Author: Tiandi Hexing Industrial Cybersecurity Research Institute
This article focuses on the cybersecurity issues of embedded systems, analyzes the factors affecting system security, interprets the key technologies within the system, discusses important security strategies during system development, and provides some suggestions for the security of embedded devices.
1. Past Cyber Threats
In 1971, Bob Thomas created the first computer worm virus in history, which was not malicious. It simply jumped back and forth between computers connected through local switches and displayed the message, “I’m a worm: Catch me if you can.”
The first real cyber attack occurred in November 1988 when Robert Morris created a computer worm that significantly slowed down the internet – this attack was quite serious. Morris’s motivation was not to cause damage but simply to highlight security flaws in Unix Sendmail and password management. However, the worm inadvertently caused partial internet outages that lasted for days, with estimated damages between $100,000 and $1 million.
It wasn’t until 1999, with the launch of Microsoft Windows 98, that security vendors began releasing anti-hacker software, marking the beginning of the cybersecurity industry. Since then, hackers have been closely monitoring the security of vulnerable devices. During this time, all players, whether attackers or defenders, primarily focused on computers and servers.
It is only recently that the cybersecurity of embedded systems has become an issue. As background, embedded systems are controllers located within larger systems, typically designed to perform dedicated functions. Once, embedded systems consisted of a hardware component, a firmware component, and, in some cases, an embedded operating system stacked as shown in Figure 1 below.
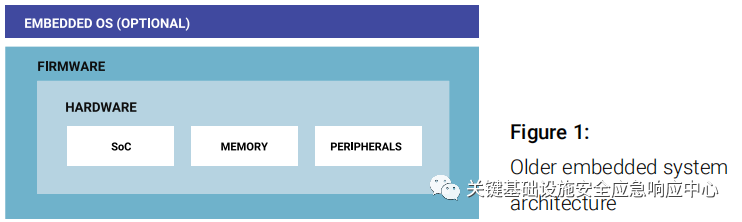
Figure 1: Older Embedded System Architecture
At that time, many embedded systems were not designed to protect themselves from attacks. The following assumptions were made, and the cybersecurity of embedded systems was not prioritized:
-
Embedded systems are not attractive targets for hackers.
-
Due to their need for complex authentication, they are not easily attacked.
-
In some cases, encryption provides sufficient protection.
2. Challenges of Embedded System Cybersecurity
In today’s market, embedded systems are becoming increasingly advanced and include many software layers in their architecture. In many cases, they perform critical tasks in increasingly complex embedded systems across various industries, from aerospace and defense to household appliances. There is much literature documenting attacks on embedded devices, from vehicle anti-theft components to control systems to printers. In the case of printers, attackers hijacked the printer and sent copies of documents to their own computers, sometimes obtaining confidential or secret information.
First, let’s take a look at the overall architecture of embedded systems. Figure 2 below shows the two layers depicted in Figure 1, which are the middleware layer and the user application layer. Middleware is software that provides services to user applications and is sometimes described as software “glue.” Some examples of middleware include databases, application servers, and content management systems. User applications are programs designed for end-users. Examples of user applications are internet browsers running on vehicle infotainment systems or Android Auto.
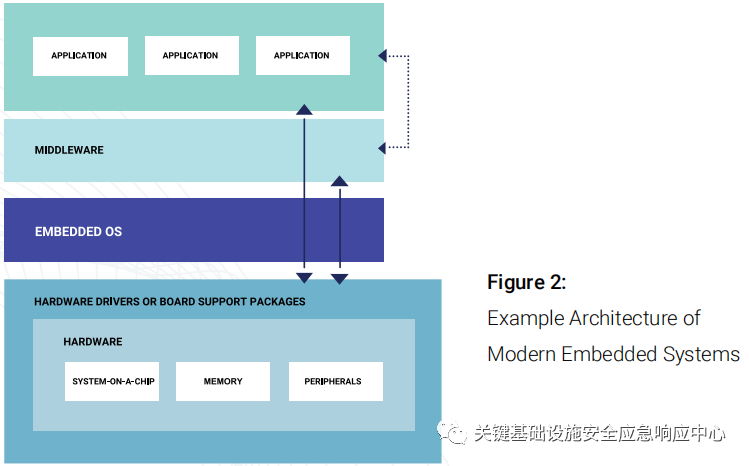
Figure 2: Example Architecture of Modern Embedded Systems
With the increasing prevalence and diversity of embedded systems, as well as their connection to the Internet of Things (IoT), attacks on these systems are becoming more frequent. The IoT refers to a system composed of interconnected computing devices as well as mechanical and digital machines. These devices can transmit data over a network without requiring human-to-human or human-to-computer interaction. The IoT involves many technologies and has evolved to include a fusion of various technologies from analytics to machine learning to embedded systems. This discussion focuses on embedded systems.
