The security standards for industrial control systems are an important part of the security assurance system for industrial control systems. They play multiple roles in promoting, standardizing, and guiding the security protection work of industrial control systems in various industries. Due to the late overall start of the security protection construction for industrial control systems in China, the security standards for industrial control systems are also obviously lagging behind. In recent years, with the acceleration of the formulation of industrial control system security standards led by the Information Security Standards Committee, the security standards system for industrial control systems in China has gradually entered the “fast lane,” with a large number of security standards being released successively. To help various industries and enterprises gain a deeper understanding of industrial control security standards, Winut has launched a series of articles titled “Understanding Industrial Control System Security Standards,” which will provide a detailed interpretation of the existing industrial control system security standards in multiple issues.
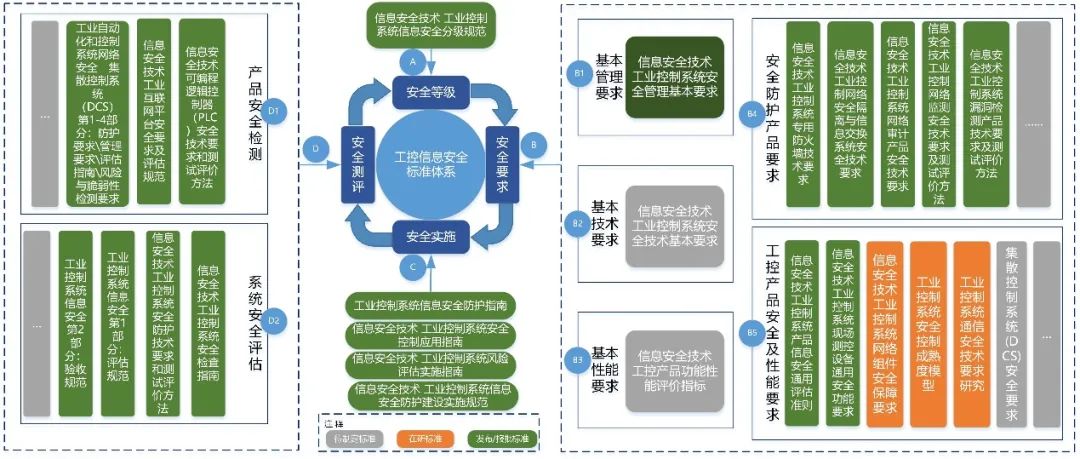
The existing security standards system for industrial control systems in China can be mainly divided into four categories: security levels, security requirements, security implementation, and security evaluation. These correspond to the planning, construction, and evaluation stages of the security protection implementation process for industrial control systems, playing corresponding normative and guiding roles at each stage. The security level standards provide classification guidance for industrial control systems during the security planning phase, determining the overall protection goals; the security requirement standards strengthen the requirements for industrial control security protection technologies, management, and products during the security construction phase; the security implementation standards primarily provide guidance for the implementation process of industrial control security protection construction; the security evaluation standards standardize the methods and processes for evaluating the security of industrial control systems and testing product safety.
According to the logical structure of the security standards system for industrial control systems, our series of articles will start with the security level standard GB/T 36324-2018 “Information Security Technology – Classification Guidelines for Information Security in Industrial Control Systems” (hereinafter referred to as “Classification Guidelines”) and will interpret the security standards for industrial control systems in the entire system one by one.


Overview of the Standards
In 2011, the Ministry of Industry and Information Technology issued a notice titled “Notice on Strengthening the Management of Information Security in Industrial Control Systems” ([2011]451), aiming to implement the relevant spirit of the notice and to achieve a graded management requirement for information security in industrial control systems. It proposed rules for classifying the security levels of industrial control systems and methods for determining these levels, providing technical basis and work guidance for the classification of information security in industrial control systems. According to the special project task book of the Information Security Standards Committee, the standard drafting unit began the standard writing work in 2012, and the standard was officially released in June 2018.

