Quoted from: “Intelligent Manufacturing Information Security Technology” (Authors: Qin Zhiguang, Nie Xuyun, Qin Zhen)
This book has been published, for details please see the end~
「 1. Overview of Industrial Control Systems」
Industrial control systems (ICS) refer to a general term for various types of control systems, including monitoring and data acquisition systems and distributed control systems. With the continuous development of the Internet, the high integration of information and industrialization has led to the inevitable trend of interconnection between various systems, and thus the threats faced by industrial control systems are also increasing day by day[1]. Unlike traditional information systems, ICS not only faces traditional network attacks, but due to its structural peculiarities, there are also some targeted attack methods at the physical level.
As a necessary infrastructure for the normal operation of society, industrial control systems, widely used in various sectors such as power, oil, natural gas, aviation, railways, transportation, and urban management, are now gradually receiving more attention regarding their security. From the consequences of attacks, their destructive power is comparable to that of any traditional information system. Therefore, we need to establish a deep-level protection system from multiple angles to ensure the long-term safe operation of control systems. The network diagram of industrial control systems is shown in Figure 1.[2].

Figure 1 Network Diagram of Industrial Control Systems
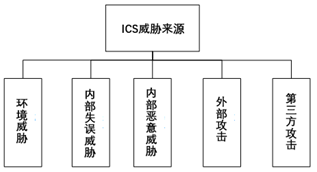
Figure 2 Threat Source Distribution Map
From the perspective of threat sources, the first, second, third, and fifth points are uncontrollable and require comprehensive consideration of various factors, such as personnel management in industrial control systems, operating system selection, and the location of industrial control systems. External personnel attacks on ICS are mainly realized through network attacks. Unlike the CIA (Confidentiality, Integrity, and Availability) principle of traditional information systems, the security importance of industrial control systems is AIC, meaning availability is greater than integrity, which is greater than confidentiality. Additionally, for a specific industrial system, due to its internal structure and network topology differences, there are also targeted attack methods, which are a fusion of multiple-step and multi-technical approaches[3]. Below are some representative attack methods.
1)Replay Attacks
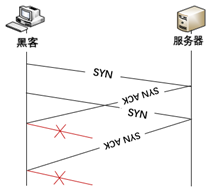
Replay attacks refer to the method where an attacker obtains authentication credentials through network eavesdropping or other means and then sends those credentials to the target host to deceive the system. This process is mainly used in the identity authentication process, which is relatively straightforward. However, due to the diversification of methods for obtaining authentication credentials, replay attacks are still relatively difficult to prevent, as shown in Figure 3.
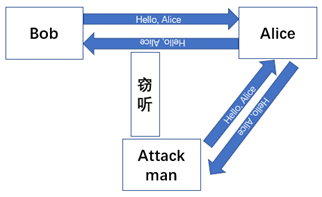
As shown in Figure 3, the attacker eavesdropped on the authentication information “Hello, Alice” and then repeatedly sent it to the target server Alice, successfully achieving the goal of deceiving the target host.
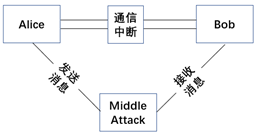
3)Remote Modification of RTU Logic
A Remote Terminal Unit (RTU) is used for remote operations of PLCs. This type of attack mainly targets the availability of the control system. However, under normal circumstances, the RTU is positioned within a local area network in the network topology. Therefore, to modify the RTU logic, one must disguise it as legitimate traffic to bypass the firewall before successfully modifying the RTU logic (Figure 5).
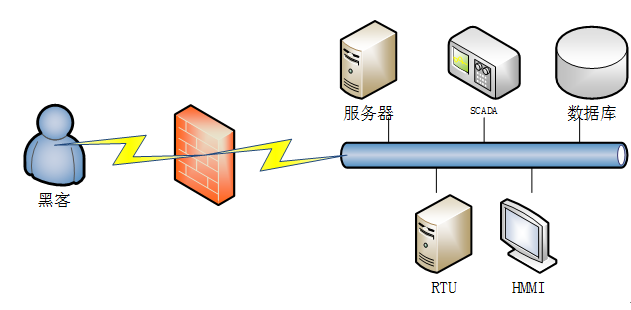
Figure 5 Remote Modification of RTU Logic
4)DoS Attack
The Advanced Persistent Threat (APT) was officially proposed in 2006 and refers to an organized, targeted, covert, highly destructive, and sustained new type of attack and security threat used by organizations or small groups employing advanced attack methods against specific targets[4]. The level of threat can generally be divided into three types: the first involves retaliatory attacks using infective computer viruses, worms, etc.; the second utilizes software vulnerabilities or social engineering emails for infiltration attacks to directly obtain benefits, with more precise and sustained targets compared to the first type; the third mainly targets infrastructure attacks and sensitive information theft, with greater strategic significance and more comprehensive and covert methods of cyber attacks.