2.1How Systems Are Attacked
Embedded operating systems are often the target of attacks because they have the most control over the entire embedded system (hardware, middleware, and user application layers). Participants attacking these systems may include: researchers, hackers, organized crime, and nation-states. Various methods can be employed to develop systems, but conventional approaches follow the process outlined below:
(1) Gain network access to the system.
(2) Understand the underlying software, hardware, and embedded OS.
(3) Look for vulnerabilities in host-based protections, whether in hardware drivers, operating systems, or middleware.
(4) Operate the software.
(5) Exploit the software or the entire system.
Most embedded systems deploy at least the following defense mechanisms.
-
Hook Detection: A method for detecting attempts to alter or enhance the behavior of software (embedded operating systems, drivers, middleware, or applications).
-
Proof: A method for checking whether unauthorized processes have altered the software.
-
Firmware/Driver Integrity Verification: Tools for detecting any unauthorized changes to hardware drivers or firmware.
-
Logical Checksums: A mechanism for detecting errors that may be introduced during data transmission or storage.
-
Encryption: The process of encoding data (stored or transmitted) in a way that only authorized users can decode.
-
Authentication Methods: A mechanism for checking usernames and passwords and implementing password policies (length, complexity, expiration, etc.).
2.2Vulnerabilities by Type
The data in this figure was compiled using BlackBerry, a cloud-based Binary Static Application Security Testing (SAST) platform, to highlight categories of vulnerabilities within embedded software in the automotive industry. The report shows that of all categories of vulnerabilities discovered, approximately 70% were caused by insecure APIs. Table 1 describes the functions or attributes that may lead to vulnerabilities in each category.
Note that buffer overflow is at the top of the exploitation list under the “Insecure API” category. Buffer overflow requires special attention because it can lead to remote code execution or allow attackers to take control of the system.
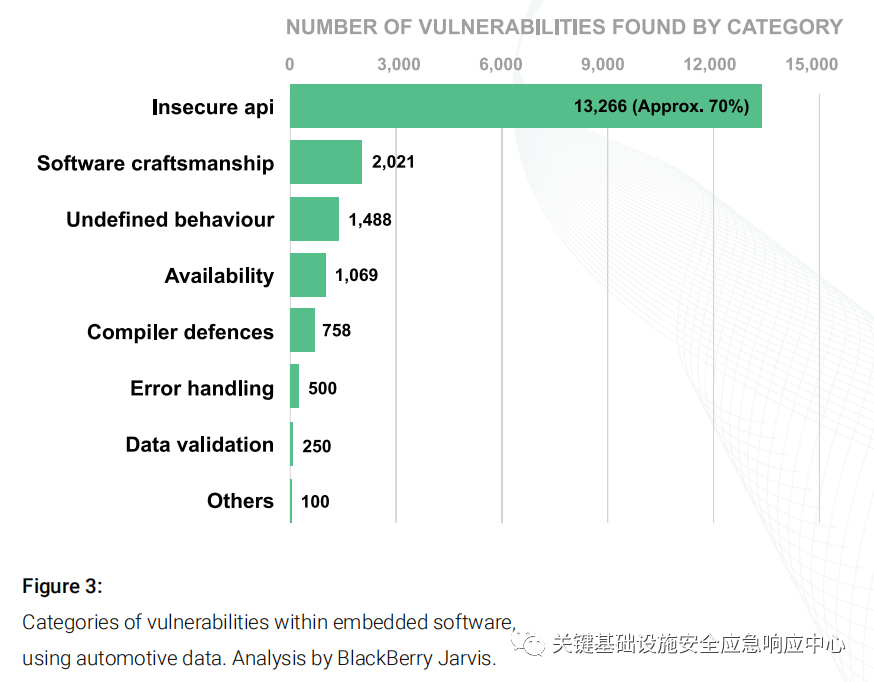
Figure 3: Categories of Vulnerabilities in Embedded Software Using Automotive Data. BlackBerry Jarvis Analysis.
