Experts can skip this; this is just a beginner’s learning note, not very substantial.
The renowned AES has always been a concept I knew vaguely, but I didn’t understand its details well and often just skimmed over it. Recently, due to circumstances, I reluctantly started to delve into it… After learning about it, I found it to be another masterpiece of genius, and I can only worship it.
There are often scenes where someone glances at it and immediately claims this is a certain algorithm, leaving me astonished and in admiration. This time, my study involved the underlying principles, which is a step forward for me; I usually first look at the code, get a rough idea, and then return to the theoretical aspects to clarify the parts I don’t understand in the code, which works well.
The following text will start with an introduction and then move on to the code; I know everyone is eager to understand something, so I will omit all irrelevant and distracting parts.
1. Terms in the AES Algorithm
1. Concept: The AES encryption/decryption algorithm is a reversible symmetric encryption algorithm that uses the same key for both encryption and decryption or two keys that can be easily derived from each other. It is generally used for server-to-server encryption/decryption of data. It is an advanced encryption standard (AES) established to replace the original DES and 3DES.
2. Essential elements to know
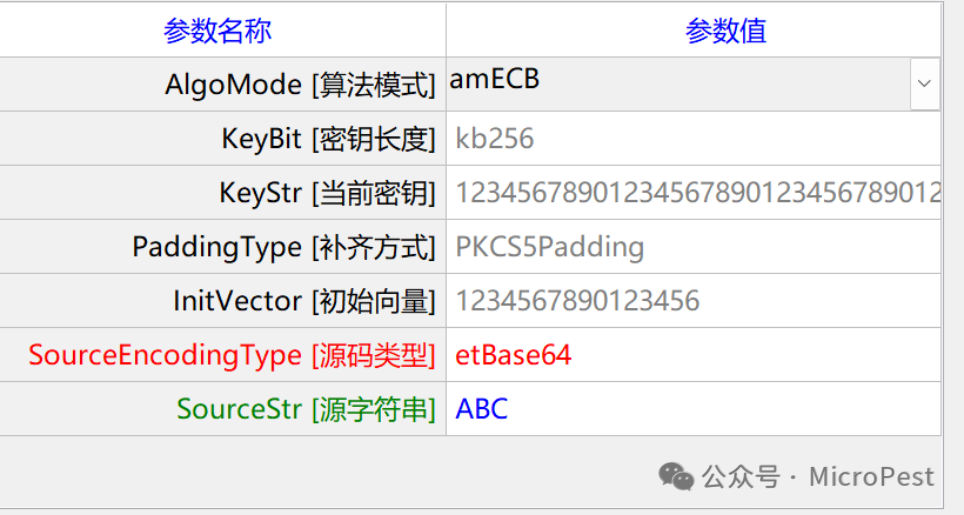
Taking this as an example,
(1) Algorithm modes: Common modes include ECB (Electronic Codebook), CBC (Cipher Block Chaining), CTR (Counter), CFB (Cipher Feedback), OFB (Output Feedback), GCM (Galois/Counter Mode);
(2) Key lengths: Commonly used lengths are 128 bits, 256 bits, and 512 bits;
(3) Padding methods: Common padding methods include PKCS#5/PKCS#7, Zero Padding, ISO Padding, etc.;
(4) IV (Initialization Vector): In AES encryption, the IV is a fixed-length random number used to enhance the security of the password. The main purpose of the IV is to ensure that the same plaintext block produces different ciphertext blocks in different encryption operations. The IV is usually used together with the key and changes with each encryption operation.
Points to note:
(1)AES is a block encryption algorithm, which means it divides data into blocks and encrypts each block; hence the need for padding methods.
(2)Which algorithm modes require padding and initialization vector IV?
A. Electronic Codebook Mode (ECB):
Padding: Yes. Since the ECB mode uses the same key for encrypting each block, identical plaintext blocks will produce identical ciphertext blocks, hence padding is required.
IV: Not applicable, as ECB mode does not use IV.
B. Cipher Block Chaining Mode (CBC):
Padding: Yes. To ensure the consistency of data block sizes, padding is required.
IV: Yes. Each data block uses the previous ciphertext block for XOR operation, and the initial block (IV) is used for the first block’s XOR operation.
C. Counter Mode (CTR):
Padding: Typically not required. The CTR mode treats each block as a counter and does not rely on dependencies between blocks.
IV: Yes. The counter is combined with the key to generate a key stream, which is then XORed with the plaintext.
D. Cipher Feedback Mode (CFB):
Padding: Yes. In CFB mode, part of the previous ciphertext block is fed back into the input of the encryption algorithm, thus requiring padding.
