Note:
1. Thank you all for your attention, continuing to summarize last week’s wonderful content.
2. Last week, a video was shared:
BSP Video Tutorial Episode 21: Easily Achieve Variable Length Serial Port DMA Send/Receive with One Click, Supporting Bare Metal and RTOS, Including Two Approaches: MDK and IAR, More Convenient Than CubeMX
1 The Ultimate Security-Critical C Code Rules Practical Manual, No Exceptions
Previous C-related books were either thick with hundreds or thousands of pages or filled with obscure C practices, leaving you only able to use if-else statements after learning, and forgetting the advanced techniques in the book, which were not very practical and optional.
This time, I share a security-critical C code manual that discards the traditional writing style of C books, directly providing rules, recommended methods, reference materials, and standard code, along with non-standard code examples, greatly facilitating everyone’s reference. Cover:

Table of Contents: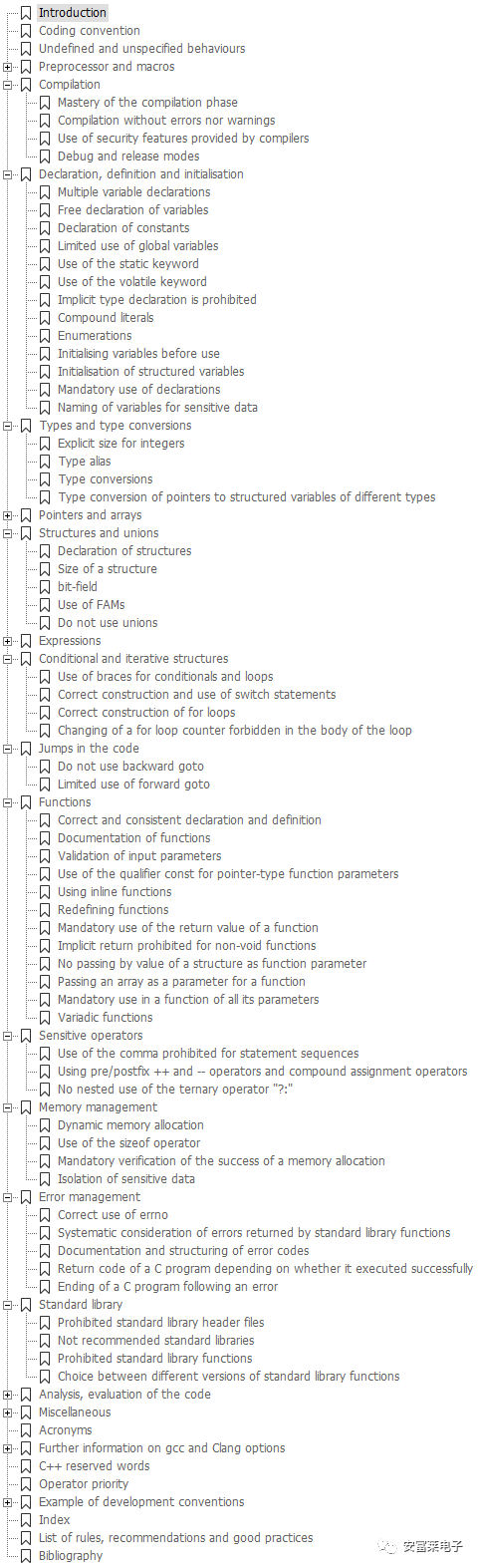 Effect Demonstration, Although in English, It Is Very Suitable for Beginners to Reference:
Effect Demonstration, Although in English, It Is Very Suitable for Beginners to Reference:
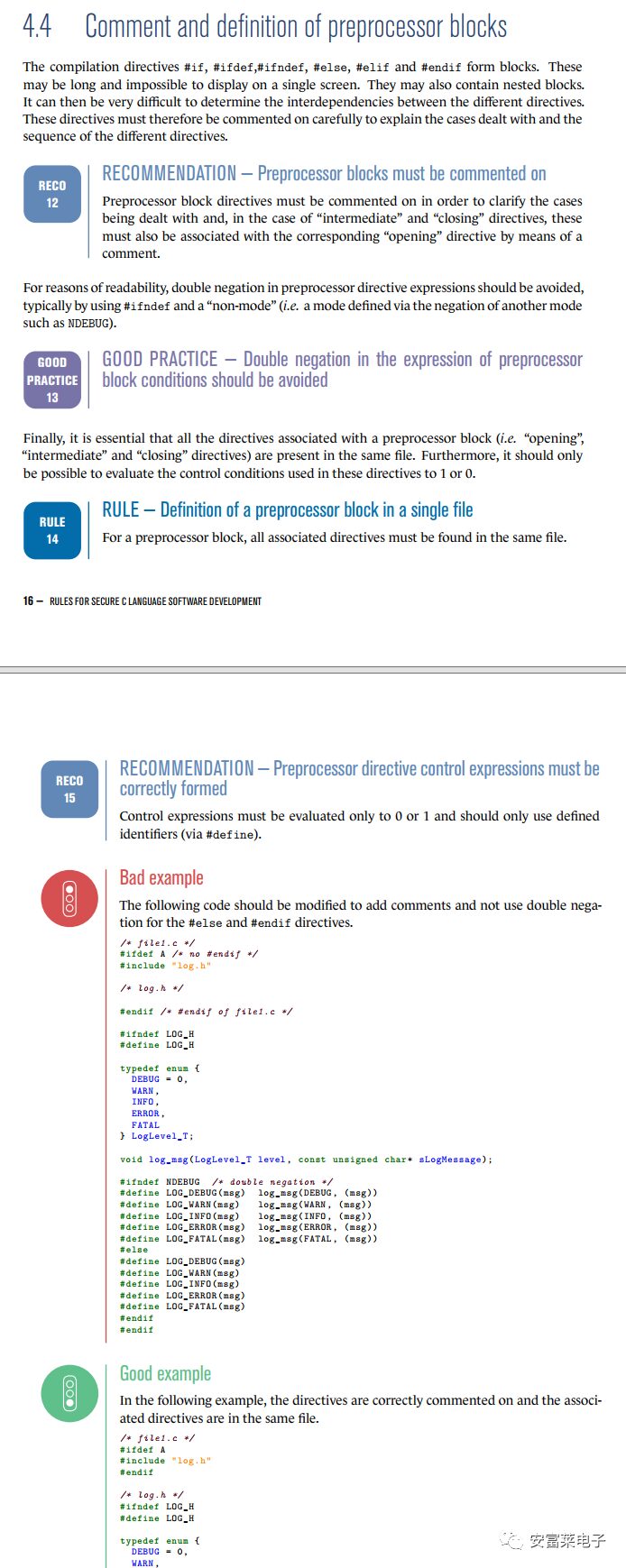
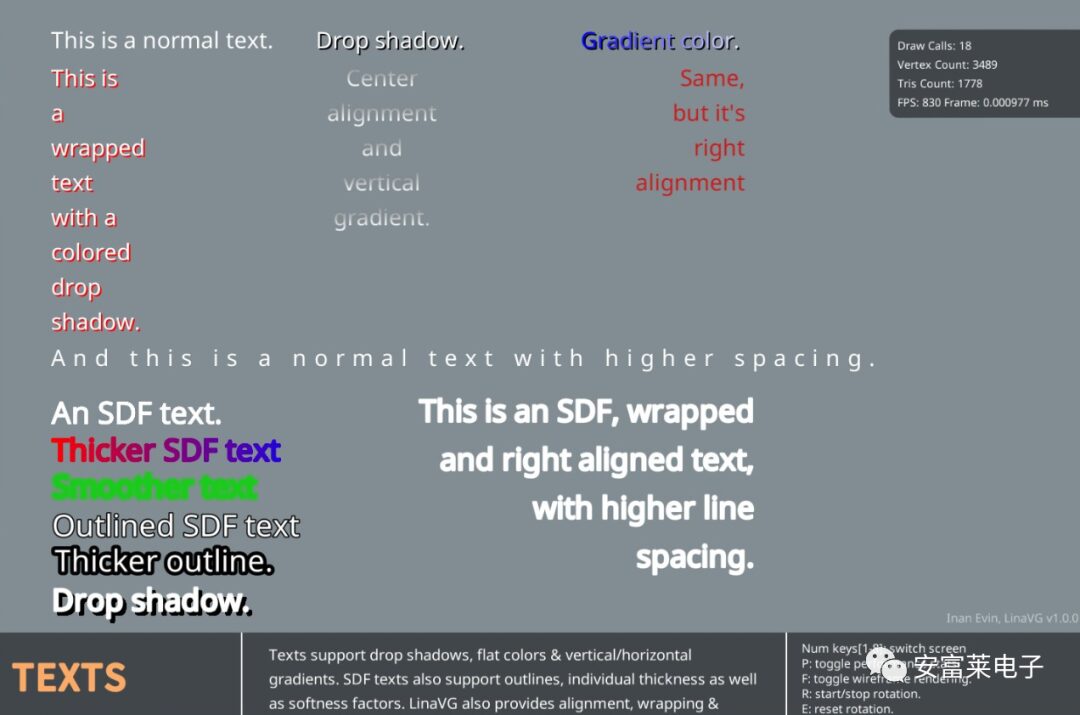
2 Open Source 2D Vector Graphics Rendering Library LinaVG
It can render anti-aliased shapes, supports gradient colors, lines, outlines, SDF text, etc.
