
Abstract
With the widespread popularity of smartphones, people’s lives have become inseparable from touchscreen devices. However, the security issues of these devices have been largely ignored. In recent years, attacks targeting touchscreen devices have been increasing, posing serious threats to users’ data security and privacy. This article studies touchscreen attacks, focusing on attacks based on electromagnetic signals and acoustic signals, analyzing their principles, security threats to devices, and existing shortcomings in research.
1
Introduction

With the widespread use of consumer electronic devices equipped with touchscreens in daily life and work, the issue of their security has gradually attracted attention. To better protect users’ information security and privacy rights, in-depth research on touchscreen attacks is crucial.
The causes of touchscreen attacks can be summarized as follows:
1. Technical Defects: There are some technical defects in the design and manufacturing processes of touchscreen devices, leading to vulnerabilities, malware, and other types of attacks.
2. User Behavior: Users have some bad habits when using devices, such as using weak passwords, which increase the risk of information theft.
3. Attacker Attacks: Attackers deceive or induce users to perform improper operations, or use special technical means to extract users’ input information in real-time, thereby obtaining sensitive information from the device.
This article focuses on the last type of touchscreen attack, which can be divided into two types: one based on electromagnetic signals and the other based on acoustic signals. This article will conduct an in-depth study of these two types of attacks, systematically summarize relevant literature, clarify future research directions, and provide corresponding suggestions.
2
Electromagnetic Signal-Based Touchscreen Attacks

Currently, research on electromagnetic signal-based touchscreen attacks mainly focuses on active attacks. This article organizes relevant knowledge about touchscreens and analyzes the related research on command injection and command cancellation attacks.
1. Capacitive Touchscreen Related Knowledge
Among existing touchscreen sensing technologies, capacitive touchscreens are widely used due to their good experience and cost-effectiveness. Research on electromagnetic signal-based touchscreen attacks is based on the working principle of capacitive touchscreens.
Capacitive touchscreens are input devices. When a finger touches the screen, a coupling capacitance is formed between the finger and the touchscreen surface, detecting the occurrence of touch events based on the change in capacitance ΔC. Currently, there are two widely used types of capacitive touchscreens: self-capacitance touchscreens and mutual capacitance touchscreens, as shown in Figure 1, where the touch sensor consists of a network of mutually perpendicular transmitting (TX) and receiving (RX) electrodes.
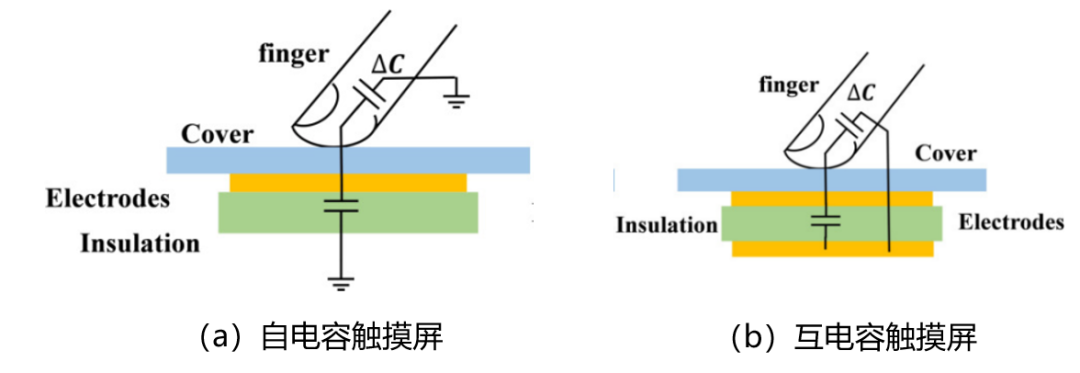
Figure 1 Capacitive Touchscreen
Self-capacitance touchscreens utilize the capacitance of a single electrode, one end connected to the excitation signal and the other end grounded. When a finger touches, it increases the finger-to-ground capacitance, which is in parallel with the electrode’s capacitance. In single-point touch, the TX is scanned first to find the location of capacitance change, determining the horizontal coordinate of the touch position; then the RX is scanned to determine the vertical coordinate of the touch point, thus obtaining the detailed coordinates of the touch position. In multi-point touch, multiple different horizontal and vertical coordinates can be obtained, resulting in multiple points that meet the coordinate conditions, making it impossible to determine the true touch point, resulting in a ‘ghost touch.’ The structural principle of self-capacitance touchscreens is simple, and the scanning speed is fast, but it measures the capacitance of a single electrode rather than the capacitance at the intersection of electrodes, leading to its inability to correctly detect multi-point touch.
