccuracies in detection results.
This article enumerates numerous manufacturers and research scholars both domestically and internationally regarding the research and application of anomaly detection methods in industrial control systems, analyzing their advantages and disadvantages,
providing a basis for the selection of methods for automatic anomaly detection in industrial control systems. It points out that as deep learning algorithms continue to be optimized, the industrial internet promotes multi-source fusion of industrial control data, and anomaly detection methods coupled with deep learning algorithms for multi-layer network traffic will inevitably become the primary methods for anomaly detection in industrial control systems.
(Scan to subscribe to the 2022 issue 4 magazine)
(Scan to subscribe to the entire 2022 magazine)
For submissions, please click “Read the original text”

This article is selected from: “Smart Manufacturing” 2022 Issue 4, pages 99-102
Original column: Software Applications
Original title:Overview of Automatic Anomaly Detection Methods in Industrial Control Systems
Authors: Liu Rufang, Jiang Yaguang, Wang Duan, Lin Xin, Gao Huifang
Affiliation: China Software Testing Center (Software and Integrated Circuit Promotion Center of the Ministry of Industry and Information Technology)
Editor: Hou Yuanyuan
Chief Editor: Wu Yongjiang
Reviewer: Zhou Zhengyu



Long press to recognize the QR code for more information

Pleasefollowthe video account
to learn more about smart manufacturing news