“This standard specifies the rules and methods for classifying the information security levels of industrial control systems based on risk assessment, proposing a classification model and classification elements, including the importance of industrial control system assets, the potential impact of existing risks, and the degree of information security threats that need to be resisted. It also proposes the characteristics of four levels of information security for industrial control systems.”
—— In-Depth Interpretation:The Classification Guidelines propose a security level classification of 1-4, which is basically consistent with the level classification of information security protection in China (the classification of information system security protection is 5 levels, but in practice, levels 1-4 are used). It is consistent with the classification of information security levels for industrial control systems in the international standard IEC-62443 (which is classified into 1-4 levels). The security levels of industrial control systems in the Classification Guidelines have a certain compatibility with the “graded protection” network security protection levels. The factors for determining the original network security protection levels (the objects of harm and the degree of harm to the objects) are included in one dimension of the factors for determining the information security level of industrial control systems (the potential impact of harm). When neglecting the importance of industrial control systems and the two dimensions of information security threats, the resulting security level of industrial control systems is basically consistent with the “graded protection” network security protection level. In other words, if a security level for an industrial control system has already been determined according to the original “graded protection” method, there may be some deviations due to incomplete consideration, but there will not be major conflicts or errors, and certain compatibility still exists. In short, when carrying out the “graded protection” construction and classification of industrial control systems, the model and classification elements of the Classification Guidelines can be referenced for classification.
“The Classification Guidelines are applicable to industrial production enterprises and relevant administrative management departments, providing guidance for the classification of information security levels in industrial control systems and serving as a basis for the planning, design, operation, maintenance, evaluation, and management of information security in industrial control systems.”
—— In-Depth Interpretation:For industrial production enterprises, the Classification Guidelines can provide classification guidance during the security planning and design phases, clarifying the overall goals and main protective measures for industrial control security (which can be based on the characteristics of systems at levels 1-4). At the same time, higher regulatory authorities can also formulate various regulatory mechanisms for guidance, supervision, inspection, and reinforcement measures based on the classification status of industrial control systems in subordinate units.
Key Points of the Standards
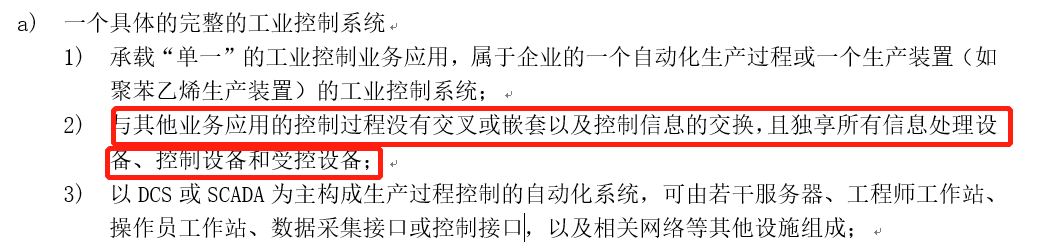
“The classification of information security levels for industrial control systems is based on a specific complete industrial control system, which can also be a relatively independent part of this industrial control system.”
—— In-Depth Interpretation:Taking an automotive manufacturing enterprise as an example, during classification, the entire industrial control system of the stamping, welding, painting, and assembly workshops can be classified, or the key assembly workshop’s industrial control system can be classified separately. However, in general, the security level of a relatively independent part of an industrial control system should not be higher than the security level of the entire industrial control system.
The information security levels of industrial control systems in the Classification Guidelines are defined based on risk impact levels and are divided into four levels. At the same time, the characteristics of industrial control systems at levels 1-4 are defined, primarily distinguishing and defining characteristics based on the degree of impact after damage, the degree of threat resistance, security protection capabilities, and regulatory intensity, providing significant level differences for the protection granularity of industrial enterprises and the intensity of regulatory oversight, thus providing a reference for users and regulatory units.
|
Security Level
|
Impact Degree After Damage
|
Threat Resistance Degree
|
Security Protection Capability
|
Regulatory Oversight
|
|
Level 1 Industrial Control System
|
Will cause damage to the general industrial production operations or damage to the legitimate rights and interests and important properties of citizens, enterprises, and other organizations, but will not harm national security (especially national economic security), environmental safety, social order, public interest, and human life.
|
Should enable the industrial control system to resist malicious threats from individuals with limited resources, general environmental threats, general accidental threats, and other threats of comparable harm level.
|
