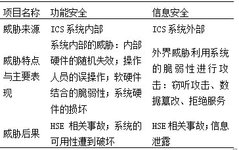
Discussion on Information Security Awareness During Cybersecurity Week: Wi-Fi Security
Discussion on Information Security Awareness During Cybersecurity Week Wi-Fi Security 01 Phishing Wi-Fi Risk Analysis In public places such as restaurants, shopping malls, train stations, and airports, free Wi-Fi hotspots are often deployed. However, attackers may create deceptive Wi-Fi hotspots. Once connected to these malicious hotspots, users may face risks such as information leakage and … Read more