From June 5 to 7, 2023, the Gartner Security and Risk Management Summit was held in the United States. As the most important cybersecurity event hosted by Gartner, this conference featured 71 analysts from Gartner taking the stage and 240 companies exhibiting. Key analysts in the field of Gartner SIEM and SOC were present to share their insights on the future of SIEM and SOC development.
The Life and Death of SIEM
The Life and Death of SIEM
Can SIEM meet the rapidly changing security demands? Is SIEM already overwhelmed? Will SIEM face extinction in the face of emerging technologies and products?
Throughout its more than twenty years of development, SIEM products have faced similar doubts multiple times, but never before have they faced such enormous challenges as in the past two years. In his speech titled “Security Operations Outlook 2023,” Gartner analyst Eric Ahlm compared the challenges posed by new technologies and products (especially XDR) to a cataclysmic collision.

Will SIEM be destroyed? Or will it be reborn after the impact? Eric Ahlm stated, “The good news is that this is not a SIEM extinction event, but it is time to reassess the value of SIEM in SOC.”
Gartner VP analyst Pete Shoard, in his speech titled “The Future of SIEM and the Evolution of TDIR,” showcased several points in time where SIEM was deemed ‘dead’.He firmly believes that SIEM will continue to thrive!

Gartner researchers believe that SIEM as a niche market and term will not disappear, but the connotation and extension of SIEM are no longer what they used to be, which precisely reflects SIEM’s unique ability to keep pace with the times.
Redefining and Positioning SIEM
Redefining and Positioning SIEM
During the conference, Pete Shoard provided the latest definition of SIEM: The SIEM platform offers a configurable security logging system that helps organizations identify and report events of interest that require investigation. It also assists organizations in verifying and responding to discovered issues that may cause damage.
Pete Shoard mentioned that this will be updated in this year’s SIEM Magic Quadrant report. In comparison, the 2022 Magic Quadrant report defined SIEM as follows: SIEM aggregates event data from various monitoring, assessment, detection, and response systems across applications, networks, endpoints, and cloud environments to achieve threat detection based on correlation rules and UEBA, response integration based on SOAR, and continuous updates of threat content based on TIP along with security reporting.

It can be seen that the previous definition of SIEM provided a more detailed description of its functions, while the new definition succinctly summarizes three key capabilities: investigation, verification, and response, with a richer connotation than before.
Further analysis shows that the core of the SIEM definition over the years has always been data collection and analysis, that is, data-centric. From a technical architecture perspective, data-driven security is not a bad thing. However, as Gartner states, the current reality indicates that after years of the big data era, more data does not mean more security value, and the marginal utility of data is diminishing. At the same time, more and more products capable of detection and response are emerging in the market. In other words, detection and response capabilities are increasingly dispersed across different security systems. Therefore, for users, while the issue of data dispersion still exists, its importance is declining, while the dispersion of security systems (especially security detection and response systems) is becoming more pronounced. This requires SIEM platforms to significantly enhance their integration capabilities with heterogeneous security systems (which Gartner refers to as Compatibility) while maintaining a big data analysis architecture, and this is precisely the reason for the emergence of the Cybersecurity Mesh Architecture. In summary, the extension of SIEM has expanded from data integration to system integration.
Since SIEM has been redefined, can the newly defined SIEM be referred to as Next-Generation SIEM (NG-SIEM) or SIEM X.0? Regarding this, Gartner’s stance is also clear.Pete Shoard stated that those who cannot learn from history are the ones who will keep inventing the so-called next-generation SIEM.SIEM is SIEM; it will not be replaced, nor will it become NG-SIEM.The evolution of SIEM’s definition is an inherent characteristic of SIEM, which has always been defined as highly extensible, capable of evolving with the changing security landscape.The definition of SIEM will continue to change in the future.

In my opinion, this continuously evolving definition of SIEM is precisely its advantage, as SIEM represents a top-down systemic security operation construction demand.