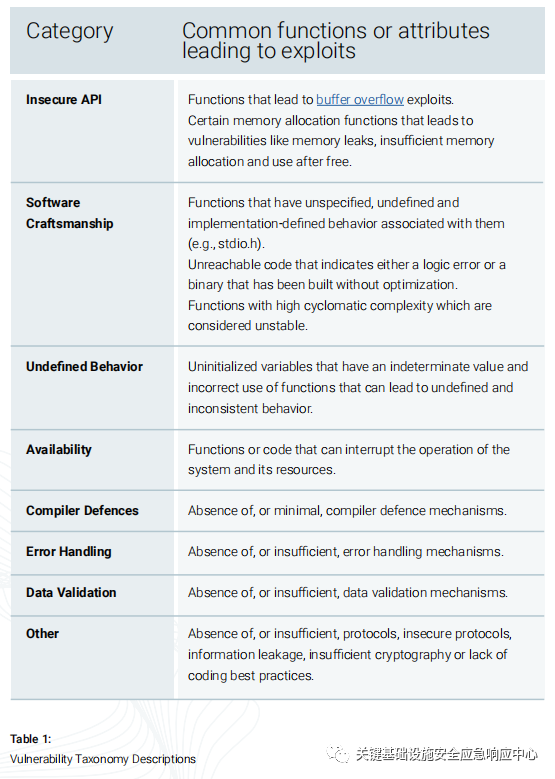
Table 1: Description of Vulnerability Categories:
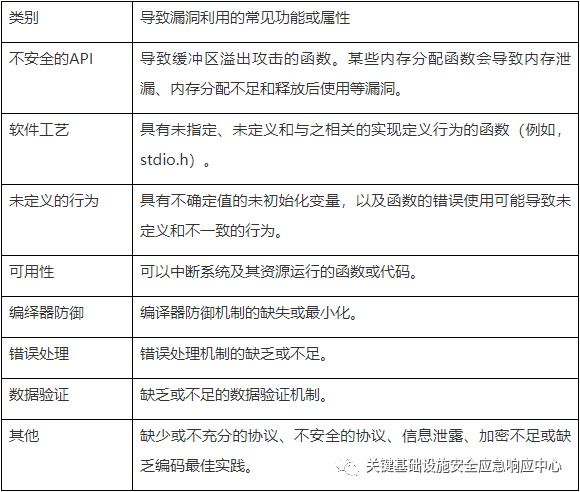
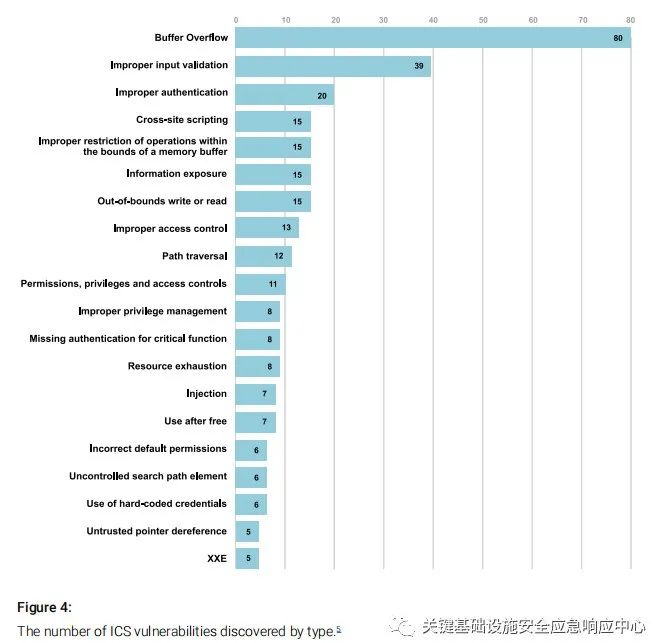
Figure 4: Number of ICS Vulnerabilities Discovered by Type
Most embedded software development is dominated by the C programming language. This is often considered a very flexible but insecure language. If operating systems, C libraries, mathematical libraries, and hypervisor security systems are certified against international standards considered most suitable for the system, such as functional safety standards ISO 26262, IEC 61508, or other standards, some known risks and vulnerabilities can be mitigated. The rigorous certification process of any of these standards (including detailed analysis for design, development, and testing) can mitigate some known risks and vulnerabilities of the C programming language.
2.3Buffer Overflow Leading to Memory Corruption
Memory corruption caused by buffer overflow is the most common vulnerability in software on embedded systems, as highlighted by the aforementioned automotive and industrial vulnerability statistics. A buffer overflow attack occurs when an attacker modifies the software to write data into a memory buffer, exceeding the buffer limits and overwriting adjacent memory buffers. This can lead to arbitrary code execution and may allow attackers to take control of the system or cause the system to crash. These types of attacks are extremely dangerous, especially when the system is performing critical tasks, such as industrial robots handling heavy materials in interaction with humans in manufacturing facilities, or advanced driver assistance systems helping navigate vehicles through traffic. Being able to attack systems through memory corruption is often complex for attackers, as it requires reverse engineering of hardware or software. Moreover, accessing the unique software of embedded systems is also challenging.
