Author / Tao Jianfeng, Director of Information Technology Department, CITIC Construction Investment Securities Co., Ltd.
Du Guowei, Chen Hongping, CITIC Construction Investment Securities Co., Ltd. Information Technology Department
Since the implementation of the “Cryptography Law of the People’s Republic of China”, it has effectively promoted the advancement of cryptographic technology, industry development, and standardized applications. In the securities and futures industry, internet securities businesses represented by online trading and online account opening have developed rapidly, facilitating a wide range of investors to conduct various businesses through the internet, promoting innovation and development in the capital market. To further enhance the cryptographic security of securities and futures information systems, the financial industry has comprehensively promoted the application of the SM (Commercial Cryptography) series of cryptographic algorithms since 2016.
Research on Trading Data Encryption Security
Securities companies actively respond to the demand for commercial cryptography applications, reinforcing the cryptography of online trading systems. The logical overall technical architecture of the online trading system consists of an online trading client, SSL (Secure Socket Layer) access gateway, and online trading server. As the entry point for users to complete stock trading via the internet, it must provide a user-friendly trading interface while also ensuring a fast, secure, and stable trading access environment. As a crucial part of securities trading, the online trading system connects the internet on one end and the online trading backend system located in the corporate intranet on the other. In terms of data security and protection, it has always been one of the key targets for prevention in the securities industry information systems and is also the focus and entry point for this cryptographic application for access security reinforcement (see Figure 1).
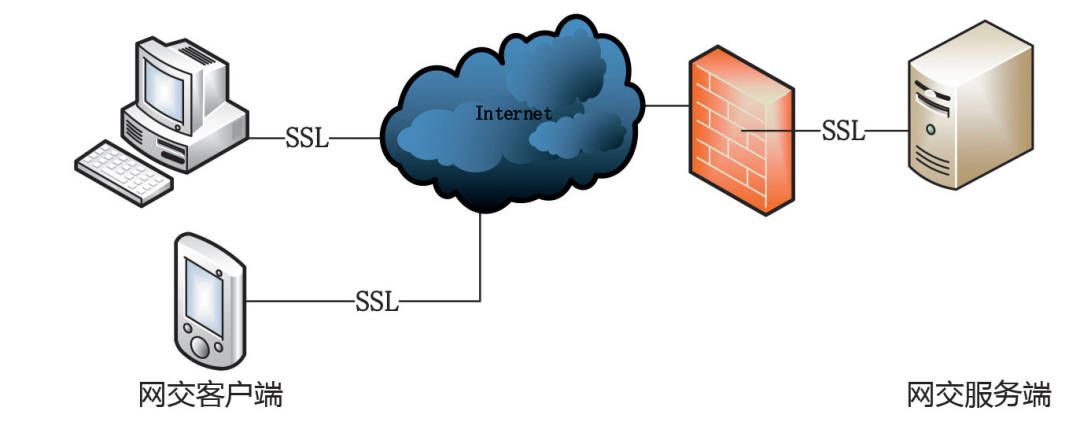
Figure 1 Logical Structure of the Online Trading System
1. Implementation of Digital Encryption Algorithms.The access security reinforcement password mainly uses SSL-VPN (secure protocol) to encrypt the client, and the SSL-VPN encryption server is responsible for channel security and implements identity verification of communication entities, ensuring the safety of user trading in the complex environment of the internet. The underlying communication transmission encryption algorithm replacement between the online trading client and the commission main station mainly involves replacing DES (Data Encryption Standard) and AES (Advanced Encryption Standard) with SM4, RSA (encryption algorithm) with SM2, and MD5 (message digest encryption algorithm) with SM3. The collaborative signature subsystem provides operations for key component cryptographic algorithms, collaboratively generates signature data, and decrypts data; the key management subsystem implements key lifecycle management functions and provides comprehensive permission management; the digital certificate subsystem provides certificate service functions, including certificate application, certificate download, certificate revocation, etc.
