Abstract
1. Introduction
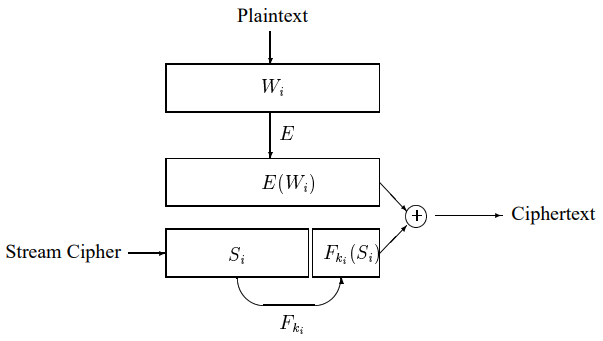
Figure 1-1 Ciphertext Retrieval Implementation Scheme
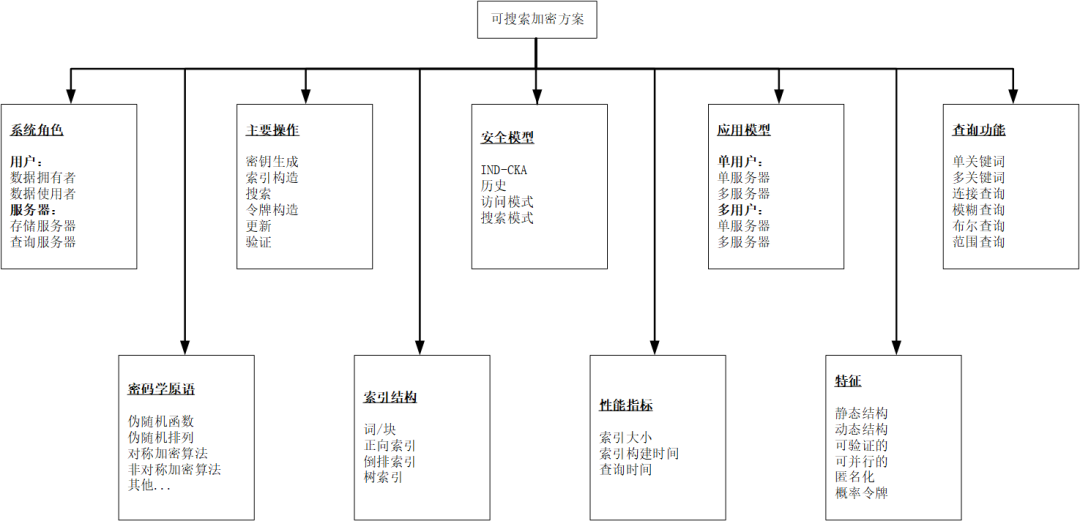
Figure 1-2 Main Research Attributes of Searchable Encryption
2. Symmetric Searchable Encryption Technology
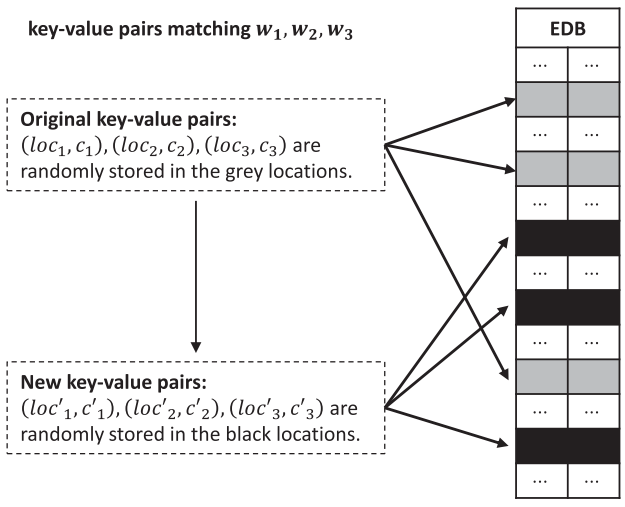
Figure 2-1 Obfuscation Method When k=3
3. Asymmetric Searchable Encryption Technology
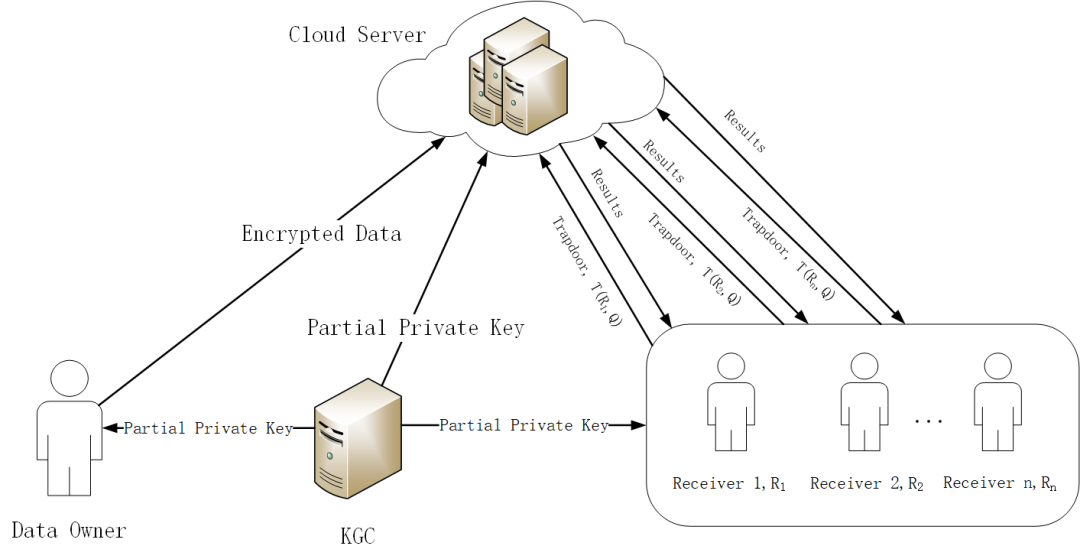
Figure 3-1 Framework of dmCLPAECKS
4. Security Threats and Defense Mechanisms
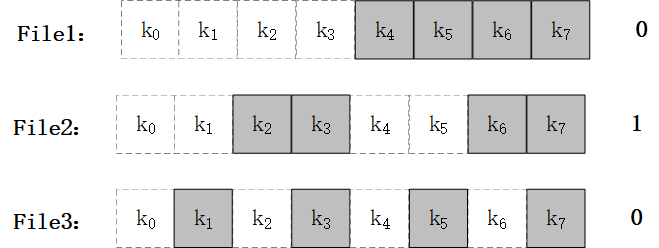
Figure 4-1 Example of File Injection Attack When |K|=8
5. Conclusion
References
[1] Song D X, Wagner D, Perrig A. Practical techniques for searches on encrypted data[C]//Proceeding 2000 IEEE symposium on security and privacy. S&P 2000. IEEE, 2000: 44-55.
[2] Goh E J. Secure indexes[J]. Cryptology ePrint Archive, 2003.
[3] Boneh D, Di Crescenzo G, Ostrovsky R, et al. Public key encryption with keyword search[C]//Advances in Cryptology-EUROCRYPT 2004: International Conference on the Theory and Applications of Cryptographic Techniques. Springer Berlin Heidelberg, 2004: 506-522.
[4] Li J, Wang Q, Wang C, et al. Enabling efficient fuzzy keyword search over encrypted data in cloud computing[J]. Cryptology ePrint Archive, 2009.
[5] Curtmola R, Garay J, Kamara S, et al. Searchable symmetric encryption: improved definitions and efficient constructions[C]//Proceedings of the 13th ACM conference on Computer and communications security. 2006: 79-88.
[6] Kermanshahi S K, Liu J K, Steinfeld R, et al. Multi-client cloud-based symmetric searchable encryption[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(5): 2419-2437.
[7] Zheng Y, Lu R, Shao J, et al. Achieving practical symmetric searchable encryption with search pattern privacy over cloud[J]. IEEE Transactions on Services Computing, 2020, 15(3): 1358-1370.
[8] Wang Q, Zhang X, Qin J, et al. A verifiable symmetric searchable encryption scheme based on the AVL tree[J]. The Computer Journal, 2023, 66(1): 174-183.
