Fundamentals of Networking
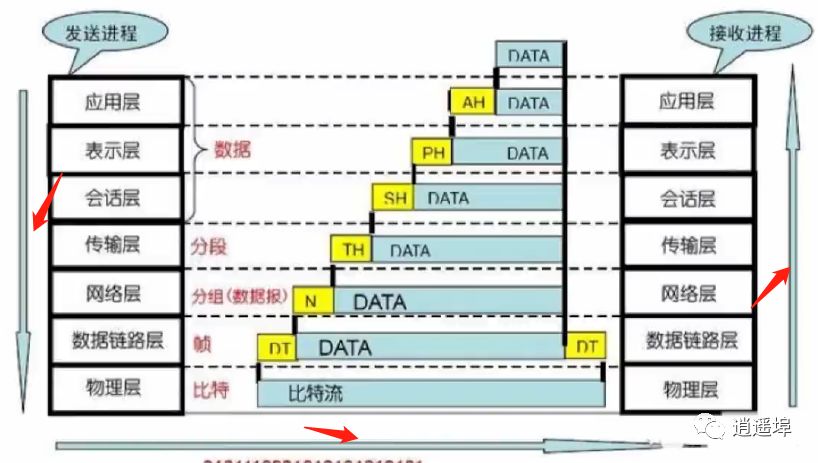
1、OSI(Open System Interconnection)Open System Interconnection Model
Seven-layer model:
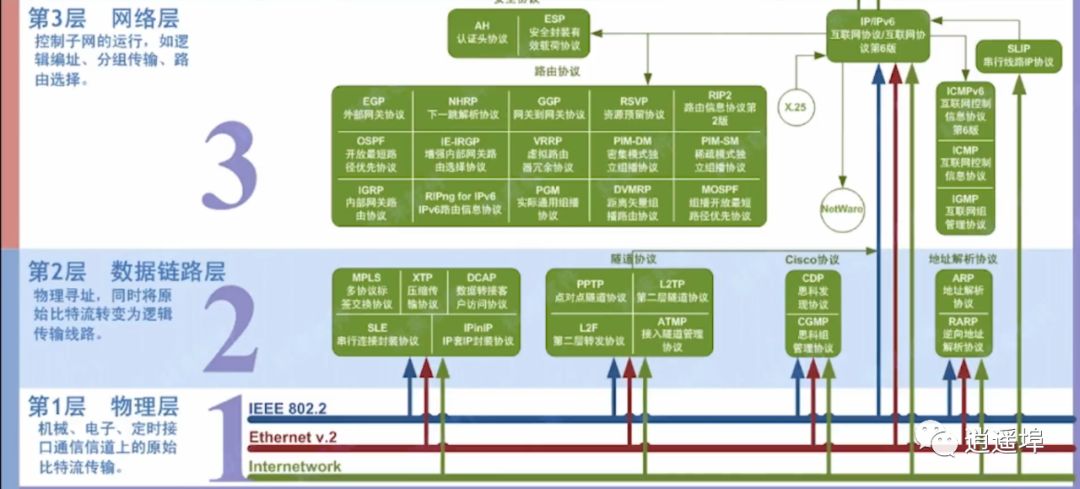
Layer 1: Physical Layer : Transmission of raw bit streams over mechanical, electronic, and timing interfaces communication channels
Layer 2: Data Link Layer: Physical addressing, while transforming the raw bit stream into logical transmission lines
Layer 3: Network Layer: Controls the operation of subnets, such as logical addressing, packet transmission, and routing
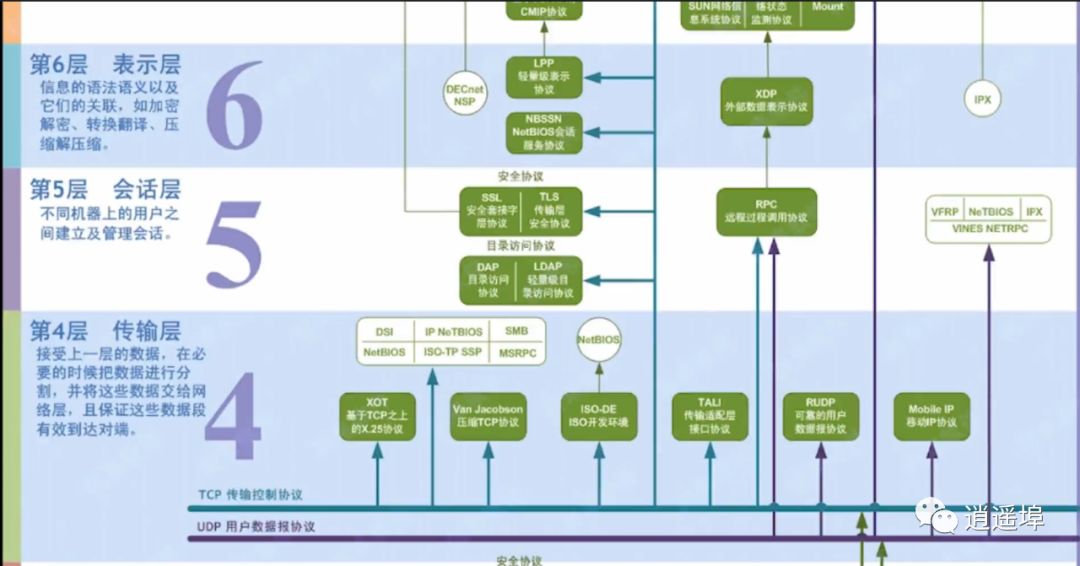
Layer 4: Transport Layer: Receives data from the previous layer, segments the data when necessary, and hands it over to the network layer, ensuring these segments reach the destination effectively.