Should at least have a basic understanding of system assets, operational environments, and security risks, take basic information security control measures, detect system anomalies and security incidents, and execute and maintain emergency response capabilities.
|
Should receive protection and management from the enterprise according to national management norms and technical standards.
|
|
Level 2 Industrial Control System
|
Will cause significant damage to general industrial production operations, or damage to key areas of industrial production operations, or serious damage to the legitimate rights and interests and important properties of citizens, enterprises, and other organizations, or damage to environmental safety, social order, public interest, and human life, but will not harm national security (especially national economic security).
|
Should enable the industrial control system to resist malicious threats from organized groups with moderate resources, general environmental threats, serious accidental threats, and other threats of comparable harm level.
|
Should at least have a relatively comprehensive understanding of system assets, operational environments, and security risks; initially establish a risk management strategy; take relatively comprehensive information security control measures; timely detect system anomalies and security incidents; execute and maintain emergency response capabilities to prevent incidents from escalating and mitigate impacts; and basically restore the operation of industrial control systems affected by security incidents.
|
The information security of Level 2 industrial control systems should be protected and managed by the enterprise in accordance with national management norms and technical standards, as well as under the guidance of national authorities and information security regulatory departments.
|
|
Level 3 Industrial Control System
|
Will cause significant damage to key areas of industrial production operations, or loss to critical areas of industrial production operations, or serious damage to environmental safety, social order, public interest, and human life, or damage to national security (especially national economic security).
|
Should enable the industrial control system to resist malicious threats from hostile organizations and organized groups with moderate resources, serious environmental threats, particularly severe accidental threats, and other threats of comparable harm level.
|
Should at least have a comprehensive understanding of system assets, operational environments, and security risks; establish a risk management strategy; implement information security governance; take comprehensive information security control measures; ensure consistency with the organization’s risk management strategy; timely and comprehensively monitor system anomalies and security incidents; execute and maintain emergency response capabilities to prevent incidents from escalating and mitigate impacts; and restore the operation of industrial control systems affected by security incidents.
|
Should receive protection and management from the enterprise according to national management norms and technical standards, as well as supervision and inspection from national authorities and information security regulatory departments.
|
|
Level 4 Industrial Control System
|
Will cause significant damage to critical areas of industrial production operations, or particularly severe damage to environmental safety, social order, public interest, and human life, or serious damage to national security (especially national economic security).
|
Should enable the industrial control system to resist malicious threats from hostile organizations with abundant resources, particularly severe environmental threats, particularly severe accidental threats, and other threats of comparable harm level.
|
Should at least have a comprehensive understanding of system assets, operational environments, and security risks; establish a comprehensive risk management strategy; implement information security governance; take comprehensive information security control measures; ensure consistency with the organization’s risk management strategy; continuously and comprehensively monitor system anomalies and security incidents; take necessary response measures; execute and maintain emergency response capabilities to prevent incidents from escalating and mitigate impacts; and timely restore the operation of industrial control systems affected by security incidents.
|
Should receive management from the enterprise according to national management norms and technical standards, as well as enhanced supervision and inspection from national authorities and information security regulatory departments.
|
The elements for classifying the information security levels of industrial control systems and their relationships are shown in the following diagram:
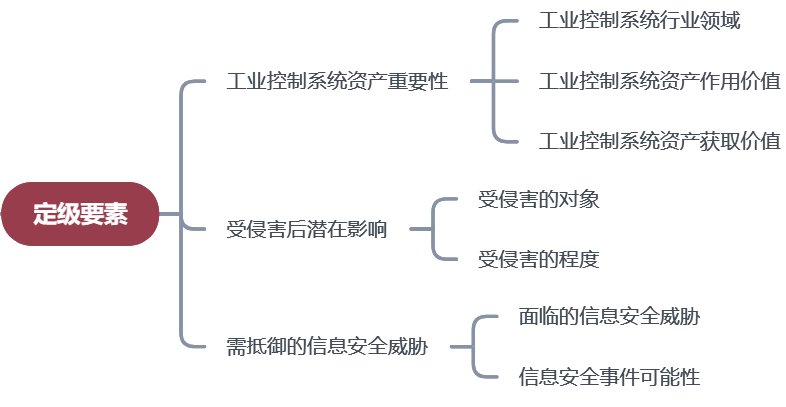 Importance of Industrial Control System Assets:Divided into general, key, and critical areas based on the importance of the industrial production industry where the industrial control system is located (commonly known areas such as steel, chemical, electric power, natural gas, urban rail transit, urban water supply, gas supply, and heating all belong to key areas). The value of an asset is generally evaluated based on its importance in the production process of industrial enterprises. The acquisition value of an asset refers to its original cost, replacement, or reconstruction cost. From the characteristic value table of importance given in the Classification Guidelines, it can be seen that the role value of assets is a key indicator affecting their importance, which also aligns with the characteristics of industrial production enterprises, especially continuous production enterprises, prioritizing the reliability of production operations.