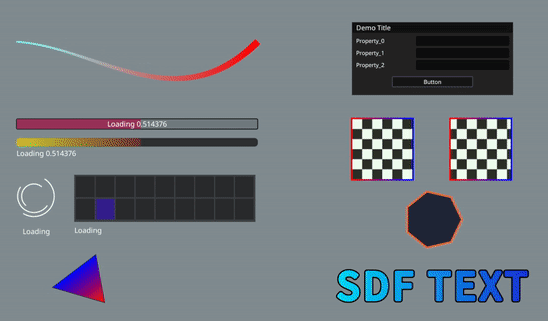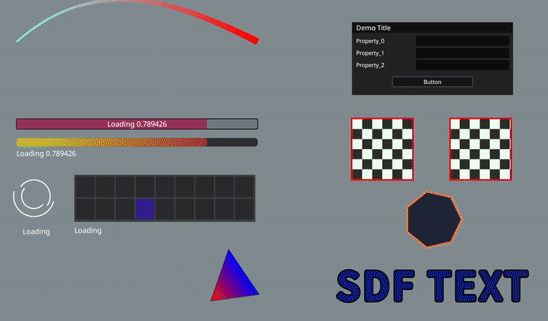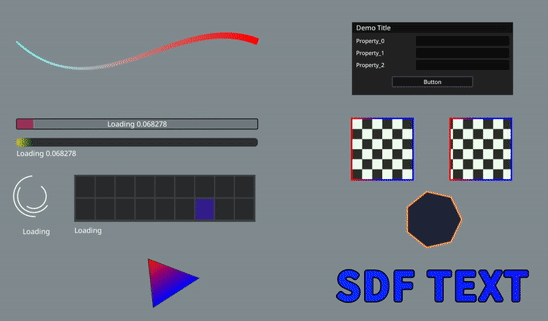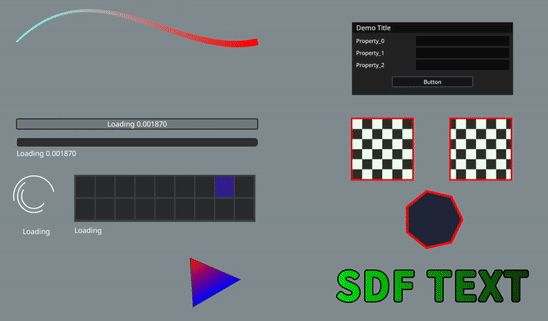
Other Screenshot Effects: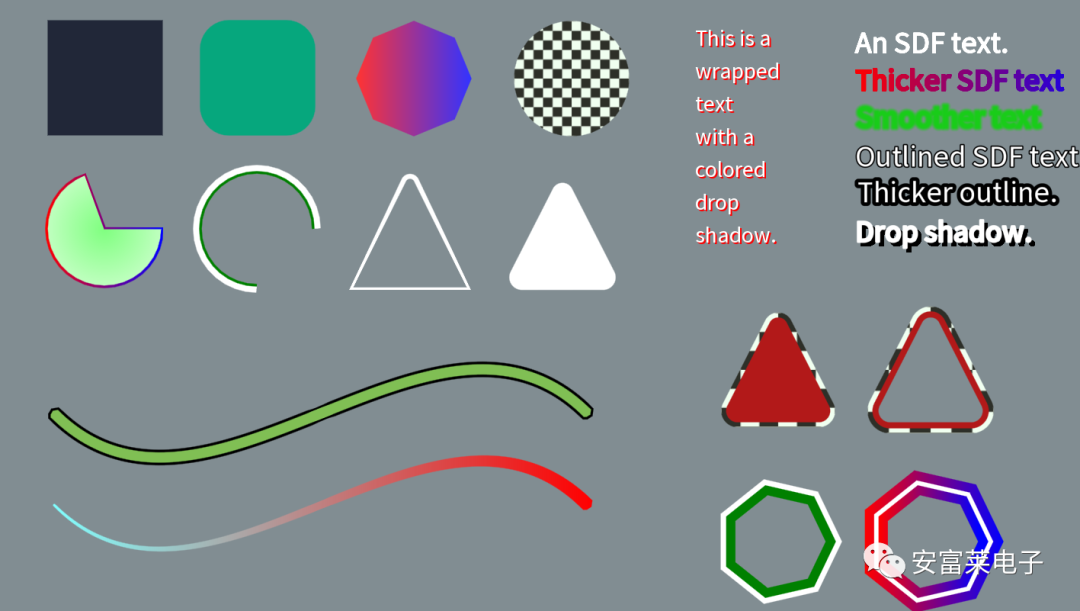
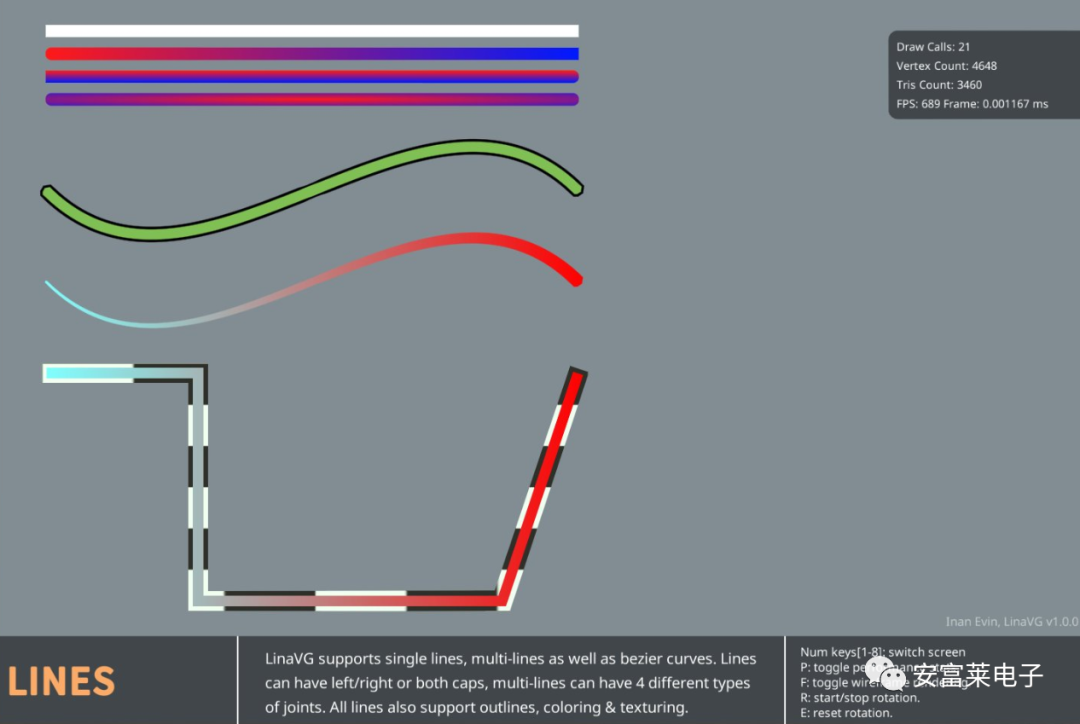
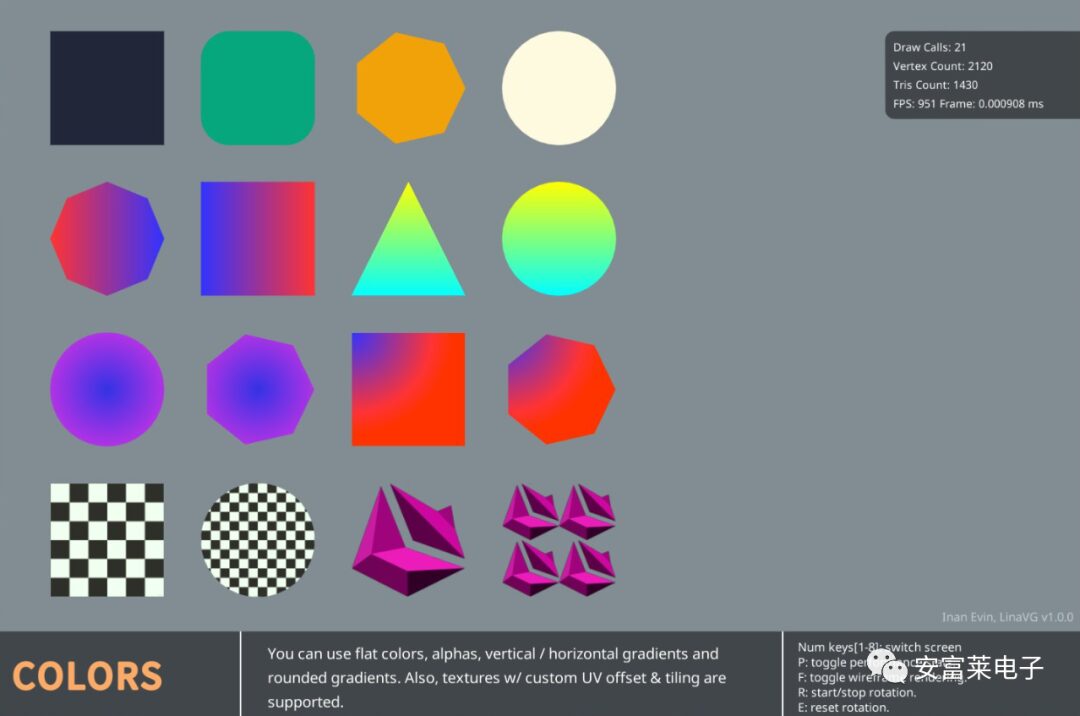
 Features:
Features: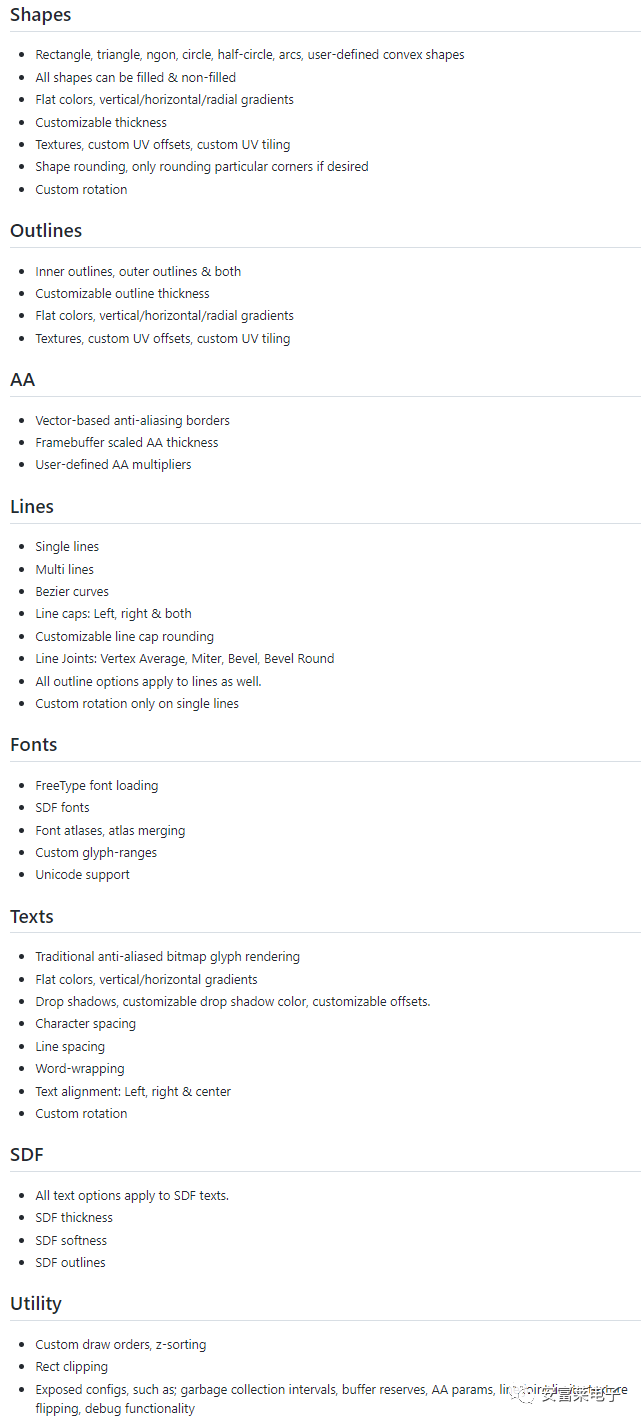
3 A Bit of a Dirty Name, But It’s Serious Programming: JSFuck
JSFuck is an esoteric and educational programming style based on JavaScript’s atomic parts. It uses only six different characters to