Article Outline
-
Information Security Risks and Challenges of Intelligent Connected Vehicles
-
Current Status of Information Security Policies and Regulations for Intelligent Connected Vehicles in China
-
Analysis and Interpretation of Key Policies and Regulations (Network | Data | Software Security)
-
Assessment of Future Management Directions
Intelligent Vehicles
Information Securityof Intelligent Connected Vehicles
Risks and Challenges
Intelligent Connected Vehicles arethe Development Direction
of the Industry
The transformation of traditional vehicles from manual control mechanical products to intelligent products controlled by electronic information systems is an inevitable trend. China has elevated the development of intelligent connected vehicles to a national strategic level and is promoting the comprehensive development of intelligent connected vehicles.
The National Government Places Great Importance on:
Companies are Fully Layouting:

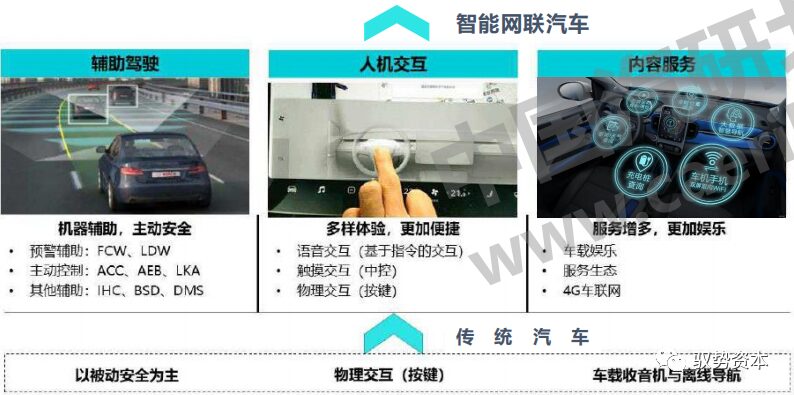
Intelligent Connectivity Increases Vehicle Information
Security Risks
With the advent of the intelligent connected era, the networking and intelligent functions of vehicles are increasing, leading to more interactions from external environmental perception to internal device systems, breaking the original closed ecosystem of vehicle control systems and introducing many security risks from the internet:
-
The driving entity shifts from “human” to “autonomous driving systems”;
-
The increase in connected vehicle functions leads to a large volume of information exchange;
-
The regulatory subjects and content become more complex.
The introduction of numerous new technologies and connected functions has led to an increase in information security risks:
-
Complex Programs: At least 100 onboard computers running 60 million lines of code, with autonomous driving exceeding 200 million lines of code.
-
Intelligent Control: Replacing human direct control of mechanical parts with perception-decision control. Information security not only suffers economic losses but may also become a social security issue.
-
Inherent Defects: The computing and networking systems used inherit existing computing and networking architectures and their inherent security flaws.
-
Data Connectivity: Onboard information systems are interconnected with the outside world, increasing the index of shared information, involving user privacy security.
-
Charging Stations: The PLC circuit of the control module connects to the management system via Ethernet, lacking protection within the entire network.
-
Battery Management Systems: Attacks on BMS control algorithms can affect the performance of electric vehicle batteries.
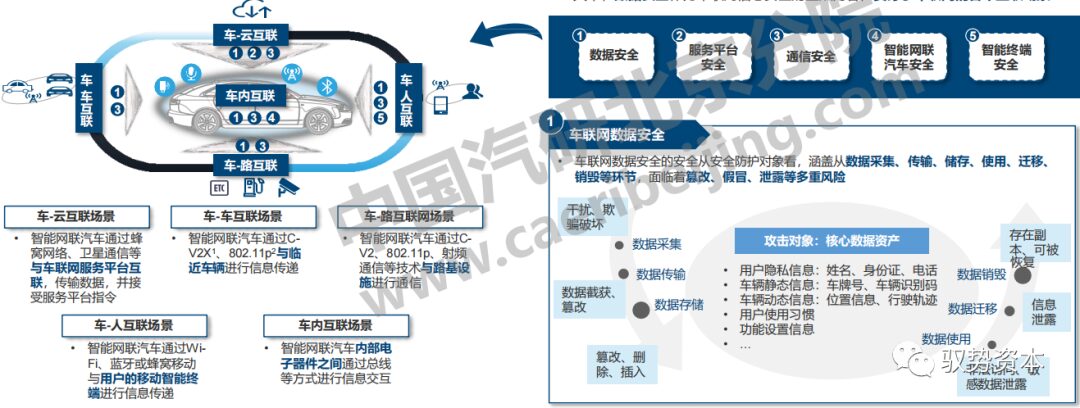
Various
Information Security Threats in Five Scenarios of Connectivity
Connected vehicles involve five interconnection scenarios among “people, vehicles, roads, and clouds,” which can be divided into five types of security: data, service platform, communication, intelligent connected vehicles, and mobile intelligent terminals, with data security permeating all interconnected scenarios.
-
Connected vehicles focus on “two ends and one cloud,” supplemented by ground infrastructure, involving vehicle-cloud, vehicle-vehicle, vehicle-road, vehicle-person, and vehicle-internal connectivity scenarios;
-
For the five interconnection scenarios, information security for connected vehicles is divided into five types: data security, connected vehicle service platform security, communication security, intelligent connected vehicle security, and mobile intelligent terminal security;
-
Data security, as a key content of connected vehicle information security, permeates all interconnected scenarios.