IV: Yes. The initial block (IV) is used for the first block’s XOR operation.
E. Output Feedback Mode (OFB):
Padding: Yes. OFB mode also uses part of the previous ciphertext block as input, hence padding is required.
IV: Yes. The initial block (IV) is used for the first block’s XOR operation.
(3)Output is generally in base64 or hex;
Summary:
Padding methods: CTR/GCM do not require padding;
Initialization vector IV: ECB, CTR/GCM do not require it.
2. Example
1. Let’s take the most commonly used AES-CBC as an example,
We need the following elements: algorithm mode, padding mode, key, key length, IV;
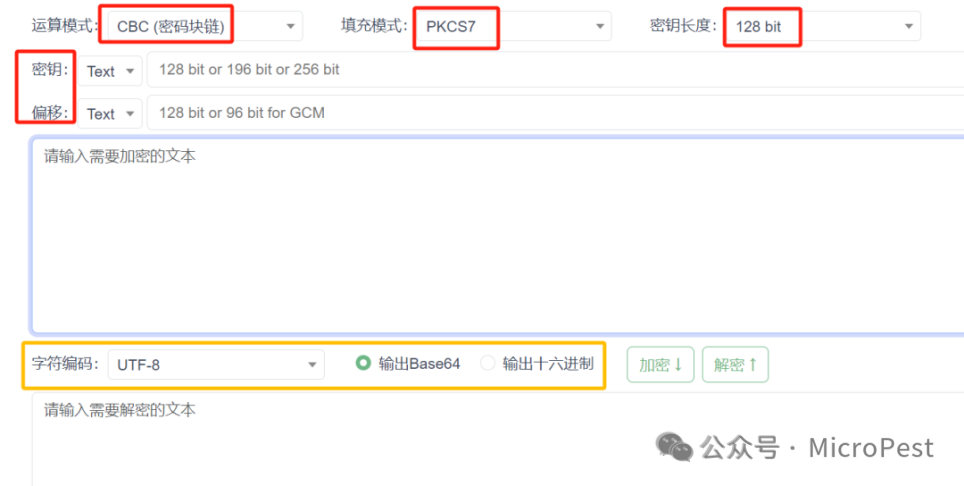
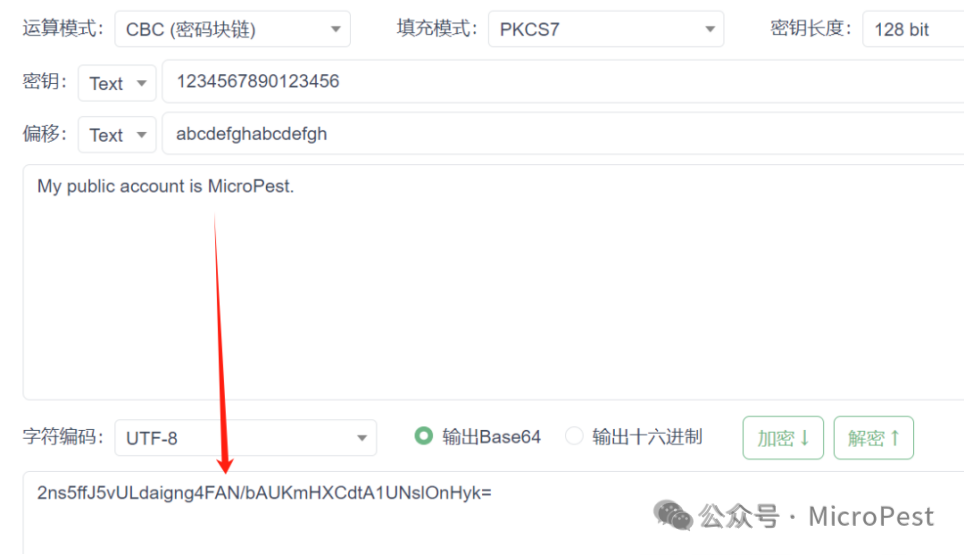
From the above, we can see the red box; let’s fill it in and derive:
2. Code example
There are many such examples; let GPT write a Python one.
from Crypto.Cipher import AES
from Crypto.Random import get_random_bytes
from Crypto.Util.Padding import pad, unpad
def aes_cbc_encrypt(data, key, iv):
"""
Encrypts data using AES-CBC mode.
Args:
data: The data to encrypt.
key: The encryption key.
iv: The initialization vector.
Returns:
The encrypted data.