However, in today’s market, embedded systems are connected to the IoT, and in some cases, they use open-source operating systems (like Linux), which significantly increases the attack surface. Using open-source operating systems requires designing one’s own software countermeasures to protect the system and keep up with the ever-changing threats. There is no trusted third party to provide continuous security updates or help guide security strategies.
Additionally, compared to commercial devices like servers or computers (2-5 years), embedded devices have a much longer lifespan (10-20 years), making it highly challenging to update embedded device software. In fact, the development of embedded devices is considered inevitable by most system designers.
3. Recommendations for Embedded System Cybersecurity
Today, there is new hope for protecting embedded systems. Three mitigation measures against vulnerabilities are now being implemented by commercial embedded operating system vendors, commonly referred to as the three musketeers:
-
Executable Space Protection (ESP): A technique that marks specific memory areas as non-executable, so attempts to execute machine code in these areas will result in exceptions.
-
Address Space Layout Randomization: A technique involving randomly locating the base address of executable files and the locations of libraries, heaps, and stacks within a process’s address space. Random mixing means that attackers no longer know the location of the required code. This makes exploiting existing vulnerabilities more challenging.
-
Stack Canaries: A technique that allows the OS to detect stack buffer overflows before executing malicious code. This method works by placing a small integer (randomly chosen at program startup) in memory before the stack return pointer. This makes exploiting buffer overflows extremely challenging, as the stack value is checked before the OS overwrites new memory space, and if it is not the same, execution is stopped and an exception is raised.
However, not all embedded operating systems possess all these security mechanisms. In fact, according to a survey by Ali Abbasi from the University of Twente, only about 7% of the 30 most popular embedded operating systems include these mechanisms. For BlackBerry QNX users, all these mechanisms are available in both the QNX RTOS and QNX hypervisor, regardless of whether it is a security-certified version or a non-security-certified version of the RTOS.
3.1Preparing for New Threats
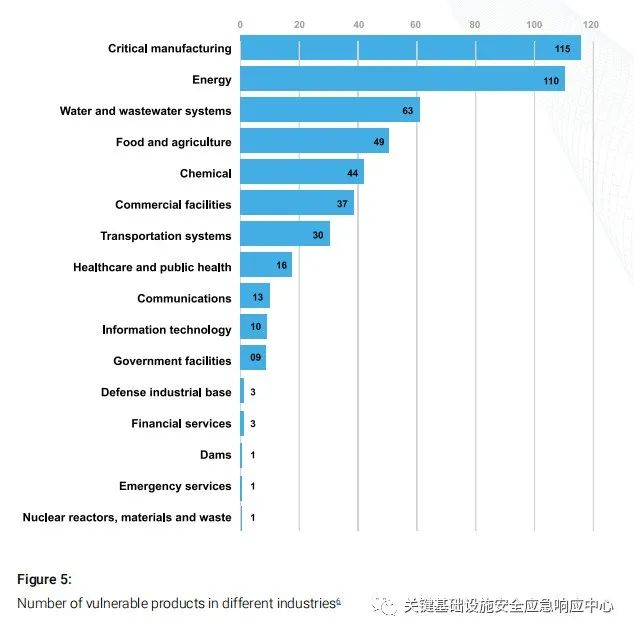
Figure 5: Number of Vulnerable Products Across Different Industries
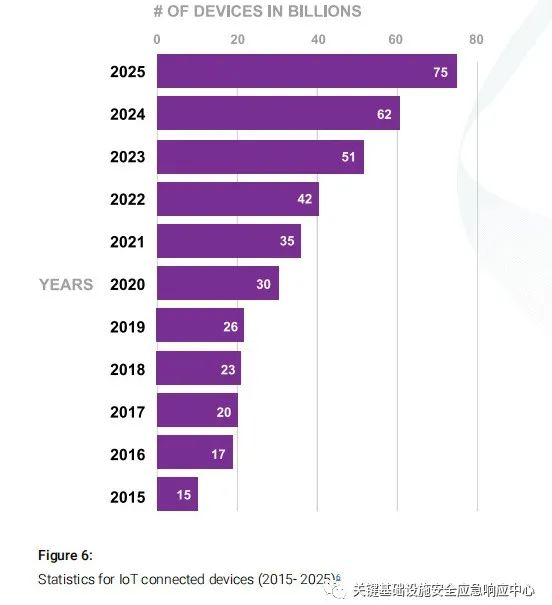
Figure 6: Statistics of IoT Connected Devices (2015-2025)
3.2Artificial Intelligence (AI) – A New Source of Threats
A new threat is emerging that can be considered one of the most significant threats we have ever seen: Artificial Intelligence (AI). These threats are not fictional threats like the artificial superintelligence system Skynet in the movie “Terminator.” Today, attacks on embedded systems leverage AI to automate systems like robots or autonomous driving systems. These attacks exist because AI algorithms have some fundamental limitations that attackers can exploit to cause systems to malfunction or behave abnormally. These attacks are different from traditional cyber attacks because they are not the result of mistakes made by programmers or users. These are all due to the shortcomings of AI. Algorithms that make AI systems work well also contain some flaws, and these limitations and defects create opportunities for cyber attacks.
