Source: On August 6, 2022, the Global Edge Computing Conference in Shenzhen, organized by the Edge Computing Community, concluded successfully. At the conference, Wang Jie, Executive Director of Kenting (Guangzhou) Law Firm, was invited to give a speech titled “Edge Computing – Seven Major Data Compliance Challenges in IoT Scenarios.”
Speaker: Wang Jie, Executive Director of Kenting (Guangzhou) Law Firm
Edited by: Xiamen University Volunteer Mutual Aid Group
Produced by: Edge Computing Community


1►
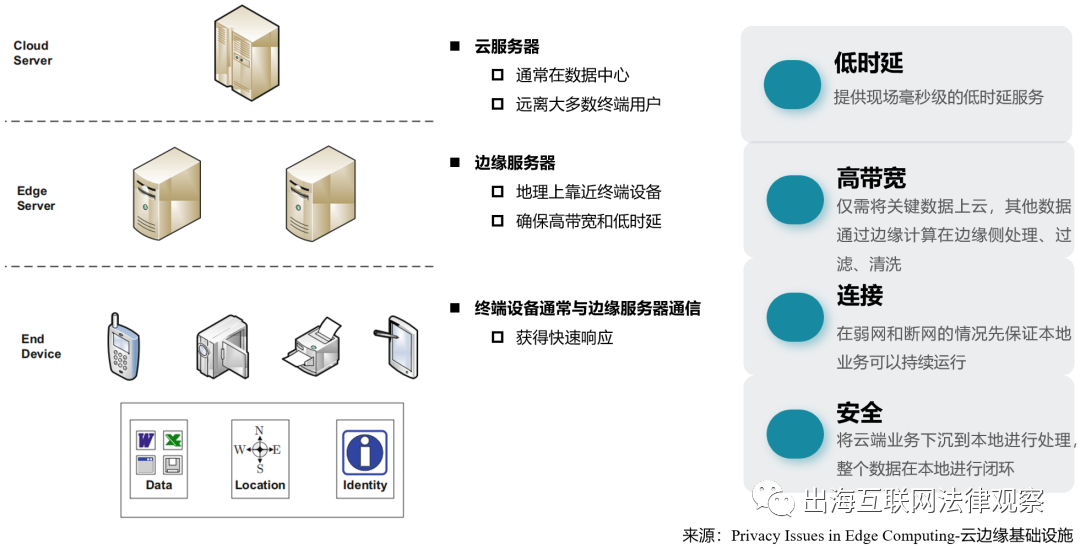
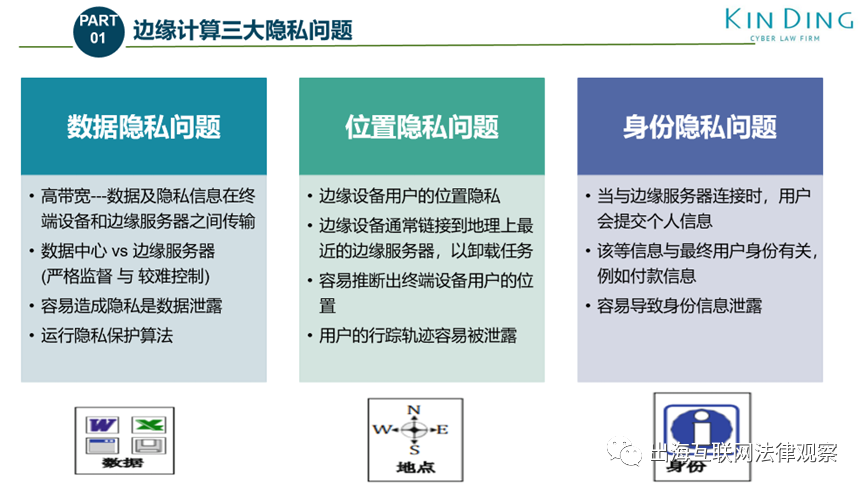
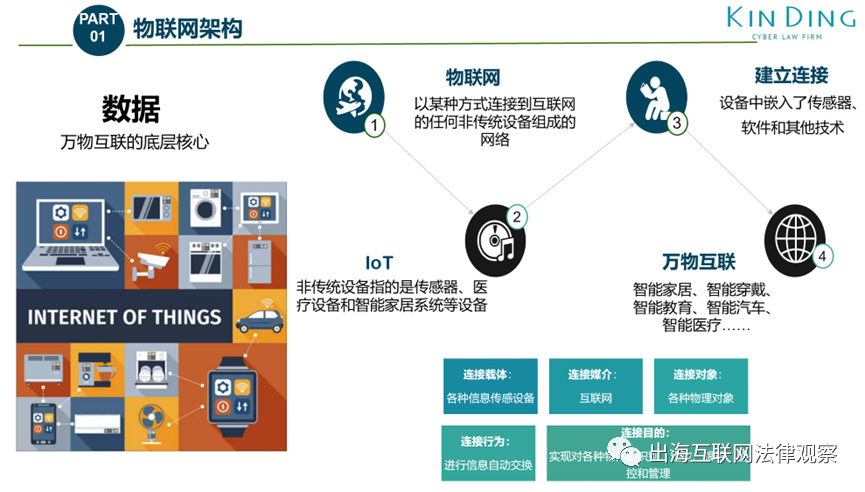
Privacy Issues in Edge Computing and IoT
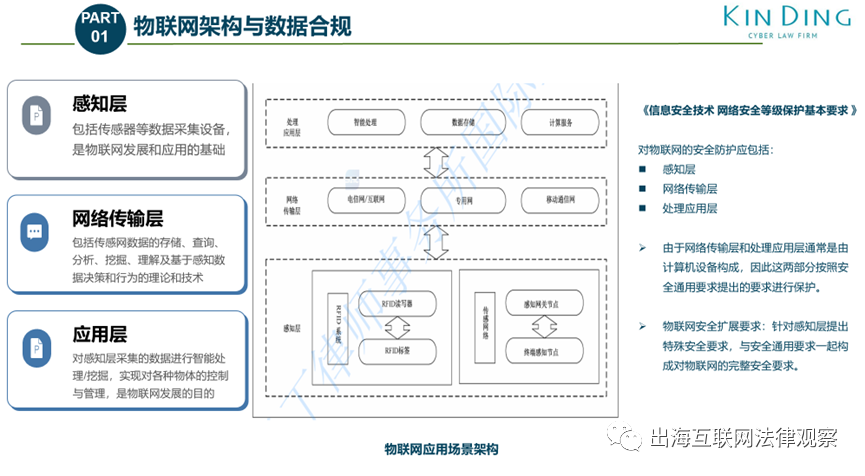