"""
# Pad the data to a multiple of 16 bytes.
data = pad(data, AES.block_size)
# Create the AES-CBC cipher object.
cipher = AES.new(key, AES.MODE_CBC, iv)
# Encrypt the data.
encrypted_data = cipher.encrypt(data)
return encrypted_data
def aes_cbc_decrypt(encrypted_data, key, iv):
"""
Decrypts data using AES-CBC mode.
Args:
encrypted_data: The encrypted data.
key: The decryption key.
iv: The initialization vector.
Returns:
The decrypted data.
"""
# Create the AES-CBC cipher object.
cipher = AES.new(key, AES.MODE_CBC, iv)
# Decrypt the data.
decrypted_data = cipher.decrypt(encrypted_data)
# Unpad the data.
decrypted_data = unpad(decrypted_data, AES.block_size)
return decrypted_data
if __name__ == "__main__":
# Generate a random AES key and initialization vector.
key = get_random_bytes(16)
iv = get_random_bytes(16)
# Plaintext to encrypt.
plaintext = b"Hello, world!"
# Encrypt the plaintext.
encrypted_data = aes_cbc_encrypt(plaintext, key, iv)
# Decrypt the ciphertext.
decrypted_data = aes_cbc_decrypt(encrypted_data, key, iv)
# Print the decrypted data.
print(decrypted_data.decode("utf-8"))The code is very simple, and I didn’t validate it; it looks fine; however, the code uses random numbers for the key and IV, just replace them with fixed ones.
GPT is an excellent tool; whatever code you want, it can fulfill all, but debugging and validation are necessary; sometimes it may mismatch, like when generating Delphi code, I found errors, but after some modifications, it can work, which is indeed labor-saving.
3. The Underlying Implementation Code of AES
1. The underlying implementation is somewhat complex; the AES encryption process involves several important steps, mainly including the following four steps:
