1. Basic Concepts
HTTP: is the most widely used network protocol on the Internet, serving as a standard for requests and responses between clients and servers. It is a protocol used to transfer hypertext from WWW servers to local browsers, making browsing more efficient and reducing network transmission.
HTTPS: is a secure version of HTTP, aimed at security. In simple terms, it is HTTP with an added SSL layer. The security foundation of HTTPS is SSL, so the details of encryption rely on SSL.
2. Browsers’ Attitudes Towards HTTPS
Browsers like Google Chrome and Firefox have begun marking HTTP sites as unsafe in their new versions. An increasing number of third-party services, especially payment APIs, recommend or even require sites to support HTTPS.
Below is a comparison of the display effects before and after the upgrade to HTTPS on the official website of the Chanzhi Enterprise Portal Building System:
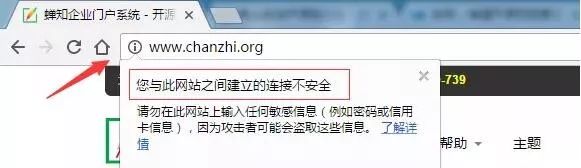
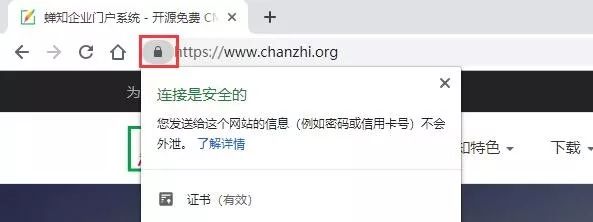
3. Search Engines’ Attitudes Towards HTTPS
Baidu: Baidu announced in 2015 that it would fully support HTTPS pages for direct indexing. Moreover, from a relevance perspective, Baidu’s search engine considers pages using HTTPS to be more secure and prioritizes them in rankings if other factors are equal. Although Baidu’s actual indexing of HTTPS sites was not ideal initially, it has become much friendlier towards HTTPS sites after several years of adjustments.
Google: In comparison to Baidu, Google’s search engine has a more mature and refined algorithm for indexing and ranking HTTPS pages. After upgrading my site to HTTPS, Google’s indexing speed and volume were quick, while Baidu lagged significantly behind.
Other search engines like 360 and Sogou have also announced that they will prioritize indexing HTTPS sites. Webmasters should note that after upgrading to HTTPS, it is advisable to redirect old HTTP page URLs to HTTPS.
4. Recommended Free SSL Certificates
When discussing HTTPS, we must first mention SSL certificates. SSL certificates are security guarantees for information transmission. The SSL security protocol provides authentication for users and servers, encrypts and hides transmitted data, ensuring that data is not intercepted or tampered with during transmission, and guarantees the security of data exchange between requesters and service providers.
Here are some recommended free SSL certificate providers:
1. Let’s Encrypt SSL Certificate
Let’s Encrypt is a public free SSL project managed by the Linux Foundation, initiated by organizations like Mozilla, Cisco, Akamai, IdenTrust, and EFF. Its goal is to automatically issue and manage free certificates for websites to accelerate the transition from HTTP to HTTPS.
Let’s Encrypt’s downside is that the validity period of an issued SSL certificate is 90 days. Although it can be renewed for free, it can be troublesome for website operations if one forgets to renew. Of course, we can set up automatic updates on the server. My personal website uses Let’s Encrypt, which I highly recommend.

2. Symantec DV SSL Certificate
Symantec is an Internet security technology company headquartered in Mountain View, California. Its SSL service originated from VeriSign. In 2010, VeriSign, Inc. sold its certification business to Symantec for $1.28 billion, including SSL certification services and public key infrastructure (PKI) services.
Most domestic free SSL certificate providers are actually collaborations with Symantec to offer free DV SSL certificates.

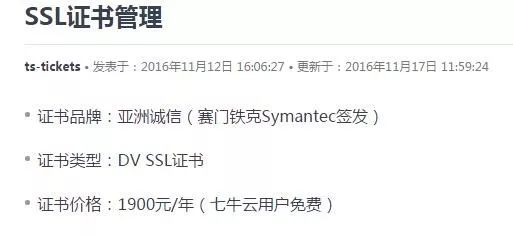
3. Tencent Cloud SSL Certificate
After registering and verifying identity on Tencent Cloud, you can apply for a free SSL certificate. The free version is a DV SSL issued by AsiaTrust, and the issuer is Symantec. However, the free term is one year, after which a renewal fee is required.
