When consulting with clients in various industries, they often ask a question: “Our industrial control system is already isolated from the Internet and is essentially an island, with no data or information coming in. Why do we still need to build network security?” In response to this question, I explain to clients the following points, informing them that isolated industrial control systems are not secure.
1. WIFI Wireless Connections Open a Channel Between Industrial Systems and the Internet
Nowadays, our smartphones can access the Internet, and almost everyone’s mobile network is on 24 hours a day. When the battery is low, we can charge our phones via a computer USB port or a power source. In industrial settings, there is a situation where dispatch or maintenance personnel plug their phones into the industrial control machine’s USB port to charge while simultaneously accessing the Internet. This directly leads to the previously isolated industrial control system being connected to the Internet through the phone, allowing Internet viruses to enter the industrial control host and spread throughout the entire control network. As shown below:
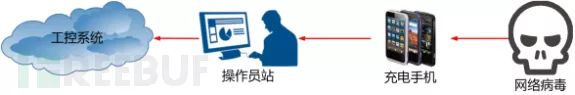
Virus Infiltration Flowchart
The University of Tulsa in the United States has conducted penetration testing specifically targeting wind farms. The first step of the penetration test is to exploit physical security vulnerabilities by connecting a small WIFI device to the control system to achieve the goal of attacking the wind farm. I will not elaborate on the details of the attack here; readers can search for the article “The Entire Process of Hacking into a Wind Power Plant” published by Security Cow to understand the entire attack process.
Currently, the following solutions are available for this issue:
Control the USB ports physically or through software to prohibit external devices from connecting;
Deploy wireless protection devices to protect wireless signals;
Use a whitelist approach to protect the host.
2. Remote Maintenance Opens a Channel Between Industrial Systems and the Internet
When problems arise at an industrial site that on-site personnel cannot handle, clients typically take two measures:
(1) Request an engineer to come on-site;
(2) If the engineer cannot come on-site, they can only resolve the issue remotely.
We will not discuss the first situation here; the focus is on the second situation, where remote troubleshooting is common in industrial settings. How is remote maintenance typically conducted in industrial systems isolated from the Internet? Generally, it is resolved in the following ways:
Connecting the problematic computer to a WIFI hotspot and using remote control software for remote operations;
Connecting the problematic computer to an Internet-enabled switch and using remote control software for remote operations.

Using a privately connected switch to access the Internet
These methods pose significant risks to industrial control systems. Firstly, the computer that is having issues is already online, thus connecting the industrial control system to the Internet; secondly, simply using remote control software to operate the on-site computer does not allow for identity verification of the remote maintenance personnel and cannot record operational actions. In the event of an incident, accountability cannot be assigned.
Therefore, when we encounter issues on-site, we should prioritize having an engineer come to handle the problem. If the engineer cannot arrive promptly, we can only resolve it through remote maintenance. In this case, we need to deploy an industrial control maintenance system within the industrial control system to address network security issues during remote maintenance. The deployment diagram is as follows:
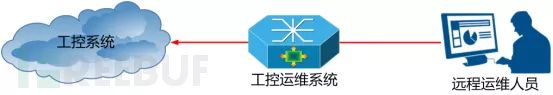
Deployment Diagram of the Industrial Control Maintenance System
This system can mainly achieve the following functions:
Support the parsing of industrial protocols (such as OPC, Modbus, etc.) to enable auditing of industrial control commands;
Flexible deployment, plug and play, facilitating targeted remote maintenance of devices;
Ensure safe isolation of maintenance devices from the devices being maintained, preventing abnormal behaviors and malicious code from spreading to the industrial control system, thereby ensuring the security of the industrial control system;
Monitor and record operations of industrial configuration monitoring software, supporting major domestic and international industrial control system vendors;
Collect and authenticate the identities of maintenance personnel, recording maintenance data throughout the process.
