Understanding the BIOS Chip on the Motherboard
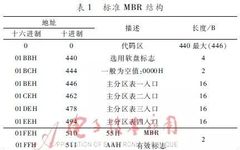
1. What is BIOS The term BIOS first appeared in 1975, and it stands for Basic Input Output System. It truly gained prominence with the launch of the IBM PC in 1981, marking the beginning of a tumultuous history. The IBM PC system generally consists of three parts: hardware, software, and the middleware BIOS, with … Read more