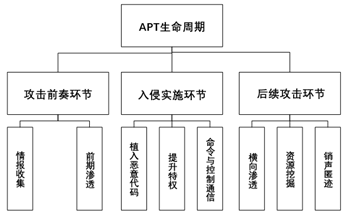
From the lifecycle of APT, APT attacks can be divided into several stages, including intelligence gathering, initial infiltration, implanting malicious code, privilege escalation, command and control communication, lateral movement, resource exploitation, and disappearing without a trace. The APT lifecycle is shown in Figure 7.
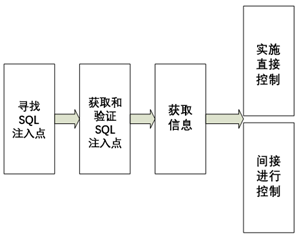
SQL injection is defined as: an attacker inserts a series of SQL statements into an application through a query operation to manipulate data. Its key feature is unauthorized access and direct retrieval from a database. The essence of SQL injection is taking advantage of the syntax processing of SQL statements input in web applications, targeting web application developers who fail to strictly check and process the parameters passed to SQL statements. Programs or websites with SQL injection points are habitually referred to as SQL injection vulnerabilities.
SQL injection has the following characteristics: wide application range, low technical difficulty, and high destructiveness. A specific example of SQL injection is as follows.
|
Generally, web applications will have two parameters for user login: username and password. The program will look up the user table in the database to check if the password matches the username. If the username is “admin” and the password is “123456”, the SQL statement would be as follows: Select * from user where username=’admin’ and password=’smith’ If we do not strictly check the parameters and input the username and password as “admin’or 1=1 –“ and “123456”, the SQL statement would change to: Select * from user where username=’admin’ or 1=1– and password=’123456′ The “or” after “1=1” will always be true, and “–” will comment out the subsequent statements, so this statement will execute successfully even if the user does not know the password. |
8)Port Scanning
Port scanning is a technique for probing which services a server has open to the outside. Attackers usually use it as a necessary means of information collection. They send probe packets to the service ports of the target host and record the responses to determine whether the service ports are open or closed, thus discovering the specific services or information provided by the ports. Attackers can also capture the data flowing in and out of the server to monitor its operation and collect server operation information for further network attacks.
The main techniques for port scanning include TCP connect scanning, TCP SYN scanning, TCP FIN scanning, TCP ACK scanning, IP range scanning, TCP reverse ident scanning, and window scanning. Different scanning techniques should be adopted for different servers, and the effectiveness of scanning may vary depending on the server.
Typically, servers can prevent port scanning attacks by closing idle and potentially dangerous ports and using firewalls to block ports showing scanning symptoms. Specifically, firewalls check each incoming data packet to the local computer, analyzing the traffic characteristics of the packets and rejecting any dangerous traffic from entering the local server, thus achieving the purpose of preventing port scanning.
References
[1] Xia Chunming, Liu Tao, Wang Huazhong, et al. Current Status and Development Trends of Industrial Control System Information Security [J]. Information Security and Technology, 2013, 4(02): 13-18.
[2] Peng Yong, Jiang Changqing, Xie Feng, et al. Research Progress on Industrial Control System Information Security [J]. Journal of Tsinghua University (Natural Science Edition), 2012, 52(10): 1396-1408.
[3] Liu Wei, Li Dong, Sun Bo. Security Analysis of Industrial Control Systems [J]. Information Network Security, 2012(08): 41-43.
[4] Chen Xingshu, Zeng Xuemei, Wang Wenxian, et al. Network Security and Intelligence Analysis Based on Big Data [J]. Engineering Science and Technology, 2017, 49(03): 1-12.



Scan to Follow Us
“Smart Manufacturing Garden”
Adhering to the concept of “advanced manufacturing, strong manufacturing country,”
Tsinghua University Press provides professional knowledge services for everyone!