write and execute code. It does not rely on the browser, so users can even run it on Node.js.For example, the following code executes alert(1):
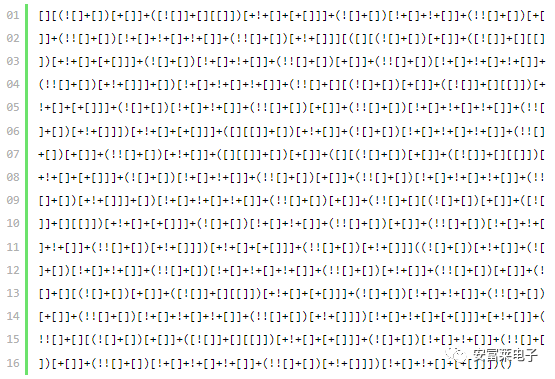
Basic Syntax: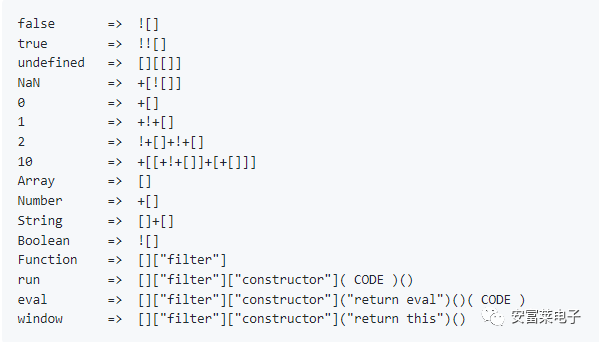
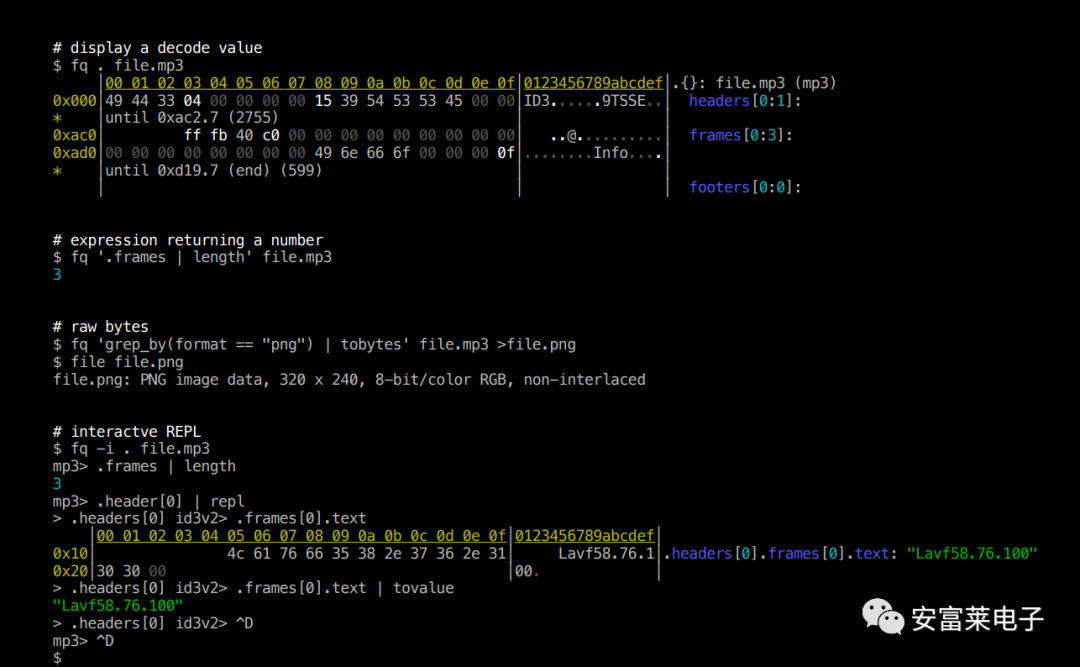
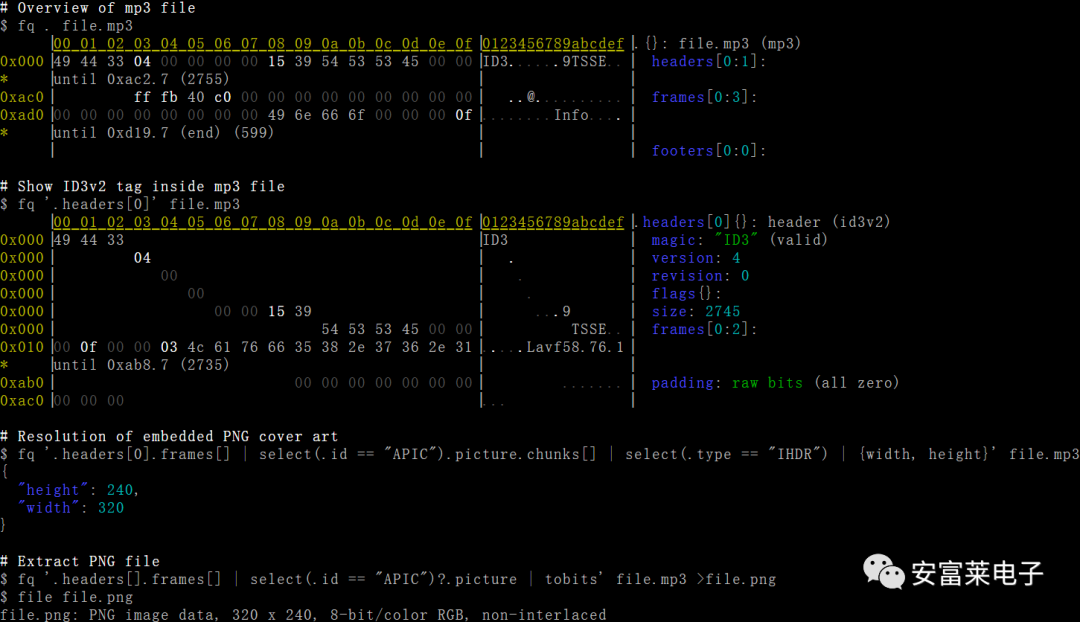
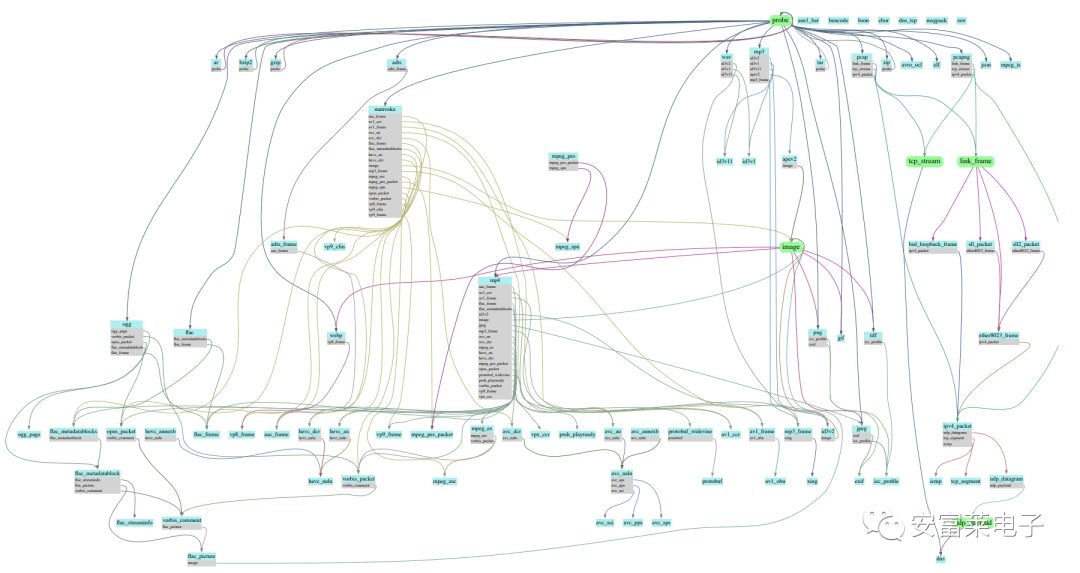
4 A Small Software Supporting Hundreds of File Formats: FQ
It was originally designed for querying, checking, and debugging multimedia formats like mp4, flac, mp3, jpeg, and has now expanded to support viewing hundreds of formats.