2. Random Number Generation. The online trading system client random number generator construction process is divided into three approaches, mainly including: First, generating a 256-bit random number R1 from the noise source chip in the SSL access gateway password card and sending it to the client. Second, the client collects the physical random sequences from the terminal, using noise data including the interval between two device interrupts, the operation time interval of the input device, and the time interval of continuous disk operations, and can also use gravity sensors, geomagnetic sensors, and acceleration sensors. It ensures that at least 2 collection sources are selected as random sources. The specific collection process is: each collection of a 32-bit sequence, and performing physical random source failure detection (the method for detecting failure of the physical random source includes all “0” and all “1” detection. The sample length for all “0” and all “1” detection is 32 bits, and if all “0” and all “1” samples appear during detection, the physical random source is determined to have failed). When the accumulated collected random sequence reaches 4096 bits, the random sequence data is processed through SM3 to calculate a 256-bit random number R2. Third, the application program simultaneously sends a kernel-mode pseudo-random number request to the operating system kernel, which generates a 256-bit kernel-mode pseudo-random number R3 through the kernel-mode pseudo-random number generator.
The random number generator performs an XOR operation on the gateway password card random number R1, the physical random source random number R2, and the kernel-mode pseudo-random number R3 to obtain the final 256-bit random number.
3. Collaborative Signature Technology.The online trading system collaborative signature technology follows the “Information Security Technology Cryptographic Module Security Requirements” and “SM2 Cryptographic Algorithm Usage Specifications”. Collaborative signature technology mainly realizes key split storage based on the SM2 signature algorithm and collaborative signature methods. Specifically, both the client and server store parts of the private key, and both parties must collaborate to perform the signature operation on messages, ensuring that neither party can obtain any information about the other’s private key. Therefore, even if an attacker invades either party, they cannot forge signatures, thus improving the security of the user’s private key. The implementation process is as follows.
In the key split generation phase, the client generates a 256-bit random number using the random number generator, and the client device information generates the user signature key component through the cryptographic algorithm. This key is generated using the user’s input PIN (Personal Identification Number) and the data hashed using SM3 from the operating environment parameters. The key component is encrypted and stored using the SM4 symmetric cipher algorithm, and the client calculates the public key factor and sends it to the server, which computes the user’s public key.
In the collaborative signature phase, the client calculates the intermediate signature result and sends it to the server. The server calculates the server-side intermediate signature result, and upon receiving the response, the client uses the server-side signature intermediate result to perform the synthesis signature operation, generating the actual digital signature, completing the signature operation.
4. Key Management System.The online trading system key management system follows the industry standard algorithms published by the National Cryptography Administration, supporting SM4 symmetric cipher algorithm, SM2 asymmetric cipher algorithm, and SM3 hashing algorithm, implementing key lifecycle management functions, including generation, import, storage, backup, recovery, and cancellation of keys, and providing comprehensive permission management and security auditing.
The key management service module within the key management system is responsible for generating user keys. The key generation process calls the hardware cryptographic module to complete it, using algorithms approved by the National Cryptography Administration. The generated keys are encrypted and protected by the main key stored in the encryption device’s memory and are encoded and stored in the database. After generation, the keys are encrypted and stored by the internal key in the password card, supporting the generation and management of SM series keys. The key generation and cryptographic operations of the key management system are provided by hardware, ensuring the security of sensitive information and the efficiency of cryptographic operations.
5. Digital Certificate System.A digital certificate is a digital credential that certifies user identity in the digital realm. It is used to sign user information to ensure non-repudiation and encrypt the information sent to users, achieving authenticity and integrity of the information. The digital certificate system provides lifecycle management functions for certificates, including application, review, issuance, publication, updates, and revocation.
6. SSL VPN Encryption Client.The client is based on the client protocol functions specified in the “SSL VPN Technical Specification”, providing the capability to establish a secure connection between the client and the SSL access gateway, integrated as functional modules within the client. When the client initiates a connection, it interacts with the SSL access gateway through SSL handshake protocol data exchange, verifying the server’s identity with a digital certificate, negotiating the session key for the connection, and after the handshake is completed, encrypting the client’s request data and decrypting the response data for use by the business application module. The functions of each component are as follows.
In the client collaborative signature module, the client collaborative signature module collaborates with the SSL access gateway collaborative signature module to generate SM2 key components, providing private key operations related to signing and decryption. The collaborative cryptographic module itself provides security reinforcement, combined with anti-reverse engineering technology obfuscation to prevent the cryptographic module from being debugged and cracked. It provides the following functionalities: collaborative signature initialization, generating parameters related to collaborative signatures; creating digital signatures, signing data using the collaborative signature scheme based on input data, and returning a digital signature that conforms to the GM/T0009 format.