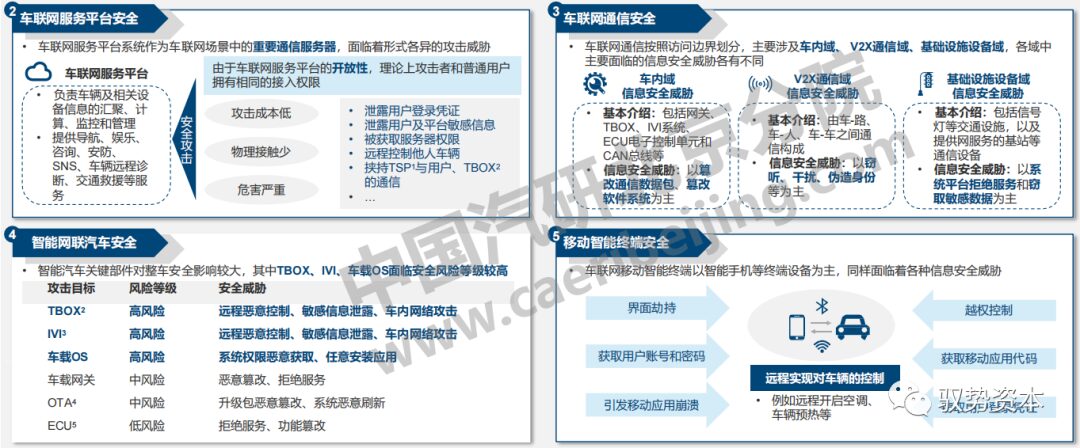
Connected vehicle service platforms, various communication domains, intelligent connected vehicles, and mobile intelligent terminals also face various information security attack risks:
In recent years, the number of information security incidents in connected vehicles has been increasing:
-
According to the Ministry of Industry and Information Technology’s dynamic monitoring of connected vehicles, since 2020, global vehicle manufacturers and information service providers have suffered over 2.8 million malicious attacks, making information security threats more severe;
-
According to Upstream’s report, publicly reported information security attack incidents in connected vehicles are continuously increasing, with the types of attacks also showing a trend of diversification;
-
Connected vehicles have faced a variety of information security attack incidents, with wireless keys and TSP servers being key attack targets:
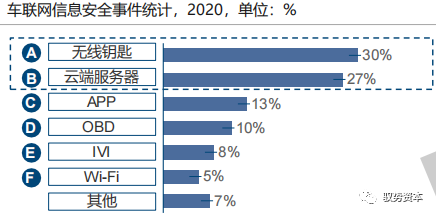
-
In summary, current information security attack incidents mainly occur in vehicle-person, vehicle-cloud, and vehicle-internal interconnection scenarios, while vehicle-vehicle and vehicle-road interconnections are still in the research and testing phase, with few typical cases.
Typical Information Security Cases in Vehicle-Person, Vehicle-Cloud, and Vehicle-Internal Scenarios
In the vehicle-person interconnection scenario:
-
Case: Cracking Digital Car Keys. Utilizing the password length vulnerability of the DST40 encryption algorithm, the digital car key of the Tesla Model S was successfully cracked, allowing the attacker to copy the car key in seconds and unlock the door.

-
Case: Shared Car App Cracked. Due to the cracking of the Car2Go mobile app, 100 luxury vehicles were stolen in Chicago, USA.

In the vehicle-cloud interconnection scenario:
-
Case: Cloud Server Data Leak. Honda India stored information from the HondaCONNECT mobile application in two publicly accessible Amazon S3 buckets, ultimately leading to the leakage of personal details of over 50,000 customers.

-
Case: Wi-Fi Protocol Vulnerability. The Volkswagen Golf GTE was found to have a Wi-Fi connection protocol vulnerability, allowing hackers to further invade the vehicle’s navigation system, accurately locate the vehicle, and update in real-time.

In the vehicle-internal interconnection scenario:
-
Case: Command Injection via OBD Interface. A certain Jeep model was attacked through physical contact by an attacker who injected commands via the OBD interface, controlling the vehicle’s power system, steering wheel, and brake system, posing a severe threat to the driver’s safety.

-
Case: IVI In-Vehicle Entertainment System Vulnerability. The BMW IVI in-vehicle entertainment system ConnectedDrive was reported to have remote control vulnerabilities, including session vulnerabilities, allowing malicious attackers to bypass the VIN vehicle identification number, obtain another user’s VIN, and access and edit other users’ vehicle settings.

Intelligent Vehicles
Current Status of Information Security Policies and Regulations for Intelligent Connected Vehicles in China
Regulatory Authorities
Various national ministries have developed relevant policies and executed supervision based on their responsibilities in key components and lifecycle stages of connected vehicles, including the Cyberspace Administration, Ministry of Industry and Information Technology, Ministry of Transport, Ministry of Public Security, National Standards Committee, etc., to jointly promote the establishment of a sound information security management mechanism for intelligent connected vehicles.
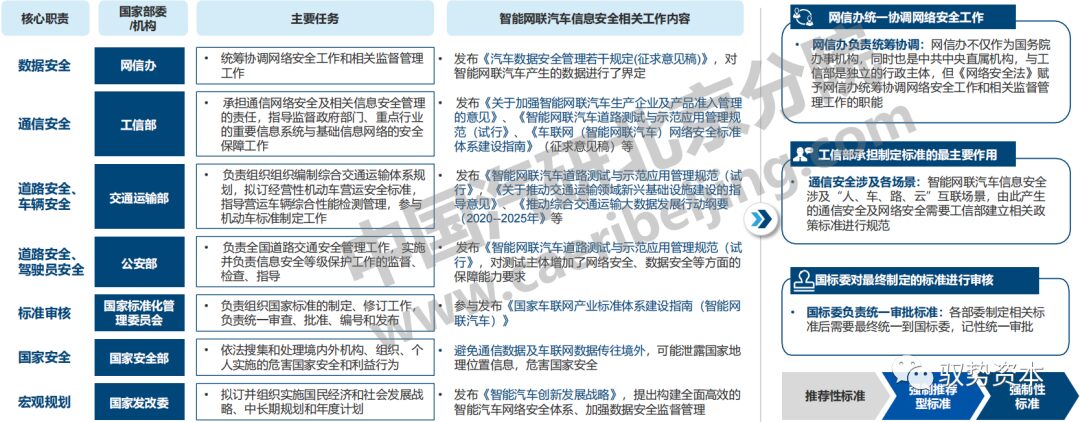
The Cyberspace Administration Coordinates Network Security Work:
-
The Cyberspace Administration is responsible for overall coordination: As an office of the State Council, it is also a direct institution of the Central Committee of the Communist Party of China, independent from the Ministry of Industry and Information Technology, but the “Cybersecurity Law” grants the Cyberspace Administration the function of coordinating network security work and related supervision and management.
