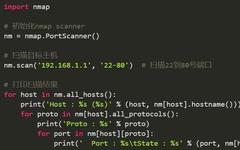
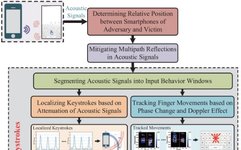
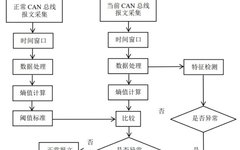
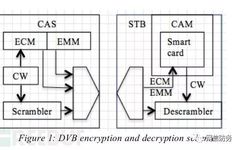
Why Python Is the Favorite Programming Language for Cybersecurity Professionals
Python was designed and developed by Guido van Rossum 35 years ago and has become one of the most widely used high-level programming languages. It is characterized by its simplicity, ease of use, a thriving ecosystem, and versatility. In the cybersecurity industry, Python’s application is also very extensive, making it a fundamental skill that cybersecurity … Read more