In this paper, we will briefly discuss the principles and practices of computer encryption algorithms.
Friendly reminder: Don’t be scared off by the word “paper”; in fact, understanding a high-level paper is quite simple!
Those who frequently surf the internet surely know that the security of computers and mobile phones is extremely important. A long time ago, there was a young man who didn’t understand data security; his name was Chen Guanxi, and the rest of the story is well known.
How can we protect important data? One important method is encryption. We often hear about various encryption algorithms and digital certificates, but how exactly does a computer encrypt data? By the end of this paper, you will understand.
Signature Algorithm
A signature algorithm is not just writing your name in the “signature” section when receiving a salary. Here, the signature is a computation performed on the message content to obtain a feature code, which is used as the signature.
What’s the use of a signature?
Let’s look at a true story that happened in a classroom.
Xiao Ming (gender: male) has long admired the goddess Xiao Hong and finally mustered the courage to write a few words on the back of his math book during class, hoping the goddess would see it. Unfortunately, the goddess sat too far away, so Xiao Ming asked his buddy Lao Wang (who sat between Xiao Ming and the goddess) to copy his message, and thus Xiao Ming successfully confessed his feelings:
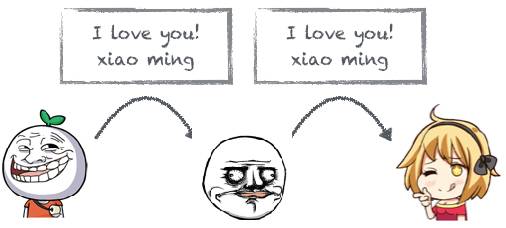
However, Lao Wang has a characteristic: he is particularly unreliable, and due to his poor eyesight, he mistakenly copied “xiao ming” as “xiao ning”, leading the goddess to mistakenly believe that it was class leader Xiao Ning confessing to her:
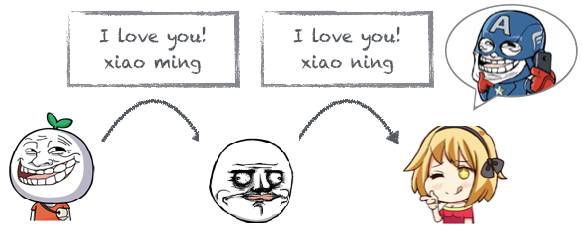
After this painful lesson, Xiao Ming decided to add a signature to his message so that if Lao Wang made a mistake, the goddess could check the signature and notice the issue:
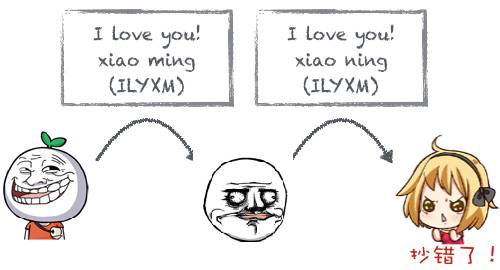
It can be seen that signatures are used to determine whether a message has been altered. If the message has been modified, the computed signature will not match the original signature.
In computers, MD5 or SHA1 is often used as a signature algorithm. The string of seemingly random numbers d41d8cd9… that you see is an MD5 signature. Those who often download software online using Thunder can use specialized software to calculate the MD5 signature of the downloaded file and then compare it with the official website; if they match, it indicates that the software has not been tampered with.
However, signature algorithms are not encryption algorithms and cannot be used for encryption; their purpose is to prevent tampering.
Symmetric Encryption Algorithm
If a message is encrypted with a password and decrypted with the same password, this encryption algorithm is called a symmetric encryption algorithm.
Since Xiao Ming started flirting with the goddess, he often sends notes to her during class, of course, through the intermediary Lao Wang.
Unexpectedly, Lao Wang has also long coveted the goddess, and he secretly altered Xiao Ming’s note, resulting in the goddess wanting to break up with Xiao Ming right after class:

Xiao Ming used all his strength to finally explain himself to the goddess. But to continue passing notes, he couldn’t avoid Lao Wang. What to do? Xiao Ming searched on his phone and finally found the AES encryption algorithm!