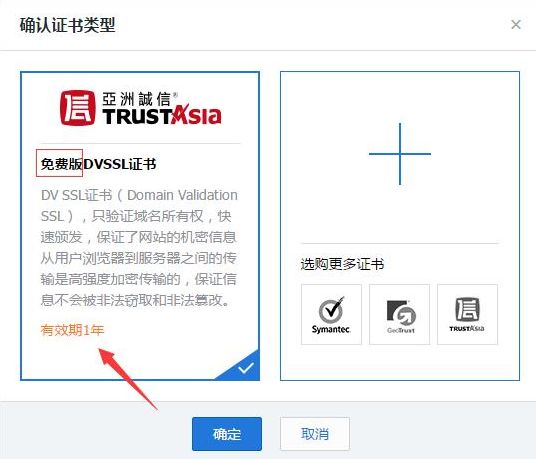
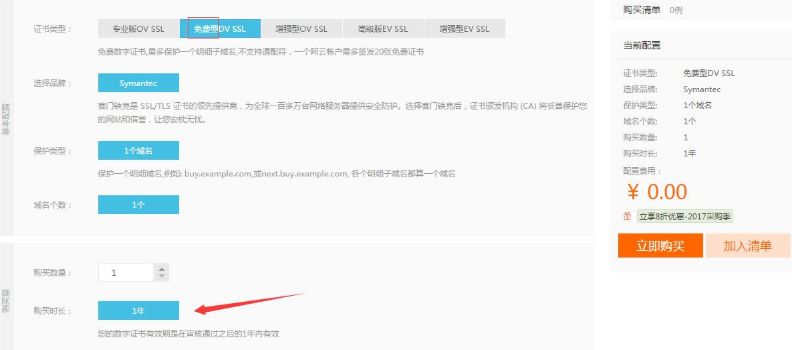
4. Alibaba Cloud SSL Certificate
Alibaba Cloud also provides free SSL certificate services, and the free certificate is also a DV SSL issued by Symantec, with a free term of one year.
5. Qiniu Cloud SSL Certificate
Qiniu recently partnered with AsiaTrust to offer DV SSL certificates issued by Symantec, with a free term of one year.
The three cloud platforms recommended above all provide free SSL certificate services, although the free term is only one year, and currently, there are no intentions for permanent free offerings. However, these three companies are well-known and reliable in China, ensuring users can feel at ease regarding service and technical support.
When choosing an SSL certificate provider, factors to consider include cost, installation environment, and after-sales service, but special attention must also be paid to compatibility support across major browsers. Some SSL certificates have poor browser compatibility, with StartSSL being a notable example. StartSSL lost trust from browsers like Chrome, Apple, and Firefox after July 2016 due to issues with 360, so caution is advised in selection.
5. Practical Deployment Process for HTTPS
Service Environment
Operating System: centos6.5 x64
Web Service: Apache 2.4+
Website Program: Chanzhi Enterprise Portal System
Free Certificate Provider: Let’s Encrypt SSL
1. Install Certificate
I am using the Let’s Encrypt SSL free certificate, which has a validity period of 3 months and needs to be updated regularly.
Download certbot and set permissions:
wget https://dl.eff.org/certbot-autochmod a+x certbot-autoUse certbot to apply for and install the certificate:
./certbot-auto certonly --webroot -w /data/wwwroot/www.chanzhicms.com -d www.chanzhicms.com-w is followed by the root directory path of the website, and -d is followed by the domain name for which the certificate is requested. If there are multiple domain names, continue adding -d for each.
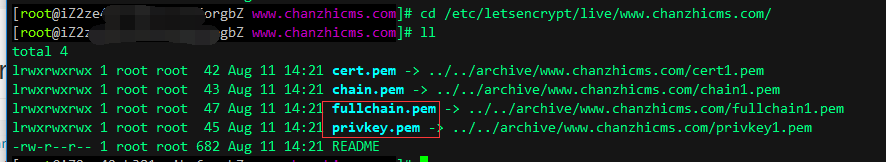
After a successful application, you can view the expiration date of the SSL certificate. The applied certificate is stored by default in the /etc/letsencrypt directory.
2. Modify Apache Configuration File
Set the Apache configuration file /usr/local/apache/conf/httpd.conf. You need to modify two places; find the following two lines and uncomment them.