3. The Development of Enterprise Informatization Requires ERP Systems to Extract Data from the Production Network
With the development of industrialization and informatization, major industrial and energy enterprises are engaged in corresponding informatization construction. Various industries have gradually completed the upgrade and transformation of industrial systems, forming advanced production technologies such as digital mines, smart power, smart oilfields, and intelligent manufacturing. The completion of these advanced production technologies brings forth network security issues, as illustrated in the enterprise informatization architecture below:
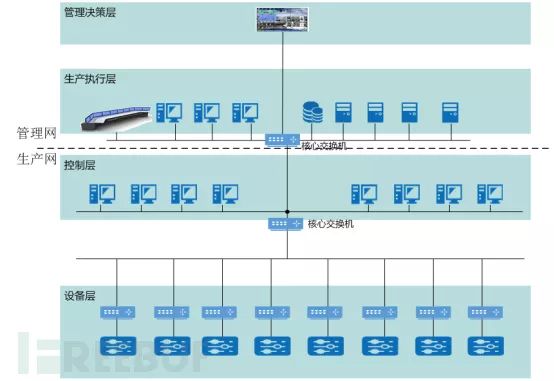
System Architecture Diagram
The construction of informatization opens a link between the production network and the management network, allowing the management network to read data from the production network for analysis to facilitate high-level decision-making. The management network transmits the decision information back to the production network for execution, improving overall production efficiency. However, if the management network is infected with viruses and malicious code, it could easily be transmitted to the production layer during data transfer.
For example, in 2017, a large energy enterprise suffered from a ransomware virus infection due to a dual-network card server connecting both the production network and the management network without any protective measures, resulting in economic losses for the entire enterprise. As shown below:
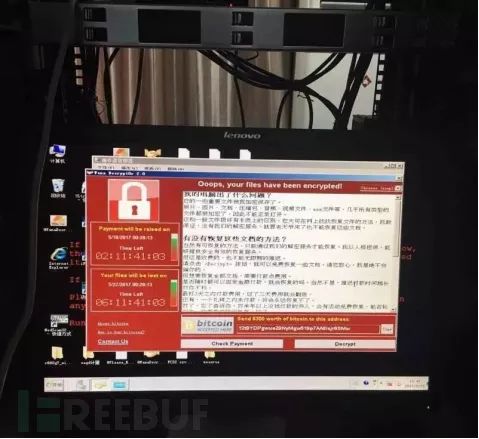
Server Infected with Ransomware on Site
The solution to this issue is to deploy an industrial firewall between the management network and the production network to achieve isolation between production and management. The deployment is shown in the following diagram:
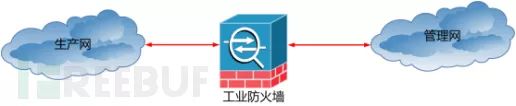
Deployment Diagram of the Industrial Firewall
4. Using USB Drives for Data Transfer Within the Production Network
We know that USB drives are significant carriers for spreading viruses, and their usage frequency in industrial settings is very high, often used for data copying. Although some sites block USB ports with seals, it is essentially ineffective, as staff will tear off the seal when they need to use the USB port and reseal it afterward.
Record of Frequent USB Insertions and Removals on Site
The best solution is to control the computer interfaces through host protection software while using dedicated secure USB drives for data copying and transfer.
5. Poor Internal Management Leading to Data Leakage or Loss
Currently, the information security management system in the industrial control field is inadequate, lacking important information security positions and personnel training in information security awareness. The phenomenon of posting passwords and using weak passwords is common, as shown below:

Discovered Passwords Posted on Site
The lack of regular vulnerability scanning and an understanding of system risks means that the security status of the system cannot be described.
The deficiencies in security management mentioned above can lead to insufficient employee security awareness, loss or theft of important data on-site, and important control programs falling into the hands of competitors or hackers for exploitation.
To address these issues, it is not enough to simply establish security management systems; regular risk assessments and employee security awareness training are also necessary. Lessons should be learned from domestic and international security incidents, continuously updating and iterating security policies and emergency plans. Overall, the formation of security management is a long-term cultivation process.
6. Conclusion
In summary, industrial control systems isolated from the Internet also need to strengthen network security construction. Network security construction is not merely about deploying a few security devices and setting some security policies. It requires referencing national standards and laws, employing both security technology and management methods, enhancing personnel security awareness training, and other comprehensive planning to better ensure the network security of industrial systems and protect our critical infrastructure.
*Author: Liu Jian Shuai, this article belongs to the FreeBuf Original Reward Program and is prohibited from reproduction without permission.