Mutual capacitance touchscreens utilize the coupling capacitance formed at the intersection of TX and RX electrodes, where the horizontal electrodes serve as the upper plate of the coupling capacitance and the vertical electrodes serve as the lower plate. During scanning, after activating a row of TX electrodes, each column of RX electrodes is scanned sequentially, detecting the coupling capacitance formed between all RX electrodes and that row of TX electrodes. When a finger touches, the capacitance changes, and the controller processes the change in capacitance to extract and calculate the coordinates of the touch point. Only points with a change greater than a certain value (called the threshold) are considered valid touches. Mutual capacitance touchscreens can detect multi-point touches, but their structure is more complex, power consumption is higher, scanning time is longer, and their noise immunity is not as good as self-capacitance.
2. Literature on Electromagnetic Signal-Based Touchscreen Attacks
Research on attacks against capacitive touchscreens can be divided into two main categories: passive touchscreen attacks and active touchscreen attacks. Among them, passive attacks usually extract private information from the victim’s touchscreen through electromagnetic leakage, while active attacks mainly involve malicious control of the victim’s device. This section selects three recent papers focusing on active touchscreen attacks for analysis.
Reference [1] describes an IEMI touchscreen injection attack based on synchronization and scanning. The mutual capacitance scanning drive method used in this study has been described earlier. It first conducts experiments on 12 different brands and models of smartphones to study the possibility of EMI injection, using the Android Debug Bridge (ADB) application to record the distribution of contact points and capacitance changes on different phones, achieving visualization of results. Then, through numerous experiments, it explores conditions to effectively inject false touch points and create touch events. Finally, it evaluates the attack system through a series of evaluation metrics.
Reference [2] introduces an IEMI touchscreen injection attack that does not rely on synchronization and scanning. This paper analyzes the working principle of charge transfer (QT) sensors in mutual capacitance touchscreens and derives the conditions to overcome synchronization limitations, namely that the output voltage change must exceed the threshold voltage, as well as the corresponding circuit model of the touchscreen under IEMI attacks, validating the factors affecting touchscreen attacks, such as the electric field strength and the frequency of IEMI signals, followed by an ideal experimental demonstration and experimental analysis of characteristics affecting IEMI attack performance.
Reference [3] proposes a new attack that completely controls the victim’s device by hijacking the user’s operations. By generating reverse current using designed IEMI signals, it neutralizes the user’s touch commands, effectively canceling the genuine touch commands. In addition to this basic denial-of-service attack, it also implements a target cancellation attack, which can cancel target commands without interfering with unrelated operations. Meanwhile, it establishes an electromagnetic model to analyze the impact of IEMI on touchscreens, deriving the reverse current value that can cancel user commands, designing the attack from four aspects: effective cancellation, screen positioning, controllable cancellation, and diversity impact suppression, and evaluates attack performance through device prototype experiments.
3
Acoustic Signal-Based Touchscreen Attacks

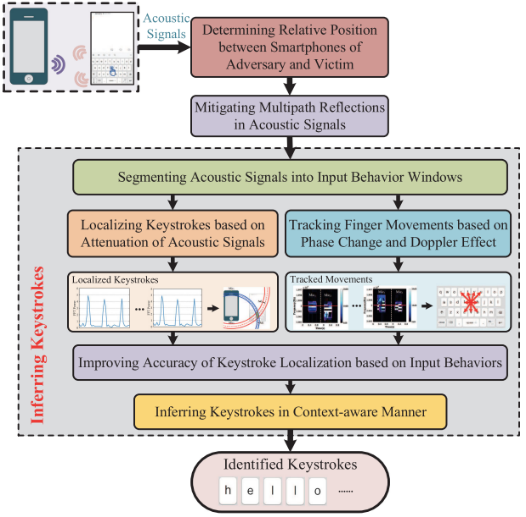
Figure 2 KeyListener System Architecture
The specific implementation process for inferring keystroke information is shown in Figure 3. When the victim types, the attacker can obtain two propagation distances based on the acoustic signal attenuation equation. These signals propagate from the speaker, are reflected by the victim’s keystroke finger, and finally propagate to two microphones. Given the relative positions of the speaker and the two microphones on the smartphone, we can determine the distance between the keystroke finger and the two microphones. By calculating, we can obtain a unique effective intersection, which is the keystroke position, but it can only locate an area of the keystroke, not an exact point.
