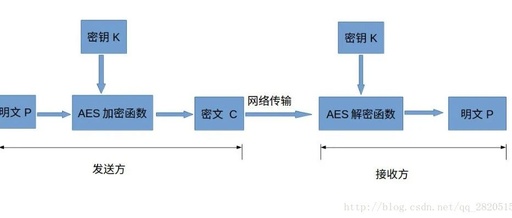
The Past and Present of Cryptographic Algorithms
Author丨labuladong Source丨labuladong The “password” mentioned here is not the same concept as the passwords we use in daily life. The cryptographic algorithms discussed in this article mainly address the issues of encryption and decryption in information transmission.We must assume that the data transmission process is insecure, and all information is being eavesdropped on, so the … Read more