Fundamentals of Cybersecurity
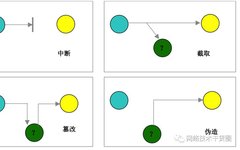
1. Overview of Cybersecurity 1.1 Definition Information Security: The technical and managerial security measures established and adopted for data processing systems, protecting computer hardware, software, and data from accidental and malicious destruction, alteration, and disclosure. Cybersecurity: Prevent unauthorized users from accessing information Prevent unauthorized attempts to destroy or modify information 1.2 Characteristics of Information Security … Read more