Recently, the cybersecurity research organization PCA Cyber Security discovered a set of serious vulnerabilities named “PerfektBlue” that exist in the BlueSDK Bluetooth framework from OpenSynergy, which could allow remote attacks on infotainment systems in millions of vehicles worldwide.
BlueSDK is a widely used Bluetooth solution in the automotive industry, supporting both classic Bluetooth and low-energy modes, and is hardware-agnostic, allowing manufacturers to customize it according to their needs. However, this flexibility also makes it a breeding ground for security risks. Research shows that attackers can exploit these vulnerabilities to achieve remote code execution, thereby manipulating the in-vehicle systems, including tracking vehicle locations, recording in-car audio, accessing phonebook data, and potentially even lateral penetration into critical functions such as steering and wipers (which has not yet been demonstrated in practice).
The core condition for executing a PerfektBlue attack is pairing with the target device to achieve the corresponding level of secure communication. However, due to the framework characteristics of BlueSDK, the pairing processes for different devices vary significantly—pairing requests may have limitations or be unlimited, may require user interaction, or may be completely disabled. Nevertheless, attackers only need a single user click to exploit the vulnerabilities wirelessly.
The discovered vulnerabilities include four items, detailed as follows:
– CVE-2024-45434: Use-after-free vulnerability in the AVRCP service, CVSS 3.1 score 8.0 (critical)
– CVE-2024-45431: Improper remote CID validation in L2CAP channel, score 3.5 (low)
– CVE-2024-45433: Function termination error in RFCOMM, score 5.7 (medium)
– CVE-2024-45432: Function call parameter error in RFCOMM, score 5.7 (medium)
Researchers have successfully demonstrated the attack on infotainment systems such as Mercedes NTG6, Volkswagen MEB ICAS3, and Skoda MIB3, and have developed related proof-of-concept exploit programs. They noted that these vulnerabilities may be exploitable on some devices without pairing, depending on the manufacturer’s implementation.
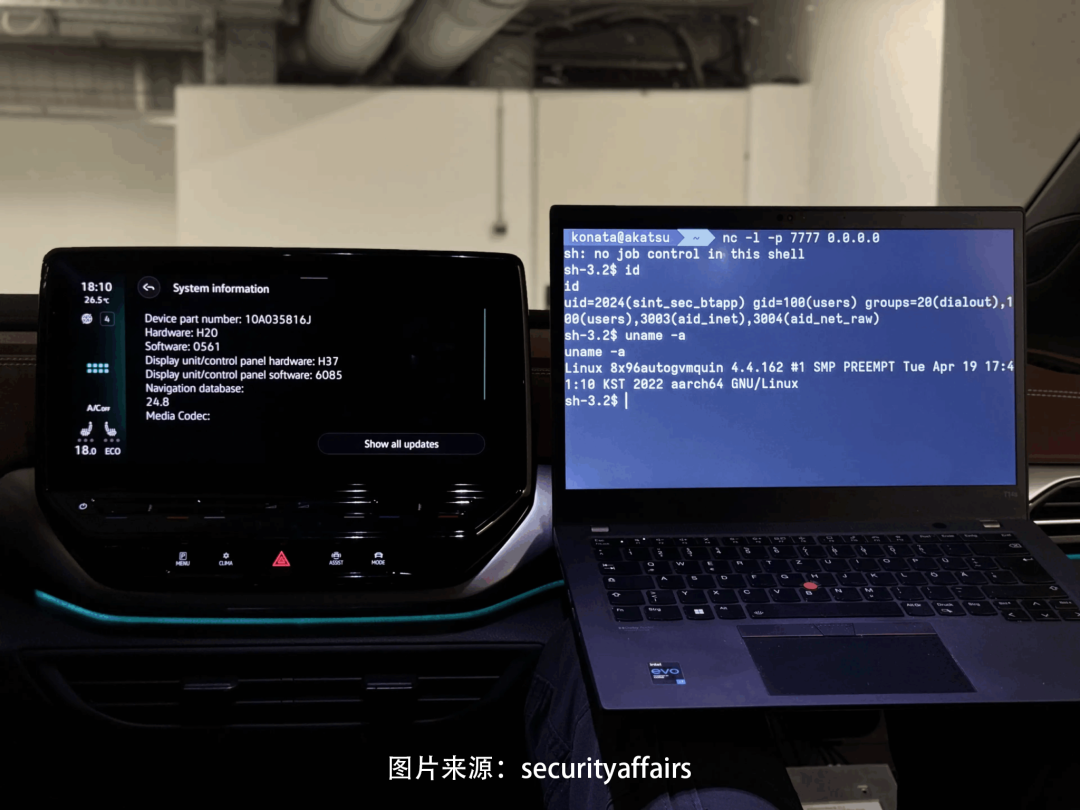
The vulnerability disclosure process has been tumultuous. PCA reported the issue to OpenSynergy on May 17, 2024, and the company confirmed and began remediation in July, completing patch development in September. In March 2025, PCA initiated a responsible disclosure process, but a certain affected automaker claimed in June that it had not received the patch. Ultimately, PCA officially released a security announcement on July 7, aimed at urging the entire industry to accelerate the patching process and enhance security levels.
Security experts recommend that users promptly update their in-vehicle system software or temporarily disable Bluetooth functionality to reduce risks.
Source: securityaffairs
Please cite the source and link to this article when sharing.
﹀﹀﹀

Share

Like

Watch

Click to read the original article for more information.