In the client key management module, the key management module implements secure storage, use, and destruction of key components generated during the collaborative signature process and user critical data.
7. SSL VPN Encryption Server.The server is based on the server protocol functions specified in the “SSL VPN Technical Specification”, providing SSL access capabilities by interacting with the client through the SSL protocol to establish a secure connection. Through the handshake protocol, it sends identity information in the form of a digital certificate for client verification, supporting more secure connection methods by sending certificate requests to the client to obtain and verify the client’s digital certificate, ensuring the authenticity of the network data transmission. It negotiates the session key for the connection, and after the SSL handshake is completed, it encrypts the application data for transmission, ensuring the integrity and confidentiality of the network data transmission.
The SSL access gateway collaborative signature module provides server-side collaborative signature functionality, completing the generation of SM2 key components, signing, and decryption operations in collaboration with the client collaborative signature module; the SSL access gateway hardware interaction module provides hardware device access functionality, ensuring key security and improving the performance of cryptographic algorithm operations; the SSL access gateway KMS (Key Management System) interaction module provides access to KMS, connecting with the key management system to provide lifecycle management of keys generated by the SSL access gateway and collaborative signature server.
The commercial cryptography application system uses standard API (Application Programming Interface) function calls to use the cryptographic services provided by the password card. The API interface is transparent to upper-level applications, allowing quick use of the security functions provided by the password card. Functions include key generation and management, data encryption and decryption, digital envelopes, digital signatures, physical random number generation, key backup and recovery, etc.
8. SSL Protocol Working Method.During SSL data encryption communication, cryptographic protocols including identity verification, key negotiation, and communication data encryption are involved. Both parties use digital certificates to verify each other’s identity, ensuring the authenticity of the entity’s identity during communication. During session establishment, both parties calculate session keys for encrypting data transmission. The following briefly introduces the working method of the SSL protocol.
In the SSL connection establishment process, the client sends a Client Hello message, which includes: supported protocol version, client random number, supported encryption algorithm suite (such as ECC-SM4-SM3), and supported compression algorithms.
If the requested version, cryptographic suite, or other parameters are not supported, the gateway closes the encrypted communication. The gateway sends a Server Hello message, which includes: confirmation of the encryption communication protocol version used, gateway random number, selected encryption suite, and gateway certificate. The gateway can also send a Server Key Exchange message along with the client’s certificate, defining additional parameters according to the protocol. The gateway may also verify the client based on the usage scenario to ensure that data is sent to a secure and legitimate client, issuing a Certificate Request message to require the client to send a certificate for client legitimacy verification.
The client verifies the gateway certificate based on the received response; if it does not match, it closes the encrypted channel. It sends its own digital certificate based on the server’s request. The client uses an asymmetric encryption algorithm to generate a pre-master key, encrypting it with the public key data in the gateway’s certificate and sending a Client Key Exchange message. When sending the certificate verification message, the client signs all handshake-related messages from the start of the Client Hello message to this message (excluding this message) using the signing key (the encrypted certificate must be included in the signature calculation). The scheme uses collaborative signature technology to interact with the gateway, ultimately merging to generate signature data on the client. Using the client, the random number generated by the gateway, and the pre-master key, the current session master key is generated, and the client updates the master key. The client sends a Change Cipher Spec to inform the gateway that it has switched to the previously negotiated encryption suite state, preparing to use the negotiated encryption suite to encrypt data and transmit it, using the updated master key to encrypt the Finished message.
The gateway can verify the client’s certificate; if it does not match, it closes the encrypted channel. Using the received client’s pre-master key and both parties’ random numbers, the current session master key is generated, and a Change Cipher Spec is sent to inform the client that the SSL connection is ready, using the updated master key to encrypt the Finished message.
For application data transmission, the generated master key is used to encrypt the data transmission, and a MAC (physical address) value of the encrypted data is attached. The other party can use the MAC value to verify the security of the currently transmitted encrypted data.
In the collaborative signature SSL connection process, the client establishes a unidirectional SSL channel with the SSL access gateway, obtaining random number data generated by the hardware cryptographic device in the SSL access gateway. The 256-bit random number generated by the noise source chip in the gateway password card is sent to the client, which collects the physical random sequences from the terminal as random sources to generate the client random number, which is used for generating the client key component in the client cryptographic module (see Figure 2).