Importance of Industrial Control System Assets:Divided into general, key, and critical areas based on the importance of the industrial production industry where the industrial control system is located (commonly known areas such as steel, chemical, electric power, natural gas, urban rail transit, urban water supply, gas supply, and heating all belong to key areas). The value of an asset is generally evaluated based on its importance in the production process of industrial enterprises. The acquisition value of an asset refers to its original cost, replacement, or reconstruction cost. From the characteristic value table of importance given in the Classification Guidelines, it can be seen that the role value of assets is a key indicator affecting their importance, which also aligns with the characteristics of industrial production enterprises, especially continuous production enterprises, prioritizing the reliability of production operations.
|
Importance of Industrial Control System Assets
|
Industry Field of Industrial Control Systems
|
|
General Area
|
Key Area
|
Critical Area
|
|
Asset Value
|
General asset role value and general acquisition value
|
1
|
2
|
3
|
|
Asset role value is general and acquisition value is very high
|
2
|
3
|
4
|
|
Asset role value is moderate
|
2
|
3
|
4
|
|
Asset role value is very high
|
3
|
4
|
5
|
Note: The characteristic value range for asset importance is from 1 to 5, with higher values indicating greater importance.
Potential Impact Degree After Harm:Reflects the direct and indirect losses caused by harm to information security in industrial control systems, including impacts on the industrial control system and its related production devices, impacts on industrial production safety, and impacts on other harmed objects (such as the legitimate rights and interests and important property security of citizens, enterprises, and other organizations, environmental safety, social order, public interest, and human life safety, national security, and national economic security).
|
Potential Impact Degree After Harm
|
Degree of Harm
|
|
General Damage
|
Serious Damage
|
Particularly Serious Damage
|
|
Harmed
Object
|
Industrial control system and related production device safety
|
1
|
2
|
3
|
|
Industrial production safety and the legitimate rights and interests and important property security of citizens, enterprises, and other organizations
|
1
|
2
|
3
|
|
Social order, public interest, environmental safety, and human life safety
|
2
|
3
|
4
|
|
National Security (especially national economic security)
|
3
|
4
|
5
|
Note: The characteristic value range for potential impact degree is from 1 to 5, with higher values indicating greater potential impact after harm.
Degree of Information Security Threats to Resist:In the face of numerous existing threats, the degree of information security threats that need to be resisted is determined based on the inherent vulnerabilities and exploitability of industrial control systems, related production devices, and the enterprises or industries they belong to, as well as the probability of information security incidents occurring. The threat levels to be resisted range from 1-5, with 5 being the highest.
The Classification Guidelines primarily establish the information security classification process for industrial control systems based on risk assessment. Typical information security risk assessment activities mainly include: determining the assessment object, risk identification, and risk calculation. The classification process for information security in industrial control systems adopts consistent methods and processes. Determining the classification object of industrial control systems is part of the risk assessment object; determining the importance of assets, potential impact after harm, and the degree of information security threats to resist are part of the risk identification process; determining the information security level of industrial control systems belongs to the risk calculation activity.
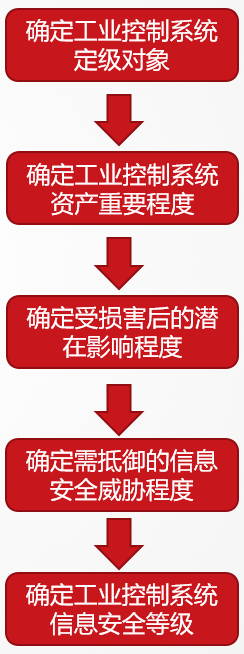
(1) Determine the Classification Object
The Classification Guidelines require that the industrial control systems to be classified meet four basic conditions:
◇ The classified industrial control system must be a complete industrial control system that can operate independently, equipped with all necessary components such as servers, engineer stations, data collection interfaces, and communication networks, without relying on other systems or exchanging control information with other systems. For example, a typical DCS system includes the upper computer, lower control components, data acquisition modules, control networks, and field control devices, which can form a complete independent system.
◇ The classified industrial control system must be a relatively independent unit capable of undertaking part of the control processes in the entire production business system and achieving partial business applications. A single independent control subsystem or multiple subsystems that form an independent production unit can be set as the classification object, but these subsystems must have common security requirements.

