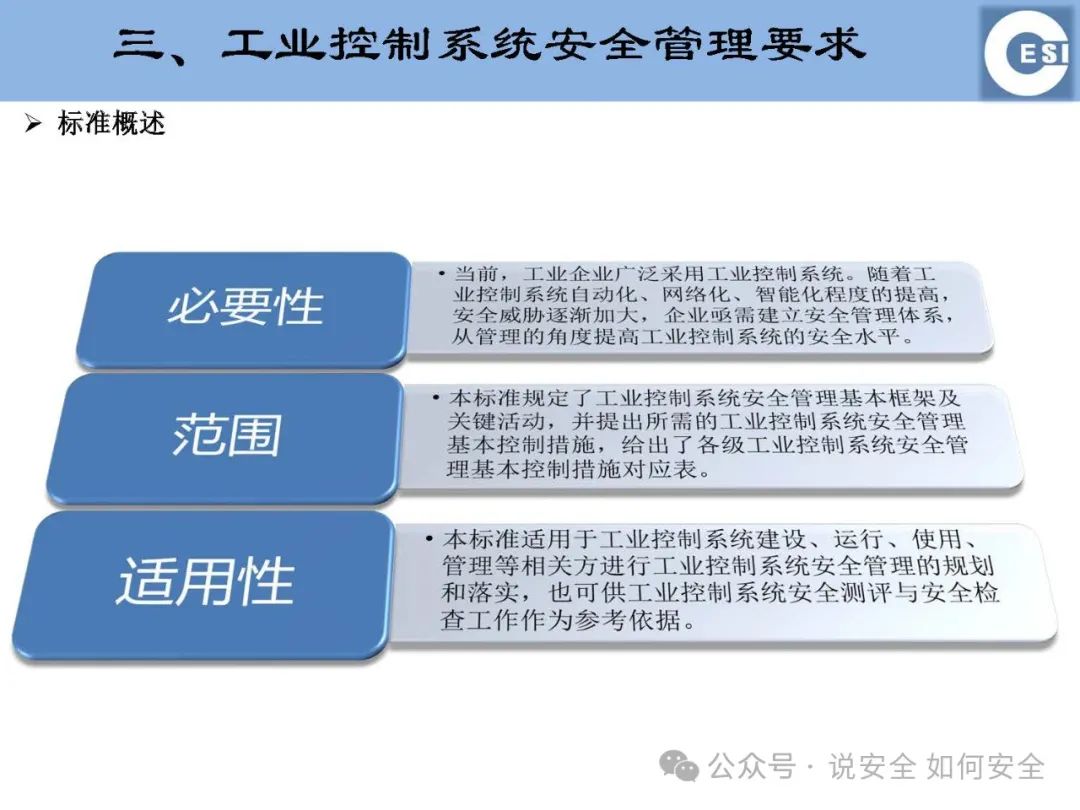
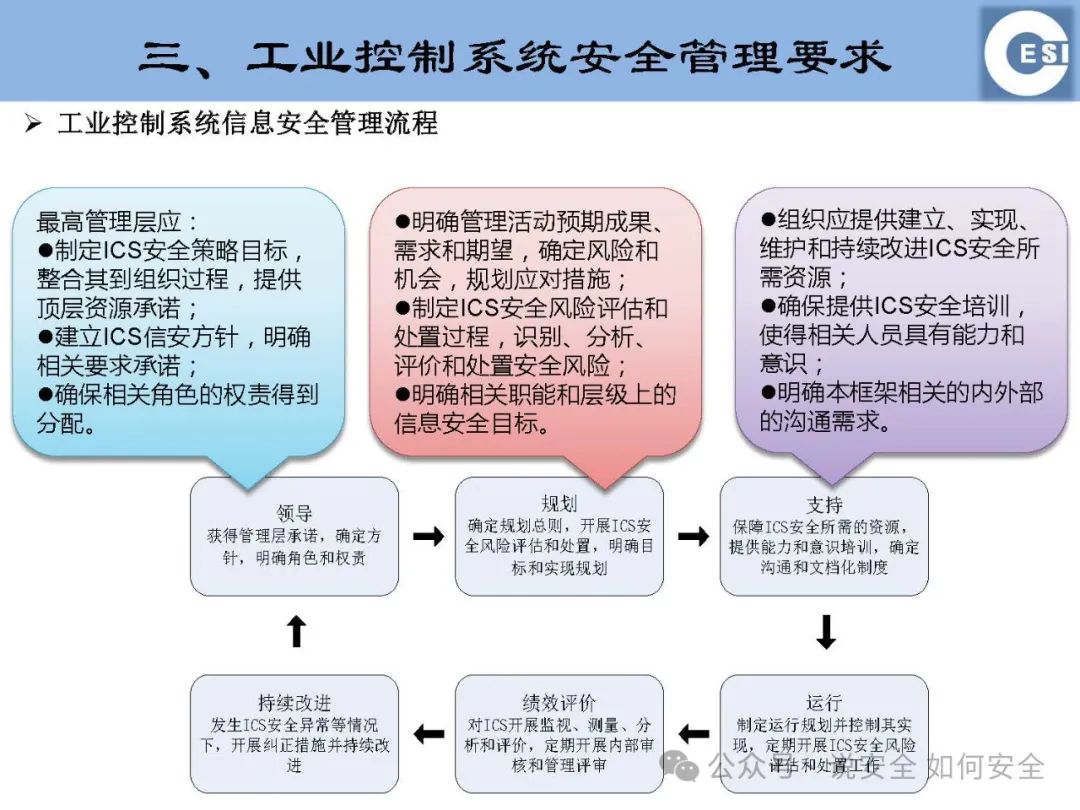
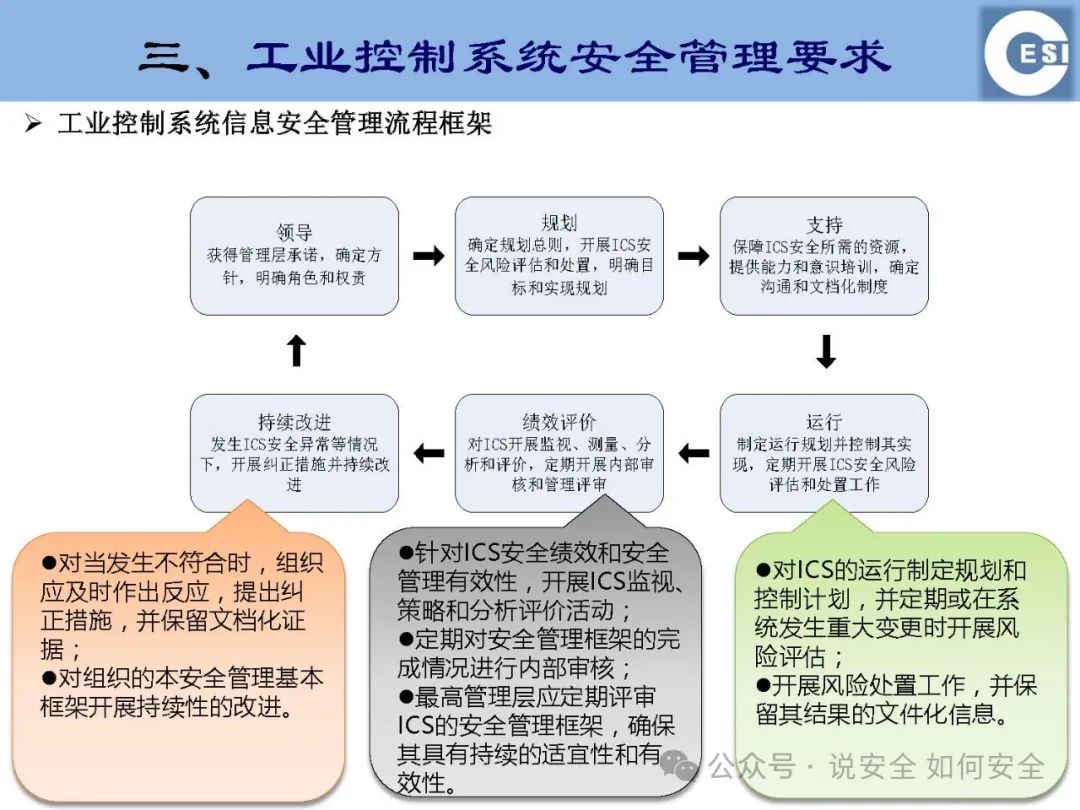
Industrial Control Systems (ICS), as the “nerve center” of national critical infrastructure, directly relate to national economic security, social stability, and the safety of people’s lives and property. However, with the acceleration of digital transformation, the information security threats faced by ICS are becoming increasingly severe. Today, we will delve into the key standards of industrial control system information security and how to build an unbreakable “invisible line” in the smart era.

