National encryption refers to the domestic encryption algorithms recognized by the National Cryptography Administration. The main algorithms include SM1, SM2, SM3, SM4, and the latest SM9. These algorithms are primarily used in domestic environments as recognized by the National Cryptography Administration.
SM2 Algorithm: The SM2 elliptic curve public key cryptography algorithm is a public key cryptographic algorithm independently designed in China. It includes the SM2-1 elliptic curve digital signature algorithm, SM2-2 elliptic curve key exchange protocol, and SM2-3 elliptic curve public key encryption algorithm, which are used for implementing digital signatures, key negotiation, and data encryption among other functions. Unlike RSA, the SM2 algorithm is based on the difficulty of the discrete logarithm problem in elliptic curve point groups. The strength of 256-bit SM2 encryption is already higher than that of 2048-bit RSA encryption.
Essentially, it is similar to the RSA algorithm, but as we all know, the RSA algorithm requires a bit length of 2048 or higher, while SM2 can achieve strong encryption strength with a shorter bit length.
SM3 Algorithm: The SM3 hashing algorithm is a cryptographic hash algorithm independently designed in China. It is suitable for generating and verifying digital signatures and message authentication codes, as well as generating random numbers in commercial cryptographic applications, meeting various cryptographic application security requirements. To ensure the security of the hashing algorithm, the length of the generated hash value should not be too short. For example, MD5 outputs a 128-bit hash value, which is too short and affects its security. The output length of the SHA-1 algorithm is 160 bits, while the output length of the SM3 algorithm is 256 bits. Therefore, the security of the SM3 algorithm is higher than that of MD5 and SHA-1.
Similar to MD5, but longer and with higher security.
SM4 Algorithm: The block cipher algorithm is a symmetric encryption algorithm independently designed in China for performing data encryption/decryption operations to ensure the confidentiality of data and information. A basic condition for ensuring the security of a symmetric encryption algorithm is that it has a sufficient key length. The SM4 algorithm has the same key length and block length of 128 bits as the AES algorithm, thus providing higher security than the 3DES algorithm.
Similar to AES.
SM9 Algorithm: Issued by the National Cryptography Administration, this is an IBE (Identity-Based Encryption) algorithm. The IBE algorithm uses the user’s identity as the public key, without relying on digital certificates.
A new type of public-private key algorithm based on identity.
Initial Exploration of OpenSSL Programming
In the implementation of these algorithms, it is inevitable to use the OpenSSL library for operations. OpenSSL is very powerful, providing a robust and fully functional encryption suite.
OpenSSL Official Website
Students interested in this can study it in detail. OpenSSL has a large number of APIs that can be used to implement a variety of cryptographic algorithms.
Open Source Algorithm (gmsll.org)
Here I am using GmSSL, developed and maintained by Associate Researcher Guan Zhi’s cryptography research group at Peking University. This project is a branch of OpenSSL that can replace OpenSSL and adds support for national encryption.
I found a lot of usage methods for this open-source library online, but none were very clear. I will summarize the usage methods for this project, which can support usage across multiple platforms.
Next, let’s look at the specific usage methods
Example code can be downloaded from GitHub, which provides test code that can be directly downloaded for debugging. The main implementations are SM2 encryption and decryption and SM4 encryption and decryption. Feel free to star.
The usage methods are as follows:
-
Compile the GmSSL library to obtain the corresponding files.
-
Reference the files.
-
Call using the corresponding programming language.
The compilation environment is (MacBook + Ubuntu virtual machine).
EVP API
Introduction
First, the EVP API is a wrapper for the GmSSL interface that hides the implementation details of the API and provides an abstract, unified interface. We can use this interface to implement usage on other platforms.
Compilation
I am working in the Ubuntu environment.
./configmake
After a successful make, it generates libcrypto.so.1.1 and libssl.so.1.1.
In the code folder, write your own sm4.c, utils.c, sm2.c.
Then use the following code for compilation.
gcc -Wall code/sm4.c code/sm2.c code/utils.c -o my_gmssl -lssl -lcrypto -L. -I include -I apps -I . -L /usr/lib/ssl
Testing
Write test code:
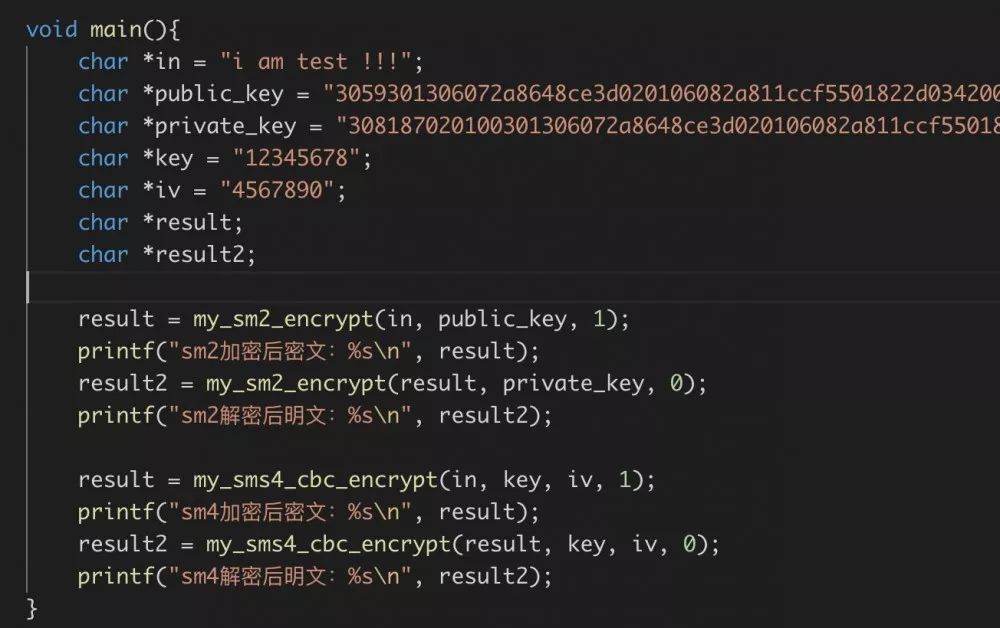
Run results:
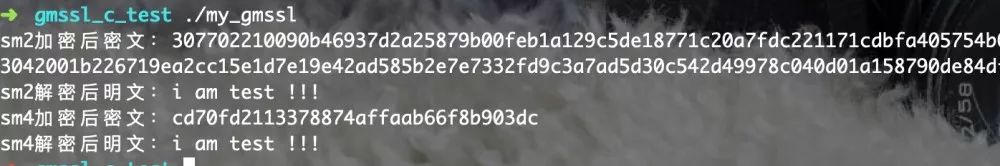
Test successful.
Java API Usage Method (Android)
Introduction
In Android, the method to call this library is mainly through compiling the .so dynamic link library. The official GitHub has provided relevant code, but lacks the NDK compilation process.
Compilation
Pitfalls
Some phones do not support the .so.1.1 soname, so problems arise when referencing libssl.so.1.1 and libcrypto.so.1.1. The solution is:
readelf -d libssl.so
rpl -R -e .so.1.1 "_1_1.so" libcrypto.so
rpl -R -e .so.1.1 "_1_1.so" libssl.soPython Calling Method
Pitfalls
When using memcpy or strcpy to copy the resulting string, it runs normally in C language, but when imported into Python, there may be an additional character or several characters. Therefore, the output result is converted to a hexadecimal string, stabilizing the result.