LoadModule ssl_module modules/mod_ssl.soInclude conf/extra/httpd-ssl.confThen modify the /usr/local/apache/conf/extra/httpd-ssl.conf file, clear its contents, and insert the following:
Listen 443AddType application/x-x509-ca-cert .crtAddType application/x-pkcs7-crl .crlSSLCipherSuite EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5SSLProxyCipherSuite EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5SSLHonorCipherOrder onSSLProtocol all -SSLv2 -SSLv3SSLProxyProtocol all -SSLv2 -SSLv3SSLPassPhraseDialog builtinSSLSessionCache "shmcb:/usr/local/apache/logs/ssl_scache(512000)"SSLSessionCacheTimeout 300Mutex sysvsem defaultSSLStrictSNIVHostCheck onFinally, modify the individual configuration file of the website, /usr/local/apache/conf/vhost/www.chanzhicms.com.conf, which originally only had the 80 port configuration, here we need to add the 443 port configuration:
<VirtualHost *:80> ServerAdmin [email protected] DocumentRoot "/data/wwwroot/www.chanzhicms.com" ServerName www.chanzhicms.com ServerAlias chanzhicms.com ErrorLog "/data/wwwlogs/www.chanzhicms.com_error_apache.log" CustomLog "/data/wwwlogs/www.chanzhicms.com_apache.log" combined<Directory "/data/wwwroot/www.chanzhicms.com"> SetOutputFilter DEFLATE Options FollowSymLinks ExecCGI Require all granted AllowOverride All Order allow,deny Allow from all DirectoryIndex index.html index.php</Directory></VirtualHost>Listen 443<VirtualHost *:443> DocumentRoot "/data/wwwroot/www.chanzhicms.com" ServerName www.chanzhicms.com:443 ServerAlias www.chanzhicms.com ErrorLog "/data/wwwlogs/www.chanzhicms.com_error_apache.log" ServerAdmin [email protected] SSLEngine on SSLCertificateFile /etc/letsencrypt/live/www.chanzhicms.com/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/www.chanzhicms.com/privkey.pem <Directory "/data/wwwroot/www.chanzhicms.com"> SetOutputFilter DEFLATE Options FollowSymLinks AllowOverride All Order allow,deny Allow from all DirectoryIndex index.html index.php Require all granted </Directory></VirtualHost>The website name, path, certificate path, and other information in the above configuration should be filled in according to your specific situation.
Note:
It must be emphasized that because my Apache version is 2.4+, in the Directory, you must add Require all granted, otherwise, the website may show 403 forbidden when accessed via HTTPS, even though HTTP access works fine. This command is a new addition in Apache 2.4, replacing the allow, deny, and order directives.
Finally, restart Apache! Restart Apache! Restart Apache!
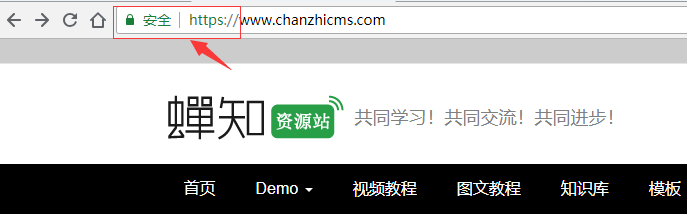
Use HTTPS to access the website and check if it is effective. See the image below:
6. Certificate Renewal
When the certificate is about to expire, Let’s Encrypt will send an email reminder. We use the certbot-auto renew command to renew the certificate.
certbot-auto renewAfter a successful SSL certificate renewal, check the updated expiration date.
./certbot-auto certificates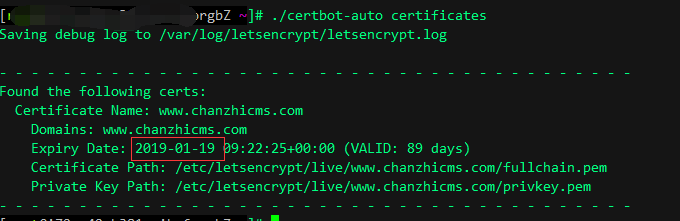
7. Common Issues
1. Error when installing the certificate, unable to verify the website.
This issue took a long time to resolve. I finally saw a similar problem on StackOverflow, where someone mentioned it might be related to the CDN. Since I had added my domain to Baidu’s CDN acceleration, I removed the CDN and tried again, and the problem was indeed resolved. I note this here, as it may help others.
2. The website works normally on http://, but https:// shows a 403 forbidden error.
Because my Apache version is 2.4+, in the Directory, you must add Require all granted, otherwise, it will show a 403 forbidden error when accessing via HTTPS while HTTP works fine. This command is a new addition in Apache 2.4, replacing the allow, deny, and order directives.