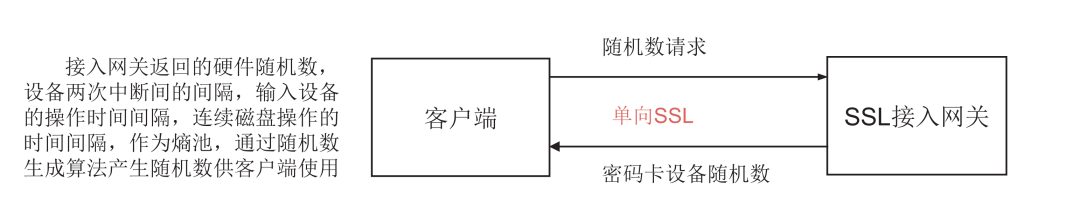
Figure 2 Generating Random Data
The client sends an identity verification request through the unidirectional SSL channel, and upon successful verification, collaborates with the SSL access gateway to generate SM2 private key components and public key information (see Figure 3).

Figure 3 Identity Verification Request
The client establishes a bidirectional SSL channel with the SSL access gateway. During the connection establishment process, both the client and gateway verify each other’s identity, including the client’s signing operation (when the client sends the certificate verification message, it uses the client key component to interact with the SSL access gateway to generate signature data), completing the establishment of the SSL channel (see Figure 4).
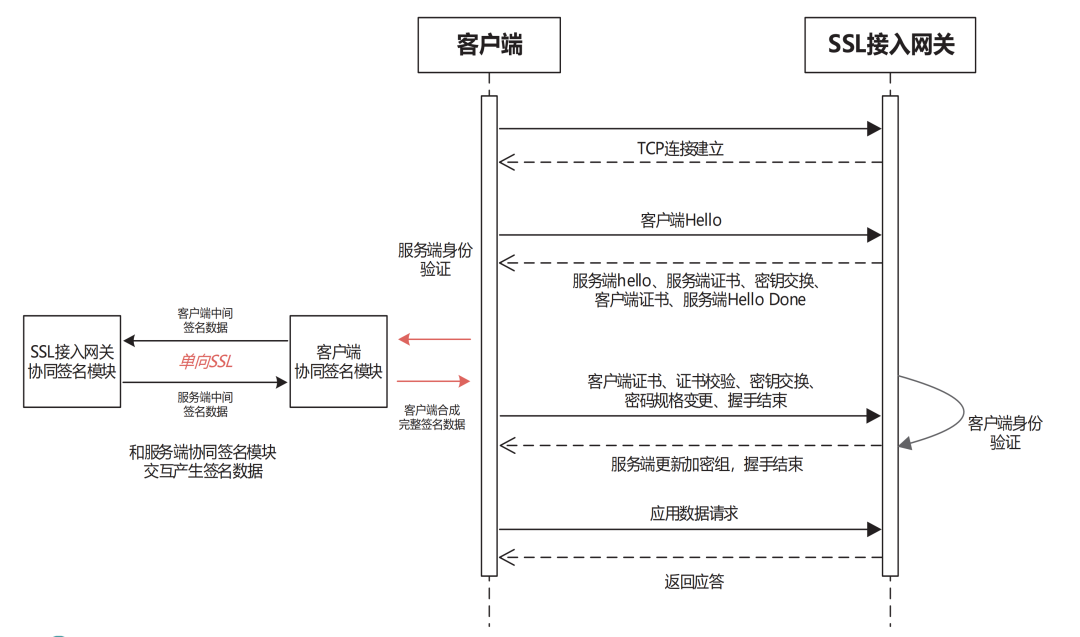
Figure 4 Client and SSL Channel
Data Encryption Security Testing and Validation
For the server-side application, the high bandwidth and larger operand instruction set support brought by the 64-bit system architecture can provide better execution efficiency in cryptographic operations. For the deployment plan, hardware environment selection is performed, adopting ARM architecture for hardware devices and the Galaxy Kirin Advanced Server Operating System V10 for the operating system.
1. Algorithm Performance Testing.Data encryption security testing mainly includes environmental adaptation testing and cryptographic algorithm performance testing. Through a large number of cryptographic operation processes, the execution efficiency and performance of cryptographic algorithms are statistically analyzed, with data length at 131072 bytes. Performance testing includes block cipher algorithms (SM4), asymmetric cipher algorithms (SM2), and hash algorithms (SM3), as shown in Tables 1-3.