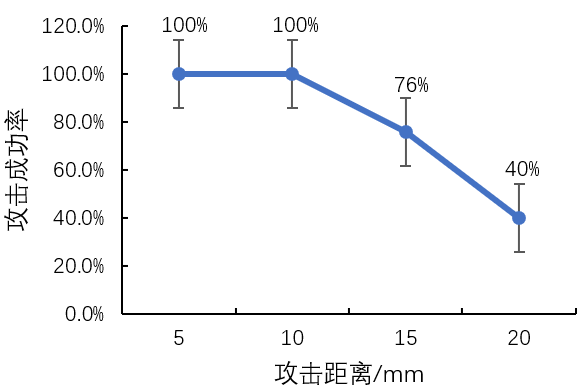
Figure 3 Specific Implementation Process for Inferring Keystroke Information
2. Gesture Input Attacks
In the use of touchscreens, users not only input via keyboard keystrokes but also through gesture inputs, where users place their fingers on the first letter of a word and then drag their fingers to each subsequent letter in the word until reaching the last letter, at which point the finger is removed, and the gesture is processed as word data. Reference [6] captures audio signals from the haptic feedback mechanism emitted during gesture keyboard input and performs classification to recognize the text entered on the device, thus utilizing haptic feedback from gesture input to implement touchscreen attacks. This feedback is usually realized as motor vibrations.
4
Summary of Literature on Touchscreen Attacks

In this section, we review the literature on two different types of touchscreen attacks and deeply compare the characteristics of these studies.
1. Electromagnetic Signal-Based Touchscreen Attacks
Reference [1] replaces mathematical modeling and theoretical derivation with numerous experiments, relying on synchronization and scanning mechanisms. It was the first to propose a non-contact EMI attack on capacitive touchscreens, with the core idea of using electromagnetic signals to interfere with the capacitive measurement of touchscreens. Since the experimental process used the Android Debug Bridge (ADB) application for visual analysis, it only analyzes Android system phones, and many experimental results lack theoretical explanations.
Reference [2] combines the working principles of capacitive touchscreens with the radiation IEMI electric field strength and signal frequency, overcoming the synchronization dependency in Reference [1] to accurately inject touch events, thus achieving attacks.
All three related papers on electromagnetic signal-based touchscreen attacks focus on active attacks on touchscreens. The two types of attacks described in References [1] and [2] achieve targeted attacks capable of remotely distributing false touch point locations, but users can always maintain absolute control over the device through the touchscreen, meaning that corresponding events will appear on the user’s screen. Once an anomaly is detected, the user can immediately terminate it, indicating that the effectiveness of existing active attacks on touchscreens is limited.
Based on this, Reference [3] explores the IEMI mechanism on touchscreens in-depth, proposing a new IEMI attack that can effectively and specifically control command cancellation, considering two scenarios where the victim’s device is placed face up or face down.
Summarizing the above literature, the innovations and shortcomings of each paper are shown in Table [1], and the basic system performance is shown in Table [2], with a detailed comparison of the influence of desktop thickness on the attack effect shown in Figures [4], [5], and [6].
