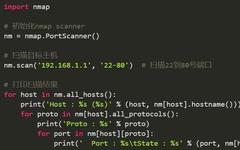
Linux io_uring Proof-of-Concept Rootkit Bypasses System Call-Based Threat Detection Tools
Shake Network Technology NewsClick the right to follow for the latest technology news! Cybersecurity researchers recently demonstrated a proof-of-concept (PoC) Rootkit named “Curing” that utilizes the Linux asynchronous I/O mechanism io_uring to bypass traditional system call monitoring. 01 Significant Blind Spots in Security Tools ARMO stated that this leads to “significant blind spots in Linux … Read more