Why has SIEM been able to survive amidst the competition from various products focused on detection and response, such as XDR? Setting aside the increasingly declining compliance functions in the SIEM domain [Note: In fact, these functions are increasingly shifting towards GRC compliance management centers], Gartner believes the key lies in SIEM’s openness. From the user side, at a certain stage of development, there is an inevitable need for a security platform that integrates global network security monitoring and response, closely tied to the user’s own business reality, and this security platform must have a high degree of openness, including configurability and customizability, which is precisely what SIEM strives for. In this sense, XDR and other specialized DR products can collaborate with SIEM.
It can be said that openness reflects the uniqueness that distinguishes SIEM from other products, and also reflects SIEM’s core positioning, which is to serve customers with customization needs. SIEM products certainly do not only serve customers with customization needs. According to Gartner’s 2022 “Key Capabilities of SIEM” report, SIEM use cases also include out-of-the-box SIEM and using it as a TDIR platform. For SIEM, the market truly under pressure is that covered by out-of-the-box SIEM use cases.
Everything has two sides. The other side of SIEM’s openness is its high complexity, along with the long-standing criticism of SIEM’s practical implementation capabilities. Essentially, SIEM is a product designed to meet complex security needs (integrating ever-changing heterogeneous data and systems to achieve global monitoring and response), and it is bound to be complex. However, from the perspective of products and solutions, we can transfer the complexity of SIEM, as much as possible, from the user side to the vendor side. Note that we are talking about transfer, not elimination! This transfer can manifest as SIEM products containing rich security content (including policies, rules, report templates, algorithm models, etc.), providing smoother interactive design and analyst experience, offering rich product add-on services (which Gartner refers to as VDSW—Vendor Delivered Service Wrap), or providing managed security services. These are all good practices to reduce the complexity of implementing SIEM for users, essentially shifting more of the implementation complexity of SIEM to vendors, packaging this complexity work into transferable knowledge (including user-friendly UI, rich security content, experienced service personnel, etc.) to provide to customers.
Three Development Trends of SIEM
Three Development Trends of SIEM
Pete Shoard introduced three future development trends of SIEM at the conference:
1) Storage will shift from a federated to a distributed model; 2) With the prosperity of the community, the security content market will gradually grow;
3) New event-based use cases will emerge.
Regarding the first point, Gartner believes that SIEM will develop from the currently popular federated big data analysis architecture towards a more complete functionally decentralized distributed architecture. Where the data is located is no longer important; the focus is on the grid of functionality, and APIs are key.
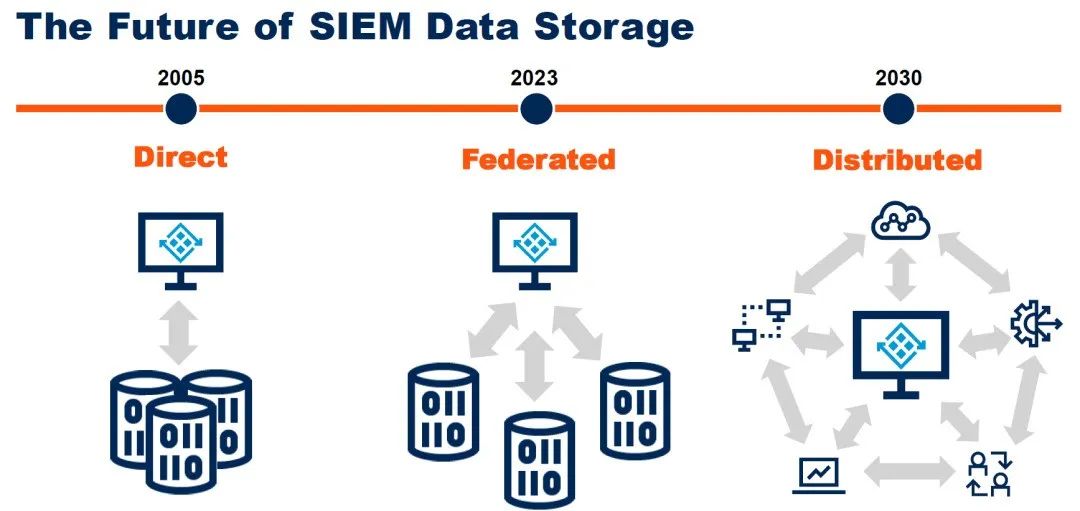
For the second point, it essentially represents a shift from the past unidirectional transfer of knowledge between vendors and users to a bidirectional sharing among vendors, users, and third parties. This is a form of knowledge monetization that will bring new business models and commercial opportunities.
