
Project Name: Password Cracking and Protection Techniques Based on Persistent Fault Injection
Submitting Unit: School of Information and Electronic Engineering, Cyber Security Center
Responsible Person: Zhang Fan
01
Project Overview
Research Background: In today’s severe international competition for chips, as China strives to promote chip autonomy and controllability, chip security has become particularly important. Ultimately, the security of chips lies in the implementation security of cryptographic algorithms on the chips. Attackers can artificially introduce external factors during the execution of encryption algorithms, causing the chip to encrypt incorrectly, thus breaking the key by analyzing the ciphertext. This method is known as fault attack. Due to its small sample size requirement and wide applicability, fault attacks have attracted widespread attention from the international community and have become a core technology in various countries’ “arsenal”.
Project Features and Main Innovations: Traditional fault attacks require strict control of the timing synchronization between encryption and fault injection, thus having considerable limitations. This project breaks through the constraints of strict synchronization between encryption and fault injection by injecting persistent faults before encryption, allowing the recovery of keys implemented by various international advanced encryption standards (AES) with just one fault injection. This technology can overcome existing fault defense measures, is applicable to almost all block cipher algorithms, and can attack embedded chips and general-purpose processor chips. Related work can serve as an important cryptographic analysis technology for China, while the proposed defense solutions can guide the secure implementation of cryptographic algorithms and controllable chips in China.
Significant Achievements:
(1) This achievement is the first paper accepted at the hardware security conference CHES from Zhejiang University, F. Zhang*, X. Lou, X. Zhao, S. Bhasin, W. He, R. Ding, S. Qureshi, K. Ren, “Persistent Fault Analysis on Block Ciphers,” IACR Transactions on Cryptographic Hardware and Embedded Systems, Issue 3, pp.150-172, 2018.
(2) This achievement was awarded the Best Paper at the 2018 China Cryptography Annual Conference (ChinaCrypt2018) and was invited to give a keynote speech at the 2018 China Cryptographic Chip Conference (CryptoIC 2018), receiving high recognition from domestic cryptography peers.
(3) This achievement was subsequently used to guide undergraduate students to complete internships at Nanyang Technological University in Singapore. The extended paper by sophomore student Pan Jingyu was accepted at the top conference in the field of Electronic Design Automation (EDA), DATE 2019, and will be presented at the DATE 2019 conference in March 2019. J. Pan, F. Zhang, K. Ren, S. Bhasin, “One Fault is All it Needs: Breaking Higher-Order Masking with Persistent Fault Analysis,” In DATE 2019, March 2019.
02
Project Team

Figure 1. Research Team Photo
This project is collaboratively conducted by Associate Professor Zhang Fan from the School of Information and Electronic Engineering, Professor Ren Kui from the School of Computer Science, and students such as Lou Xiaoxuan from the Cyber Space Security Research Center. The Cyber Security Center of Zhejiang University is an interdisciplinary research institution supported by the three schools of Computer Science, Information and Electronics, and Control, dedicated to high-level research in the field of cyber security.
03
Scientific Interpretation
Figure 2. Research Diagram
A novel chip attack method proposed by experts from Zhejiang University has recently attracted strong attention from scholars and industry experts at international top conferences in the field of hardware security.
Associate Professor Zhang Fan from the School of Information and Electronic Engineering at Zhejiang University told reporters that he innovated on the traditional method of “fault attack” targeting cryptographic chips, proposing a simpler and more efficient attack method, which can be called “persistent fault attack”. The discovery of this new attack technology helps chip manufacturers improve their security detection methods and serves as a foundation for addressing security vulnerabilities in the next steps.
