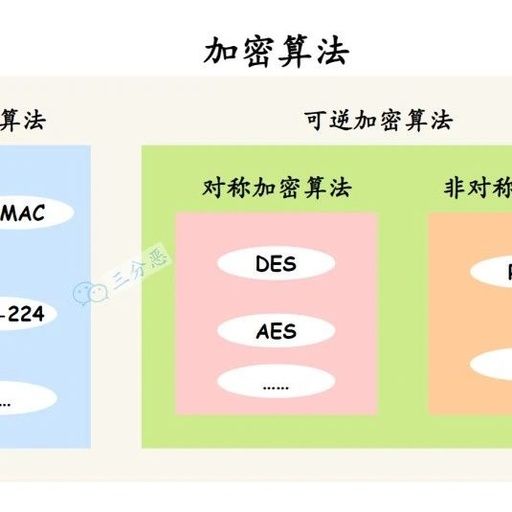
Overview of Five Common Encryption Algorithms
Source丨Authorized Reprint from Sanfen E (ID: Fighter3FullStack) Author丨Sanfen E Introduction In our daily work, we often use encryption and decryption in various scenarios, such as: User passwords should not be stored in plaintext; they must be stored as encrypted ciphertext. Sensitive data like bank card numbers and ID numbers need to be transmitted securely. For … Read more