(1)Key Expansion: Generate a series of round keys from the initial key for subsequent rounds.
(2)Initial Round: XOR the plaintext with the first round key.
(3)Main Rounds: Perform a series of iterations based on the number of rounds, each round includes four basic transformations: SubBytes, ShiftRows, MixColumns, and AddRoundKey.
SubBytes: Replace each byte using a fixed substitution box (S-Box).
ShiftRows: Perform circular left shifts on the rows of the matrix.
MixColumns: Perform linear transformations on the columns of the matrix.
AddRoundKey: XOR the round key with the matrix.
(4)Final Round: In the last round, MixColumns is excluded.
The decryption process: The AES decryption process is similar to the encryption process, but the order of transformations is reversed, and inverse operations are used. The main steps include inverse SubBytes, inverse ShiftRows, inverse MixColumns, and inverse AddRoundKey.
You can check Bilibili for clear explanations.
2. Besides theory, I also look at the underlying implementation code; for example, this snippet, the shifting and XOR operations left me bewildered, but when I put it on GPT, it quickly replied: This is the AES-CBC encryption algorithm. 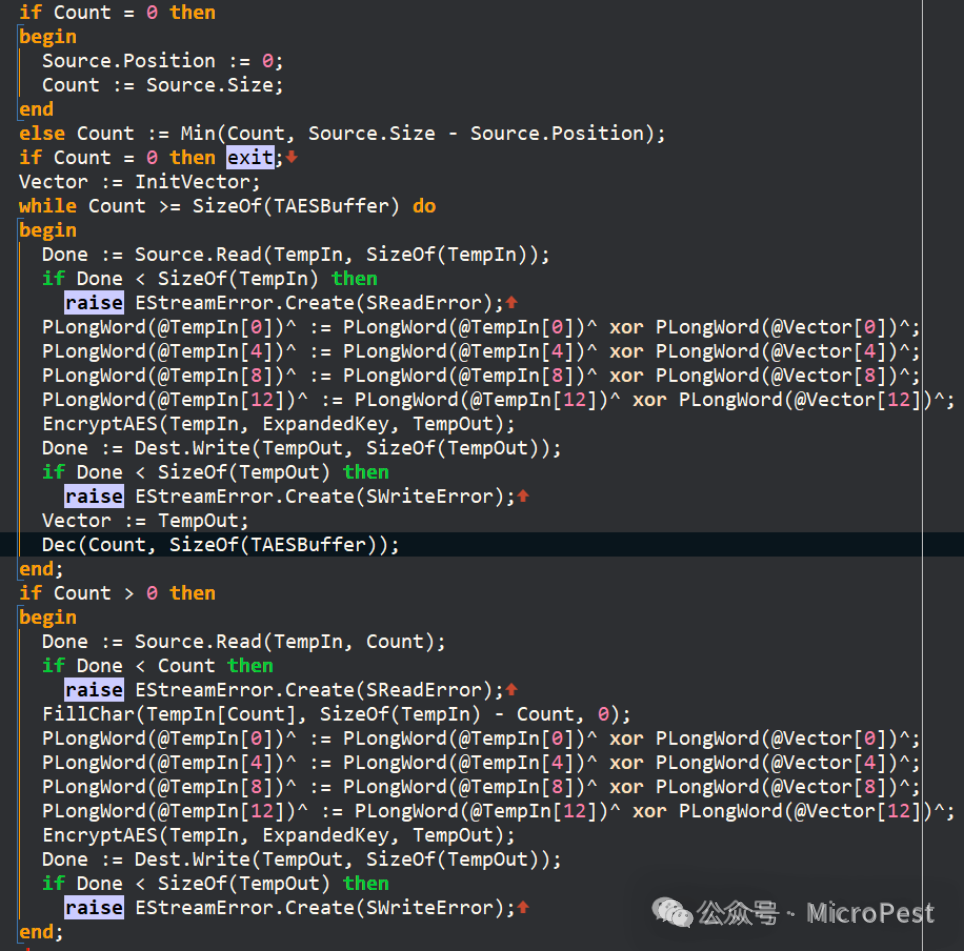
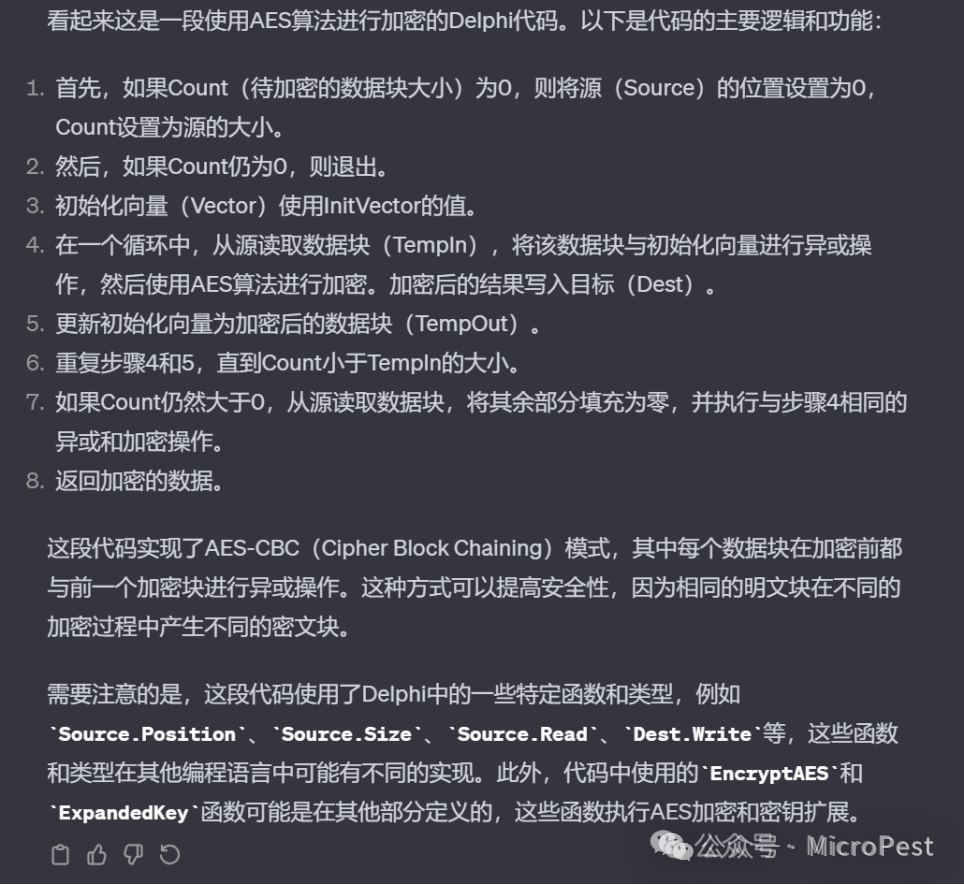
Ah, humanity is being replaced in just a few decades.
Last year, while completing a task assigned by my superior, I reverse-engineered a program and found it used a “Triple DES” encryption algorithm for defense. The AES introduced this time is a more advanced encryption algorithm than DES, and I believe it will appear in hacker programs in the future.