Interpretation of Industrial Control System Cybersecurity Protection Guidelines
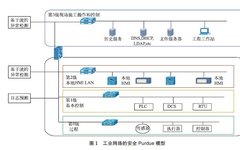
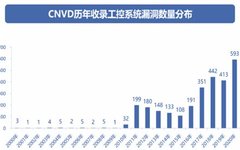
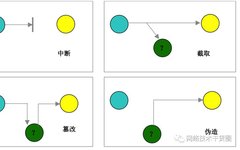
Introduction Overview Industrial control systems, as the cornerstone of industrial production operations, play an indispensable role in ensuring the stability of enterprise operations, facilitating the smoothness of the supply chain, promoting healthy economic and social development, and safeguarding national security. To guide industrial enterprises in strengthening control security protection, the Ministry of Industry and Information … Read more