Layer 5: Session Layer: Establishes and manages sessions between users on different machines.
Layer 6: Presentation Layer: The syntax and semantics of information and their relationships, such as encryption/decryption, translation, and compression/decompression.
Layer 7: Application Layer:
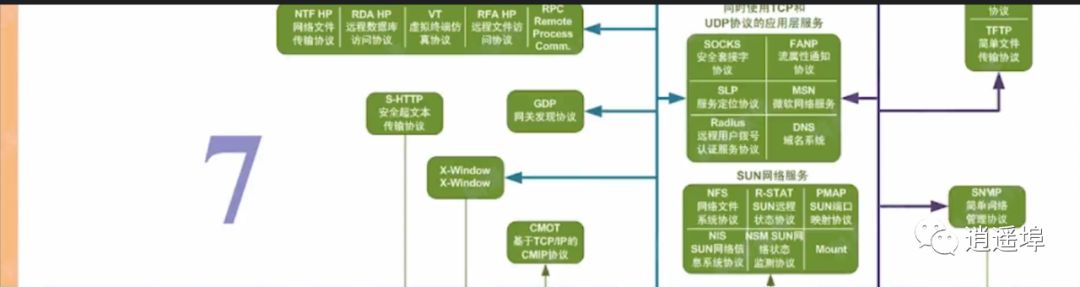
OSI Open Systems Interconnection Reference Model
Process data headers from top to bottom and then from bottom to top
2、TCP/IP
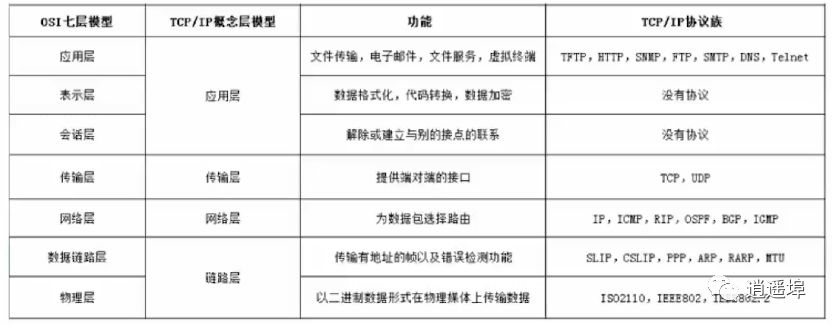
Implementation of OSI: TCP/IP
Comparison of OSI and TCP/IP:
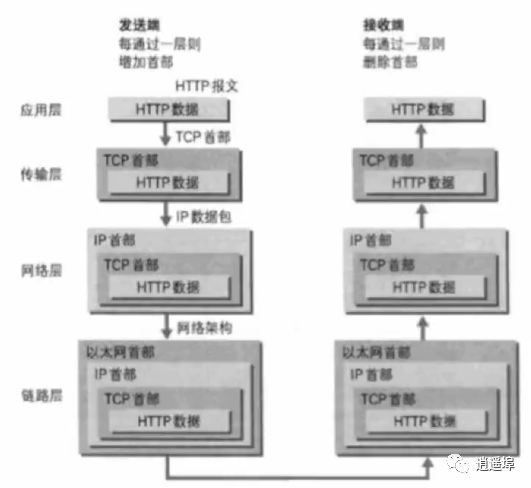
Process data headers from top to bottom and then from bottom to top:
2、Discuss TCP‘s Three-Way Handshake
Introduction to TCP (Transmission Control Protocol):
1、Connection-oriented, reliable, byte-stream-based transport layer communication protocol.