|
Paper Title |
Innovations | Shortcomings |
| Reference [1] | The first non-contact EMI attack on capacitive touchscreens; proposed ‘similarity to human touch’ performance metrics | Experimental results lack theoretical support; attack system cannot control user operations |
| Reference [2] | The first attack that does not rely on synchronization to inject touch events; combines the working principles of capacitive touchscreens with radiation IEMI electric field strength and signal frequency; proposes a threshold voltage that does not rely on synchronization | Attack system cannot control user operations |
| Reference [3] | The first command cancellation attack; proposes a threshold for reverse current that can neutralize touch commands; broadens application scenarios | Attack fails on Bluetooth (extra channel for command transmission) |
Table 1 Comparison of Innovations and Shortcomings of Literature
|
Performance |
Reference [1] | Reference [2] | Reference [3] |
| Device Orientation | Device Face Down | Device Face Down | Device Face Up, Face Down |
| Device Diversity | Android | Android, IOS, Windows | OLED, IPS, AMOLED, Android, IOS, HarmonyOS |
| Desktop Material | Non-Metallic Material | Non-Metallic Material | Non-Metallic Material |
Table 2 Performance Comparison of Systems

Figure 4 Impact of Different Desktop Thicknesses on Injection Speed in Reference [1]
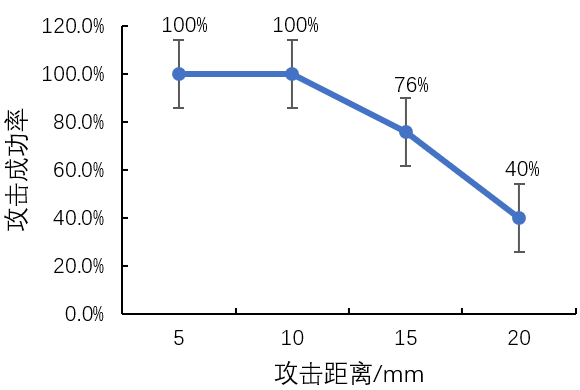
Figure 5 Impact of Different Desktop Thicknesses on Attack Success Rate in Reference [2]
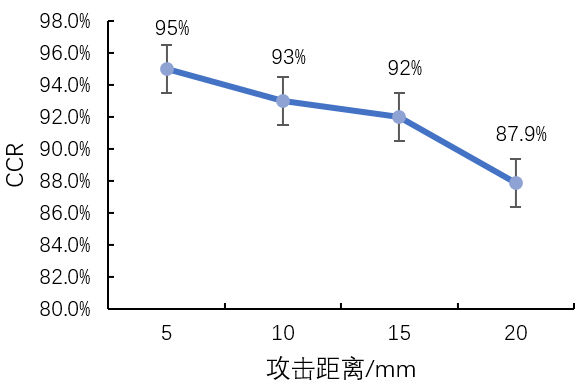
Figure 6 CCR under Different Desktop Thicknesses in Reference [3]
2. Acoustic Signal-Based Touchscreen Attacks
Research in Reference [4] shows that acoustic features have high accuracy under practical conditions and can effectively distinguish user inputs at different positions and directions, but acoustic features are limited by the physical separation of inputs, reducing accuracy on smaller input area interfaces.
Reference [5] implements an indirect keystroke eavesdropping attack on touchscreen virtual keyboards, which does not require directly obtaining keystroke-related side-channel information from the victim’s device and has various advantages:
-
The attack scenario is not limited by the coverage of Wi-Fi infrastructure, but this attack has many limitations;
-
Uses a single-word dictionary for keystroke inference, with the inference accuracy of different words being independent of each other;
-
Robust to various environments, without requiring additional infrastructure.
However, there are also many limiting factors in the implementation of this attack:
-
Positional Relationships: The attacker’s smartphone axis must be parallel to the victim’s smartphone axis, and recognition accuracy is affected by the relative position between the attacker’s and victim’s smartphones;
-
Human Factors: Experimental results show that when the victim intentionally prevents others from seeing input on the touchscreen, the accuracy of keystroke inference drops significantly; it only applies to users using QWERTY virtual keyboards and cannot attack users using T9 keyboards or gesture keyboards;
-
Attack Distance: As the distance between the attacker and the victim’s smartphone increases, accuracy significantly decreases.
Research shows that due to different pause points and redirect points in gesture-based words, there are differences in how different words are typed. Based on this, Reference [6] proposes a new attack vector that utilizes gesture keyboards to capture acoustic signals to attack the victim’s device, but the diversity of devices and samples in the experiment is poor, only using Moto G5S Plus (XT1803) and Samsung Galaxy S10e with 20 sentence samples, making the experiment not comprehensive. At the same time, the effectiveness of this attack method is influenced by the device’s position, users’ typing styles, and nail lengths.