The Ministry of Industry and Information Technology Plays a Leading Role in Standard Development:
-
Communication security involves various scenarios: Information security for intelligent connected vehicles involves interconnection scenarios of “people, vehicles, roads, and clouds,” hence the resulting communication security and network security require the Ministry of Industry and Information Technology to establish relevant policy standards for regulation.
The National Standards Committee Approves the Final Standards:
-
The National Standards Committee is responsible for unified approval of standards: After various ministries develop relevant standards, they need to be finally unified under the National Standards Committee for approval.
Industry Policy Requirements
The national design for the top-level industrial development policy for intelligent connected vehicles has considered information security, with varying degrees of planning and requirements:
-
In May 2015, the State Council published “Made in China 2025”;
-
In May 2016, the National Development and Reform Commission, Ministry of Science and Technology, Ministry of Industry and Information Technology, and Central Cyberspace Administration issued the “Three-Year Action Implementation Plan for the Internet+ Artificial Intelligence”;
-
In August 2016, the National Development and Reform Commission and Ministry of Transport issued the “Implementation Plan for Promoting Convenient Transportation and Intelligent Transportation Development through Internet+”;
-
In October 2016, the Ministry of Industry and Information Technology published the “Energy Saving and New Energy Vehicle Technology Roadmap”;
-
In April 2017, the Ministry of Industry and Information Technology, National Development and Reform Commission, and Ministry of Science and Technology published the “Medium and Long-Term Development Plan for the Automotive Industry”;
-
In July 2017, the State Council published the “New Generation Artificial Intelligence Development Plan”;
-
In November 2017, the National Development and Reform Commission published the “Three-Year Action Plan to Enhance the Core Competitiveness of Manufacturing (2018-2020)”;
-
In December 2018, the Ministry of Industry and Information Technology published the “Action Plan for the Development of the Connected Vehicle (Intelligent Connected Vehicle) Industry”;
-
In May 2019, the Ministry of Transport issued the “Guiding Opinions on Promoting the Development of Road Traffic Autonomous Driving (Draft for Comments)”;
-
In July 2019, the Ministry of Transport published the “Outline for the Development of Digital Transportation”;
-
In September 2019, the Central Committee of the Communist Party of China and the State Council published the “Outline for Building a Strong Transportation Nation”;
-
In December 2019, the Ministry of Industry and Information Technology published the “New Energy Vehicle Industry Development Plan 2021-2035”;
-
In February 2020, 11 ministries including the National Development and Reform Commission published the “Strategic Plan for the Innovative Development of Intelligent Vehicles”;
-
In October 2020, the China Automotive Society published the “Energy Saving and New Energy Vehicle Technology Roadmap 2.0”.
Relevant Laws and Regulations
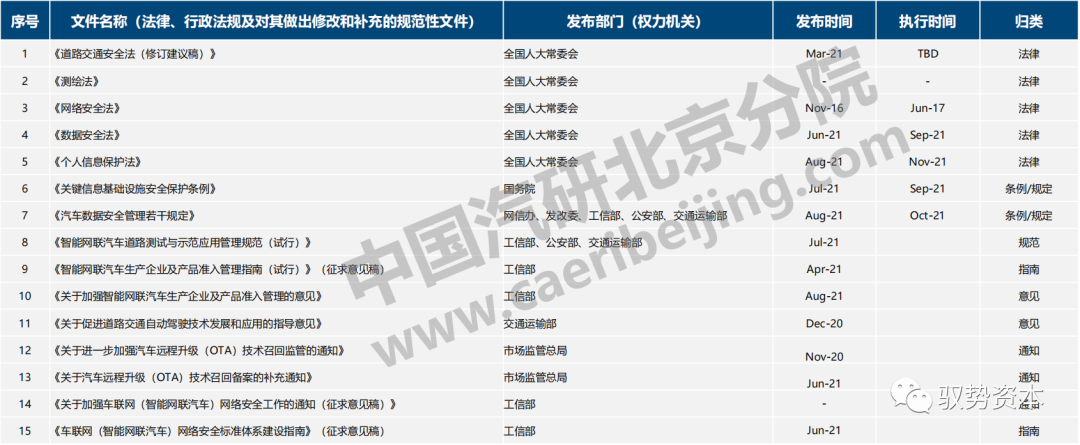
The national emphasis on information security (network security) management has led to the rapid issuance of laws, regulations, and other normative documents to strengthen information security supervision:
Summary
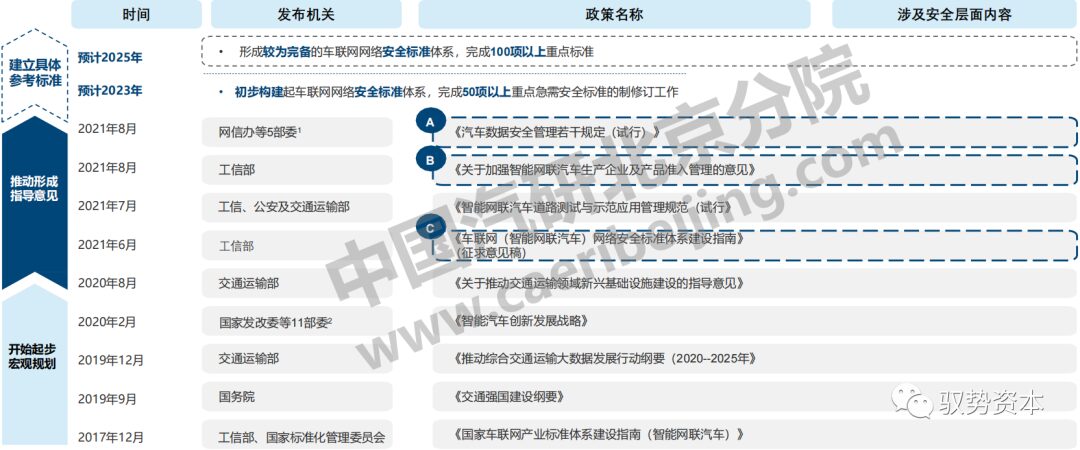
The formulation of information security policies and regulations for connected vehicles can be divided into three stages, currently in the stage of promoting the formation of guiding opinions, with the policy and regulatory system taking shape:
Notes:
-
The Cyberspace Administration and five ministries: including the National Internet Information Office, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, and Ministry of Transport;
-
The National Development and Reform Commission and 11 ministries: including the National Development and Reform Commission, Central Cyberspace Administration, Ministry of Science and Technology, Ministry of Industry and Information Technology, Ministry of Public Security, Ministry of Finance, Ministry of Natural Resources, Ministry of Housing and Urban-Rural Development, Ministry of Transport, Ministry of Commerce, and State Administration for Market Regulation.
