Introduction
Abstract
Edge computing, as a new computing paradigm following cloud computing, processes part of the data at the terminal, bringing computation closer to users and data sources at the network edge. This effectively avoids problems such as data latency, high data centralization, and network jitter. The unique advantages of low latency, mobility, and cost-effectiveness have led to an increasing number of applications in edge computing, promoting the innovative development of traditional technologies and businesses, with large-scale applications in various valuable industries such as electricity, transportation, manufacturing, and smart cities. However, the security threats faced by edge computing are also increasing, and edge security issues have become one of the obstacles restricting the development of the edge computing industry.

1
Introduction to Edge Computing
Edge computing refers to the technology that allows computation on downlink data from the cloud and uplink data from IoT terminal devices at the network edge, where the “edge” can be defined as the computing or network resources between the terminal data source and the cloud data center. Edge computing attempts to process data at the edge so that data does not have to be fully sent to the cloud for processing, thereby reducing bandwidth pressure and latency. The computing power in the cloud is generally superior to that of edge devices, which has proven to be an effective data processing method in past practices. However, compared to the rapidly growing speed of data generation, the bandwidth and data transmission speed of the network have basically stagnated, gradually becoming a bottleneck in the development of cloud computing. Traditional centralized big data processing models based on the cloud are limited by the physical distance between cloud servers and terminal devices, facing issues such as latency, bandwidth, and energy consumption, making it difficult to cope with emerging application scenarios.
The core idea of edge computing is “to provide reliable and stable services close to users,” processing and storing data at the network edge near user terminal devices. Edge servers provide services directly to ensure low latency; data processing no longer requires uploading all data to the cloud, alleviating bandwidth pressure; widely distributed edge servers share the data processing tasks, reducing energy consumption of central cloud servers. Therefore, edge computing features distributed architecture, low latency, and high computational efficiency.
2
Application Status
With its unique advantages, edge computing has gained attention from academia and government agencies and is transitioning from design concepts to industrial practice. Industries with high real-time interactive demands, sensitivity to network latency and jitter, and high security requirements, represented by electricity, transportation, manufacturing, and smart cities, are gradually becoming the main stage for edge computing. For example, in smart cities, a large amount of data is generated continuously, and many real-time services need to be provided. Edge computing, with its efficient distributed data processing capabilities, has become the technical foundation for smart city construction. Intelligent traffic control systems can be run on edge servers to obtain and analyze real-time information about road traffic flow and incidents, and make decisions on traffic signal settings to alleviate vehicle congestion, thus achieving smart transportation. With the help of edge computing, special places like residential areas or construction sites can implement camera monitoring for people and vehicles, with edge servers analyzing the data to complete tasks such as alerts for unauthorized personnel and dangerous situations.
To enable edge computing to have a universal architecture applicable to more fields, relevant enterprises, industrial organizations, and academic institutions both domestically and internationally are exploring edge computing architectures. In 2016, the Edge Computing Industry Consortium (ECC) proposed the Edge Computing Reference Architecture 3.0, which consists of three layers, each with modeled open interfaces for full-layer openness. The edge layer is located between the cloud and the on-site device layer, supporting the access of on-site devices downward and connecting with the cloud upward. The edge layer includes two main components: edge nodes and edge managers. Edge nodes are the hardware entities that carry edge computing services, while edge managers are the software that manages and schedules edge nodes uniformly. Three end-to-end intelligent services are set up vertically, where security services take into account the unique characteristics of edge application scenarios, and the protection strategies consider various protective measures from the physical layer to the application layer for multi-layer security protection. In 2017, the Linux Foundation also launched the open-source project EdgeX Foundry, aimed at creating a standardized universal framework for IoT edge computing. As shown in Figure 2, EdgeX Foundry can be divided into four service layers and two foundational system services, including core service layer, supporting service layer, export service layer, and device service layer.