AES encryption is to encrypt a message into ciphertext with a password, and the other party decrypts it with the same password. Since the same password is used, it is called symmetric encryption.
Xiao Ming and the goddess agreed to use her birthday as the password:
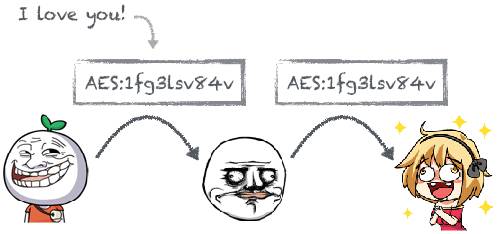
However, the battle-hardened Lao Wang quickly guessed the password. Should they change to a new password regularly?
If they use a random password each time, then Lao Wang wouldn’t be able to guess it! Xiao Ming thought of this good idea and couldn’t help but applaud his own cleverness!
But, how to inform the goddess of the random password before passing the note? Through Lao Wang? Haha!
Xiao Ming fell into deep thought again.
DH Key Exchange Algorithm
The math class representative reminded Xiao Ming: You are now facing the problem that both parties need to agree on a password, but must transmit the password through an insecure channel, so you need the DH key exchange algorithm!
It turns out that studying math is so useful! Xiao Ming quickly brushed up on the Diffie-Hellman key exchange algorithm and found it very simple!
First, Xiao Ming selects a prime number and a base, for example, prime number p=23, base g=5 (the base can be any), then chooses a secret integer a=6, calculates A=g^a mod p=8, and then sends a note to the goddess: p=23, g=5, A=8;
After receiving the note, the goddess also selects a secret integer b=15, then calculates B=g^b mod p=19, and sends a note back to Xiao Ming: B=19;
Xiao Ming calculates the password s=B^a mod p=2, and the goddess also calculates the password s=A^b mod p=2, so the password agreed upon by Xiao Ming and the goddess is 2.
And all this happened under Lao Wang’s nose, yet he could not calculate the password agreed upon by Xiao Ming and the goddess:
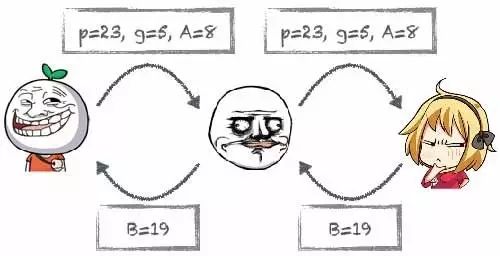
Man-in-the-Middle Attack
Since Lao Wang cannot know the password agreed upon by Xiao Ming and the goddess, he changed his approach: when Xiao Ming is negotiating the password, Lao Wang pretends to be the goddess, and when negotiating with the goddess, he pretends to be Xiao Ming, thus successfully using a man-in-the-middle attack to obtain the password!
Asymmetric Encryption
Xiao Ming once again sought help from the math class representative.
“It seems that to deal with a master like Lao Wang, you need to use RSA asymmetric encryption.” The math class representative said slowly, “You and the goddess each generate your own public and private keys, then make your public keys public, for example, write them on the blackboard at the back of the classroom. If you want to send a message to the goddess, you encrypt it with her public key, then sign it with your private key, she decrypts the message with her private key and verifies the signature with your public key. Lao Wang doesn’t have either of your private keys, so he can’t decrypt or tamper with it!”
Xiao Ming excitedly generated his RSA public and private keys with the goddess. Now Xiao Ming no longer has to worry about Lao Wang; from the beginning of class, he started using the RSA algorithm to encrypt the content of his notes. Due to the large amount of computation involved in the RSA algorithm, Xiao Ming did not finish calculating until after class.
The math class representative patted Xiao Ming on the shoulder and said, “For encryption, you still need to use a computer to calculate. Learn some JavaScript, and you can write code to let the computer help you encrypt! Click Read the original text to directly learn how to implement encryption and decryption using JavaScript!”