Intelligent Vehicles
Analysis and Interpretation of Key Policies and Regulations
(Network | Data | Software Security)
The “Innovative Development Strategy for Intelligent Vehicles”
Lists network security as one of the six main tasks, particularly emphasizing the need to “build a comprehensive and efficient network security system for intelligent vehicles.”
Improve the Network Security Management Linkage Mechanism:
-
Strictly implement the national network security level protection system, focusing on the operational security of intelligent vehicle-related systems, data security, and device security, clarifying the security management responsibilities of relevant entities, and regularly conducting security supervision and inspection;
-
Establish risk assessment, operational monitoring, and emergency response mechanisms, comprehensively covering intelligent vehicle manufacturing enterprises, operational enterprises, and management institutions to prevent various illegal intrusion attacks and information security incidents.
Enhance Network Security Defense Capabilities:
-
Build a multi-layered defense and integrated hardware-software security protection system, strengthening the security design of onboard chips, application software, operating systems, and vehicle encryption;
-
Conduct safety inspections of onboard information systems, service platforms, and key electronic components, strengthening security management for remote software updates, monitoring services, etc.;
-
Implement unified identity and permission authentication management. Establish a Beidou anti-jamming and anti-deception security protection system. Establish a network security situation awareness platform for intelligent vehicles.
Strengthen Data Security Supervision and Management:
-
Establish a security management mechanism covering the entire lifecycle of intelligent vehicle data, clearly defining the data security protection responsibilities and specific requirements of relevant entities;
-
Implement classified and graded management of important data, ensuring that user information, vehicle information, mapping geographic information, etc., are secure and controllable;
-
Enhance data security supervision and inspection, conducting assessments of data risks, data outbound security, etc., and strengthening management system construction.
The importance of network security will be further reinforced. The COVID-19 pandemic has exposed shortcomings in emergency management, which will greatly promote the government’s focus on emergency response capabilities, establishing and improving monitoring, assessment, and response capabilities for social security risks, with network security being one of them. The rapid development of the intelligent vehicle industry also requires an enhancement in network security levels.
The level of network security protection will improve. In strengthening the protective capabilities of network security systems, the official version adds security inspection requirements for onboard information systems, service platforms, and key electronic components, indicating that network security will receive equal emphasis as functional safety. Additionally, the world’s first automotive network security standard ISO/SAE21434™ is expected to be released this year, which will profoundly impact the development of network security protection and regulation for intelligent vehicles.
The “New Energy Vehicle Industry Development Plan”
(2021-2035)
Integrates the development of new energy vehicles with information communication, building a network security assurance system, accelerating the improvement of road traffic, accident responsibility, data usage, and other policies and regulations that meet the requirements of intelligent connected vehicle development.
-
Promote efficient collaboration of “people-vehicle-road-cloud” based on data. Based on information from vehicle perception, traffic control, urban management, etc., build a multi-layer data integration and computing platform for “people-vehicle-road-cloud” and carry out demonstration applications in specific scenarios, regions, and roads.
-
Create a network security assurance system. Improve the network security management system for new energy vehicles, establish a unified vehicle identity authentication and security trust system, promote the in-depth application of encryption technology, strengthen safety inspections of onboard information systems, service platforms, and key electronic components, enhance the graded classification and compliant application management of new energy vehicle data, and improve risk assessment, early warning monitoring, and emergency response mechanisms to ensure information security at each link of “vehicle-end-transmission network-cloud-end”.
-
Accelerate the improvement of road traffic, accident responsibility, data usage, and other policies and regulations that meet the requirements of intelligent connected vehicle development.
The “Connected Vehicle (Intelligent Connected Vehicle) Industry Action Plan”
Focuses on management enhancement and security assurance as principles, clearly defining primary responsibilities, improving management systems, strengthening protective mechanisms, and constructing a management system that ensures personal safety.
Improve standards and promote testing and verification:
-
Accelerate the formulation and revision of related standards for basic universality of intelligent connected vehicles, advanced driving assistance systems (ADAS), autonomous driving, information security, and networking functions, using testing scenarios as a starting point and whole vehicle function evaluation as a goal, systematically conducting research and formulation of standards and specifications related to autonomous driving testing and evaluation.
-
Promote research and formulation of relevant standards for wireless communication security in connected vehicles, security of connected vehicle platforms and applications, data security, and personal information protection.
Establish a sound safety management system:
-
Focusing on the operational safety, network security, and data security of products and systems, clearly defining the responsibilities of relevant entities, and regularly conducting security supervision and inspection.
-
Improve the safety management work of incident reporting, emergency response, and responsibility identification for network and data security in connected vehicles.
Enhance security protection capabilities:
-
Focus on breakthroughs in core technology research and development for functional safety, network security, and data security in the industry, supporting the research and development of a series of security products such as security protection, vulnerability discovery, intrusion detection, and situation awareness.
-
Urge enterprises to strengthen network security protection and data security protection, construct a comprehensive safety inspection and evaluation system for intelligent connected vehicles, wireless communication networks, and data and networks of connected vehicles, and conduct safety capability assessments.
