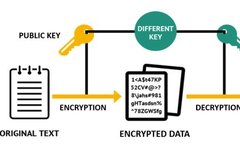
Digital Signature Algorithm (DSA) in Cryptography: How It Works and Its Advantages
The COVID-19 pandemic has made remote working the new norm and brought the business world into a phase that is yet to be explored. Undoubtedly, due to the lack of face-to-face interaction and standard distance restrictions, many users have had to digitally sign some official documents over the past few years. To maintain the authenticity … Read more