
As a means of security, cryptographic algorithms are closely linked to the lives of most of us. As long as you are online, you will benefit from it, as all websites using https have already employed the encryption protocol TLS/SSL. Therefore, we are all passively enjoying the privacy protection and communication security brought by cryptographic algorithms. Moreover, from a security technology perspective, whether at the network layer or the host file layer, any layer of encryption application or protocol is supported by various cryptographic algorithms.
This article attempts to discuss the evolution of cryptographic algorithms, which are closely related to our online lives, from ancient to modern times, and to elaborate on the key cryptographic algorithms that emerged throughout this process, leading everyone to understand the fascinating algorithms behind them.
The main function of cryptographic algorithms is to convert plaintext into ciphertext to prevent information leakage. The encrypted ciphertext looks a lot like gibberish, but it is not gibberish. Most gibberish is caused by inconsistent encoding, which does not belong to cryptographic algorithms; it merely changes the display format. For example, base64 is merely a form of encoding and cannot guarantee the security of plaintext. If you hear someone say base64 encryption, it indicates that they are not professional.
Cryptographic algorithms need to ensure the following three points:
1. Confidentiality: Ensures that even if data is stolen, the thief does not know what it is.
2. Integrity: Ensures that even if data is intercepted and modified during transmission, the receiver can detect that the information has been intercepted and choose to discard it.
3. Availability: Ensures that the overhead and complexity of the encryption algorithm are within usable limits.
Cryptographic algorithms that meet the above requirements have undergone a long historical development from classical ciphers to modern ciphers.
How Did Ancient People Encrypt?
1. The Earliest Cryptographic Algorithms
Substitution Method
The earliest cryptographic algorithms were mainly used for military purposes, with the earliest record of cryptographic algorithms coming from the “Six Secret Teachings” in the military book of the Zhou Dynasty, which includes the “Yin Fu” and “Yin Shu”. It records:
Taigong said: “The master and the general have secret symbols, a total of eight types. There is a symbol for great victory over the enemy, one foot long. A symbol for capturing generals, nine inches long. A symbol for conquering cities, eight inches long. A symbol for repelling enemies, seven inches long. A symbol for warning the crowd to defend, six inches long. A symbol for requesting food and increasing troops, five inches long. A symbol for defeated troops and lost generals, four inches long. A symbol for lost soldiers, three inches long. All envoys have their travel symbols. If anyone leaks the secret, they shall be executed. The eight symbols are the secret messages of the master and general, so that communication is not leaked to outsiders. Even if the enemy is wise, they cannot recognize them.”
King Wu asked Taigong: “… The symbols cannot be clear; the distance is far, and communication is not possible. What should we do?” Taigong said: “For all major secret matters, one should use writing instead of symbols. The master sends a letter to the general, and the general asks the master by letter. The letters are split into three parts, and it takes three to know one. The split means dividing the letter into three parts. It takes three to know one means that three people hold one part, and they cannot know the content. This is called a secret letter. Even if the enemy is wise, they cannot recognize it.”
In simple terms, the Yin Fu uses eight different lengths of symbols to express different messages and commands, belonging to the substitution method in cryptography, which transforms information into symbols that the enemy cannot understand. This symbolic method can only express the most critical eight meanings. The Yin Shu, as a supplement to the Yin Fu, uses a method of splitting text directly into three parts, sending them through three channels to the target. The enemy can only decipher it if they intercept all three parts simultaneously.
Shift Method
Coincidentally, in the distant West, cryptographic algorithms were also widely used in warfare. In Herodotus’s “Histories,” it is recorded that during the 5th century BC, Greek city-states frequently fought against the Persian Empire, and the Greek city-states widely used the shift method to encrypt military communication information, making it difficult for the Persian Empire to obtain military intelligence and unable to make military deployments in advance. Each segment of text used by the Greek city-states to transmit military information and orders had a fixed number of characters, and the receiver would have a shift instruction. The decryptor would receive the ciphertext and decipher it according to the shift instruction to reveal military orders or messages.
2. The Evolution of Ancient Ciphers: Caesar Cipher
Classical ciphers mainly used the shift and substitution methods. Among them, the shift method involves moving the plaintext a fixed number of positions in a specific direction. For example, “I love you” shifted right by 4 positions becomes “M pszi csy”. Gradually developed and perfected, the most famous is the Caesar cipher. However, the frequency of English or Latin letters is not uniform. For instance, the letter “e” appears more frequently than other letters. After obtaining enough ciphertext samples, the shift rule can be accurately found through frequency analysis, thus cracking the ciphertext. Therefore, most Caesar ciphers use substitution methods to define a plaintext-ciphertext mapping table:
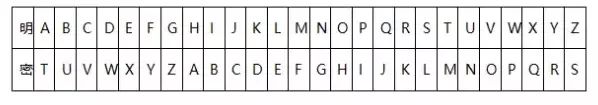
This method can somewhat solve the problem of key exhaustion but is still powerless against frequency attacks with large data volumes. Later, this model developed to introduce specific parameters to disrupt frequency and increase decryption difficulty.
