Bouncy Castle: A Cryptographic Library for Enhanced Security!
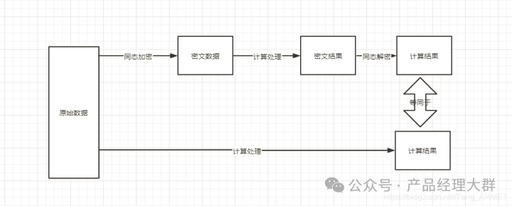
Bouncy Castle Cryptographic Library: Making Data Security Simpler! Hello everyone, I am a programmer passionate about cryptography. Today, I want to share with you the powerful cryptographic library in the Java world—Bouncy Castle. It not only provides a rich set of cryptographic algorithms but also ensures high reliability in security. As a cryptography enthusiast, I … Read more