◇ The classified industrial control system must include all basic elements of an industrial control system, and the classification object should contain all basic elements of the automation system (detectors, controllers, actuators, and objects) and be able to independently complete a complete control process in industrial production. It cannot be a single control component.

◇ The classified industrial control system must have a uniquely determined security responsibility unit, requiring enterprises to clearly define the security responsibility unit for the classified industrial control systems before classification.

(2) Determine Asset Importance
Asset importance is determined based on the asset value, industry field, and business mission of the classified industrial control system. Enterprises are required to reasonably classify the importance of their industrial control systems in their production business before classification. The importance characteristic value should be a relative value reflecting the importance of all system assets within the enterprise, highlighting the differences in importance among various systems. For instance, if the asset value and business mission of the DCS system in a thermal power plant are higher than those of the SIS system, then the characteristic value of the DCS system should also be higher in terms of asset importance.

(3) Determine the Potential Impact Degree After Harm
The analysis of the impact degree after harm to the classified industrial control system is mainly based on the following aspects:
◇ Confirm whether the industrial control system has been harmed: This is mainly judged by whether the availability, integrity, and confidentiality attributes of the information security of the classified industrial control system have been partially or completely compromised.

◇ Confirm the manifestation of harm: This is mainly divided into damage to system services and damage to business data. The objects of harm and the degree of impact vary between these two forms of harm. Damage to system services mainly affects system availability, while damage to business data mainly affects the integrity and confidentiality of system business operations.

◇ Evaluate the objects harmed, which generally include national security (especially national economic security), environmental safety, human life safety, social order stability, public interest, industrial production safety, as well as the legitimate rights and interests and important property safety of citizens, enterprises, and other organizations. The classification guidelines provide judgment criteria for various objects.

◇ Evaluate the degree of harm suffered, defining the degree of harm for various objects according to general damage, serious damage, and particularly serious damage. The classification guidelines provide conditions for categorizing the degree of harm for various objects.

(4) Determine the Degree of Information Security Threats to Resist
The classification guidelines mainly define the degree of information security threats based on the existing threats and the likelihood of information security incidents occurring:
◇ The existing information security threats are primarily identified based on the source of threats, forms of threat manifestation, and the degree of threat. The analysis of threats faced by the classification object includes: common threat lists, industry statistics and analysis, and historical security incidents of the system.

