(Click the public account above to follow quickly)
Author: Bole Online Column Author – Zhijun
Link: http://blog.jobbole.com/107930/
Cryptography is widely used in computer science, and HTTPS is a secure communication protocol based on cryptography. HTTPS was first proposed by Netscape in 1994, and now, with the promotion by many Internet companies, HTTPS has been widely used on various websites of all sizes. Before fully understanding HTTPS, it is necessary to clarify some cryptographic concepts, such as: plaintext, ciphertext, cipher, key, symmetric encryption, asymmetric encryption, hash, digital signature, and digital certificate.
Cipher
The term cipher in cryptography is different from the password we use in daily life. In computer terminology, ‘cipher’ is an algorithm used for encryption or decryption, while ‘password’ is a set of text strings used for authentication. Here, we will discuss the former: cipher.
Key
A key is a parameter input during the encryption process using a cipher algorithm. The same plaintext calculated under the same cipher algorithm with different keys will produce different ciphertexts. Many well-known cipher algorithms are public, and the key is the important parameter that determines whether the ciphertext is secure. Generally, the longer the key, the harder it is to crack. For example, an 8-bit key has a maximum of 256 combinations, which can be easily cracked using brute force. The well-known DES algorithm uses a 56-bit key, which is no longer considered a secure encryption algorithm mainly because 56 bits is too short and can be cracked within hours. Keys can be categorized into symmetric keys and asymmetric keys.
Plaintext/Ciphertext
Plaintext is the original data before encryption, while ciphertext is the result obtained after the cipher operation.
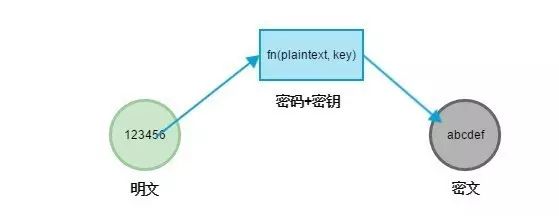
Symmetric Key
A symmetric key (symmetric-key algorithm) is also known as shared key encryption. The same key is used for both encryption and decryption. Common symmetric encryption algorithms include DES, 3DES, AES, RC5, and RC6. The advantage of symmetric keys is their fast computation speed, but they also have drawbacks. The keys need to be shared between the two ends of communication; both parties must know the key in order to decrypt correctly. If all clients share the same key, then this key acts like a master key that can decrypt everyone’s ciphertext. If each client and server maintains a separate key, then the server must manage thousands of keys, which can be a nightmare. Below is a simple symmetric encryption example that encodes plaintext into ASCII.
# Encryption method: based on ASCII + key value
def encipher(plain_text, key):
# Encrypt
cipher_text = []
for c in plain_text:
cipher_text.append(str(ord(c) + key))
return ' '.join(cipher_text)
def decipher(cipher_text, key):
# Decrypt
plain_text = []
for c in cipher_text.split(" "):
plain_text.append(chr(int(c)+key))
return "".join(plain_text)
if __name__ == '__main__':
print "cipher_text:", encipher("abcdef", 0)
print "plain_text:", decipher("97 98 99 100 101 102", 0)
Asymmetric Key
An asymmetric key (public-key cryptography), also known as public key encryption, involves the server generating a pair of keys: one private key kept on the server that only it knows, and one public key that can be freely distributed for anyone to use. The client’s plaintext is encrypted using the public key, and the ciphertext needs to be decrypted using the private key. In this process, different keys are used for encryption and decryption, which is why it is called asymmetric encryption. Compared to symmetric key encryption, asymmetric encryption does not require sharing keys between client and server; as long as the private key is not given to any user, even if the public key is intercepted online, it cannot be decrypted. A stolen public key is of no use. Common asymmetric encryption methods include RSA, and the process of asymmetric encryption and decryption is as follows:
The server generates a pair of public and private keys.
The private key is kept on the server, and the public key is sent to the client.
The client uses the public key to encrypt plaintext and transmits it to the server.
The server uses the private key to decrypt the ciphertext to obtain the plaintext.
Digital Signature
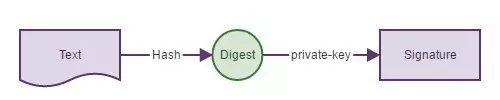
Data transmitted between the browser and the server may be intercepted and altered by impostors. How can we ensure that the data is genuinely sent from the server and not tampered with? To address these two issues, we must use digital signatures. A digital signature is like a signature in daily life; once you sign a contract, it legally confirms that you signed it, which cannot be forged because it is your unique handwriting. So, what is a digital signature in computing? A digital signature is used to verify that the transmitted content is indeed sent by the server and that the data has not been altered. It serves these two purposes and is an application scenario of asymmetric encryption.However, it uses the private key for encryption and the corresponding public key for decryption.
First Step:The server processes the message through hashing to generate a digest. The digest is encrypted with the private key to generate the signature, which the server sends along with the message to the client.
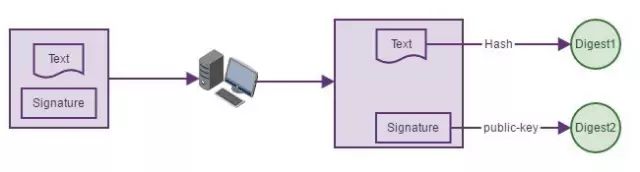
Second Step: After the client receives the data, it extracts the signature and decrypts it using the public key. If it successfully decrypts Digest2, it confirms that the message is from the sender.
Third Step: The client extracts the message text and performs the same hashing process to obtain Digest1, which is then compared to the previously decrypted Digest2. If they are equal, it indicates that the content has not been tampered with; otherwise, it has been altered. This is because even a slight change in the text will produce a completely different hash.
Digital Certificate
A digital certificate (CA) is a recognition credential issued by an authority to a website. This credential is recognized by everyone (browsers). Why do we need a digital certificate? Is a digital signature not secure enough? There is a situation where the browser cannot determine whether all real servers are indeed genuine. For example, if a manufacturer installs a lock for you and gives you the key, as long as the key opens the lock, you can confirm that the key and lock match. However, if someone replaces the key or lock, you cannot open the door, and you know it has been tampered with. But if someone changes both the lock and key to a similar-looking but much lower quality set, even though the key and lock fit, you cannot confirm whether it is indeed from the manufacturer. In this case, you can ask a quality inspection department to verify whether the lock truly comes from the manufacturer; the quality inspection department is an authority, and its word is recognized by the public.
Similarly, if someone (Zhang San) replaces the public key sent by the real server to the browser with their own public key, Zhang San can use their own private key to perform the same steps on the text hash and digital signature, resulting in no issues. However, what the browser sees is not the real server’s data but what Zhang San has altered (from public key to private key). So, how can we ensure that the public key you are using is genuinely sent by the real server? We use digital certificates to solve this problem. Digital certificates are generally issued by a Certificate Authority (CA), and the certificate contains the real server’s public key and other information about the website. The certificate authority encrypts it with its private key and sends it to the browser. The browser uses the certificate authority’s public key to decrypt it and obtain the real server’s public key. This process relies on the public recognition of the certificate authority to ensure the security of the public key.
Follow ‘Algorithm Enthusiasts’
See more selected algorithm technology articles
↓↓↓
