Introduction
Click the “Shenzhen Network and Information Security Industry Association” public account below to follow and set it as a star.
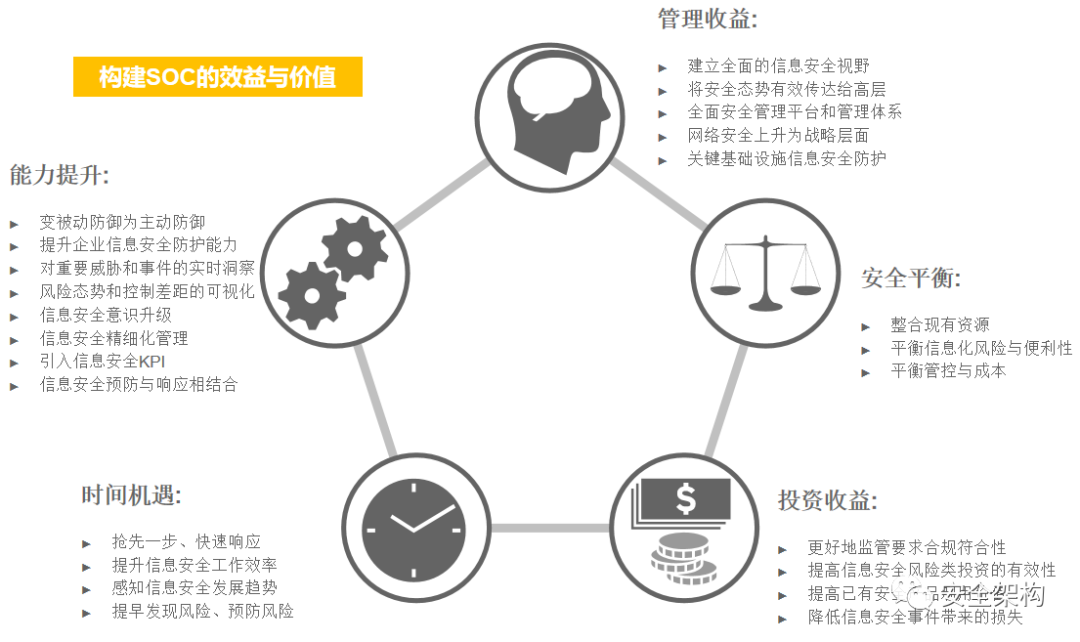
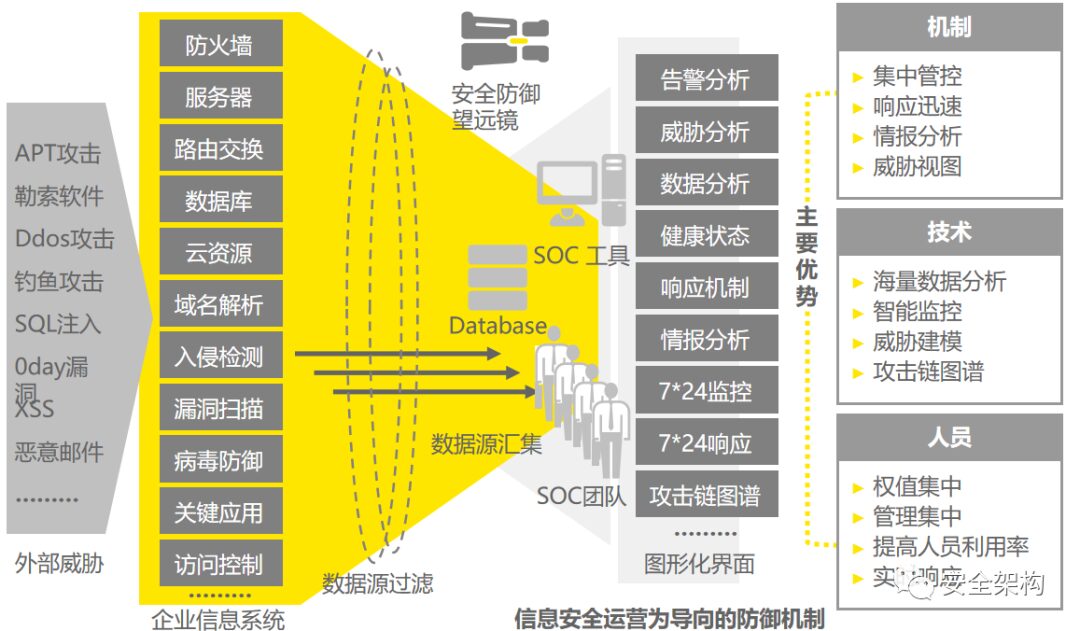
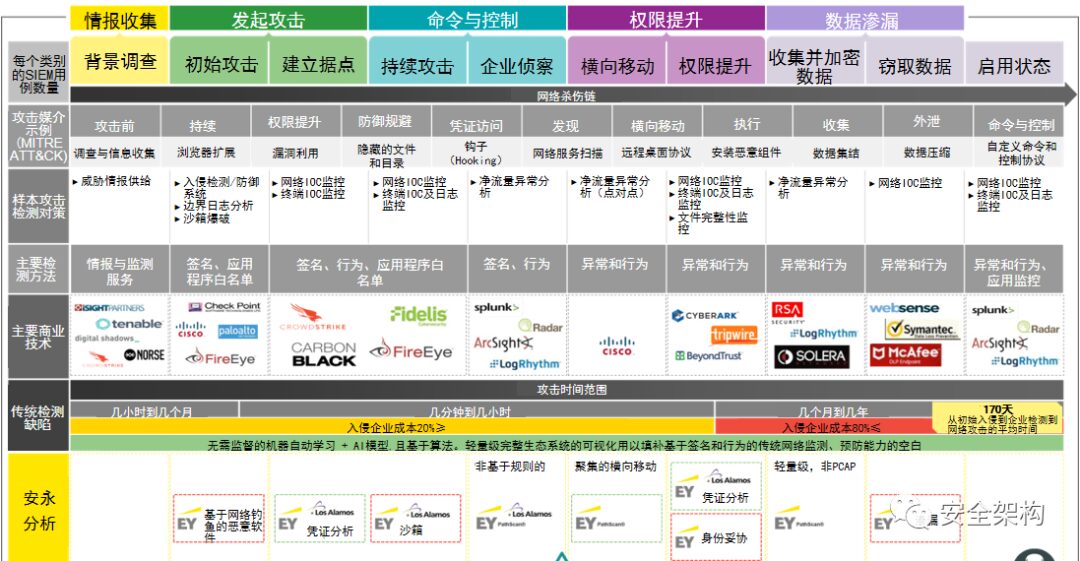
The Security Operations Center is commonly referred to as SOC (Security Operations Center), which adopts a centralized management approach to unify the management of relevant security products, collect security information from all assets within the network, and conduct in-depth analysis, statistics, and correlation of the collected security events to timely reflect the security status of managed assets, identify security risks, and promptly detect and locate various security incidents. It also provides methods and suggestions for handling incidents, assisting administrators in incident analysis, risk analysis, early warning management, and emergency response.
S->Security, meaning that the events or processes handled by SOC should be related to the enterprise’s network security;
O->Operation, representing a dynamic action that includes but is not limited to real-time detection and response;
C->Center, which refers to a systematic construction, a comprehensive defense line formed by the “stacking” of multi-domain security products and services.
The Security Operations Center platform analyzes logs from various security systems, implements the design configuration of the operations center, and continuously optimizes to help discover and report security incidents, manage incident handling, and provide intuitive displays of security risk status.