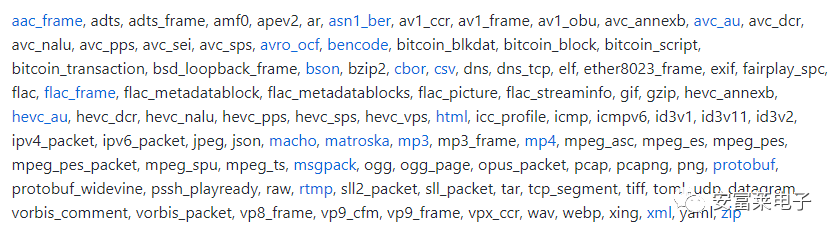 On Windows, it can be easily installed using the scoop command:
On Windows, it can be easily installed using the scoop command: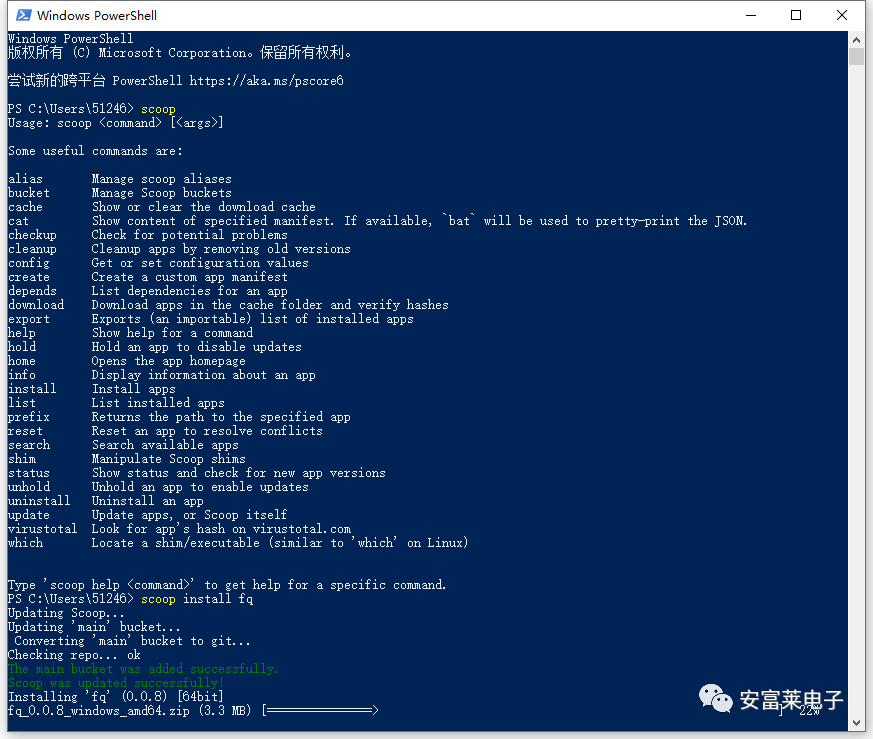
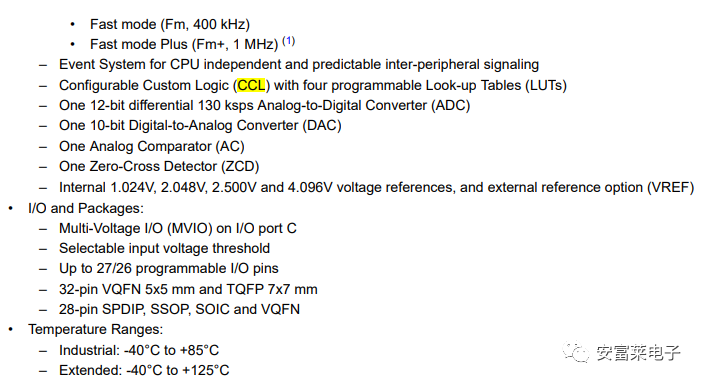
5 Microchip Launches New AVR DD Series Products
Who would have thought that AVR is still releasing new products.
Specifications:
 Block Diagram:
Block Diagram: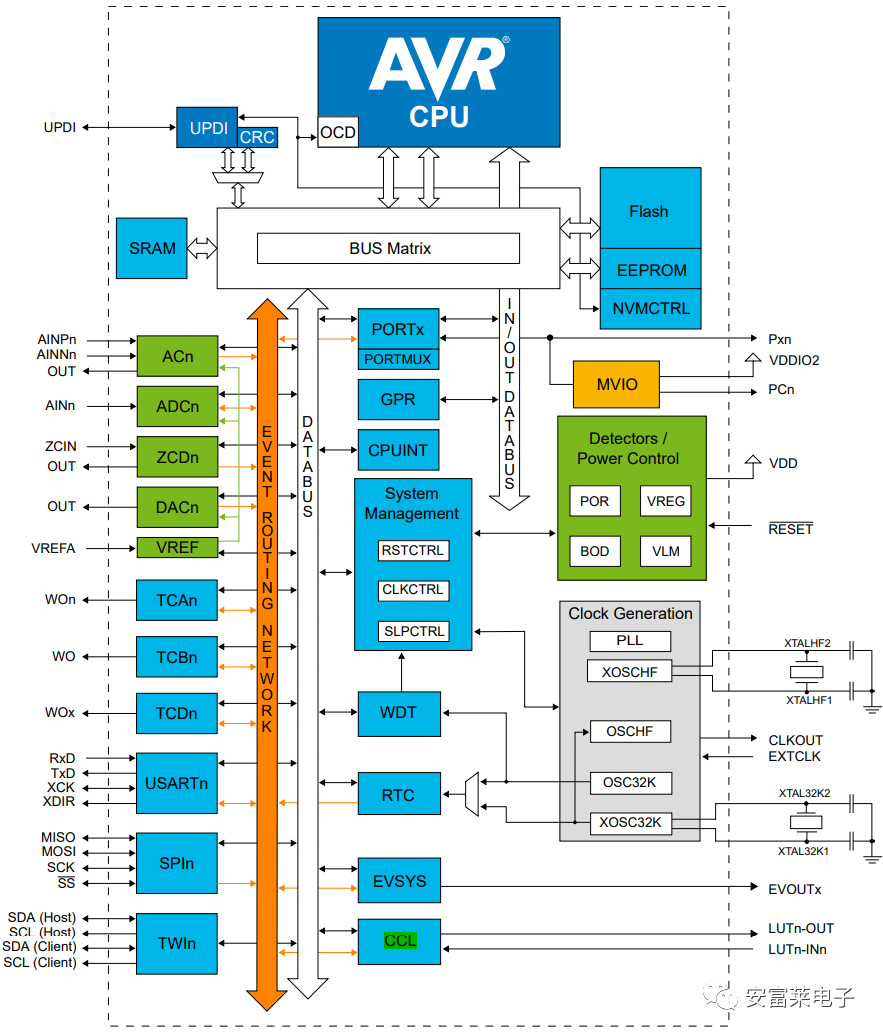 Kit:
Kit: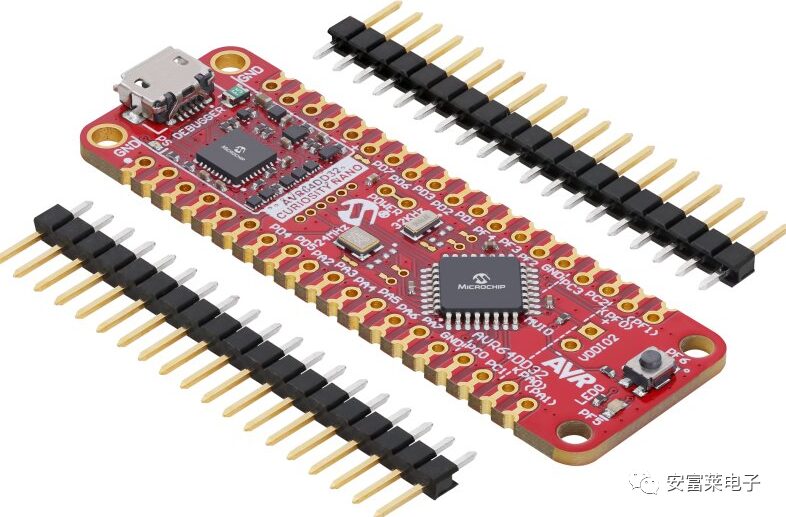
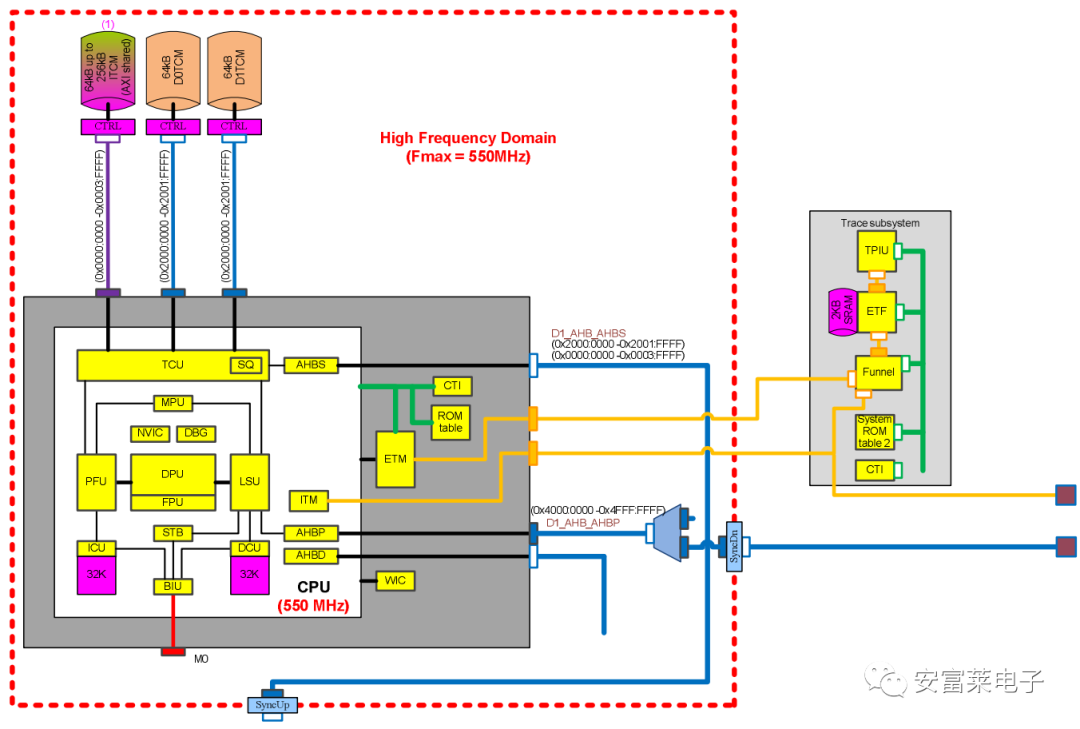