3.3Operating System Security Design is the Best Defense
Embedded device manufacturers need to architect and implement security designs that ensure all layers (hardware, drivers, embedded operating systems, middleware, and user applications) are protected from tampering, data theft, communication, and malicious attacks. Unfortunately, manufacturers of these products and even security vendors do not have a one-size-fits-all security design or solution, but some of the suggestions listed below are worth following.
-
Secure Boot.
-
Authentication.
-
Intrusion Detection/Protection.
-
Embedded Security Management.
-
Security Updates.
-
Secure Communication.
-
Security Monitoring.
-
Data Security.
-
Embedded Firewalls.
-
Device Tamper Detection.
Some of the security methods and regulations identified above are interdependent. For example, to have an embedded firewall or intrusion detection/protection, it is necessary first to determine how to perform security updates, as both of these projects require frequent updates (e.g., virus definitions, signature files, or security patches) to keep up with new attacks. It should also be considered that in some cases (such as drivers or embedded operating systems), security updates may require restarting the system. For safety-critical devices or other critical devices, these should be done in a controlled environment. This is different from regular personal computer updates, where data can be saved before restarting the computer. For critical embedded systems, data loss must not occur under any circumstances.
3.4Building Cybersecurity
The key to defending against attacks now and in the future is to consider the risks and costs of successful attacks when developing systems. These costs include economic, environmental, social, informational, personal privacy breaches, and damage to brand reputation. The benefits of implementing robust security solutions far outweigh the costs of inaction. Attacks can jeopardize systems and render engineering operations, legal, and other teams unable to cope with the consequences. The risks and possibilities of these attacks and their associated attack vectors are real and increasing. When beginning to consider elements of an embedded system cybersecurity strategy, consider the following components:
-
Encryption: The process of encoding information in a way that only authorized users can access.
-
Network Communication: A method to ensure secure communication between all layers of the embedded system.
-
Lifecycle Management: Managing the entire lifecycle of cybersecurity for the product from start to finish.
-
Identity Management: A framework for policies and access lists to ensure that appropriate software or users using the embedded system have proper access to required resources (hardware or software).
-
Threat Defense: Preventing or managing cybersecurity attacks.
-
Software or Driver Updates: Safely updating software or drivers while minimizing or eliminating impact on end users and the overall functionality of the embedded system.
References
[1] “Cyber Threat Forecast Through 2022,” https://www.secureworldexpo.com/industry-news/isfthreat-horizon-report-2022
[2] “First Computer Virus”. https://history-computer.com/Internet/Maturing/Thomas.html
[3] “What the world’s first cyber attack has taught us about cybersecurity,”
https://www.weforum.org/agenda/2018/11/30-years-ago-the-world-s-first-cyberattack-set-thestage-for-modern-cybersecurity-challenges
[4] “Security Requirements for embedded devices – what is really needed?”
https://www.iconlabs.com/prod/security-requirements-embedded-devices-–-what-really-needed
[5] “20% of industrial control systems affected by critical vulnerabilities,”
https://www.bleepingcomputer.com/news/security/20-percent-of-industrial-control-systems-affected-by-critical-vulnerabilities/
[6] “IoT Connected devices installed base worldwide from 2015 to 2025”.
https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/
[7] “Attacking Artificial Intelligence: AI’s Security Vulnerability and What Policymakers Can Do About It,”
https://www.belfercenter.org/publication/AttackingAI
[8] Technical talk by Ali Abbasi of the University of Twente on the security of RTOS found in PLC’s and other devices,https://www.youtube.com/watch?v=rlic2A7VB80
[9] “Seventeen steps to safer C code,” https://www.embedded.com/seventeen-steps-to-safer-c-code/
[10] “Heading off the inevitable hack attack,”
https://www.sme.org/technologies/articles/2017/october/heading-off-the-inevitable-hack-attack/
Original Source: Critical Infrastructure Security Emergency Response Center