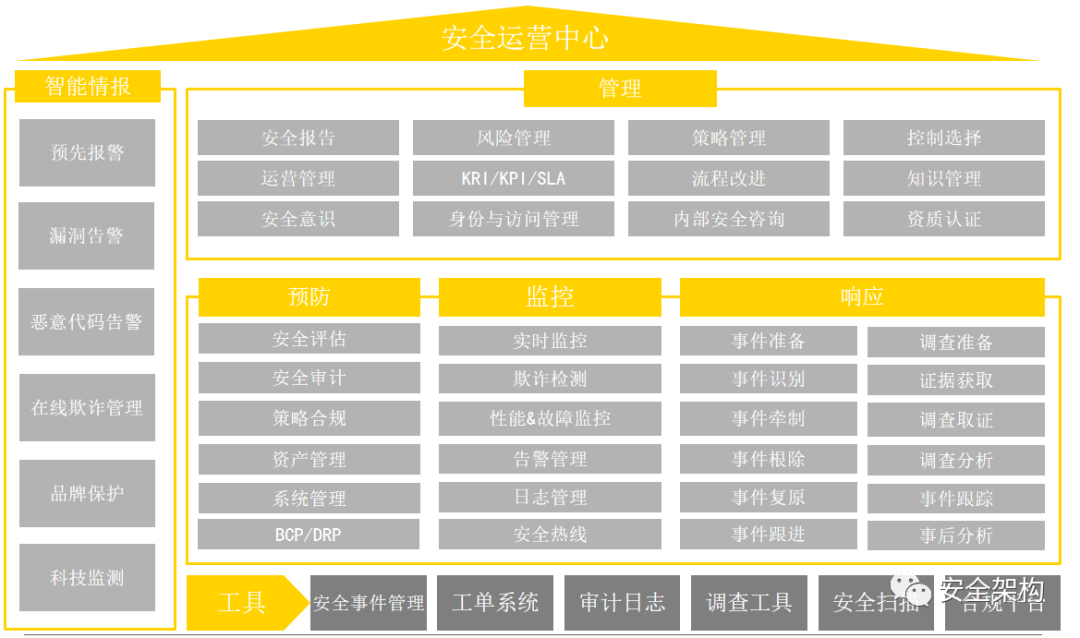
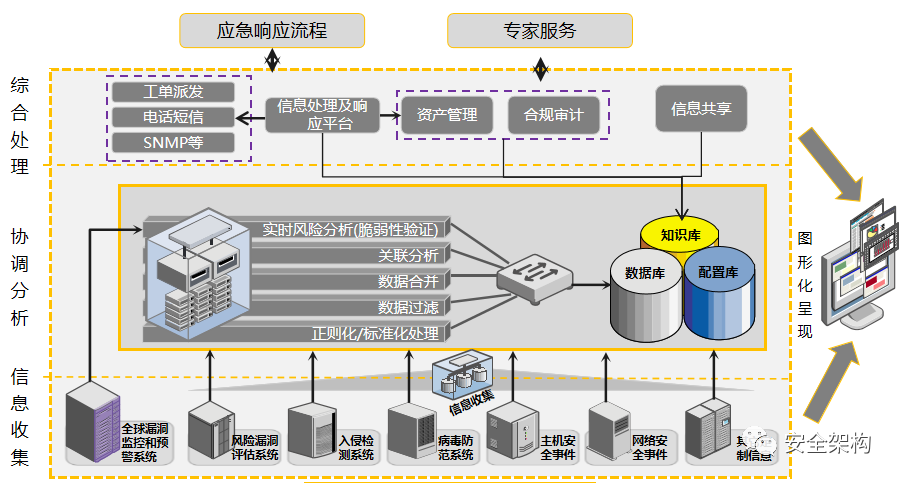
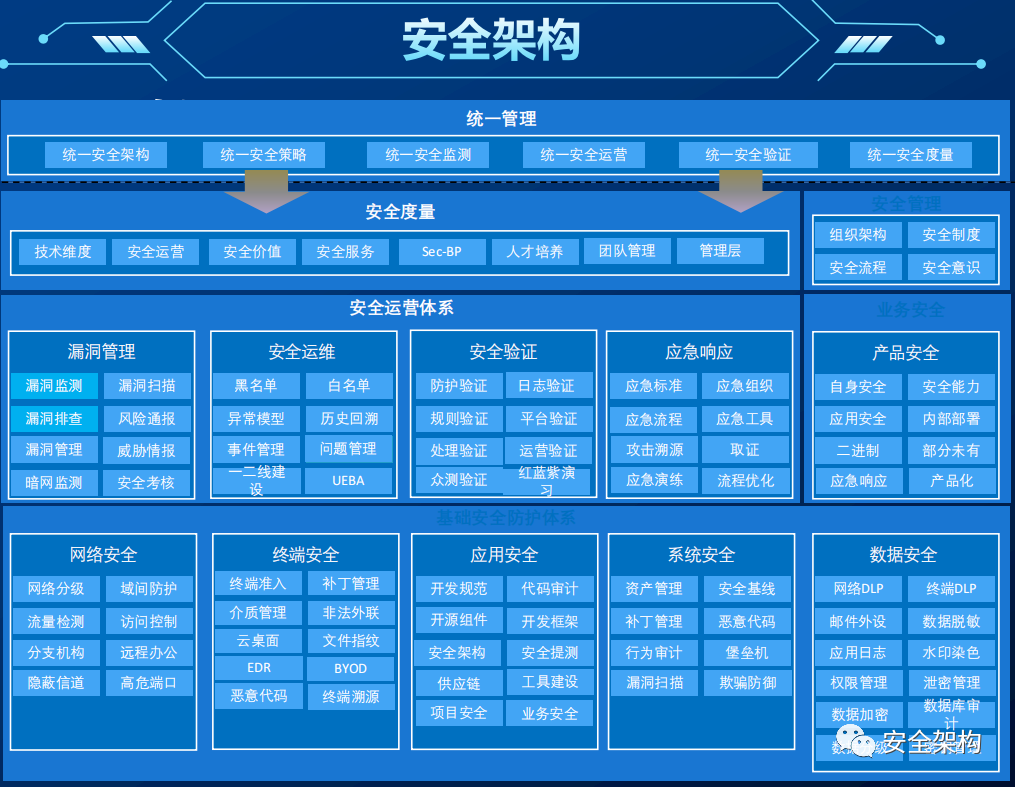
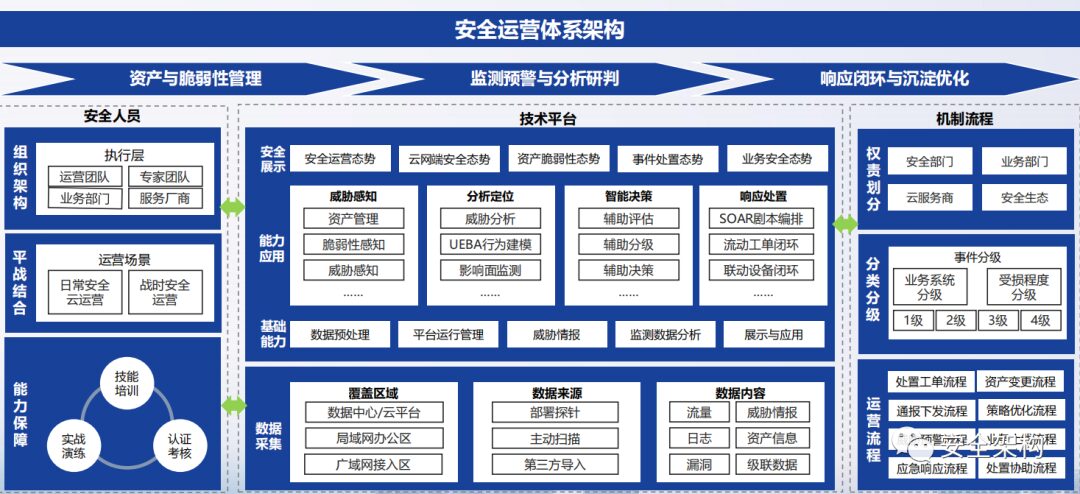
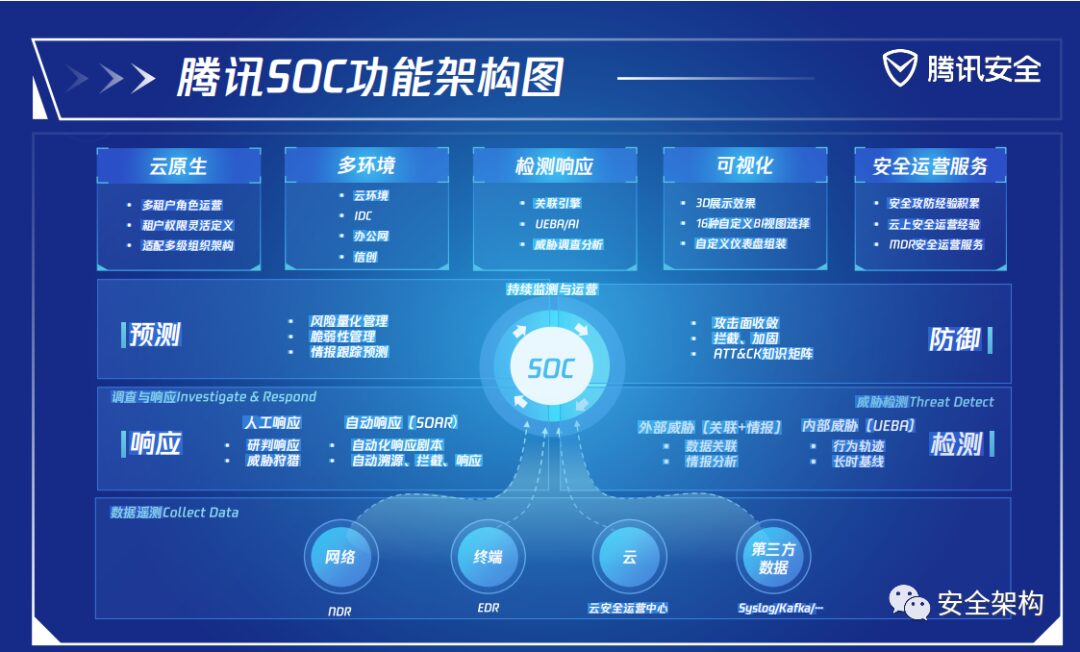