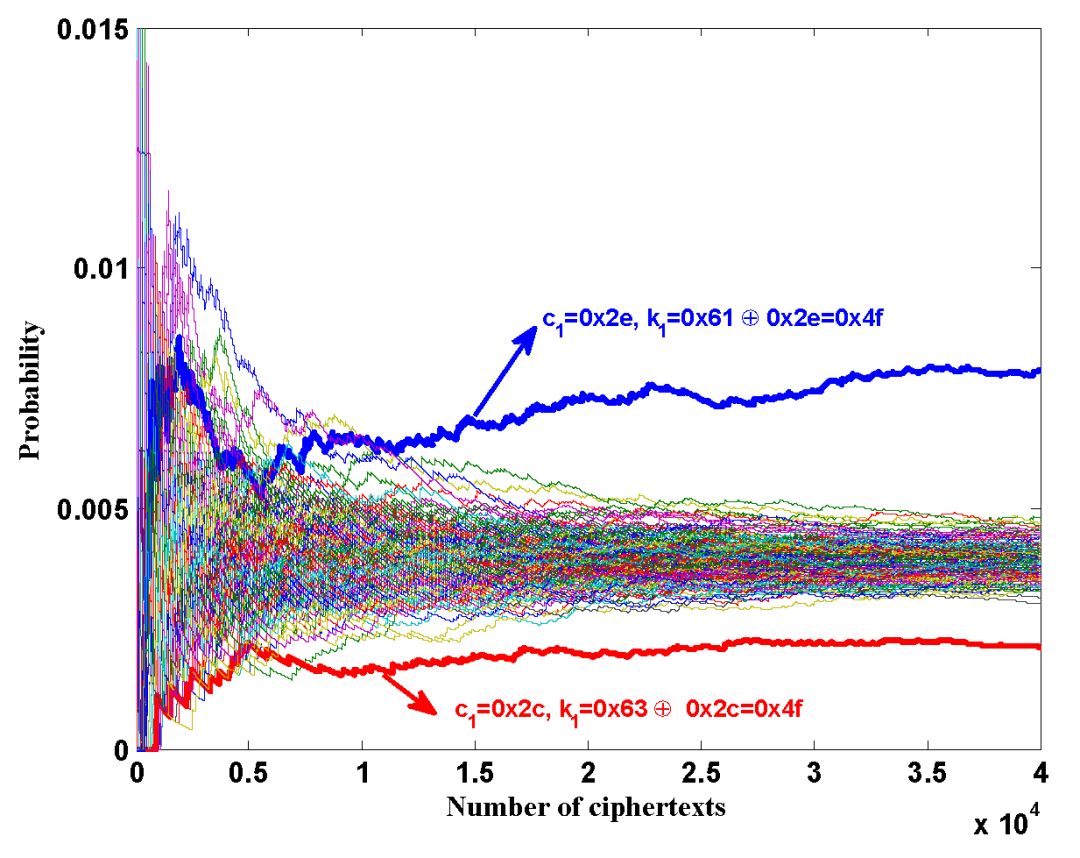
Figure 3. Research Diagram
The related papers of this achievement were accepted at the international top conference in the fields of cryptography and chip security, CHES. Zhang Fan was invited to Amsterdam, Netherlands, to give a keynote speech at CHES2018. This is the only paper from China (including mainland and Hong Kong, Macao, and Taiwan) at this conference and the first paper published by Zhejiang University scholars at CHES. On the last day of the conference, Zhang Fan appeared as the final presenter, and after the report, many experts and scholars asked questions and exchanged views, believing that this method is clever and applicable in many scenarios, deserving much attention.
Today, our convenient daily life is inseparable from chips. Computers, smartphones, credit cards… all rely on chips to function, and these chips store our important information. Given the critical nature of chips, they are naturally subject to strict protection. However, high-level attackers do not need to call you with scam calls; they have ways to crack the keys of chips. Fault attacks are one such type of attack, analyzing and recovering keys based on the erroneous ciphertext information obtained after the attack.
“By using lasers, electromagnetic pulses, or other means to induce specific faults in chips, as long as the timing of the attack is precise enough to synchronize with specific stages of the chip’s computational process, the fault information can be used to recover the keys,” Zhang Fan said. Traditional fault attacks rely heavily on precise timing control and have high operational requirements, followed by extremely complex analysis. Additionally, operations like using lasers to attack chips have many limitations in application scenarios.
Zhang Fan’s proposed “persistent fault attack” exploits inherent flaws in current memory designs, no longer relying on instantaneous attack methods. “We can continuously trigger faults in the chip with a simple piece of code, and the resulting fault information greatly simplifies the subsequent analysis and key recovery work,” Zhang Fan said. These attack codes can be hidden in emails or webpages, significantly simplifying the implementation conditions compared to traditional methods that require lasers.
Zhang Fan stated that the discovery of this new attack method provides many insights for chip security research, and further efforts will be made to seek ways to prevent such attacks.
Click the bottom right corner “Like” to cheer for the project