Conclusion and Outlook
Through in-depth analysis of relevant literature on touchscreen attacks, we have gained a clearer understanding of the current research status in this direction.
Currently, electromagnetic signal-based touchscreen attacks mainly focus on active attacks, and research in this area is quite comprehensive. Researchers have not only studied how to remotely distribute false touch point locations for targeted attacks but have also explored how to use false commands to implement denial-of-service and target cancellation attacks. However, these attack methods also have some shortcomings, such as a relatively singular attack surface and significant limitations on desktop materials and thickness. In terms of acoustic signal-based touchscreen attacks, recent research has shifted from attacks on physical keyboards to attacks on touchscreen virtual keyboards, continually expanding the scope of attacks. However, through in-depth analysis, we find that the success rate of attacks using acoustic signal extraction is relatively low, and there are many limiting conditions in the attack environment.
In the future, research on touchscreen attacks will become more in-depth, and correspondingly, we should also study countermeasures against potential touchscreen attacks. Furthermore, we need to further investigate other human-computer interaction interfaces that may face attacks and corresponding countermeasures.
References
[1] Wang, Kai, Richard Mitev, Chen Yan, Xiaoyu Ji, Ahmad-Reza Sadeghi and Wenyuan Xu. “GhostTouch: Targeted Attacks on Touchscreens without Physical Touch.” in Proceedings of USENIX Security, 2022.
[2] H. Shan, B. Zhang, Z. Zhan, D. Sullivan, S. Wang, and Y. Jin, “Invisible finger: Practical electromagnetic interference attack on touchscreen-based electronic devices,” in Proceedings of IEEE S&P, San Francisco, CA, USA, 2022, pp. 1246-1262, doi: 10.1109/SP46214.2022.9833718.
[3] M. Gao et al., “Expelliarmus: Command Cancellation Attacks on Smartphones using Electromagnetic Interference,” IEEE INFOCOM 2023-IEEE Conference on Computer Communications, 2023.
[4] K. R. Teo, B. T. Balamurali, C. J. Ming and J. Zhou, “Retrieving Input from Touch Interfaces via Acoustic Emanations,” 2021 IEEE Conference on Dependable and Secure Computing (DSC), Aizuwakamatsu, Fukushima, Japan, 2021, pp. 1-8, doi: 10.1109/DSC49826.2021.9346271.
[5] J. Yu, L. Lu, Y. Chen, Y. Zhu and L. Kong, “An Indirect Eavesdropping Attack of Keystrokes on Touch Screen through Acoustic Sensing,” in IEEE Transactions on Mobile Computing, vol. 20, no. 2, pp. 337-351, 1 Feb. 2021, doi: 10.1109/TMC.2019.2947468.
[6] J. Francis Roscoe and M. Smith-Creasey, “Acoustic Emanation of Haptics as a Side-Channel for Gesture-Typing Attacks,” 2020 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), Dublin, Ireland, 2020, pp. 1-4, doi: 10.1109/CyberSecurity49315.2020.9138864.
China Confidential Association
Science and Technology Branch
Long press the QR code to follow us

Author: Bi Jiaqing, Institute of Information Engineering, Chinese Academy of Sciences
Editor: Cai Beiping
Top 5 Highlights from Previous Articles
Cross-Network Attacks: An Introduction to Techniques for Breaking Physical Isolation Networks
Thoughts on the Top-Level Design of Smart City Security
Revisiting Some New Issues Faced in the Development of Digital Forensics Technology
Development and Challenges of Low Earth Orbit Satellite Interconnected Networks
Introduction to LaserShark Non-Contact Attack Implant Technology
Recent Highlights Review
Wireless Vibration Sensing: Principles, Technologies, and Applications
Brief Development of Electromagnetic Fingerprint Technology
Application of RF Sensing Technology in Healthcare
Introduction to Electromagnetic Metamaterials
Overview of Research on Mobile Encrypted Traffic Classification and Recognition
Application of Video Analysis Technology in Personnel Identity Recognition Tasks