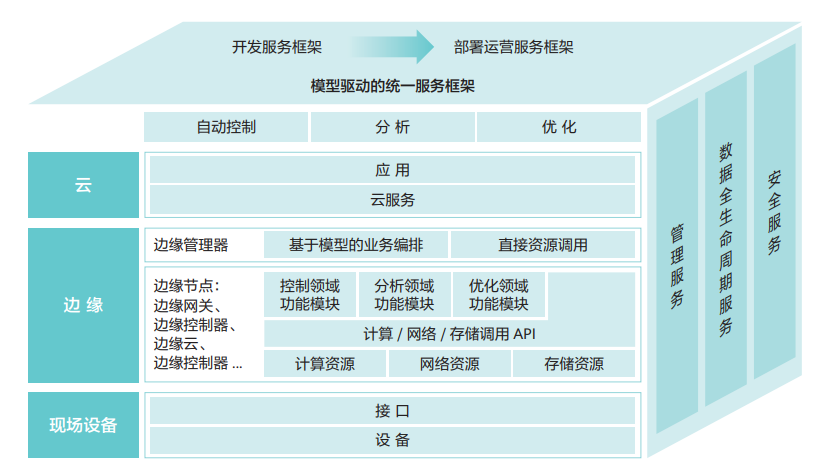
Figure 1: The Edge Computing Reference Architecture 3.0 proposed by ECC
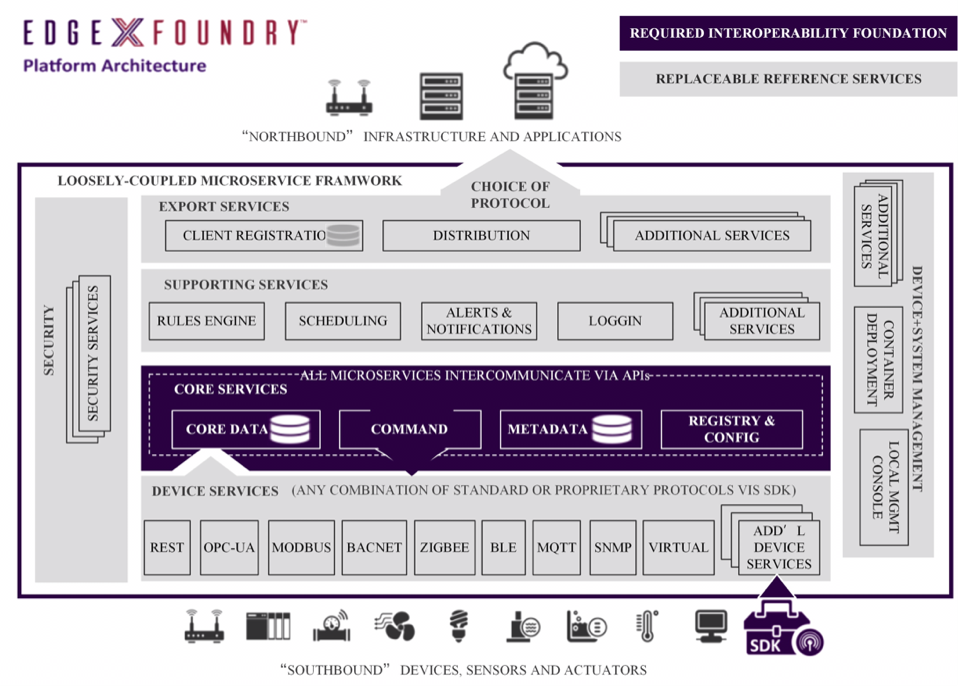
Figure 2: EdgeX Foundry Architecture
3
Security Threats in Edge Computing
4
Conclusion
References
[1] Shi W, Cao J, Zhang Q, et al. Edge Computing: Vision and Challenges[J]. IEEE Internet of Things Journal, 2016, 3(05):637~646.
[2] Li Xiaowei, Chen Benhui, Yang Dengqi, et al. A Review of Security Protocols in Edge Computing Environments[J]. Computer Research and Development, 2022(059-004).
[3] Edge Computing Industry Consortium. Edge Computing Security White Paper[EB/OL]. [2019-11]. www.ecconsortium.org/Uploads/file/20191126/1574772963483806.pdf.
[4] Yang Dequan. Security Threats and Defenses in Edge Computing[J]. Automation Expo, 2022, 39(2):3.
[5] Roman R, Lopez J, Mambo M. Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats and Challenges[J]. Future Generation Computer Systems, 2016, 78(PT.2):680-698.
[6] Yahuza M, Idris M, Wahab A, et al. Systematic Review on Security and Privacy Requirements in Edge Computing: State of the Art and Future Research Opportunities[J]. IEEE Access, 2020, PP(99):1-1.
[7] Zheng Fengbin, Zhu Dongwei, Zang Wenqian, et al. Edge Computing: A Review of New Computing Paradigms and Application Research[J]. Computer Science and Exploration, 2020, 14(4):13.
[8] Cao Ziwen. Edge Computing: Framework and Security[J]. Confidential Science and Technology, 2019(9):5.
[9] Liu Yunyi, Zhang Jianmin, Feng Xiaoli. Security Capability Deployment Scheme for 5G Edge Computing Systems[J/OL]. Telecom Science. https://kns.cnki.net/kcms/detail/11.2103.tn.20220614.1655.002.html
[10] Fu Wenjun, Mao Xiongfei, Yu Haisheng, Ke Bin, Zhang Su. Analysis of the Current Situation and Direction of 5G Edge Computing Technology[J]. China Instrumentation, 2021(06):80-82.
[11] Zhao Ming. Overview of Edge Computing Technology and Applications[J]. Computer Science, 2020, 47(S1):268-272+282.
[12] EdgeX Foundry. EdgeX Foundry documentation[OL]. https://www.edgexfoundry.org.
China Confidentiality Association
Science and Technology Branch
Scan to follow us

Author: Wang Jiawen
Editor: Xiang Lingzi
Top 5 Highlights of 2021
Insights on Paper Recovery Technology’s Importance for Carrier Destruction
Recent Highlights Review
Introduction to Software Security Entity Relationship Prediction
Introduction to Network Security Incident Analysis