Later developments of classical ciphers produced a series of cipher types such as Vigenère cipher, ROT5/13/18/47, Morse code, etc. However, they are all based on the substitution and shift methods, and their security mainly relies on the algorithms not being disclosed.
More Scientific Encryption Algorithms for Modern People
Classical encryption algorithms essentially change linguistic patterns. Until the mid-20th century, Shannon published “A Mathematical Theory of Communication,” marking the shift of cryptographic algorithms towards applications of mathematics. Thus, three important types of encryption algorithms gradually emerged today: asymmetric encryption, symmetric encryption, and hash algorithms. These three types of algorithms are often used in combination for optimal results.
1. Symmetric Encryption Algorithms
Symmetric encryption algorithms are among the most widely used encryption algorithms. Common ones include DES, AES, 3DES, TDEA, Blowfish, RC5, IDEA, etc. Their characteristic is that both parties use the same key for encryption and decryption. Symmetric encryption can generally be divided into two types: stream encryption and block encryption.
Stream Encryption
Stream encryption is a type of symmetric cipher algorithm that encrypts plaintext character by character. The plaintext and key are aligned bit by bit for the agreed operation to obtain ciphertext. The most famous algorithms in stream encryption are RC4 and GSM, with the simplest model being XOR stream encryption, such as:
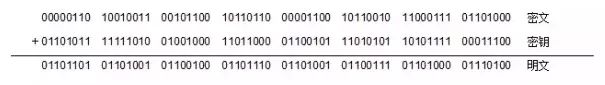
Stream encryption has a simple principle, but its algorithm structure has weaknesses. As long as partial plaintext is leaked, attackers can easily calculate the key. Additionally, since encryption is performed bit by bit, attackers can modify the data without destroying the original data structure, making it difficult for the receiver to detect changes. Although stream encryption is fast and efficient, its security is relatively low, and it is not recommended to use this method for encrypting critical information.
Block Encryption
Block encryption is much more complex internally, with each encryption block undergoing at least 16 rounds of operations. The representative algorithms include DES and AES. Currently, AES is recommended, as DES is no longer secure.
DES
DES is an earlier symmetric encryption standard, primarily divided into three steps: initial permutation, round function, and inverse permutation, and was widely used at the time. As computer performance continues to improve, brute-forcing DES has become increasingly easy. Therefore, DES is no longer secure and has gradually been replaced by 3DES and AES over the past decade.
AES
AES has been widely analyzed and proven, and is currently one of the most secure symmetric encryption algorithms used globally. Over the past decade, AES has become one of the most popular algorithms in symmetric key encryption. Unlike DES, AES uses a substitution-permutation network rather than a Feistel structure.
Most AES computations are completed within a special finite field, and the encryption process operates on a 4×4 byte matrix, known as the “state“, with its initial value being a plaintext block. During encryption, each round of AES encryption cycles (except for the last round) includes four steps:
AddRoundKey——Each byte in the matrix is XORed with the round key; each sub-key is generated by the key generation scheme.
SubBytes——Each byte is replaced with a corresponding byte using a non-linear substitution function and lookup table.
ShiftRows——Each row of the matrix is cyclically shifted.
MixColumns——Fully mixes the operations of each column in the matrix, using linear transformations to mix the four bytes of each column. The MixColumns step is omitted in the last encryption cycle, replaced by another AddRoundKey.
Encryption Modes
AES and DES both support different encryption modes internally, each with varying security and efficiency. Among the two most common modes, ECB and CBC, ECB mode has high encryption efficiency but low security, as shown in the figure below:
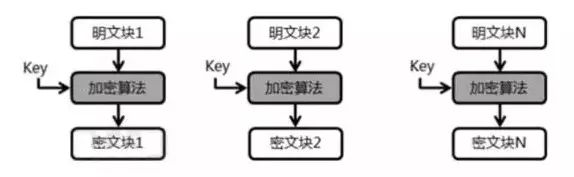
Each time, the key encrypts individual blocks, making it easy for the opponent to crack. However, since there is no correlation between the modules, parallel computation is possible, greatly improving encryption efficiency. Typically, the encryption efficiency of ECB is 5-6 times higher than that of CBC. However, CBC is much more secure than ECB. The mode is shown in the figure below:
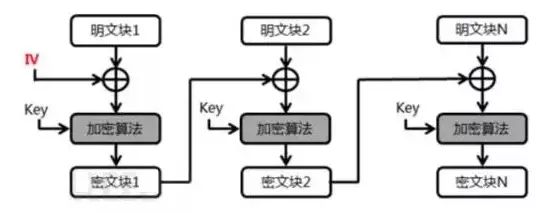
Each block of encryption introduces a different IV, requiring the previous block for iteration to complete the entire encryption process. Since each block’s IV is related to the ciphertext block, concurrent processing cannot be used, and the entire process must be serial. Unless there is an extremely high performance requirement, it is recommended to use the more secure and reliable CBC mode.