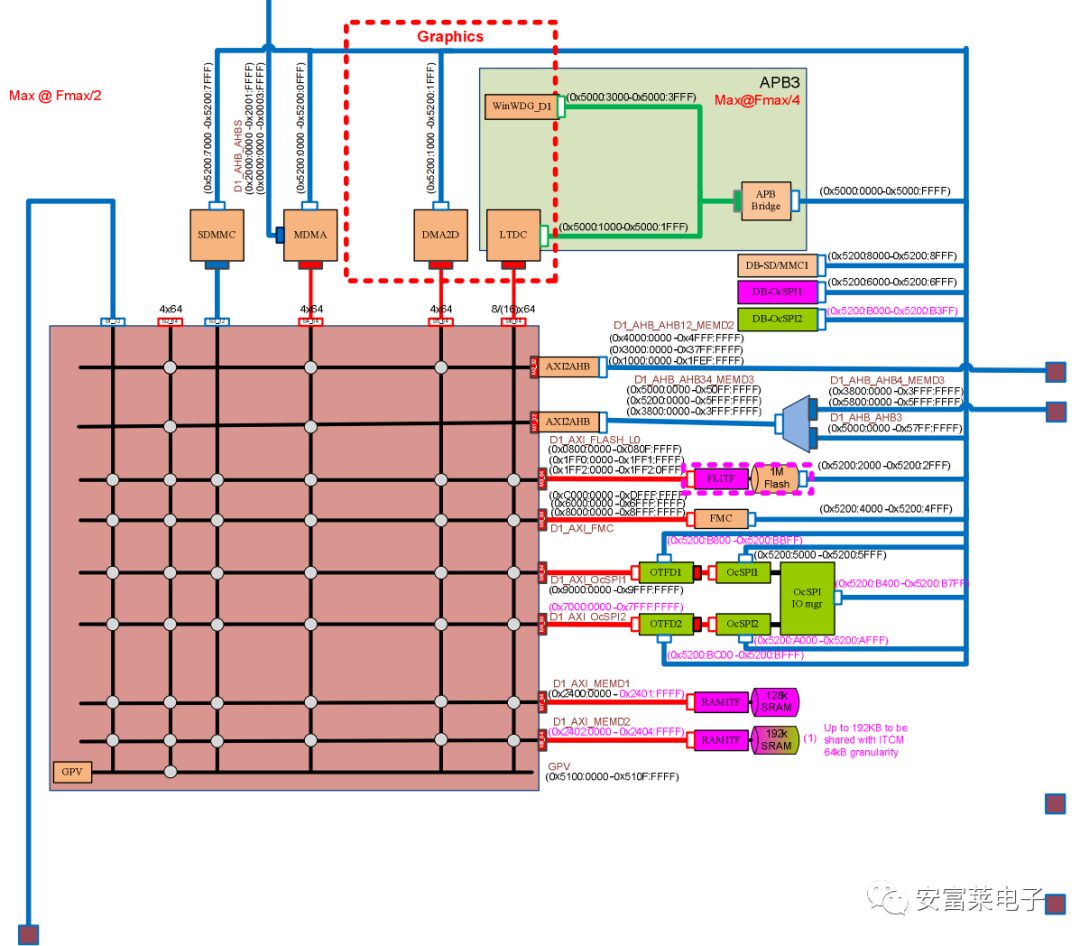
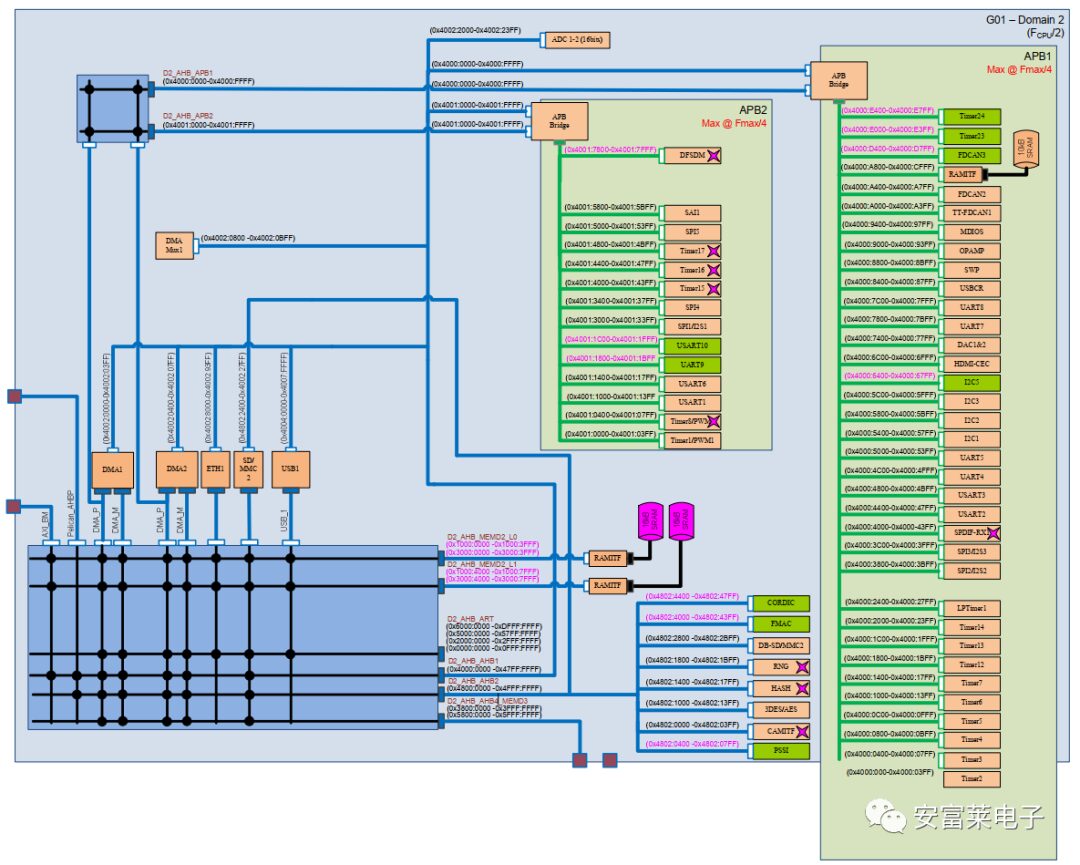
6 New System Block Diagram for STM32H7
More detailed than the previous system block diagram, it’s beautifully drawn.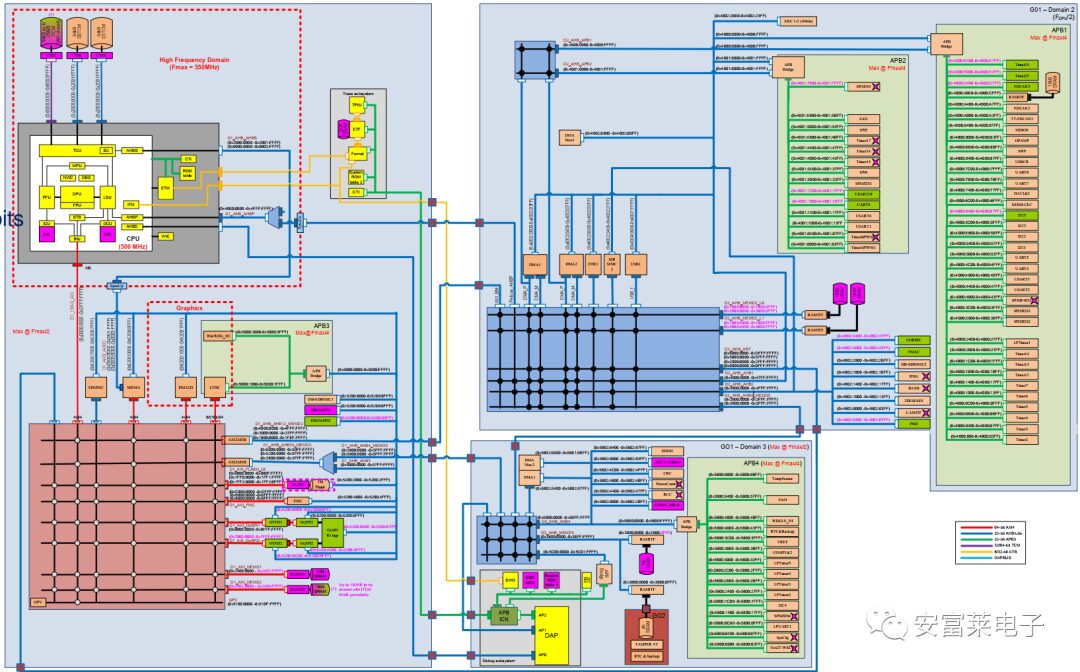
 Nordic’s Wireless Communication Magazine has published its second issue of 2022, a quarterly publication that has been released for 16 consecutive years. Students interested in Zigbee, Bluetooth, LoRa, Thread, WIFI, NBIOT, etc. can take a look; the magazine is made with care, and the electronic version can be downloaded for free.