2、Segments the application layer data stream and sends it to the target node’s TCP layer.
3、Packets have sequence numbers, and the recipient sends an ACK confirmation upon receipt; if not received, retransmission occurs.
4、Uses checksums to verify data integrity during transmission.
TCP Header:
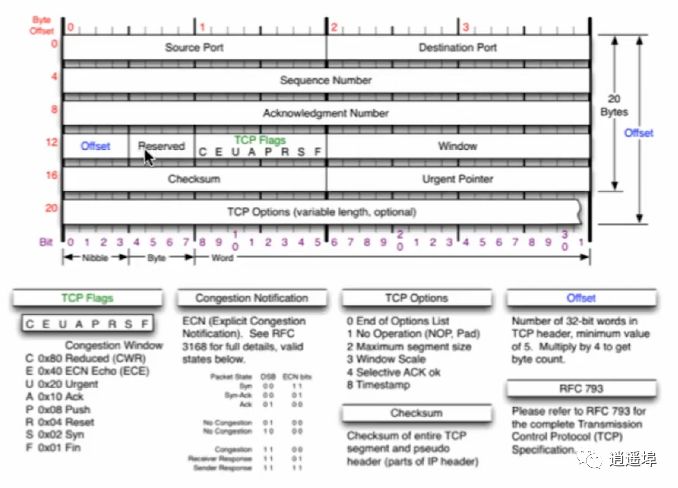
TCP Flags:
1、URG: Urgent Pointer Flag
2、ACK: Acknowledgment Number Flag
3、PSH: Push Flag
4、RST: Reset Connection Flag
5、YSN: Synchronization Number, used in the connection establishment process
6、FIN: Finish Flag, used to release the connection
Window: Flow control function.
CheckSum:
Urgent Pointer:
TCP Options:
“Handshake” is for establishing a connection; the flow chart of TCP’s three-way handshake is as follows:
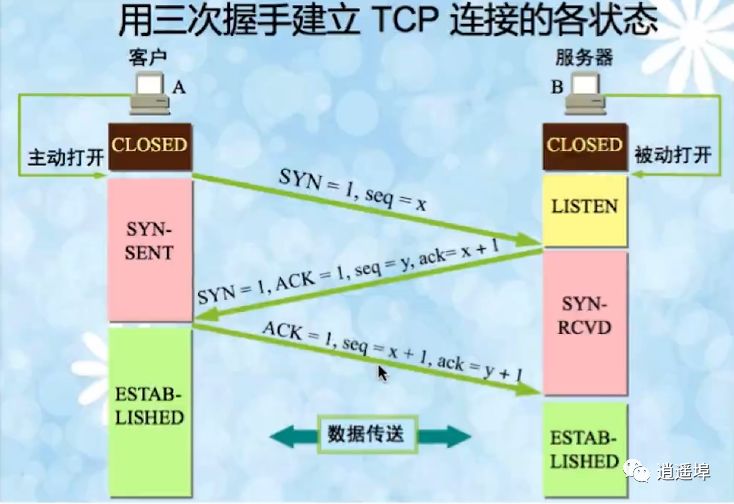
*** (Understanding and Memorizing) Detailed Explanation of TCP/IP Three-Way Handshake:
In the TCP/IP protocol, the TCP protocol provides reliable connection services, establishing a connection using a three-way handshake.
