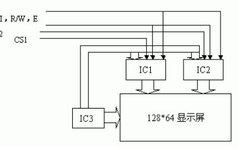
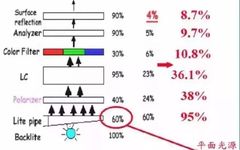
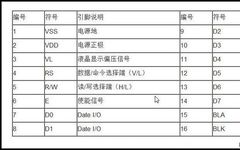
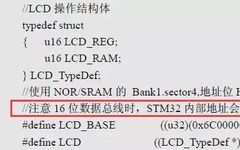
OLED vs Micro/Mini LED: Advantages Compared
From LG Display official website introducing OLED Comparison of OLED with traditional LCD screens From LG Display official website Being “thin” and “curved”. Since OLED does not require a large backlight layer and liquid crystal layer, it has a natural advantage in thickness over LCDs, allowing it to achieve extremely thin forms, which is in … Read more