Enhance security protection capabilities:
-
Strengthen the industry’s technical support capabilities for safety, focusing on enhancing the levels of hidden danger investigation, risk discovery, and emergency response, and establishing safety platforms for monitoring and early warning, threat analysis, risk assessment, testing and verification, and data security.
-
Encourage enterprises to increase safety investment, innovate service models for safety operations and consulting, and enhance the safety assurance service capabilities of the industry.
The “Cybersecurity Law”
Clearly defines the responsible entities for network security incidents, imposing legal requirements on vehicle manufacturers, onboard information system providers, and network service operators regarding automotive information security, enabling the automotive industry to achieve “law-based compliance” in the production and operation of automotive information security functional products.
Systematically defines network security:
-
Network: Refers to a system composed of computers or other information terminals and related devices that collects, stores, transmits, exchanges, and processes information according to certain rules and procedures.
-
Network Data: Refers to various electronic data collected, stored, transmitted, processed, and generated through the network.
-
Network Operators: Refers to the owners, managers, and network service providers of the network. The open description means that whether recognized as a “network operator” mainly depends on whether the enterprise has become the owner and manager of the network information system, as well as whether its business provides various network services, especially internet information services.
-
Network Security: Refers to the ability to prevent attacks, intrusions, disruptions, destruction, and illegal use of the network through necessary measures, ensuring the network operates in a stable and reliable state and guaranteeing the integrity, confidentiality, and availability of network data. Broadly, information security should include traditional network security and data security, emphasizing network operational security and information security.
-
Critical Information Infrastructure: Important industries and fields such as public communication and information services, energy, transportation, water conservancy, finance, public services, and electronic government, as well as other critical information infrastructures that, if damaged, lose functionality or leak data, may seriously endanger national security, economic stability, and public interest. Similar to the “Cybersecurity Strategy” and the “Critical Information Infrastructure Security Protection Regulations”.
-
Personal Information: Refers to various information that can identify the identity of a natural person, recorded in electronic or other forms, including but not limited to a person’s name, date of birth, identification document number, personal biometric information, address, phone number, etc. Personal information differs from personal data and personal privacy.
Promote Safe and Trusted Network Products and Services:
-
Ensure user control over data, product or service providers should not illegally obtain users’ important data by taking advantage of the convenience of providing products or services, damaging users’ control over their own data;
-
Ensure user control over systems, product or service providers should not illegally control and manipulate users’ devices through the network, damaging users’ control over their owned and used devices and systems;
-
Ensure users’ right to choose, product and service providers should not use users’ dependence on their products and services to restrict users’ choice of using other products and services or stop providing reasonable security technical support, forcing users to upgrade, thus harming users’ network security and interests.
The “Cybersecurity Law” is the fundamental law in the field of network security in China, serving as a guiding document and basic requirement for network security work across various industries and fields in China, as well as a fundamental document that the construction of the automotive information security standard system needs to follow.
The “Data Security Law”
Achieves effective regulation of data, filling the legislative gap in data security protection, and improving the legal system for governance in cyberspace security. Data, as a new and independent protection object, has now received legislative recognition.
-
Effective regulation of data has been achieved: Although the “Cybersecurity Law” has clarified the requirement to ensure the integrity, confidentiality, and availability of network data, the emergence of data security hot events in recent years has made the demand for data protection increasingly urgent, thus necessitating a separate law targeting the field of data security protection to strengthen data regulation.
-
Enhances the national data security protection capability: Data security is an important component of national security, and with the use of new technologies such as “big data, cloud computing, and artificial intelligence,” the large-scale application of data in all scenarios poses a serious threat to national security, thus the legislation and implementation of this law can effectively enhance the capacity for data security protection.
-
Activates innovation in the digital economy and enhances the value of data utilization: Data, as a key production factor in the digital economy era, possesses significant economic value. The release of this law indicates the state encourages the lawful, reasonable, and effective utilization of data, ensuring the orderly and free flow of data, thereby promoting the development of the digital economy with data as a key element.
-
Expands the scope of data protection: Data refers to any record of information in electronic or non-electronic forms, including electronic data and non-electronic data. This broadens the requirements for data security protection compared to the data scope in the “Cybersecurity Law,” which refers specifically to network data and does not include non-electronic data.
-
Encourages the development and commercial utilization of the data industry: This law adheres to the principle of balancing security and development, clearly stating that the state insists on balancing “maintaining data security” and “promoting data development and utilization” in legislation and regulatory concepts. The law requires the construction of a data security system to ensure data security, further iterating and promoting the healthy development of the data industry, establishing and improving the data security standardization system, and supporting the development of data security assessment and certification services.
The digital economy has become an important engine supporting China’s economic development, and the development and utilization of data are key to the innovation and development of the digital economy:
-
The digital economy needs to fully explore the value of data, treating data as a production factor for development and utilization, while ensuring data security in the process of development and utilization.
-
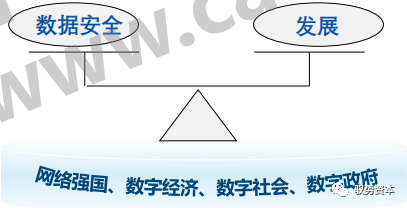
The balance between data security and development, ensuring data security while promoting data development and industry growth is complementary, and one must not neglect security in the name of development, nor hinder development in the name of security.
-
The law states that “the state coordinates development and security, insisting on promoting data security through data development and utilization, and ensuring data development and utilization through data security,” clearly indicating the state’s encouragement of lawful and reasonable data utilization to promote digital economic development.
-
The law emphasizes maintaining national data sovereignty, protecting personal and institutional data rights, reflecting the state’s high attention to the field of data security, and “encouraging lawful and reasonable data utilization while ensuring orderly and free data flow.”
The “Automotive Data Security Management Regulations (Trial)”
Address the issue of automotive data security risks that should be jointly focused on and prevented by all participants in the automotive industry chain. Automotive data processors should establish and improve compliance systems for automotive data security, in accordance with relevant regulations on automotive data security in China.
