Adding a Safety Lock to Children’s Smartwatches
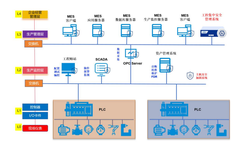
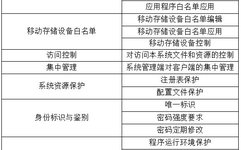
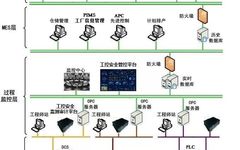
Real-time positioning, video calls, community interaction… Children’s smartwatches have become essential smart hardware for kids due to their rich and powerful features. However, due to the special nature of child users, the hidden concerns behind children’s smartwatches have also attracted widespread attention. The “Guidelines for the Protection of Personal Information and Rights of Children Using … Read more