1. Why is ICS Information Security Crucial?
In emerging fields such as smart manufacturing, smart cities, and smart grids, ICS plays a pivotal role. They achieve precise control and efficient management of industrial processes through the integration of sensors, actuators, controllers, and communication networks. However, as ICS deeply integrates with the Internet and the Internet of Things, their exposure to cyber threats has expanded. Security threats such as hacker attacks, malware, and internal leaks are rampant, posing unprecedented challenges to the secure operation of ICS.
In recent years, several major security incidents targeting ICS have occurred both domestically and internationally, resulting in significant economic losses and social impacts. These incidents warn us that ICS information security is no longer an optional “add-on” but a “must-answer question” concerning national security. Therefore, formulating and improving key standards for ICS information security and enhancing the protective capabilities of ICS have become urgent tasks.
2. Key Standards for ICS Information Security: Building a Comprehensive Protection System
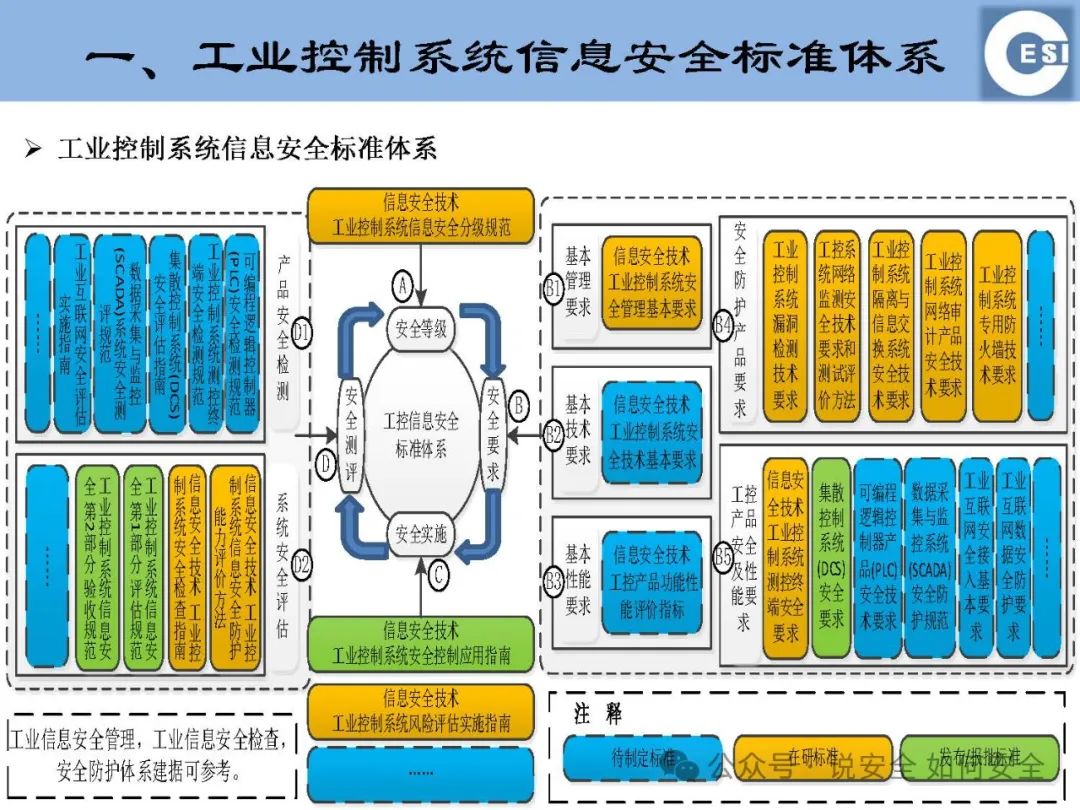
To address the challenges of ICS information security, China’s Ministry of Industry and Information Technology, in collaboration with the National Information Security Standardization Technical Committee, has jointly developed a key standards system for industrial control system information security. This system covers all aspects of ICS information security and provides a scientific basis for building a comprehensive and effective ICS information security protection system.