Four Key Points for Building a Modern SOC
Four Key Points for Building a Modern SOC
The changes in security operations demands, concepts, and technologies have not only brought about changes in SIEM but have also driven the evolution of SOC. With the popularization of cloud technology and remote work, Gartner views SOC as a collection of security operation capabilities rather than a physical location. The scene of many people sitting in a room with a giant screen, staring at various screens, is becoming a thing of the past.
In the speech “Is Your SOC a Modern SOC?”, Gartner analyst Eric Ahlm proposed four key points for building a modern SOC: adopt a hybrid operating model, optimize the detection technology stack, focus on daily automation, and implement metric-based iterative evolution.
1) Adopt a hybrid operating model
As cybersecurity challenges become increasingly severe, users are facing more obvious bottlenecks in resources and capabilities, making it difficult to run SOC solely relying on their own strength. Gartner anticipates that in 2023, all SOCs will be hybrid SOCs, meaning they will rely on external forces to some extent, utilizing various security services to fill gaps in personnel and capabilities during SOC planning, construction, and operation. Furthermore, for those users who insist on relying solely on their own operations for SOC, Gartner suggests that their operational team should consist of no fewer than 12 people; otherwise, they will not be able to truly operate the SOC.
2) Optimize the detection technology stack
As previously mentioned, users need to reassess the value of SIEM in SOC; SIEM cannot dominate the SOC technology platform. Gartner recommends that when building the SOC technology platform, users should dismantle the SIEM technology stack, replacing outdated or inefficient parts of SIEM with other technologies, while introducing new functionalities (especially XDR and exposure management) and better integrating with other technologies. Analyst Neil MacDonald directly suggested in his report on “Emerging Security Market Trends and Growth Opportunities” that vendors should introduce multi-telemetry data fusion analysis technologies, eliminate or upgrade outdated SIEM, incorporate proactive security monitoring, and also suggested that managed security service providers increase exposure management and incident response services.
3) Focus on daily automation
Eric Ahlm stated that high-level end-to-end operational process automation is still too far off; what users need more now is automation of (smaller-grained) daily operational activities. Because security processes are inherently variable and dynamic, with many branching scenarios, it is very difficult to fully describe them, which would consume a lot of design and development effort, and cross-departmental processes are even more challenging. Given the current management and technical conditions, achieving comprehensive process-level automation would be too costly. Conversely, automating the security activities that constitute security operational processes is more practical and efficient. At the process level, it is more suitable to link relevant activities through manual and semi-automated methods. I completely agree with this; the SOAR system I helped design adheres to this philosophy.
In terms of achieving process and activity automation, SOAR is not the only choice; there are three technological routes: from the most flexible SOAR platform to simplified automation tools embedded in SIEM and ITSM, to pre-built automation functions in XDR or other DR products.
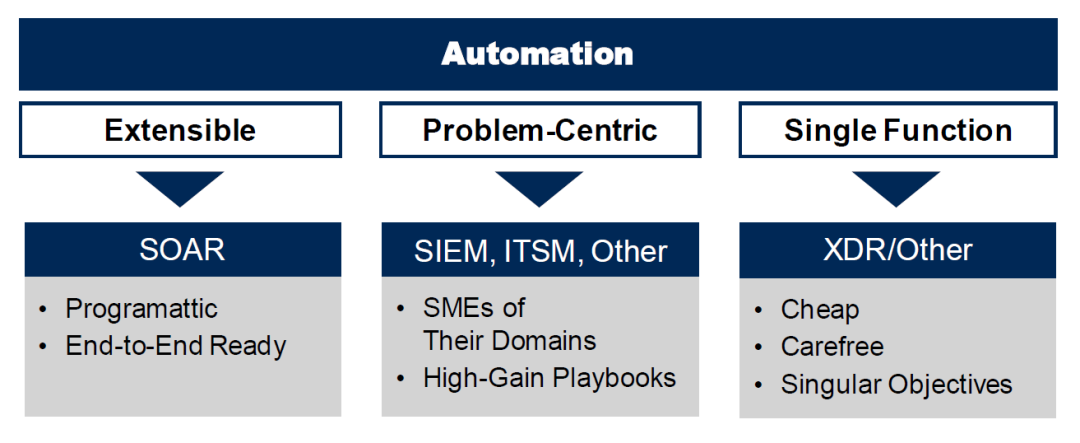
For users, the choice of which technological route to take depends on their actual needs and future development plans.