[9] Zhang Y, Xu C, Ni J, et al. Blockchain-assisted public-key encryption with keyword search against keyword guessing attacks for cloud storage[J]. IEEE Transactions on Cloud Computing, 2019, 9(4): 1335-1348.
[10] Chenam V B, Ali S T. A designated cloud server-based multi-user certificateless public key authenticated encryption with conjunctive keyword search against IKGA[J]. Computer Standards & Interfaces, 2022, 81: 103603.
[11] Byun J W, Rhee H S, Park H A, et al. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data[C]//Secure Data Management: Third VLDB Workshop. Springer Berlin Heidelberg, 2006: 75-83.
[12] Zhang Y, Katz J, Papamanthou C. All your queries are belong to us: The power of file-injection attacks on searchable encryption[C]//USENIX Security Symposium. 2016: 707-720.
[13] Bost R. ∑ oφoς: Forward secure searchable encryption[C]//Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. 2016: 1143-1154.
[14] Bost R, Minaud B, Ohrimenko O. Forward and backward private searchable encryption from constrained cryptographic primitives[C]//Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. 2017: 1465-1482.
China Secret Association
Scientific and Technological Branch
Long press to scan the code and follow us

Author: Long Hongping, Institute of Information Engineering, Chinese Academy of Sciences
University of Chinese Academy of Sciences, School of Cybersecurity
Editor: Xia Tiantian
2022 Top 5 Highlights Review
Cross-network Attacks: An Introduction to Techniques for Breaking Physical Isolation
Introduction to LaserShark Non-contact Attack Implant Technology
Recent Highlights Review
Security Analysis of Electric Vehicle Charging Station Management Systems
Summary of Common Cybersecurity Threats and Protection Technologies
A Brief Analysis of Security Algorithm and Protocol Verification Issues
A Brief Analysis of IoT Security Issues in Blockchain
Overview of Federated Learning Security