-
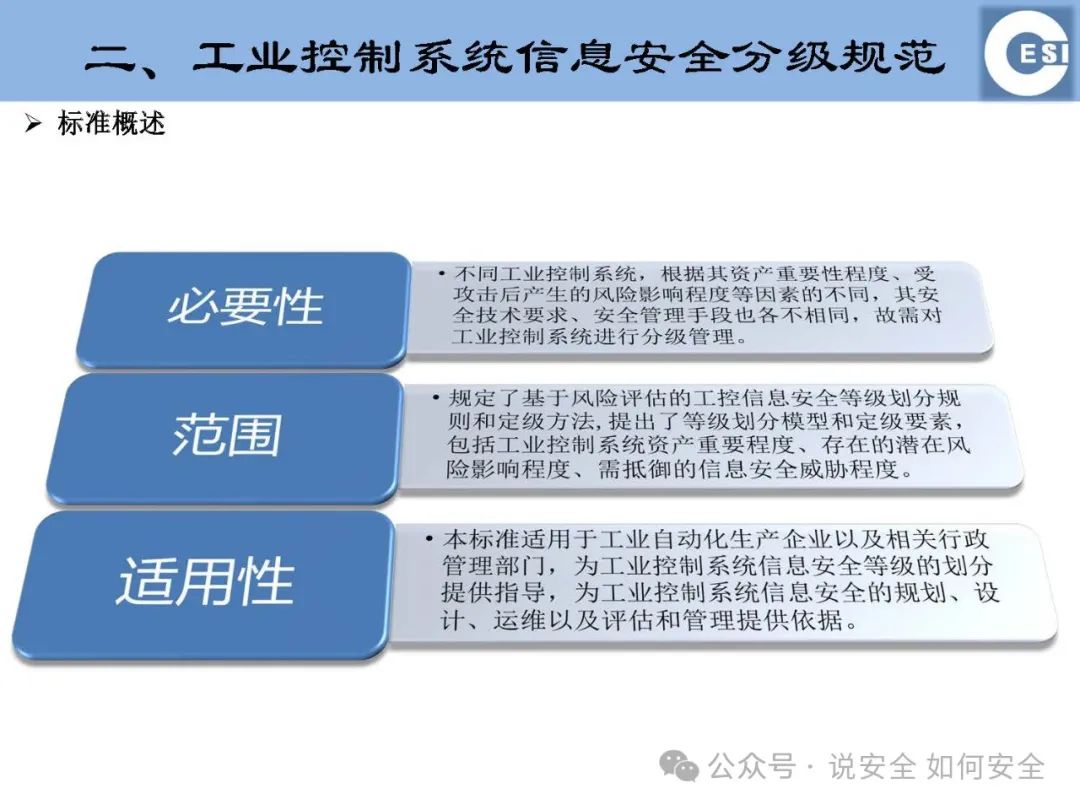
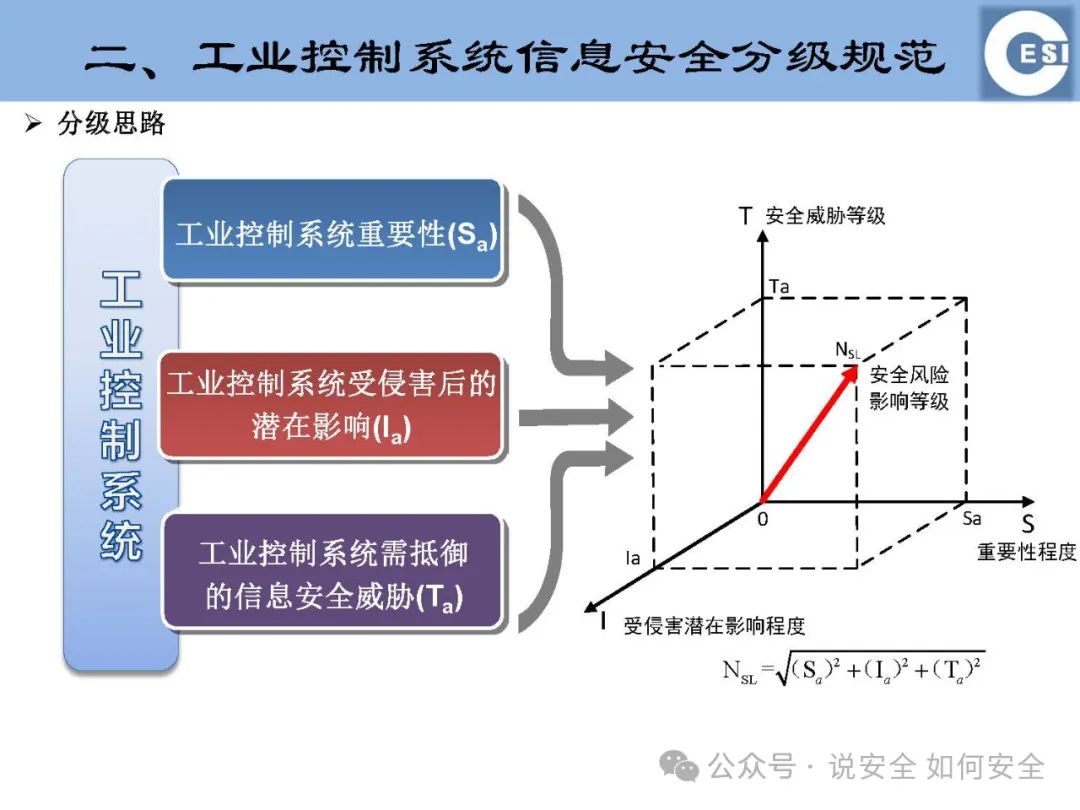
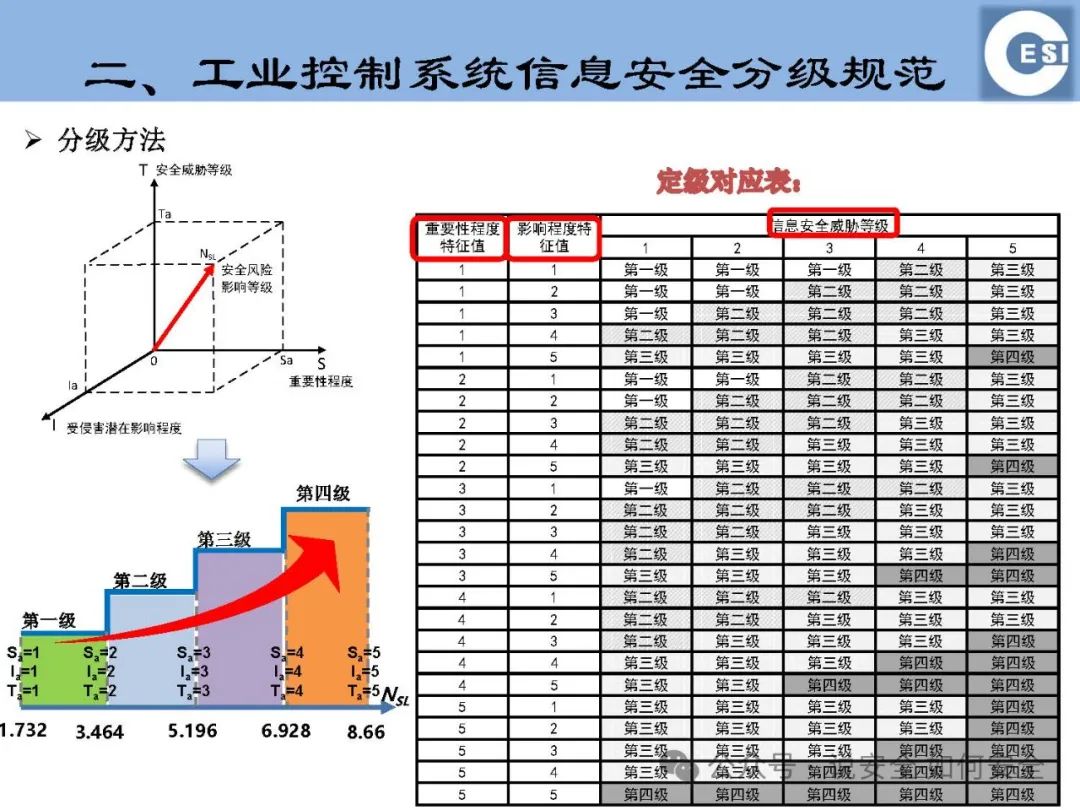
Graded Specifications: ICS information security is categorized into different levels based on potential impacts, importance, and the information security threats that need to be resisted. This helps in formulating differentiated security measures for ICS at different levels, achieving reasonable allocation and efficient utilization of resources.
-
Basic Security Management Requirements: From three dimensions—management, operation, and technology—18 families and 186 security control measures have been proposed. These measures cover access control, security assessment, system and service acquisition, risk assessment, operation and maintenance, and provide comprehensive and detailed guidance for ICS information security management.
-
Security Control Application Guidelines: Guidelines for risk disposal principles and plans have been formulated in response to the vulnerabilities and threats faced by ICS. By applying these guidelines, enterprises can systematically identify, analyze, and assess security risks, and develop effective risk disposal measures to keep ICS security risks at an acceptable level.
-