4) Implement metric-based iterative evolution
Gartner repeatedly emphasizes that building a SOC is a continuous iterative journey, which should iterate at least three times across six phases: planning, prioritization, building, operating, reporting, and maturity. This iterative journey is a process of continuously enhancing SOC capabilities and improving maturity. This process must evolve under the guidance of quantifiable security metrics.
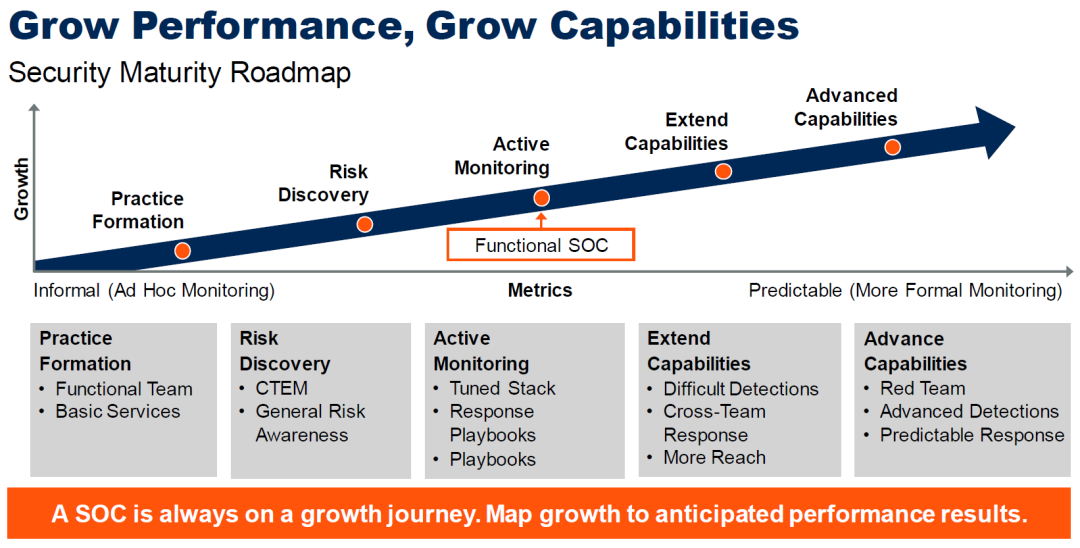
The design of SOC measurement indicators should align with the current maturity level. As shown in the above image, after entering the “proactive monitoring” stage, a formal indicator system should be introduced to measure the effectiveness and value of SOC.
Additionally, reporting metrics should be targeted to different levels and responsibilities of superiors, avoiding situations where communication is ineffective. Analyst Alex Michaels cited a disheartening example in his report on “The Evolution and Expectations of Modern High-Performance SOC” as shown in the image below.

Gartner states that for unit executive leaders, reports should use business metrics (rather than operational metrics) and business terminology they understand; for CIOs and higher-level leaders, a results-driven metric design methodology should be used to output business value-oriented metrics.
Conclusion
Conclusion
The security threat landscape is becoming increasingly severe, emphasizing practical security defenses and results-oriented approaches, making security operations more important. Surrounding the core of network threat defense, the connotation and extension of SIEM are continuously evolving, while the methodology of SOC is also maturing. The security operations, including SIEM and SOC, are inherently complex issues; there are no shortcuts to good security operations, only continuous iterative improvement. This is akin to the journey of Tang Seng and his disciples to the West for scriptures, where Sun Wukong, the somersault cloud, and the golden hoop rod are powerful tools for battling along the way, but cannot directly take them to the West. If we regard XDR, ChatGPT, and AI as new tools for security operations, they still cannot ensure the success of security operations.
A journey of a thousand miles begins with a single step, effort is in the details, and persistence is key.
Original source: Hufu Think Tank
