Common Security Threats and Protections in Embedded Systems
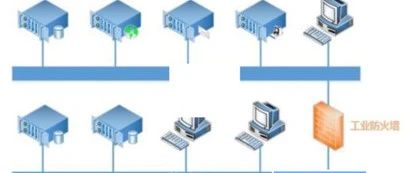
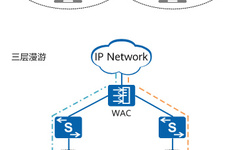
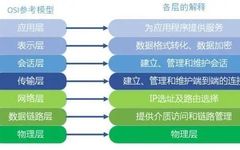
Due to the uniqueness of embedded systems, there are many security threats. Firstly, because embedded systems have limited resources, with small RAM and ROM and limited processing speed, they cannot implement multiple security defense measures simultaneously, making them vulnerable to attacks. Secondly, the diverse deployment environments of embedded systems, such as industrial production environments, medical … Read more