List of Quarterly Issues Over the Past Decade:
Nordic’s Wireless Communication Magazine has published its second issue of 2022, a quarterly publication that has been released for 16 consecutive years. Students interested in Zigbee, Bluetooth, LoRa, Thread, WIFI, NBIOT, etc. can take a look; the magazine is made with care, and the electronic version can be downloaded for free.
List of Quarterly Issues Over the Past Decade: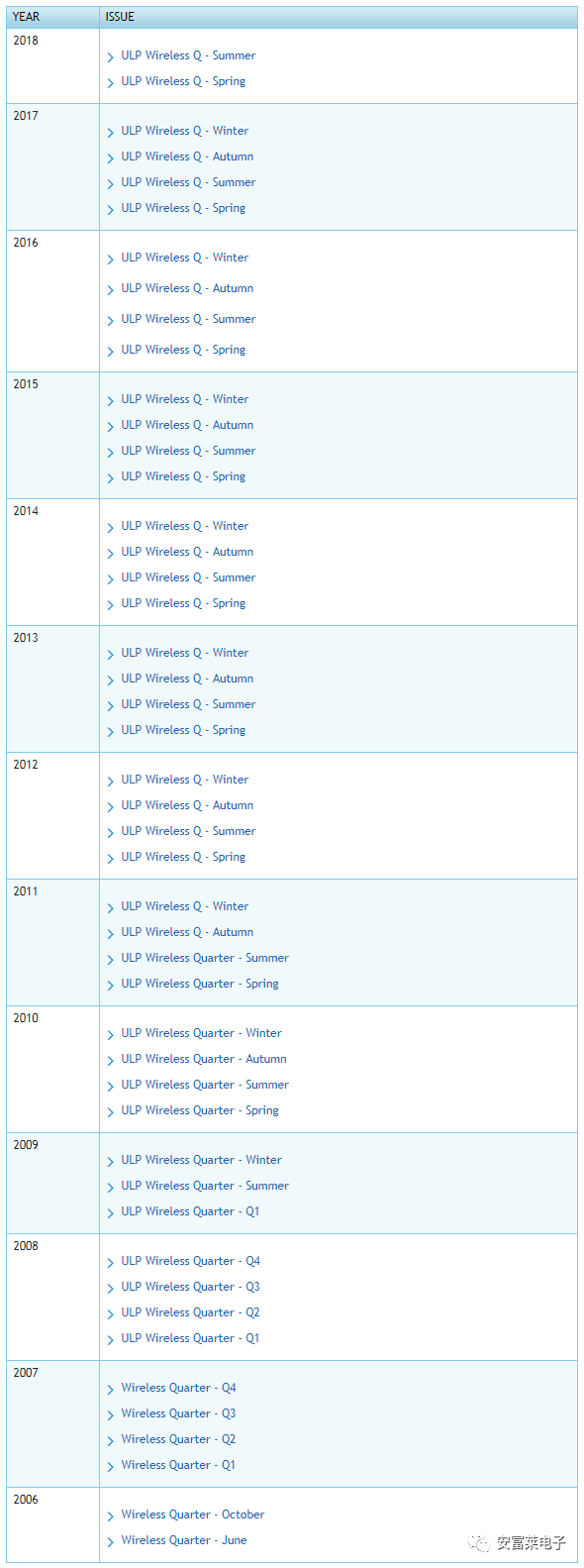 Here are a few effects:
Here are a few effects:

8 Open Source C Library and Data Structure Package SC
Features: High performance, minimal code requirements, each function has its own C and H files, making it easy to port and use individually. 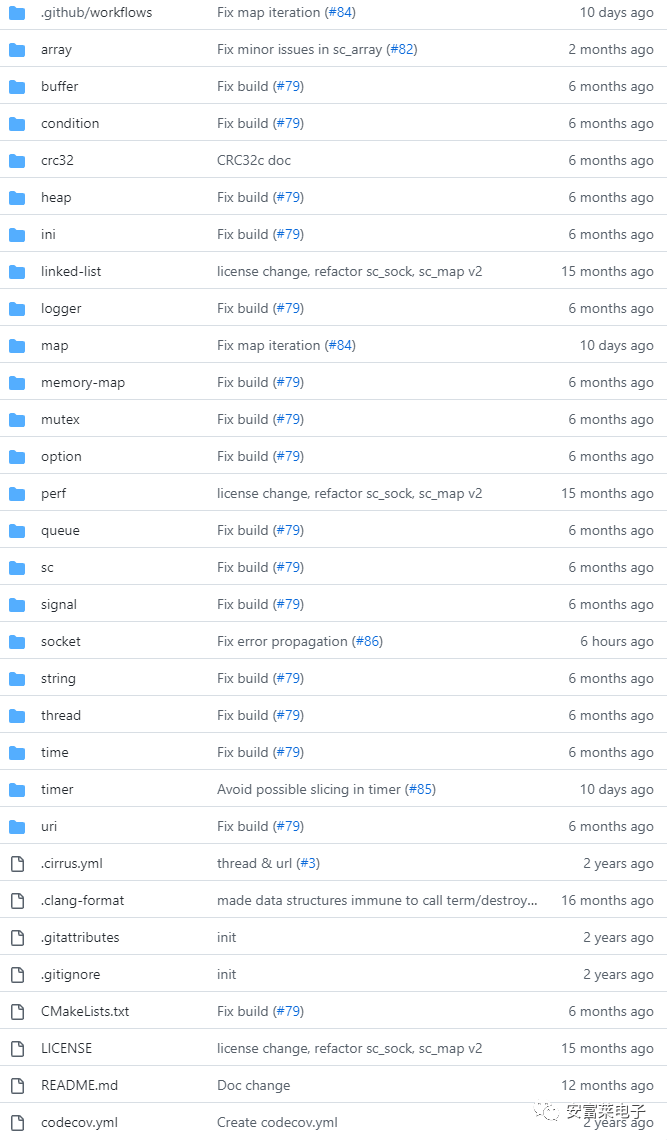 What’s more, each file contains corresponding usage examples, which is very convenient. For example, using lists:
What’s more, each file contains corresponding usage examples, which is very convenient. For example, using lists: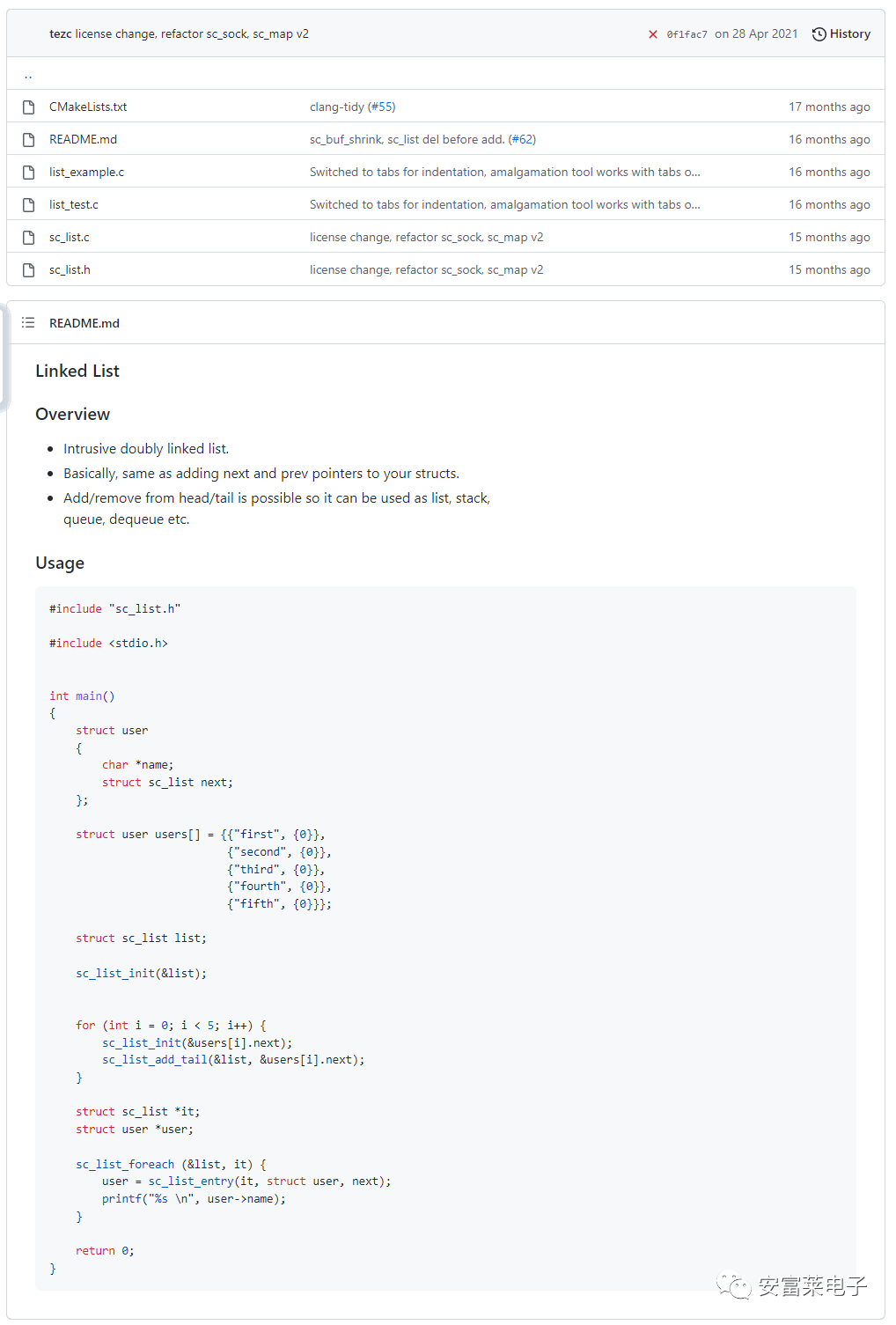 (1) ST Releases Motor Reference Design Suitable for Power Up to 250W for Industrial Compressors and Home Appliances. Each design’s core is the STSPIN32F0601Q, which integrates a motor controller and a three-phase inverter using SIP packaging technology.
