There are two sayings:
1) Algorithms and data structures are an important part of programming. If you lose algorithms and data structures, you lose everything. 2) Programming is algorithms and data structures; algorithms and data structures are the soul of programming.
Note that this is not my own statement, but a summary from countless programmers. The words are very practical and insightful. If you want to develop sustainably in the long run, it is essential to study algorithms. Today, I will talk about symmetric encryption algorithms in encryption algorithms and teach everyone how to program with symmetric encryption algorithms. This includes the programming usage of DES, 3DES, and AES symmetric encryption algorithms, packed with useful information.

1. Symmetric Encryption Algorithms
Symmetric encryption algorithms are the most widely used and frequently applied encryption algorithms today. They are popular not only in the software industry but also in the hardware industry. Any infrastructure that involves security requirements will prioritize symmetric encryption algorithms.
The encryption key and decryption key of symmetric encryption algorithms are the same. For most symmetric encryption algorithms, the encryption and decryption processes are inverses of each other.
(1) Encryption and Decryption Communication Model
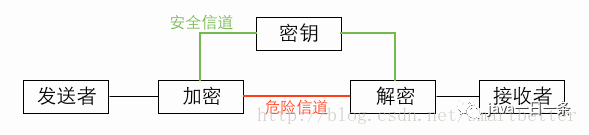
(2) Characteristics: Algorithm is public, low computational load, fast encryption speed, high encryption efficiency
(3) Weakness: Both parties use the same key, which does not guarantee security
Symmetric encryption includes stream ciphers and block ciphers, but currently, block ciphers are most commonly used:
(4) Block Cipher Working Modes
1) ECB: Electronic Codebook (most commonly used, each encryption produces independent ciphertext blocks, and does not affect other ciphertext blocks, meaning that the same plaintext encrypts to the same ciphertext)
2) CBC: Cipher Block Chaining (commonly used, plaintext must first XOR with the previous ciphertext before encryption, meaning that the same plaintext encrypts to different ciphertext)
3) CFB: Cipher Feedback
4) OFB: Output Feedback
5) CTR: Counter
These five working modes are mainly applied to algorithms in cryptography during the reasoning process.
6. Block Cipher Padding Methods
1) NoPadding: No padding
2) PKCS5Padding:
3) ISO10126Padding:
7. Common Symmetric Ciphers:
1) DES (Data Encryption Standard)
2) 3DES (Triple DES, an algorithm that performs triple DES encryption)
3) AES (Advanced Encryption Standard, AES can effectively resist known attacks against DES)
Let’s first look at a simple comparison of these three algorithms:
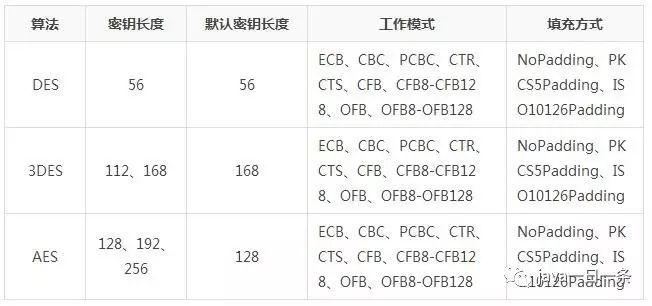
Next, let’s see how to implement symmetric encryption using the DES / 3DES / AES algorithms:
2. DES Algorithm
1. DES: Data Encryption Standard, a typical algorithm in the field of symmetric encryption algorithms
2. Characteristics: Short key length (56 bits), short lifecycle (to avoid being cracked)
3. Java Implementation
1) Generate Key
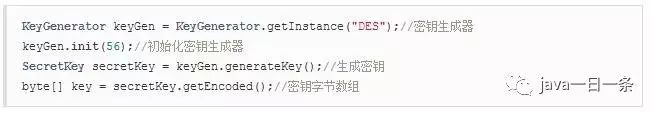
2) Encryption
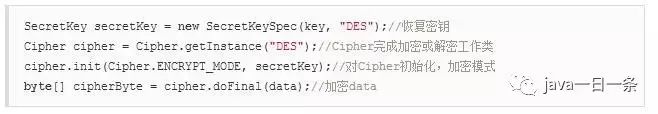
3) Decryption
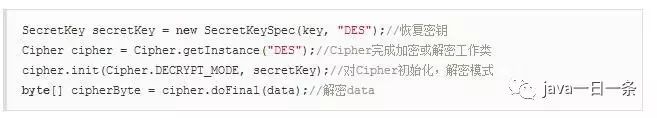
We can see that encryption and decryption are just set with different modes.
3. 3DES Algorithm
1. 3DES: Increases key length to 112 bits or 168 bits, improving security by increasing the number of iterations
2. Disadvantages: Slower processing speed, longer key calculation time, lower encryption efficiency
3. Java Implementation
1) Generate Key
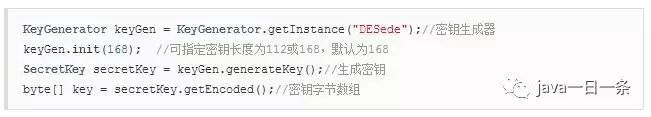
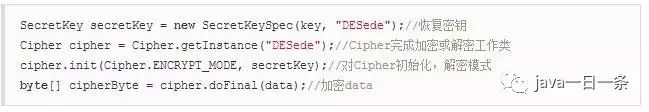
2) 3DES Encryption
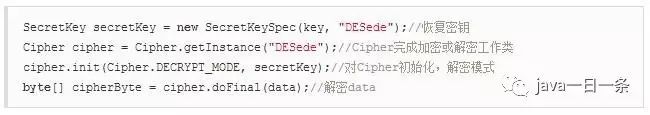
3) 3DES Decryption
4. AES Algorithm (Recommended)
1. AES: Advanced Encryption Standard, effectively resists all known attacks against the DES algorithm
2. Characteristics: Short key establishment time, good sensitivity, low memory requirement, high security
3. Java Implementation
1) Generate Key
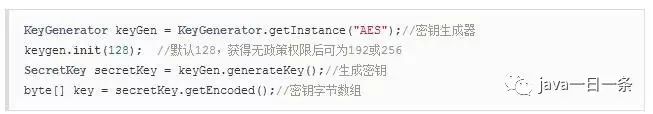
2) AES Encryption
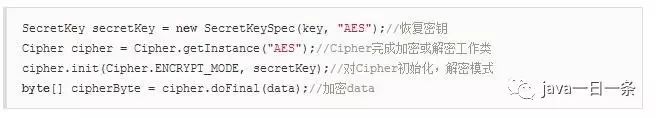
3) AES Decryption
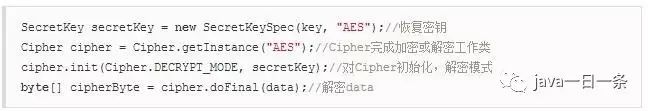
For convenience, I have written utility classes for the DES / 3DES / AES algorithms. Address: https://github.com/smartbetter/AndroidUtilsLibrary (new DES/3DES/AES utility classes).