Key Points:
-
Applicable to the entire lifecycle: From the research and design of automotive products to the entire lifecycle after sales to end customers, automotive data processors should handle personal information or important data in accordance with the requirements of the “Regulations”;
-
Clarify the principles for processing personal information and important data: Advocate for the localization of storage and processing of personal information and important data onboard, and where it is necessary to provide data externally, anonymization and desensitization should be performed as much as possible;
-
Specific management requirements for automotive data processing: Automotive data processors should conduct risk assessments for important data processing activities in accordance with regulations and submit risk assessment reports to the provincial, autonomous region, or directly controlled municipality’s Cyberspace Administration and relevant departments, and should report the annual management status of automotive data security;
-
If it is necessary to provide important data abroad for business reasons, it should undergo a security assessment organized by the Cyberspace Administration in conjunction with relevant State Council departments, and automotive data processors should report relevant situations annually; when relevant departments verify the provision of important data abroad through random checks or conduct data security assessments based on their responsibilities, the relevant automotive data processors should cooperate.
What is intelligent connected vehicle data?
-
From a business perspective, data related to intelligent connected vehicles can be roughly divided into vehicle working condition data, vehicle control data, environmental perception data, geographic information data, personal data, and application service data;
-
From a legal and regulatory perspective, the data types that need to be focused on in intelligent connected vehicle data mainly include personal information, important data, and mapping geographic information;
-
The “Regulations” state: Automotive data refers to data involving personal information and important data throughout the processes of automotive design, production, sales, use, and operation.
What are the management regulations and requirements for intelligent connected vehicle data?
-
Four Principles: In-vehicle processing, default non-collection, applicable precision range, desensitization principle.
-
Three Requirements: First, all enterprises in the entire industry chain of intelligent connected vehicles should comply with data security and cross-border data flow regulatory rules; second, the law stipulates different obligations for different roles, and different data types correspond to different risks, thus enterprises should conduct graded classification management for data internally; third, enterprises should pay attention to managing data security risks in the supply chain.
How should enterprises prevent legal risks related to data security?
-
Relevant parties: Involves all upstream and downstream enterprises in the automotive industry chain, including automotive design, production, sales, use, and maintenance enterprises or institutions;
-
Focus on data lifecycle behaviors: Collection, storage, use, processing, transmission, provision, and disclosure, etc.;
-
Conduct self-examinations, identify risks, and perform compliance gap analysis;
-
Conduct comprehensive risk management for the entire chain of the supply chain;
-
Establish a data grading and classification system that meets regulatory requirements;
-
Establish and improve the data security management system.
The “Opinion on Strengthening the Management of Automotive Production Enterprises and Product Access”
Proposes strengthening data and network security management, standardizing software online upgrades, and accelerating the promotion of automotive data security, network security, online upgrades, and management requirements for enhancing the technology and network security and data security levels of intelligent connected vehicles.
Policy Interpretation: “Opinion on Strengthening the Management of Automotive Production Enterprises and Product Access”.
-
Background: In April 2021, the Ministry of Industry and Information Technology published the “Guidelines for the Management of Automotive Production Enterprises and Product Access (Trial) (Draft for Comments)”; in August 2021, the Ministry of Industry and Information Technology’s “Opinion on Strengthening the Management of Automotive Production Enterprises and Product Access” replaced the previous guideline documents.
-
Main Purpose: The “Opinion” aims to require strengthening the management of automotive data security, network security, software upgrades, functional safety, and expected functional safety management, ensuring product quality and production consistency, and promoting the high-quality development of the intelligent connected vehicle industry.
Key Points of Interpretation:
-
Compliance Requirements: Strengthen data security management capabilities; strengthen network security assurance capabilities;
-
System Level: Establish and improve the automotive data security management system; establish the automotive network security management system, especially the network security level protection system;
-
Organizational Structure Settings: Clarify the responsible departments and personnel for data security; clarify the responsible departments and personnel for network security;
-
Important Measures: Implement data security risk assessments; implement localization storage requirements; data outbound must complete outbound security assessments; implement time reporting and handling requirements for network security; real-name registration and level management requirements for connected vehicle cards.
Enterprises:
-
Establish a self-examination mechanism;
-
Report issues to the Ministry of Industry and Information Technology and the local telecommunications regulatory authorities in a timely manner.
The Ministry of Industry and Information Technology:
-
Guides relevant institutions to implement review work;
-
Accelerates the improvement of the standard system for intelligent connected vehicles;
-
Encourages third-party service institutions and enterprises to strengthen related;
-
Testing verification and inspection capability construction.
Expert Interpretation, In-Depth Perspectives:
Continues the management framework of enterprise access, product access, and supervision of product production consistency, clarifying the primary responsibilities of enterprises and the principles required.
—————— Deputy Director of the Equipment Industry Department of the Ministry of Industry and Information Technology, Zhai Guochun
Clarifies the essential capability-building requirements for enterprises, the primary responsibilities of enterprises, and the obligations they must undertake, as well as the supervisory responsibilities of industry management departments, which is internationally leading and has significant implications.
—————— Deputy Director of the China Automotive Technology Research Center, Wu Zhixin
The requirements for strengthening data security management provide direction for intelligent connected vehicle production enterprises in managing, protecting, and legally utilizing data.
—————— Deputy Director of the China Electronic Information Industry Development Research Institute, Huang Zihe
Clearly stipulates requirements for product testing, addressing the issue of what to measure, which is beneficial for third-party service institutions and enterprises to enhance testing and verification capabilities and self-examination system construction.
—————— General Manager of the China Automotive Engineering Research Institute Co., Ltd., Wan Xinming
Establishing security as the bottom line, clarifying the principles and requirements for access management will undoubtedly drive collaborative innovation and joint development of the intelligent connected vehicle industry chain.
—————— Deputy Director of the Intelligent Connected Development Institute of China FAW, Zhou Shiying
“Notice on Further Strengthening the Regulation of Remote Upgrade (OTA) Technology Recall”
Standardizes the application of OTA technology in recall work, clearly requiring producers who use OTA to eliminate automotive product defects and implement recalls to file with the State Administration for Market Regulation.