Table 1 Block Cipher Algorithm Performance Testing
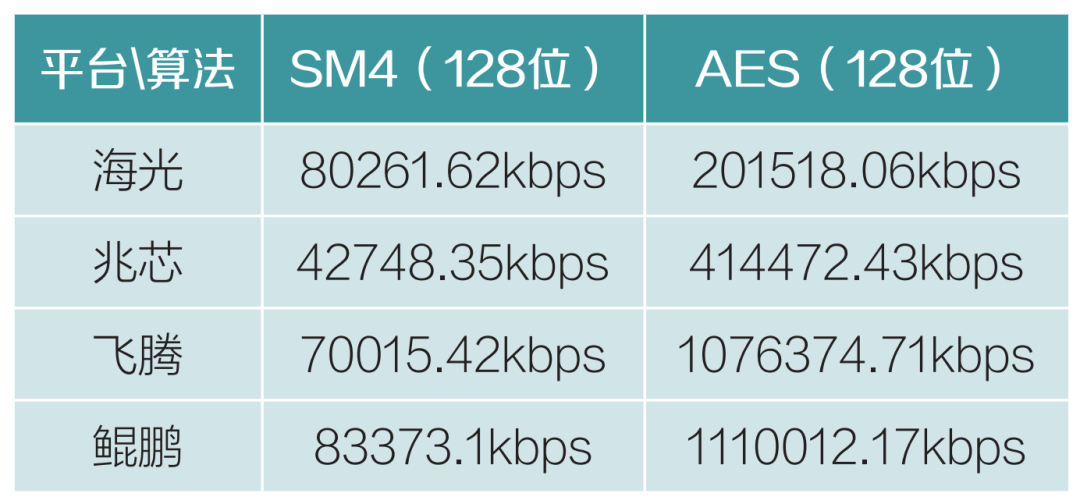
Table 2 Asymmetric Cipher Algorithm Performance Testing
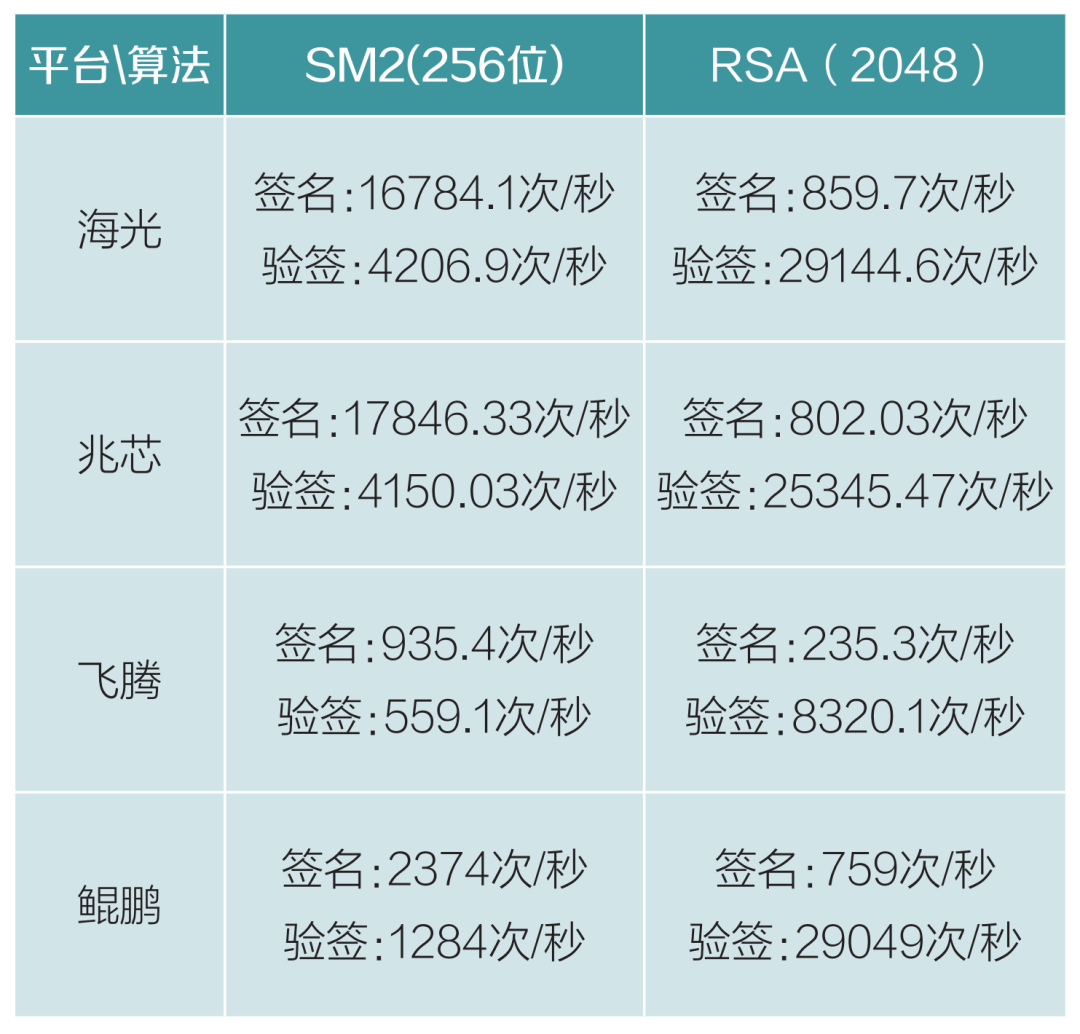
Table 3 Hash Algorithm Performance Testing
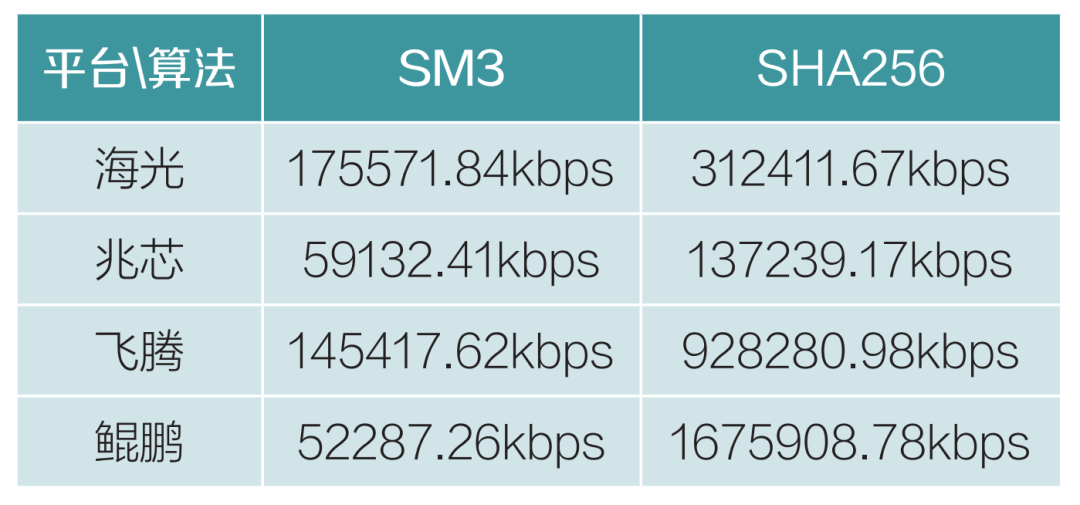
Compared to previous international algorithms, commercial cryptography algorithms have seen a decrease in performance, but the new algorithms have shown stable performance overall in testing. Different devices and architecture platforms exhibit some differences in performance indicators. The Haiguang chip generally outperforms other chips, and this chip is selected for compatibility testing during the algorithm upgrade.
2. SSL Access Gateway Performance Testing.High concurrency system application scenarios are simulated to reflect the high concurrency support capability of the application system. By comparing the test results, a corresponding network capability assessment can be made for the system application.