First Handshake: When establishing a connection, the client sends a SYN packet (seq=x) to the server and enters SYN_SENT state, waiting for server confirmation.
Second Handshake: The server receives the SYN packet, must confirm the client’s SYN(ack=x+1), while also sending a SYN packet (seq=y), that is, the SYN+ACK packet, at this point the server enters SYN_RECV state.
Third Handshake: The client receives the server’s SYN+ACK packet, sends a confirmation packet ACK (ack=y+1), after sending this packet, both the client and server enter ESTABLISHED state. The three-way handshake is complete.
Why is three-way handshake necessary to establish a connection?
To initialize the Sequence Number initial value
Risks of the First Handshake: SYN Timeout
Problem Analysis:
1、Server receives the Client‘s SYN, but does not receive the ACK confirmation when replying with SYN-ACK.
2、Server keeps retrying until timeout (5 times), with Linux default waiting63 seconds (1+2+4+8+16+32) before closing the connection.
Regarding the retry mechanism, there may be malicious SYN Flood attacks:
Protection Measures against SYN Flood:
1、After the SYN queue is full, respond with SYN cookies through the tcp_syncookies parameter.
2、If it is a normal connection, the Client will return the SYN_Cookie, establishing the connection directly
What to do if the Client fails after establishing the connection?
Measures: Keep-alive mechanism
1、Send keep-alive probes; if no response is received, continue to send.
2、If attempts reach the keep-alive probe count and no response is received, interrupt the connection
4、Discuss TCP‘s Four-Way Handshake
“Handshake” is for terminating a connection; the flow chart of TCP’s four-way handshake is as follows:
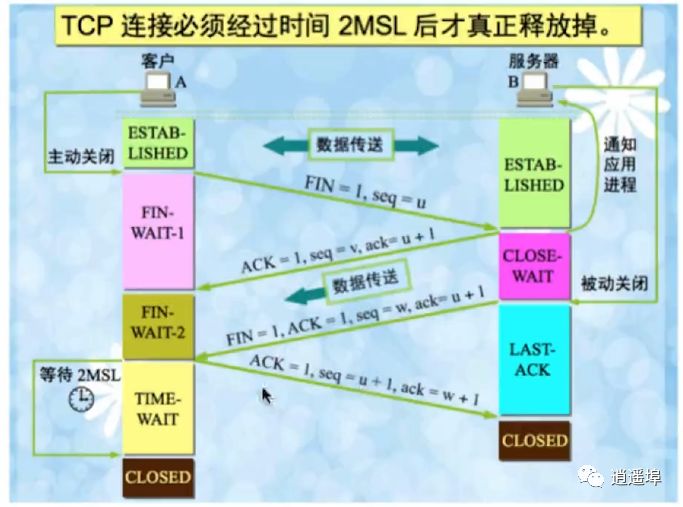
Detailed Explanation of TCP’s Four-Way Handshake Process:
1、First Handshake: The Client sends a FIN to close the Client to Server data transmission, entering FIN_WAIT_1 state;
2、Second Handshake: The Server receives the FIN and sends an ACK to the Client, confirming the sequence number received +1 (similar to SYN, one FIN occupies a sequence number), entering CLOSE_WAIT state.
3、Third Handshake: The Server sends a FIN to close the Server to Client data transmission, entering LAST_ACK state.
4、Fourth Handshake: The Client receives the FIN, enters TIME_WAIT state, then sends an ACK to the Server, confirming the sequence number received +1, and the Server enters CLOSED state, completing the four-way handshake.
Why is there a TIME_WAIT state?
Reason:
1、To ensure sufficient time for the other party to receive the ACK packet
2、To avoid confusion between old and new connections
Why is four-way handshake necessary to disconnect?