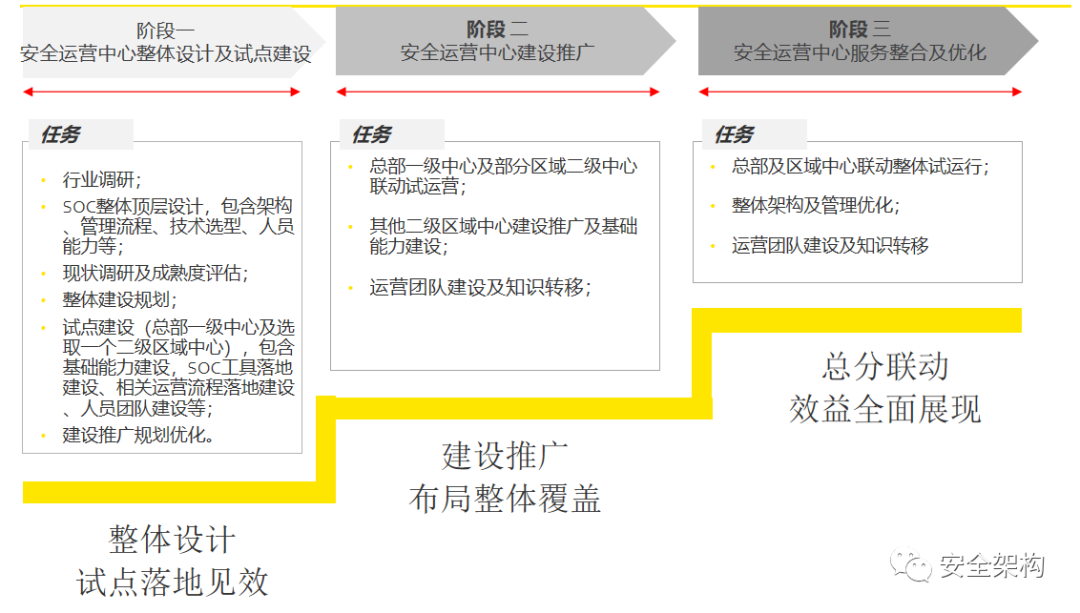
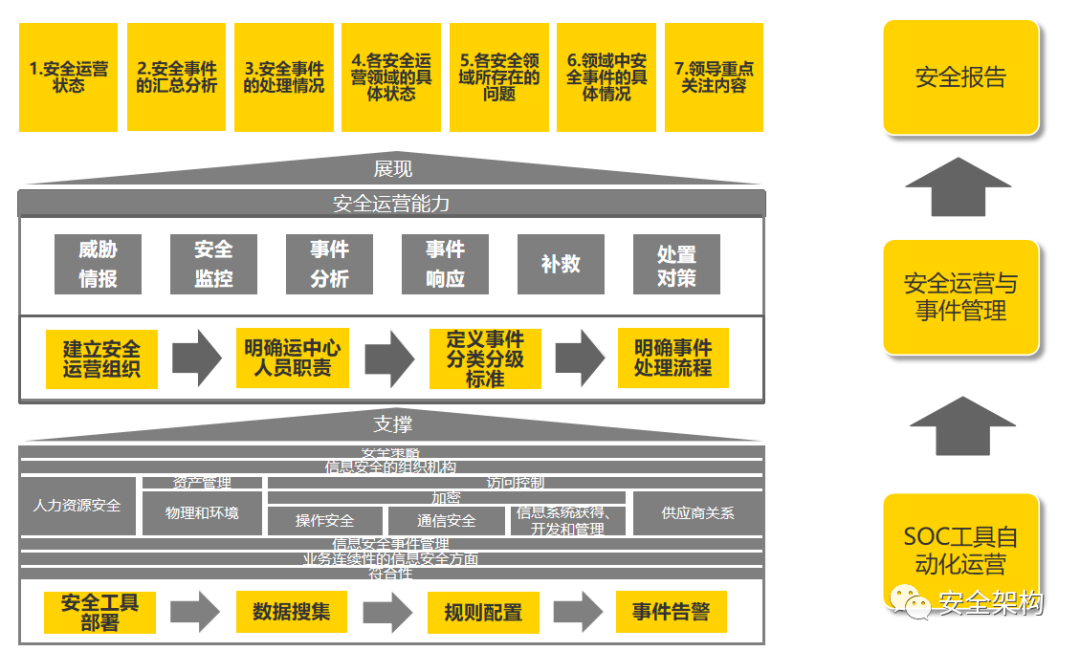
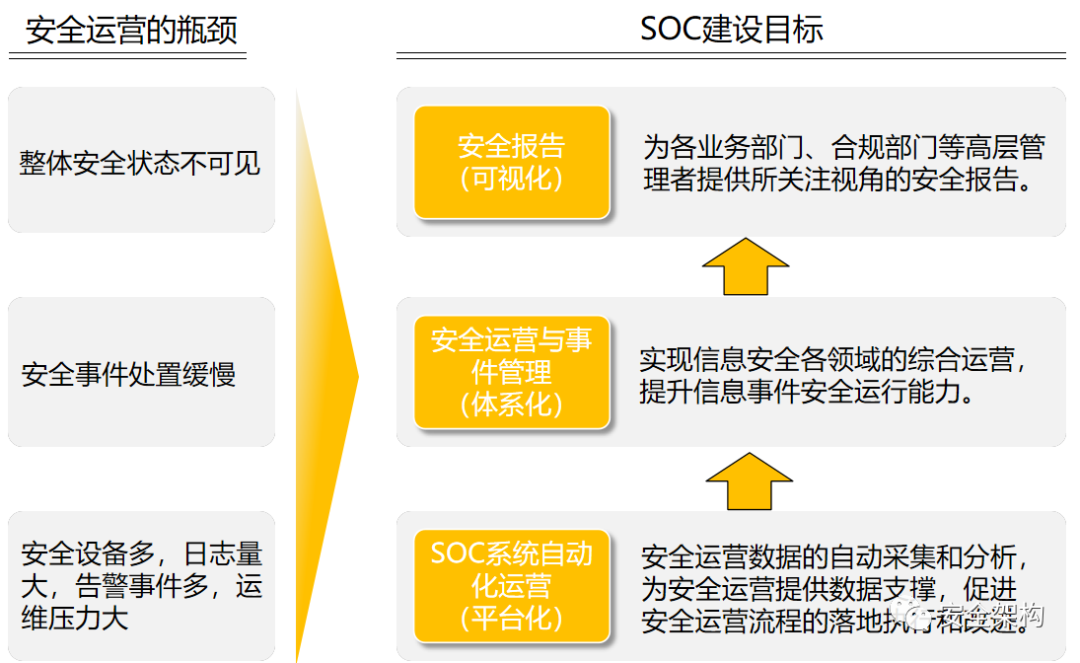
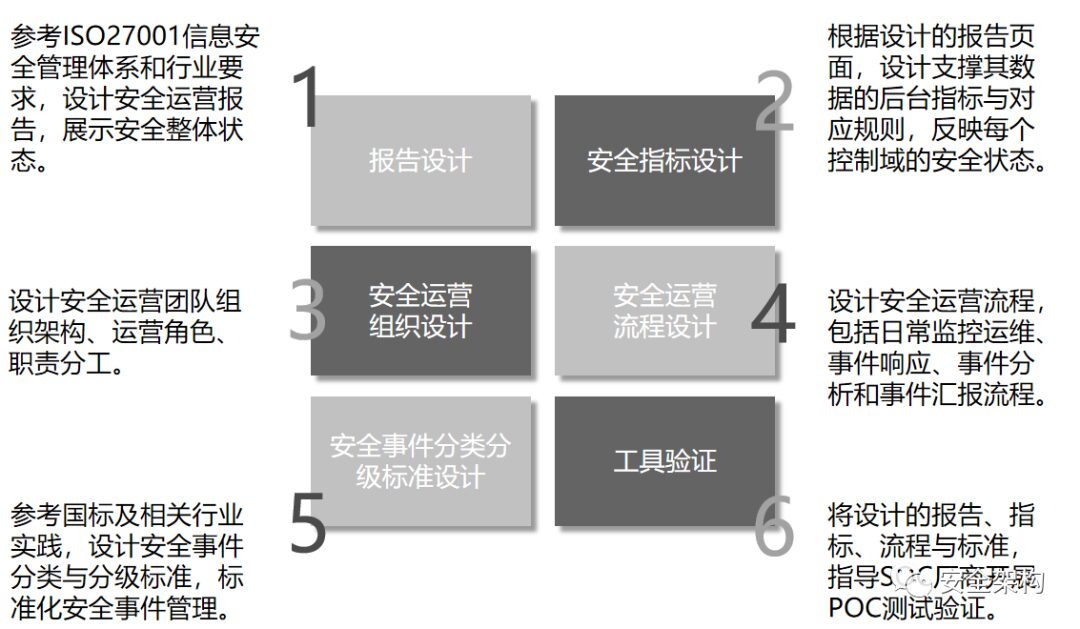
