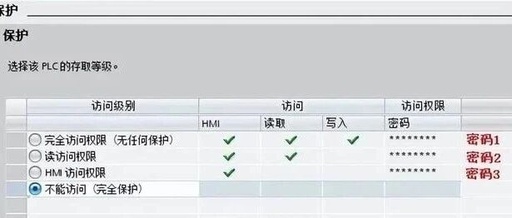
Summary | Introduction to Commercial Cryptography Products
NIS Research Institute Shenzhen Network and Information Security Industry Association —— For more content, click to read the original article. In recent years, the independent innovation capability of commercial cryptography products in our country has continuously strengthened, and the industrial support capability has been continuously improved. A rich variety of commercial cryptography product systems have … Read more