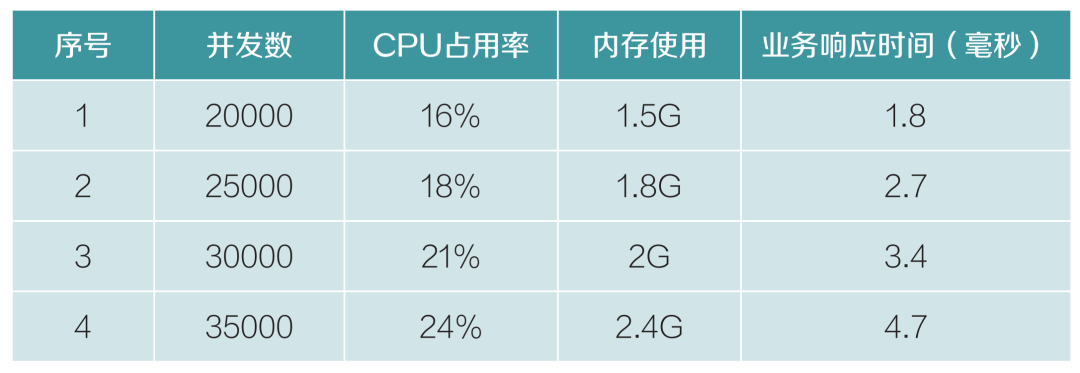
The test environment uses trading ports, creating trading connections to conduct trading business, simulating users online, with a request interval set at 15 seconds, measuring the online concurrent processing capability of the gateway. The cryptographic functionality used in establishing SSL connections is processed by cryptographic devices, using Sanwei Xin’an hardware cryptographic card (SJK1727), with five pressure testing tools testing a single SSL access gateway. The test data is shown in Table 4. Under high concurrency, CPU usage is sufficient, memory usage is low, and business response time is low, meeting customer transaction day usage.
Table 4 Gateway Performance Testing
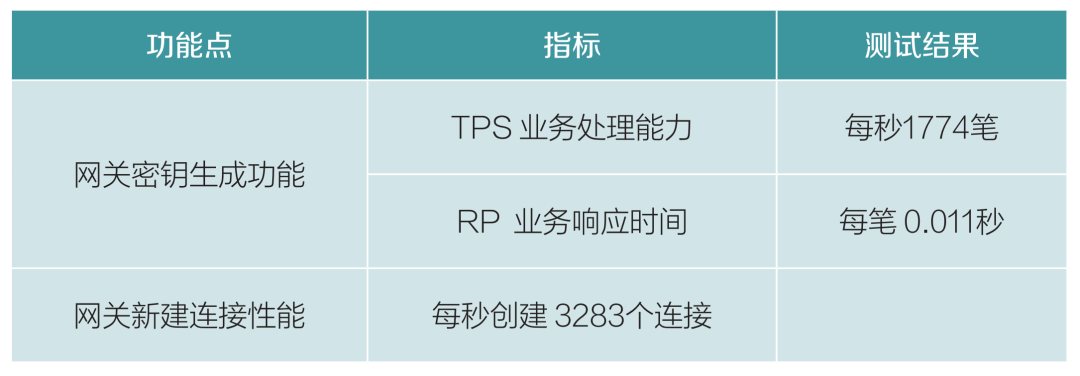
3. Collaborative Signature Performance Testing.In the cryptographic application scheme, collaborative signature technology is adopted. Compared to conventional cryptographic algorithms, it has higher complexity, making it an important processing node in the application phase, requiring higher execution efficiency and computational performance. For this scenario, collaborative signature performance testing is designed to evaluate and validate the processing performance of the collaborative signature algorithm at the access gateway.
The collaborative cryptographic functionality relies on cryptographic device processing, using Sanwei Xin’an hardware cryptographic card (SJK1727), with five pressure testing tools testing a single SSL access gateway. The test data is shown in Table 5.
Table 5 Collaborative Signature Performance Testing
Summary and Outlook
Various commercial cryptography applications used in the securities and futures industry, such as data encryption and decryption, digital signature verification, etc., generally adopt foreign commercial cryptography technologies. All security facilities and products supporting such applications are built on foreign basic algorithms and cryptographic technologies, posing a significant challenge to the safe and stable development of the entire industry. Financial data security is an important part of national information security. The application of cryptographic security reinforcement in the online trading system adopts a series of cryptographic algorithm standards formulated by the National Cryptography Administration, ensuring the security, reliability, and scientific norms of cryptography.
(This article was published in the May 2024 issue of “Financial Electronics”)









New Media Center
Director / Kuang Yuan
Editors / Yao Liangyu, Fu Tiantian, Zhang Jun, Tai Siqi