(1) ST Releases Motor Reference Design Suitable for Power Up to 250W for Industrial Compressors and Home Appliances. Each design’s core is the STSPIN32F0601Q, which integrates a motor controller and a three-phase inverter using SIP packaging technology.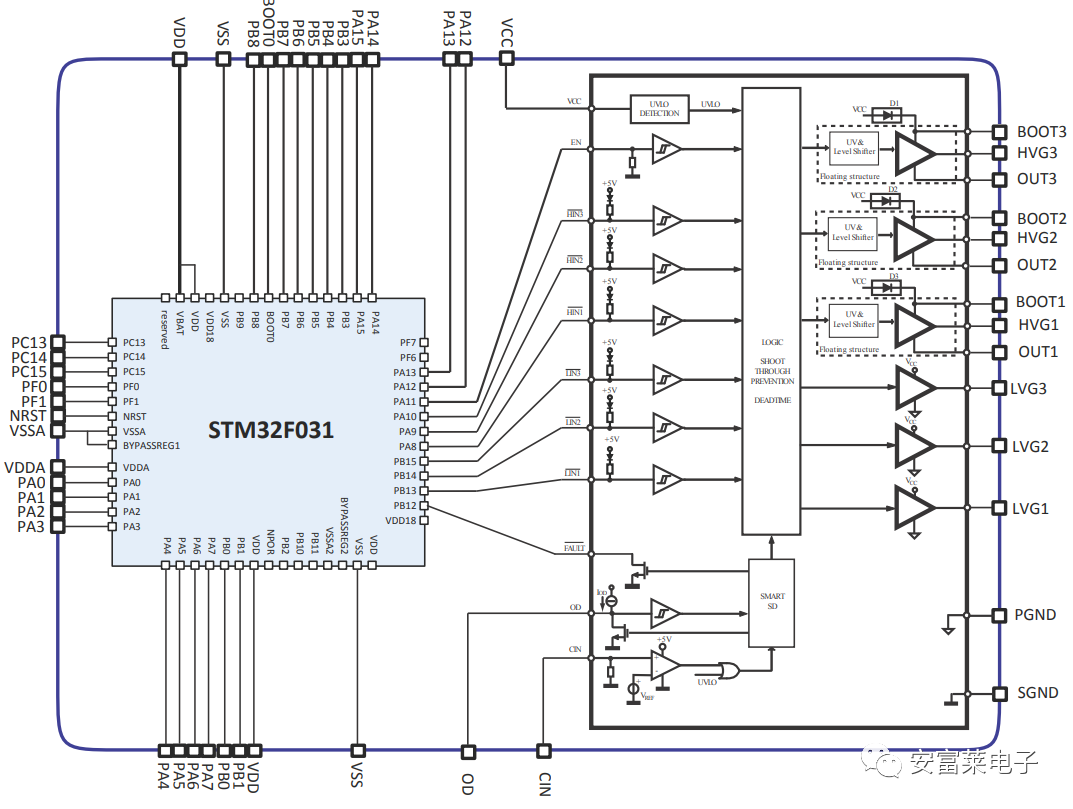 Kit:
Kit: (2) Volkswagen’s New Independent Software Division CARIAD Will Collaborate with ST to Develop SoCs for the Automaker’s Future Software-Defined Vehicles. The core idea is simple: complete control over automotive hardware and software, with chip manufacturing by TSMC, and in the future, only using SoCs developed in collaboration with ST and ST’s automotive-grade chips for the CARIAD regional architecture. Automotive systems will be developed based on QNX as part of the software-defined initiative.
ps: CARIAD was established in 2020. The department currently has about 5,000 engineers and developers dedicated to developing a unified software platform and operating system for all Volkswagen Group brand vehicles.
(2) Volkswagen’s New Independent Software Division CARIAD Will Collaborate with ST to Develop SoCs for the Automaker’s Future Software-Defined Vehicles. The core idea is simple: complete control over automotive hardware and software, with chip manufacturing by TSMC, and in the future, only using SoCs developed in collaboration with ST and ST’s automotive-grade chips for the CARIAD regional architecture. Automotive systems will be developed based on QNX as part of the software-defined initiative.
ps: CARIAD was established in 2020. The department currently has about 5,000 engineers and developers dedicated to developing a unified software platform and operating system for all Volkswagen Group brand vehicles.
10 ARM Releases PAF Physical Attack Framework
PAF is a library of tools designed to understand physical attacks, such as fault injection and side-channel attacks, and aims to help strengthen codebases against these threats. 
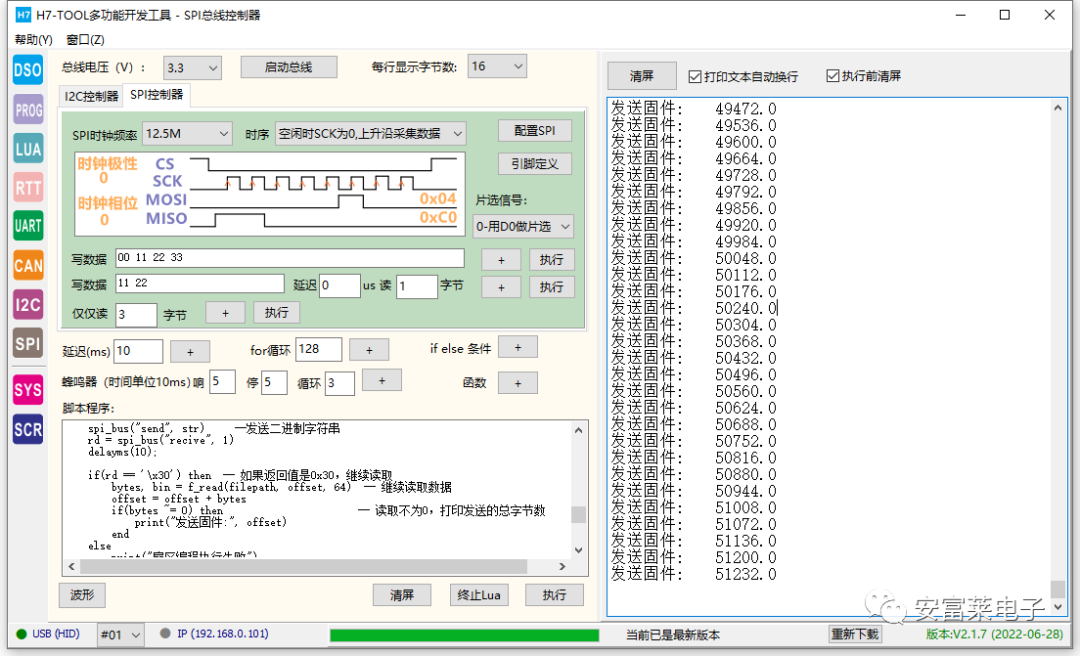
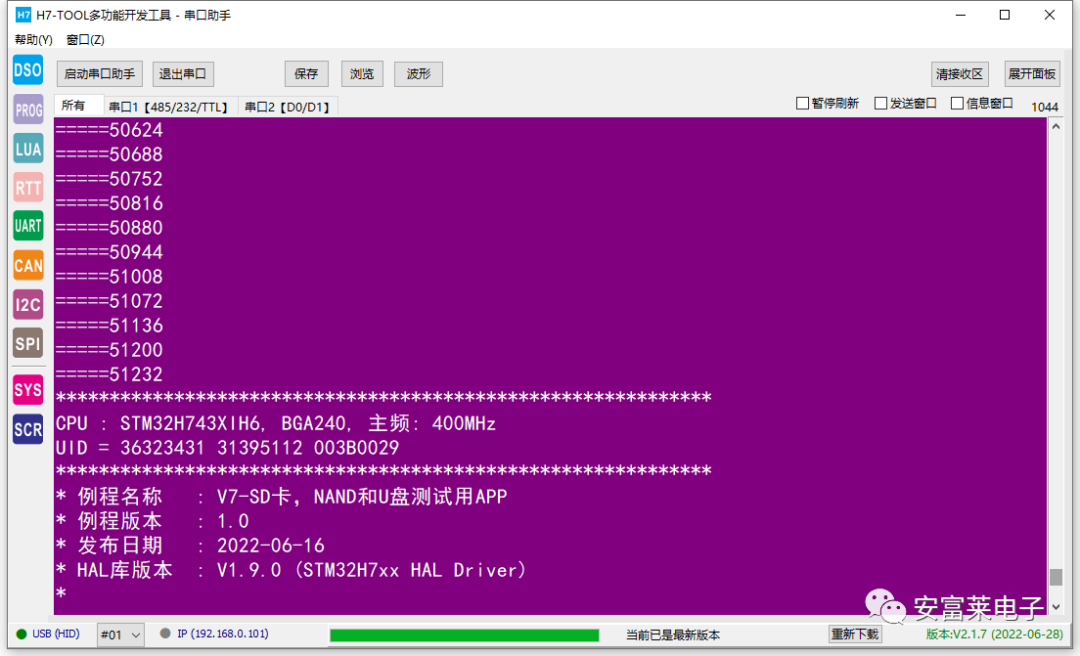
11 H7-TOOL Progress This Week
The H7-TOOL’s SPI interface offline programming has also been implemented. Through a Lua script, we can easily perform firmware programming via the SPI interface online or run the Lua script offline for programming. So far, we have officially gathered the SPI, I2C, CANFD, and serial interface methods for offline programming with H7-TOOL. If I have time this week, I will record a video tutorial on bootloader using these interface methods.
