Understanding Symmetric Encryption Algorithms
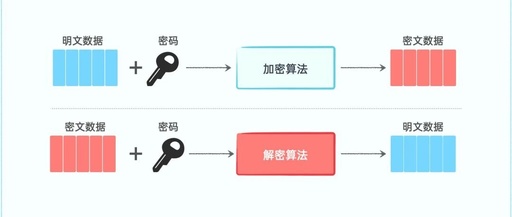
1. What is it Symmetric encryption refers to the use of the same key for both encryption and decryption. The process of encryption and decryption is illustrated in the following diagram: Symmetric encryption algorithms have the advantages of fast speed and high efficiency, but they face challenges in key distribution and are susceptible to eavesdropping. … Read more