Security Protection Capability Evaluation Methods: To evaluate the strength of ICS security protection capabilities, detailed evaluation indicators covering 11 major items and 30 minor items related to data security, network security, and host security have been developed. Through on-site evaluations, regular rectifications, and re-evaluations, a comprehensive understanding of the security status and protective capabilities of ICS can be obtained, providing a basis for formulating targeted security protection strategies.
3. How to Build the “Invisible Line” in the Smart Era?
In the smart era, protecting ICS information security is no longer a simple technical issue but a systematic project requiring the joint participation of governments, enterprises, research institutions, and others. To build an unbreakable “invisible line,” we need to start from the following aspects:
-
Strengthen Top-Level Design: The government should increase support for the ICS information security standards system, promoting the formulation and improvement of relevant laws and policies. At the same time, strengthen cooperation and communication with the international community to jointly address the challenges of ICS information security.
-
Enhance Enterprise Protection Capabilities: Enterprises should establish and improve ICS information security management systems and emergency plans, strengthen employee training and education on information security. At the same time, advanced technologies and equipment should be adopted to enhance the security protection capabilities of ICS.
-
Strengthen Technological Research and Innovation: Research institutions should increase investment in the research and development of ICS information security technologies, promoting breakthroughs and innovations in key technologies. At the same time, strengthen cooperation and communication with enterprises to promote the transformation and application of scientific and technological achievements.
-
Enhance Public Security Awareness: Through media promotion, public welfare activities, and other means, raise public awareness and importance of ICS information security. Encourage the public to actively participate in ICS information security protection work, jointly creating a safe and harmonious network environment.
Guarding the “Lifeline” of the Smart Era
Industrial control system information security is the “lifeline” of the smart era, concerning national economic security, social stability, and the safety of people’s lives and property. By formulating and improving the key standards system for ICS information security, strengthening top-level design, enhancing enterprise protection capabilities, boosting technological research and innovation, and increasing public security awareness, we can collectively build an unbreakable “invisible line” to safeguard the stable operation and sustainable development of the smart era.
Key Standards for Industrial Control System Information Security.pdf: https://url22.ctfile.com/f/57015622-1454011070-d0d185?p=5662 (Access password: 5662)