Animated GIF:
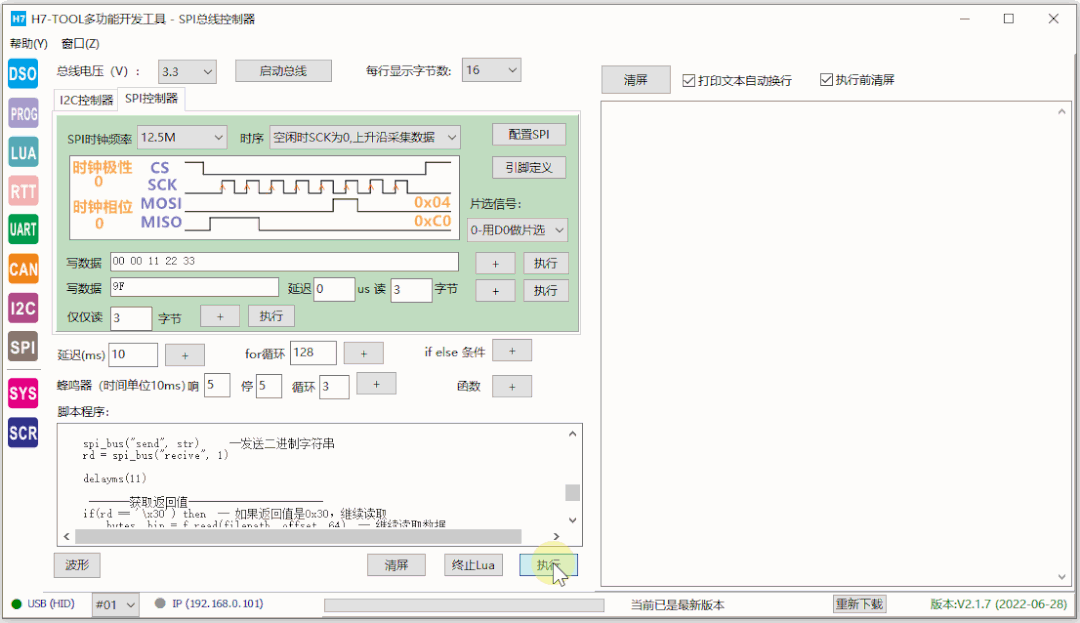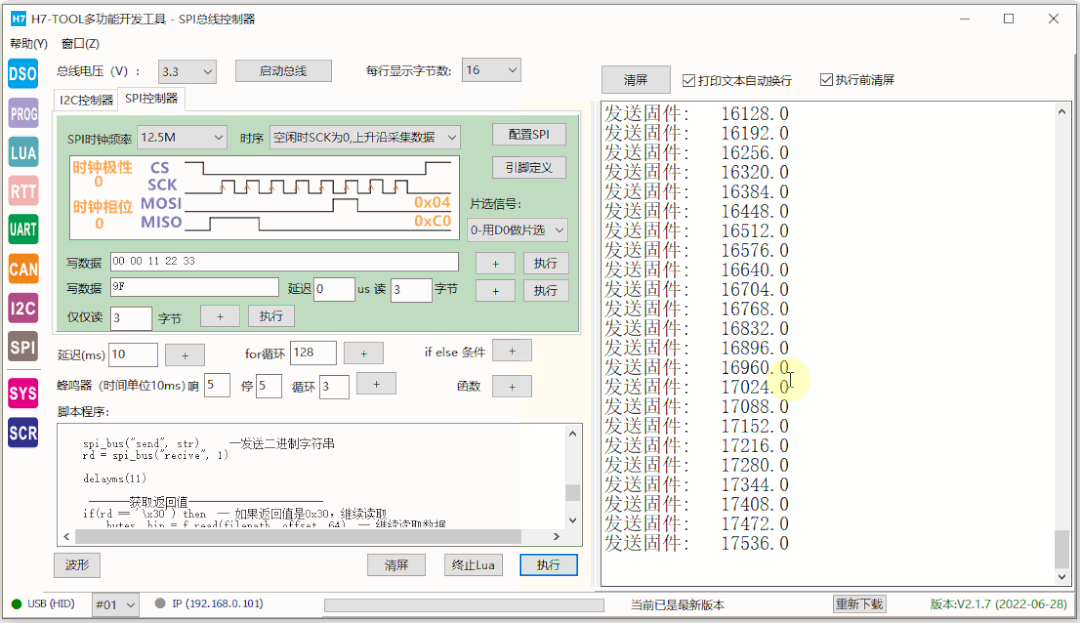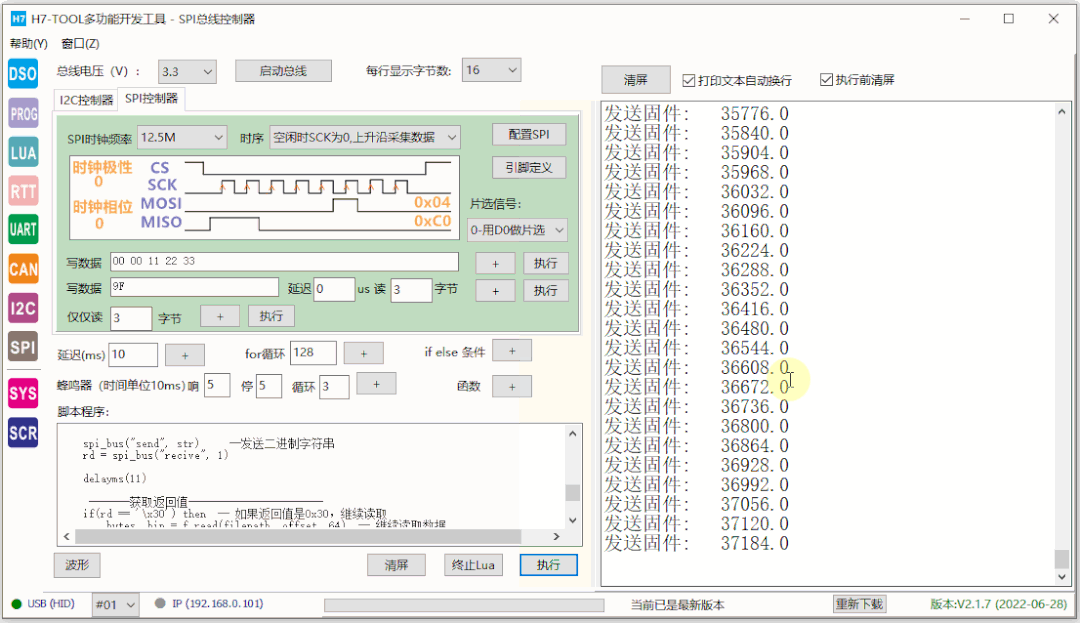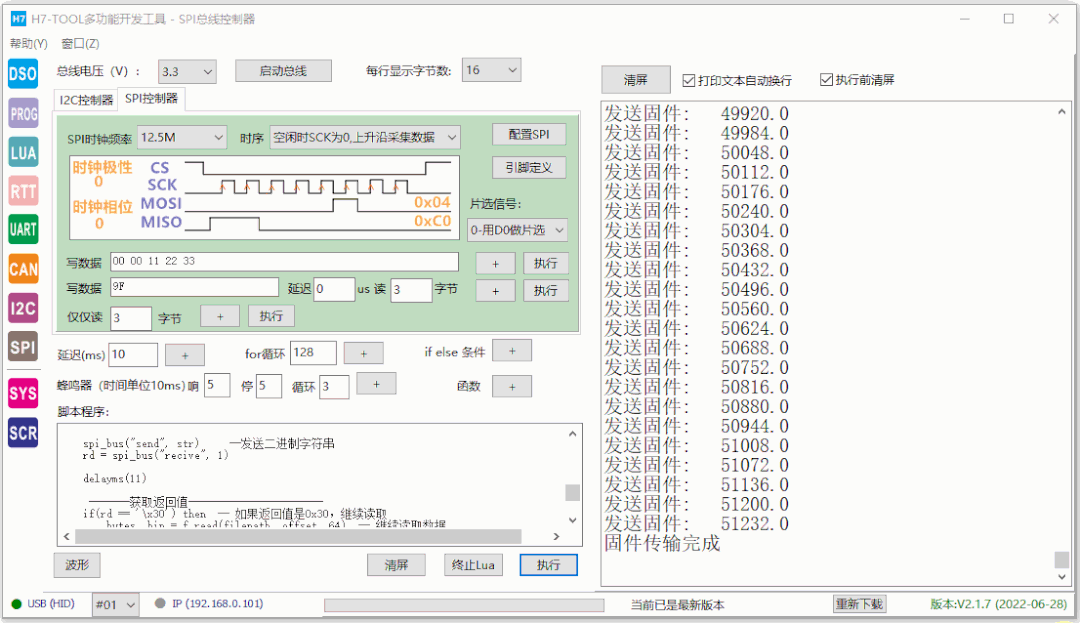
Screenshot:
For all news source links and attachments, click to read the original text at the end