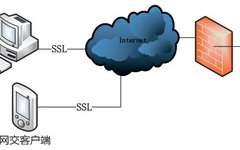
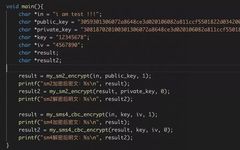
Research on Data Encryption Security System in Securities Trading
Author / Tao Jianfeng, Director of Information Technology Department, CITIC Construction Investment Securities Co., Ltd. Du Guowei, Chen Hongping, CITIC Construction Investment Securities Co., Ltd. Information Technology Department Since the implementation of the “Cryptography Law of the People’s Republic of China”, it has effectively promoted the advancement of cryptographic technology, industry development, and standardized applications. … Read more