3. Stuck on Installing Python packages… when updating the SSL certificate.
The certificate can only be used for free for 3 months, and there were issues when updating the SSL certificate, getting stuck on Installing Python packages. See the image below:
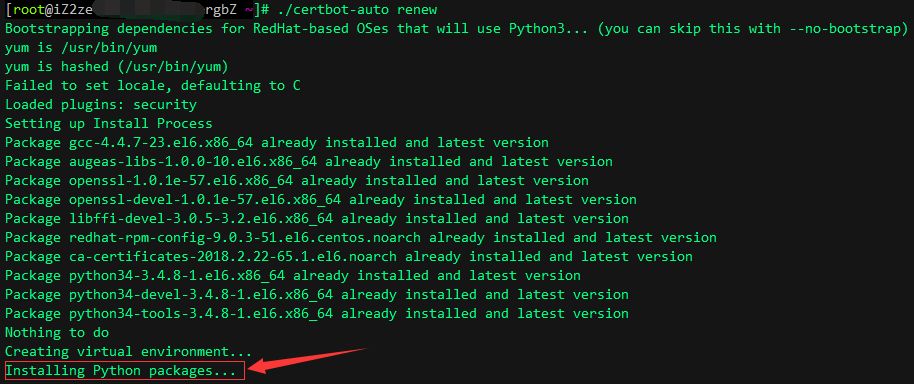
I am using Alibaba Cloud’s ECS server with centos6.5 x64. To solve this problem, simply modify the pip.conf file and replace Alibaba Cloud’s mirror with Tsinghua’s mirror. The method is as follows:
vim ~/.pip/pip.conf
[global]index-url=https://pypi.tuna.tsinghua.edu.cn/simple/[install]trusted-host=pypi.tuna.tsinghua.edu.cn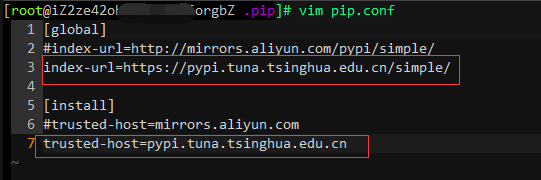
After saving the changes, try ./certbot-auto renew and ./certbot-auto renew again, and it should work normally.
4. When updating the certificate, an error message appears: The manual plugin is not working.
When the certificate is about to expire, I used the certbot-auto renew command to renew the certificate, but received the following error:
Attempting to renew cert (www.chanzhicms.com) from /etc/letsencrypt/renewal/www.chanzhicms.com.conf produced an unexpected error: The manual plugin is not working; there may be problems with your existing configuration.The error was: PluginError('An authentication script must be provided with --manual-auth-hook when using the manual plugin non-interactively.',). Skipping.All renewal attempts failed. The following certs could not be renewed: /etc/letsencrypt/live/www.chanzhicms.com/fullchain.pem (failure)Solution:
-
Create a manual authorization script and enter the following command
vim /etc/letsencrypt/renewal/www.chanzhicms.com.sh#!/bin/bashecho $CERTBOT_VALIDATION > /path/to/wwwroot/.well-known/acme-challenge/$CERTBOT_TOKENWhere /path/to/wwwroot/ is your domain verification site’s root directory.
Make the script executable:
chmod +x /etc/letsencrypt/renewal/www.chanzhicms.com.sh-
Execute the command with parameters
certbot-auto renew --manual-auth-hook /etc/letsencrypt/renewal/www.chanzhicms.com.sh-
After success, check the updated expiration date
./certbot-auto certificates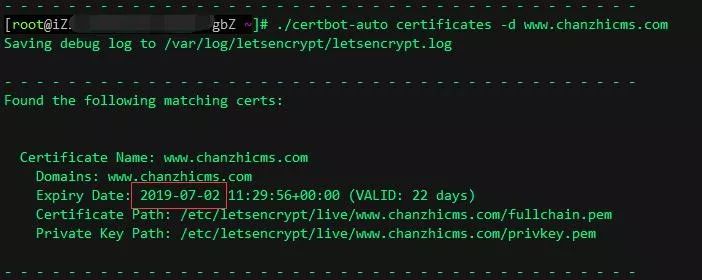
8. Conclusion
In this article, we introduced relevant knowledge and practical operations of HTTPS from the aspects of concepts, browsers, search engines, SSL certificates, and the deployment and update processes of HTTPS. HTTPS is the trend of the times, and it is strongly recommended that sites that have not yet deployed the HTTPS protocol upgrade as soon as possible. If you have any other related questions, feel free to discuss and communicate.