2►
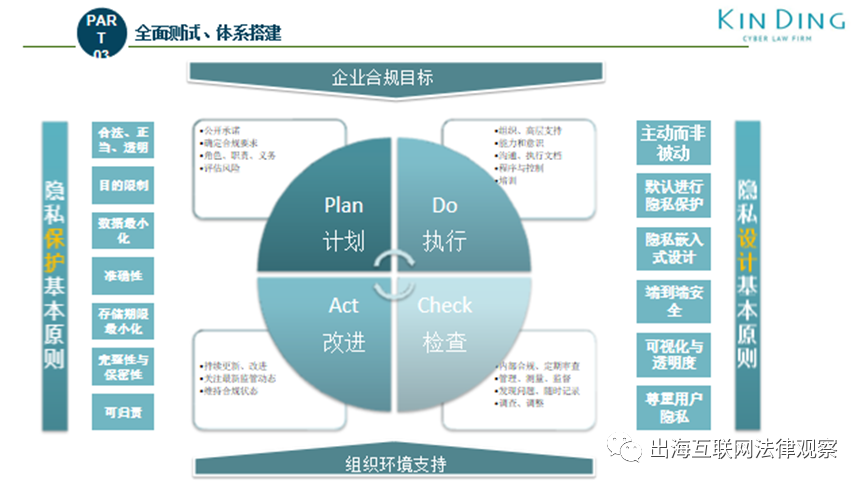
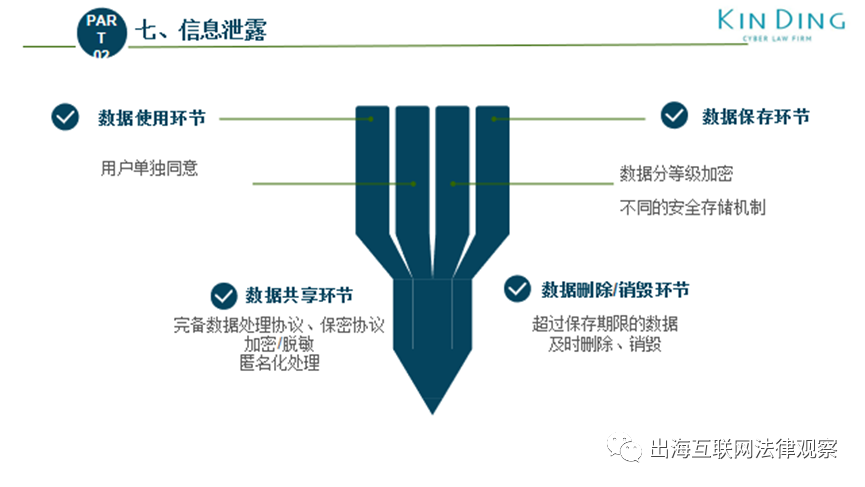
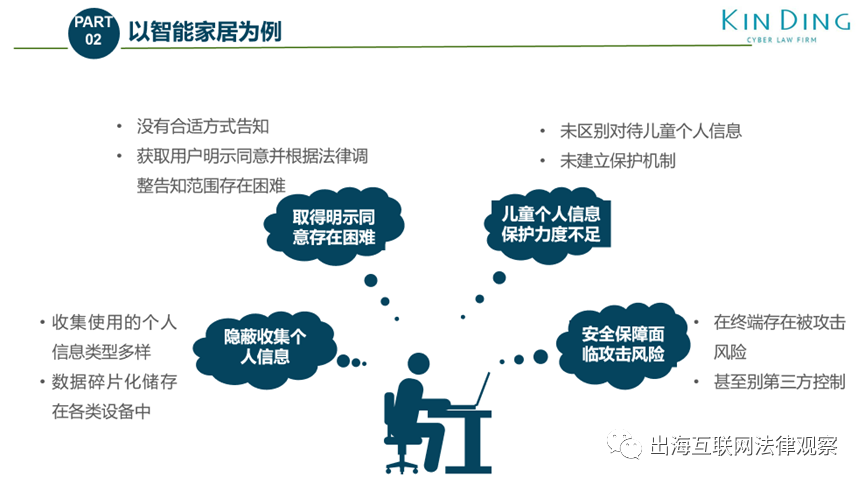
Seven Major Data Compliance Challenges in IoT Scenarios

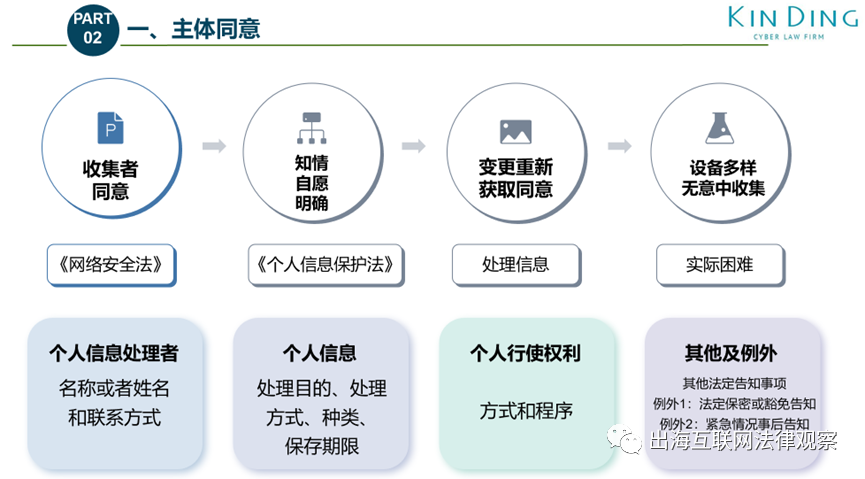
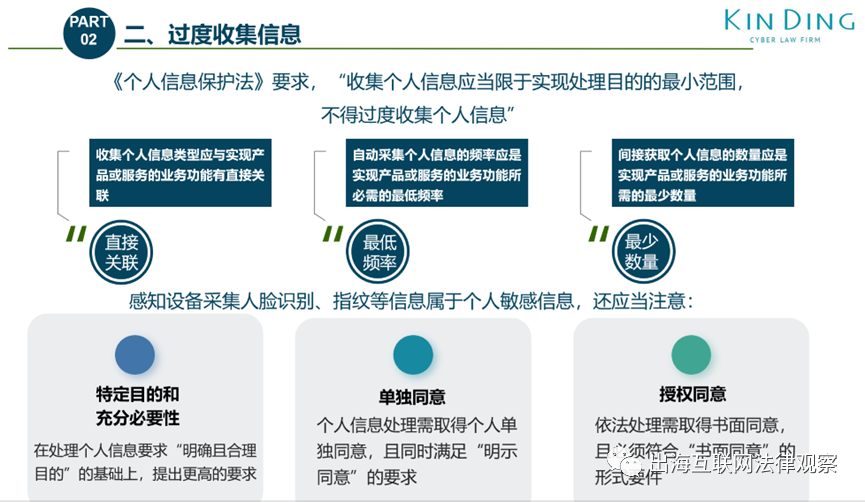
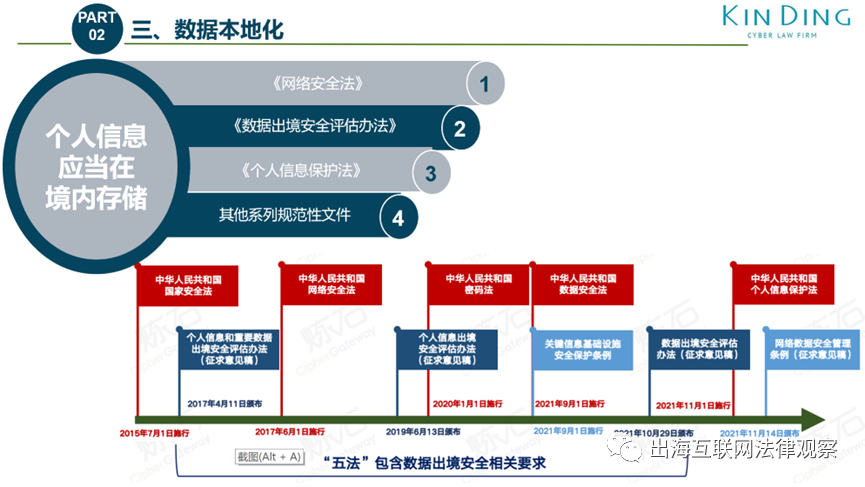
3►
How to Achieve Data Compliance in IoT