Background:
-
The increase in automotive software issues. According to statistics from the National Market Supervision Administration’s Defective Product Management Center, from 2014 to 2019, the proportion of recalls related to software in global automotive recall cases was consistently above 40%. In the Chinese market alone, as of 2019, there were 213 recalls involving program or software issues, affecting 6.8302 million vehicles, accounting for about 9% of the total recall quantity;
-
OTA is becoming normalized and popular. Using OTA technology for remote upgrades not only continuously improves the end functions and services of vehicles, providing owners with a more convenient and intelligent vehicle experience but can also be used to quickly fix vulnerabilities, helping to implement automotive recalls. It is gradually becoming an important measure for enterprises to solve software and hardware system issues.
Key Points:
-
When using OTA for technical service activities, automotive companies must file with the State Administration for Market Regulation;
-
If automotive companies use OTA to eliminate vehicle defects and implement recalls, they must also file with the State Administration for Market Regulation.
What is OTA?
-
OTA (Over-The-Air), refers to the technology for downloading over the air, which was widely used in the mobile phone industry in its early days, ending the cumbersome operation of needing to connect to a computer, download software, and then install updates.
-
In recent years, as automotive networking technology continues to develop, OTA has been widely adopted by enterprises, and automotive OTA has become a hot term in the industry.
What are the advantages and risks of OTA applications?
-
Risks: First, online data transmission must go through end-pipe-cloud and relies on the internet, posing security risks; unlike digital products, slight errors can lead to severe consequences for vehicles; second, due to the convenience of OTA, some manufacturers may prioritize speed and overlook reliability verification steps, even allowing defective vehicles to be released first and then using OTA to push patches to remedy the issues; third, there is a potential risk of internet attacks.
-
Advantages: First, it enhances efficiency and reduces costs; by online fixing software bugs, it not only saves vehicle owners the time of traveling to and from the 4S shop but also saves recall costs for the 4S shop and manufacturers; second, it adds freshness for vehicle owners and creates a property of vehicles that is not easily outdated; third, manufacturers can continue to interact with vehicle owners after sales, continuously improving user experience and expanding the scope of “services” and “operations.”
“Recall” ≠ Must Return:
-
“Recall” is merely an activity to eliminate defects, and returning to the factory is not a necessary condition!
-
Consumers do not need to let recalled vehicles leave their possession to eliminate defects, and no vehicle is physically recalled.
-
If OTA does not effectively eliminate defects or causes new defects, producers should take recall measures again (physical recall).
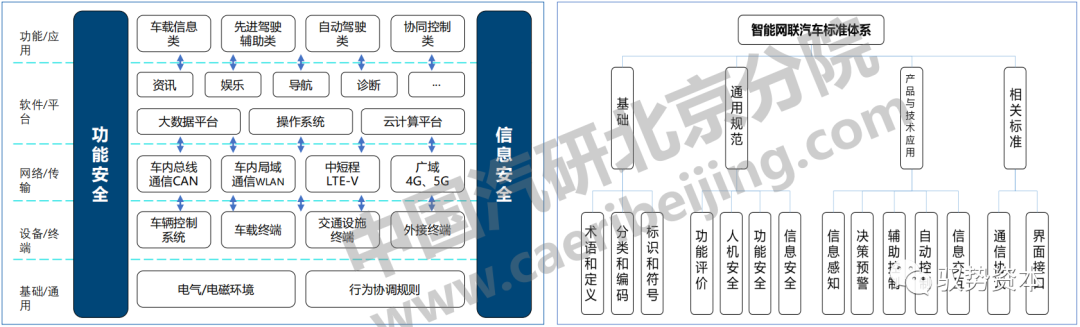
The “Guidelines for the Construction of the National Connected Vehicle Industry Standard System (Intelligent Connected Vehicles)”
Proposes general norms, core technologies, and key product applications for intelligent connected vehicles, guiding the standardization work of the connected vehicle industry purposefully, planned, and with focus, accelerating the construction of a standard system for intelligent connected vehicles that includes functional safety and information security of vehicles and key systems.
-
The physical structure of intelligent connected vehicle products includes two important components: functional safety and information security, both of which are essential conditions that various products and applications of intelligent connected vehicles must universally meet, ensuring safe, stable, and orderly operation throughout the physical structure of the product;
-
The construction of the automotive information security standard system is a systematic project, which should consider all channels, methods, and links of interaction between vehicles and external information;
-
Information security must be regarded as an important component of the standard system construction for intelligent connected vehicles.
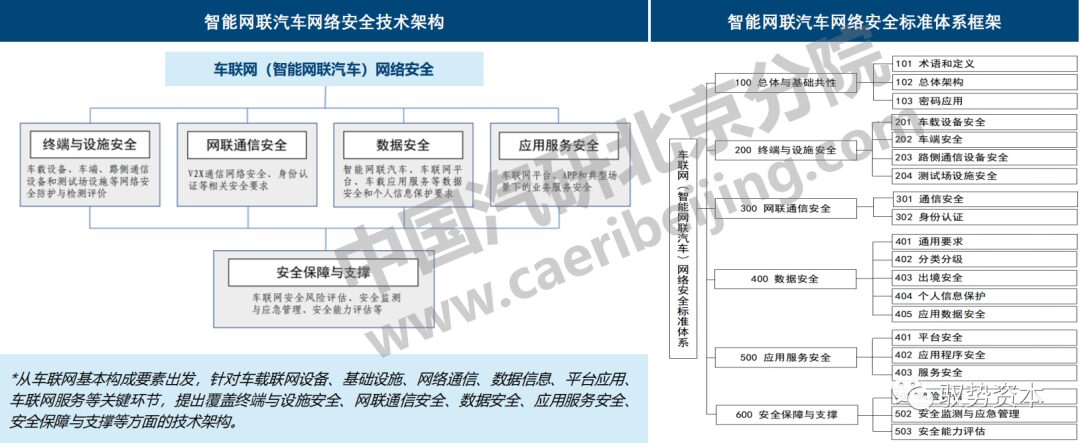
The “Connected Vehicle (Intelligent Connected Vehicle) Network Security Standard System Construction Guidelines”
Starts from key links and objects of connected vehicles, V2X communication networks, connected vehicle service platforms, connected vehicle applications, and data protection, establishing a network security standard system for connected vehicles (intelligent connected vehicles) based on typical application scenarios.