2. Asymmetric Encryption Algorithms
The main difference between asymmetric encryption algorithms and symmetric encryption algorithms is that the encryption key and decryption key are no longer the same. This method is primarily designed to address the “multiple encryptors, one decryptor” model. Thus, in this many-to-one relationship, a public key system emerges. One public key corresponds to one private key. The public key is public, and any data sender encrypts data using the public key, but only the private key can decrypt the content encrypted with the public key. The underlying mathematical principles range from large number factorization to complex discrete logarithm problems on elliptic curves, making them very complex. Common asymmetric encryption algorithms include DSA, RSA, Elgamal, knapsack algorithm, Rabin algorithm, D-H algorithm, ECC algorithm, etc. The execution efficiency of asymmetric encryption algorithms limits their practical application, so most are used in identity verification and not in communication.
3. Hash Algorithms
Hash algorithms are also very common encryption algorithms. They are not used for data transmission but for verifying whether data has been tampered with, preventing malicious individuals from altering data. Their characteristic is that regardless of the original text’s length, they will become a fixed-length string, and they can only encrypt but not decrypt (only one-way operation). Common hash algorithms include MD5, SHA-1, and SHA 224/256/512, etc. The first two have been proven to be no longer secure, and it is recommended to use more secure algorithms such as SHA 256/512.
The above encryption algorithms have been widely applied in various fields.
Database Encryption Algorithms
With the rapid development of cloud and big data, databases are gradually migrating from secure local area network environments to private and even public clouds. As databases move to the cloud, they face more severe security challenges. Databases store critical data, and cloud hosts have many security risks, so cloud database encryption becomes a remedy for security hazards.
Symmetric Encryption Algorithms
Unlike file encryption and communication encryption, database encryption requires special attention to whether encryption algorithms have expansion properties and has stringent performance requirements for encryption algorithms. In 2009, Anhua Jinhui excluded stream encryption algorithms from symmetric algorithms when developing database encryption products, because although this algorithm has natural advantages in operational efficiency and addressing data expansion, it has certain security issues in certain situations.
To pursue encryption efficiency, some domestic security vendors still adopt this method, but the most basic security requirements are overlooked. A more prudent approach is to use block encryption (AES) from symmetric encryption for related encryption processing. Block encryption has high security and is relatively assured in terms of safety, but it needs to address the expansion issues caused by data block size limitations. This requires a sufficiently ingenious usage plan based on specific conditions or field designs to address expansion issues for different fields or types, ultimately forming a perfect database encryption plan.
Domestic Cryptographic Algorithms
Cryptographic algorithms are core technologies for ensuring information security and play a crucial role in protecting national secrets and core data across various industries. Using internationally recognized cryptographic algorithm systems such as 3DES, SHA-1, RSA, etc., poses significant security risks. Therefore, relevant national authorities and regulatory bodies have proposed the promotion of domestic cryptographic algorithm application implementation and strengthening industry security control from the perspective of national security and long-term strategy. Currently, many domestic database encryption products face user selection evaluations, with a significant portion prioritizing support for domestic cryptographic algorithms, which is very important for government, military, and confidentiality-related industry users. Ensuring national information security must break away from excessive reliance on foreign technologies and products, and cryptographic algorithms, as key security technologies, should be domesticated.
Specifically, domestic cryptographic algorithms refer to commercially available cryptographic algorithms recognized by the National Cryptography Administration. For example, in the financial sector, the publicly used SM2, SM3, and SM4 algorithms are currently the main ones. Taking SM4 as an example: SM4 is a block cipher algorithm independently designed in China for implementing data encryption/decryption operations to ensure data and information confidentiality. The basic condition to ensure the security of a symmetric cipher algorithm is that it has sufficient key length, and the SM4 algorithm has the same key length and block length of 128 bits as the AES algorithm, therefore, it is more secure than the 3DES algorithm.
Recommended Articles
< Swipe left or right to view related articles >





Click the image, enter the article ID, or scan the QR code to go directly