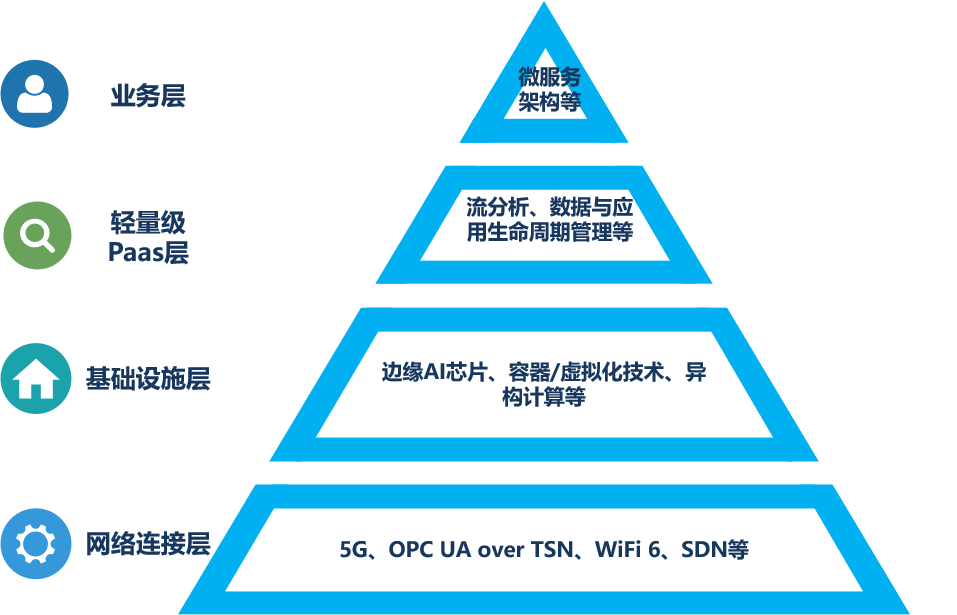
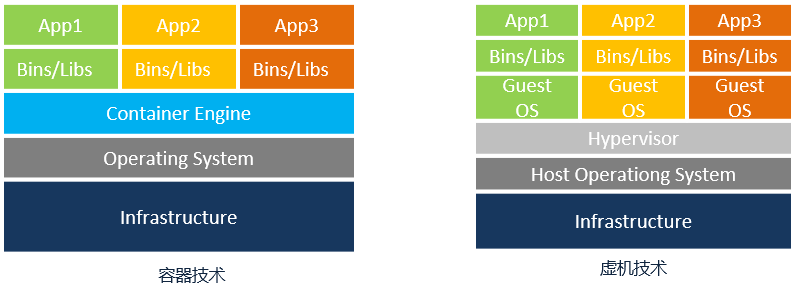
Author Bio
Xu Muhong, Master of Engineering, Senior Engineer at the TIER Terminal Laboratory of the China Academy of Information and Communications Technology, mainly engaged in research on new technologies for intelligent terminals.
Contact:xumuhong@caict.ac.cn
Recommended Reading
