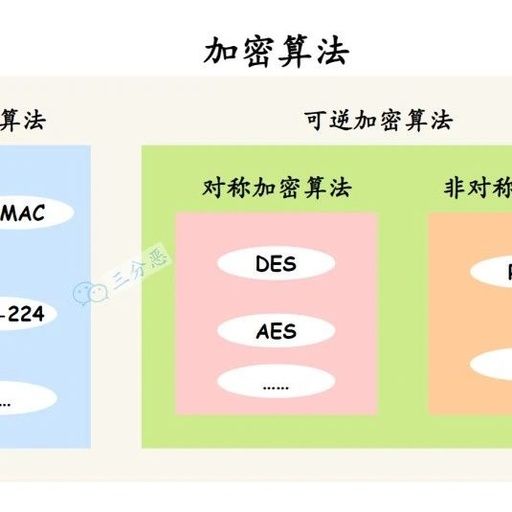
Understanding RSA Algorithm Principles: Overview of Common Encryption Algorithms
Alan Turing was primarily responsible for breaking the German Enigma cipher system during World War II. Decrypting codes required extensive computation, and Turing understood that to do a good job, one must first sharpen their tools. Thus, a computer called COLOSSUS was developed in 1943, and a total of 10 such electronic computers were produced, … Read more