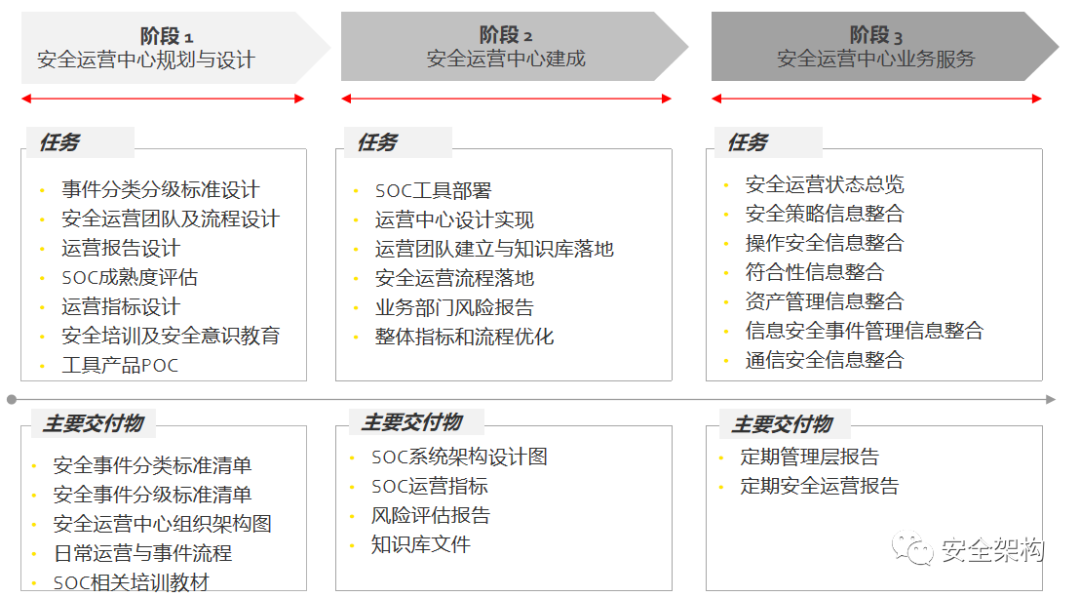
To achieve the construction goals of the Security Operations Center, it is necessary to establish a security operations team, plan daily operations and incident handling processes, and set classification and grading standards for security incidents, relying on the SOC system platform to implement them into the daily work of the operations team.
Compiled and edited by NIS Research Institute
Please note:Job Type + Location + School/Company + Nickname(e.g., Network Engineer + Shenzhen + Huawei + Li Ming) to expedite approval and invitation to the group~