◇ The likelihood of information security incidents occurring should be based on a thorough vulnerability assessment of the classified industrial control system, combining industry data to define and analyze the frequency of occurrence, and determining the characteristic value of the likelihood of information security incidents based on the degree of exploitability of vulnerabilities and frequency of occurrence.
|
Likelihood of Information Security Incidents
|
Ease of Exploitability of Inherent Vulnerabilities
|
|
Low
|
Medium
|
High
|
|
Threat Occurrence Frequency
|
Low
|
1
|
2
|
3
|
|
Medium
|
2
|
3
|
4
|
|
High
|
3
|
4
|
5
|
(5) Determine the Information Security Level of the Industrial Control System
Finally, using the determined characteristic values for the importance of assets, potential impact after harm, and the degree of information security threats to resist, one can look up the corresponding level in the table below to determine the information security level of the industrial control system based on risk.
|
Asset Importance Characteristic Value
|
Potential Impact Degree After Harm Characteristic Value
|
Degree of Information Security Threats to Resist Characteristic Value
|
|
1
|
2
|
Level 1 (1)
|
Level 1 (2)
|
Level 1 (3)
|
Level 1 (4)
|
Level 2 (5)
|
|
2
|
1
|
Level 1 (2)
|
Level 1 (3)
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
|
3
|
1
|
Level 1 (3)
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
|
4
|
1
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
|
5
|
1
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
|
1
|
2
|
Level 1 (3)
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
|
2
|
2
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
|
3
|
2
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
|
4
|
2
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
|
5
|
2
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
Level 4 (11)
|
|
1
|
3
|
Level 1 (3)
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
|
2
|
3
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2(7)
|
Level 3 (8)
|
|
3
|
3
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
|
4
|
3
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
|
5
|
3
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
Level 4 (11)
|
|
1
|
4
|
Level 1 (4)
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
|
2
|
4
|
Level 2 (5)
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
|
3
|
4
|
Level 2 (6)
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
|
4
|
4
|
Level 2 (7)
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
Level 4 (11)
|
|
5
|
4
|
Level 3 (8)
|
Level 3 (9)
|
Level 3 (10)
|
Level 4 (11)
|
Level 4 (12)
|
Note: The numbers in brackets in the table represent the characteristic values of the information security levels of industrial control systems, where the characteristic values for asset importance, potential impact after harm, and the degree of information security threats to resist range from 1 to 5. The characteristic values for information security levels range from 1 to 13, with the corresponding relationship being that the first level of information security corresponds to a characteristic value range of 1-4, the second level is 5-7, the third level is 8-10, and the fourth level is 11-13.

The Classification Guidelines provide rules and methods for classifying information security levels based on the risk impact of industrial control systems, propose classification models and elements, and clarify the characteristics of potential risk impacts, information security threats, information security capabilities, and information security management across various levels of industrial control systems. They are applicable to industrial automation production enterprises and relevant administrative management departments, providing guidance for the classification of information security levels in industrial control systems, and can also provide more scientific and accurate classification methods and guidance for numerous industrial enterprises in the process of establishing security protection, especially compliance with graded protection.
Beijing Winut Technology Co., Ltd. (hereinafter referred to as “Winut”) is a leading enterprise in industrial control network security in China, one of the six companies in the world to receive the ISASecure CRT Tool certification from the International Society of Automation, and the only founding member of the Global Cybersecurity Alliance (GCA) of the International Society of Automation (ISA) in the Asia-Pacific region.
As a national high-tech enterprise, Winut focuses on innovative “white environment” overall solutions and has independently developed a full range of dedicated products for industrial control network security, holding 52 invention patents, 50 software copyrights, and 52 original vulnerability proofs as core intellectual property. Winut actively leads and participates in the formulation of national and industry standards in the field of industrial control network security, and has been invited to successfully complete network security tasks for major events such as the 70th anniversary of New China, the 19th National Congress of the Communist Party of China, and the Two Sessions, receiving high recognition from national government departments such as the Central Cyberspace Affairs Commission, the Ministry of Public Security, and the Ministry of Industry and Information Technology. To date, Winut has successfully provided comprehensive and effective security guarantees for over 1,000 industrial enterprises in key national industries such as electric power, rail transit, petroleum and petrochemicals, military industry, tobacco, municipal administration, smart manufacturing, and metallurgy.
Winut is committed to its mission of “focusing on industrial control and safeguarding security,” dedicated to ensuring the cybersecurity of critical information infrastructure in China!





Channel Cooperation Consulting: Mr. Zhang 18201311186
Manuscript Cooperation: WeChat: Luo_xiaoran