Summary
“Broadly defined, automotive information security includes the security of the vehicle itself, the information communication of the vehicle with the outside world, and the security of automotive-related information stored or transmitted by other external terminals or nodes; narrowly defined, automotive information security primarily focuses on the internal information security of the vehicle, avoiding external interference, but does not involve network security related to the vehicle’s external connections, including vehicle-to-vehicle, vehicle-to-facility, and other facilities related to automotive security.”
“The construction of the automotive information security standard system must consider both broad and narrow perspectives simultaneously. That is, narrowly ensuring that vehicles establish safe and reliable in-vehicle information security protection mechanisms that can withstand illegal external intrusions and prevent vehicle information leakage; broadly, it should ensure that vehicle information does not leak or is accessed illegally during transmission, storage, and processing from the perspectives of information interaction methods, channels, and nodes.”

Intelligent Vehicles
Assessment of Future Management Directions
of Intelligent Connected Vehicle Information Security
Regulatory Trends Will Become Stricter
Information security for intelligent connected vehicles will become increasingly important, with key policies and regulations focusing on data security, network communication security, software platform security, terminal and facility security.
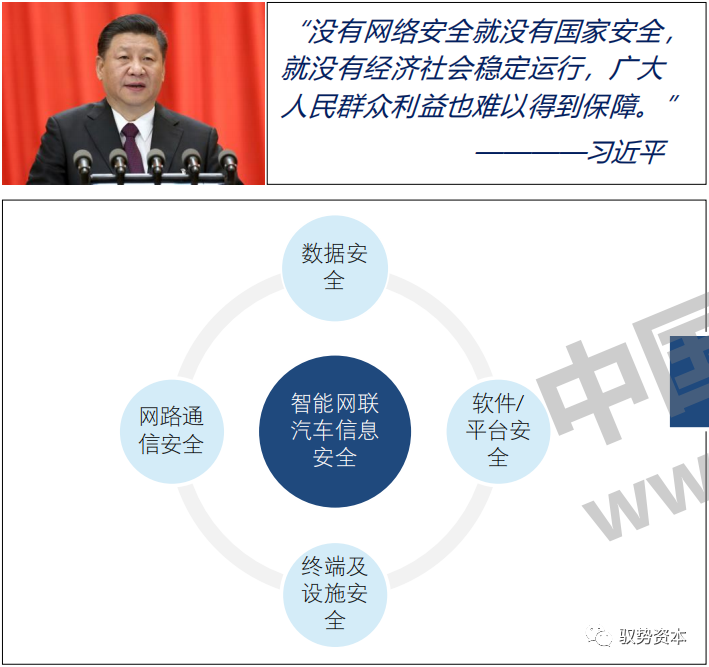

Policies and regulations related to information security have made requirements in six main areas: including national security, network security, data security, personal information security, geographic information security, and product liability and accident responsibility (including access, recalls, and OTA software upgrades, etc.).
Many laws and regulations have been published and are gradually being implemented, with stricter regulation expected in the future. First, supporting policy interpretation documents and standards will be issued successively to support the implementation of these laws and regulations. Second, the progress and intensity of information security assurance work will also accelerate and enhance. Finally, information security testing, evaluation, and certification work will also be quickly launched, with relevant authorities introducing a system for information security testing, evaluation, and certification.
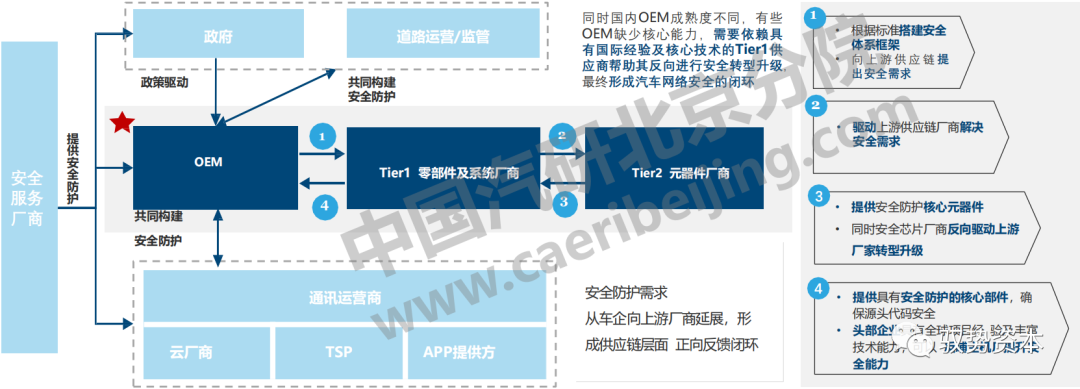
Future Regulatory Framework for Automotive Information Security
Driven by policies and regulations, the future demand for information security will center on OEMs, horizontally driving the leading manufacturers in the upstream automotive supply chain, and vertically collaborating with telecommunications operators and various cloud service providers to jointly construct a security protection and key responsibility system for suppliers within the connected vehicle system.
At the same time, the maturity of domestic OEMs varies, with some lacking core capabilities and needing to rely on Tier 1 suppliers with international experience and core technologies to assist them in reverse safety transformation and upgrading, ultimately forming a closed-loop for automotive network security;
Security protection needs will extend from vehicle manufacturers to upstream manufacturers, creating a positive feedback loop at the supply chain level.
References from: China Automotive Research Securities, Yushi Capital Research Institute
There are groups for automotive industry complete vehicles, key parts, new energy vehicles, intelligent connected vehicles, aftermarket, automotive investment, autonomous driving, connected vehicles, and dozens of others. To join, please scan the administrator’s WeChat (please indicate your company name). There are also startup financing groups, welcome to angel round and A round enterprises to join;