Reason: Because it is full duplex, both the sender and receiver need FIN and ACK packets
Reasons for a large number of CLOSE_WAIT states on the server:
The other party closes the socket connection, while we are busy reading or writing, failing to close the connection in time
Solution: 1、Check the code, especially the resource release code 2、Check the configuration, especially the request handling thread configuration
5、UDP Introduction
UDP Packet Structure:
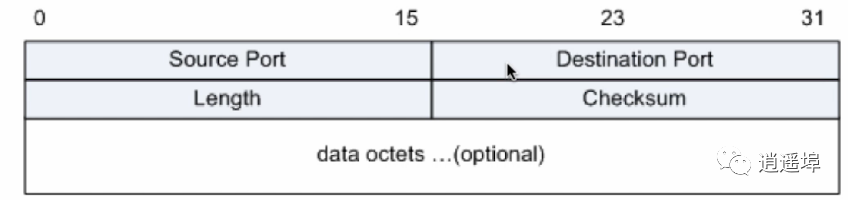
Characteristics of UDP:
1、Connectionless
2、Does not maintain connection state, supports simultaneous transmission of the same message to multiple clients
3、Packet header is only 8 bytes, with minimal overhead.
4、Throughput is only limited by data generation rate, transmission rate, and machine performance
5、Best-effort delivery, does not guarantee reliable delivery, does not require maintaining a complex connection state table
6、Message-oriented, does not split or merge the message information submitted by the application
Differences between TCP and UDP:
1、TCP is connection-oriented, while UDP is connectionless
2、TCP is reliable, with features like handshaking and retransmission
3、Orderliness, TCP uses sequence numbers, while UDP does not guarantee order
4、Speed: TCP is slower, while UDP is faster, suitable for TV broadcasting and live streaming,
5、Size: TCP has a larger overhead, while UDP has a smaller overhead
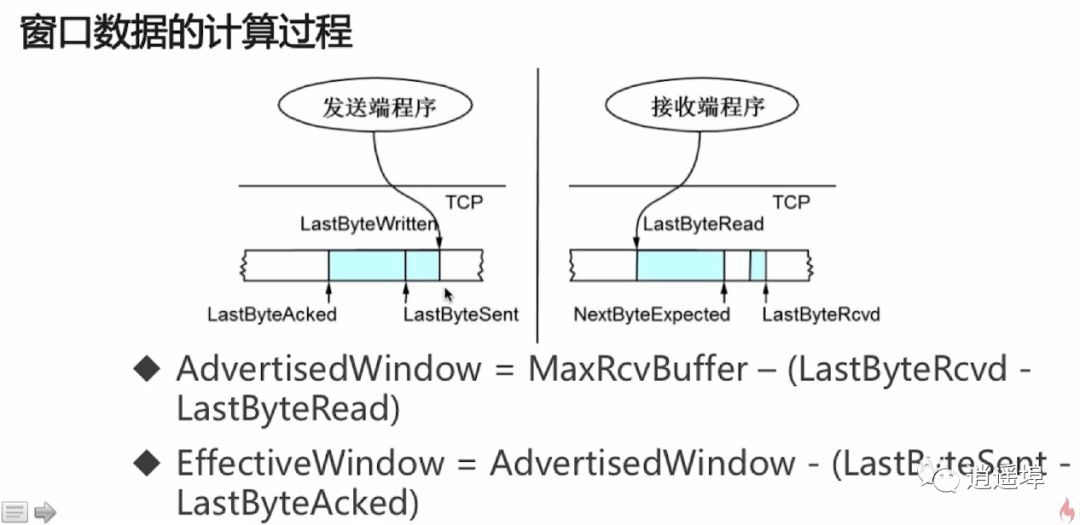
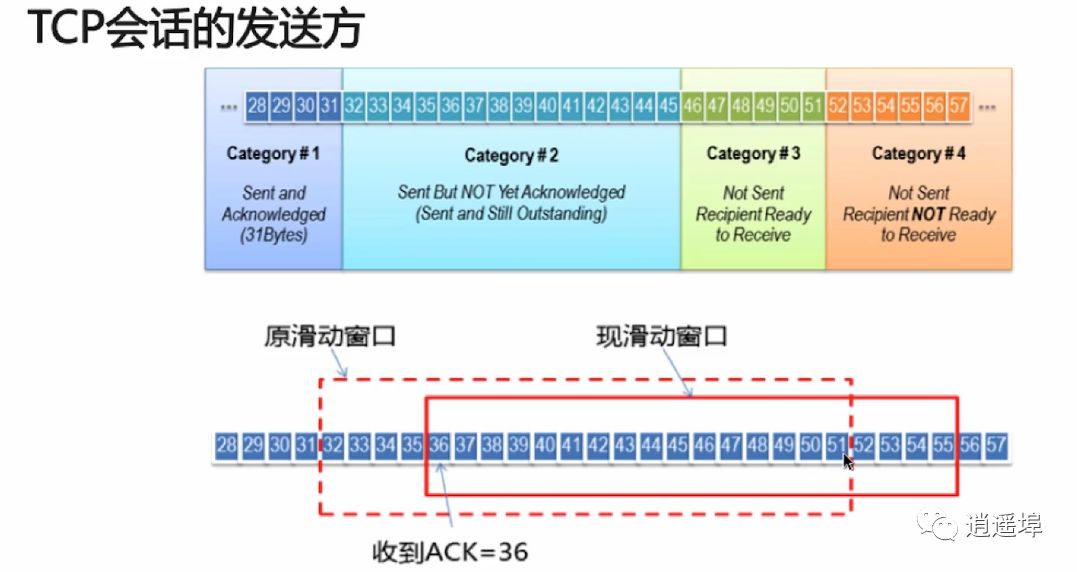
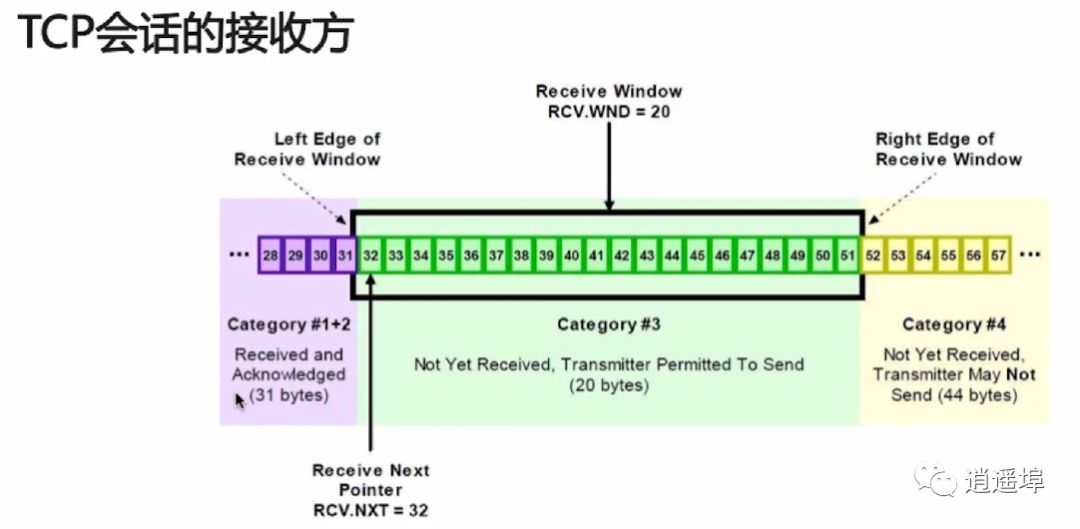
6、TCP Sliding Window
RTT and RTO
RTT: Round-Trip Time: Time taken to send a data packet and receive the corresponding ACK.
RTO: Retransmission Time Out: Time interval for retransmission
TCP uses sliding window for flow control and out-of-order reassembly:
1、Ensures TCP reliability
2、Ensures TCP flow control characteristics
1、HTTP Introduction
Hypertext Transfer Protocol HTTP Main Features:
1、Supports client/server model
2、Simple and fast
3、Flexible
4、Connectionless
5、Stateless
HTTP Request Structure:
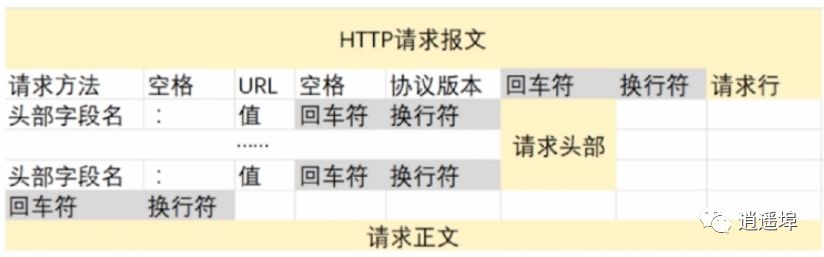
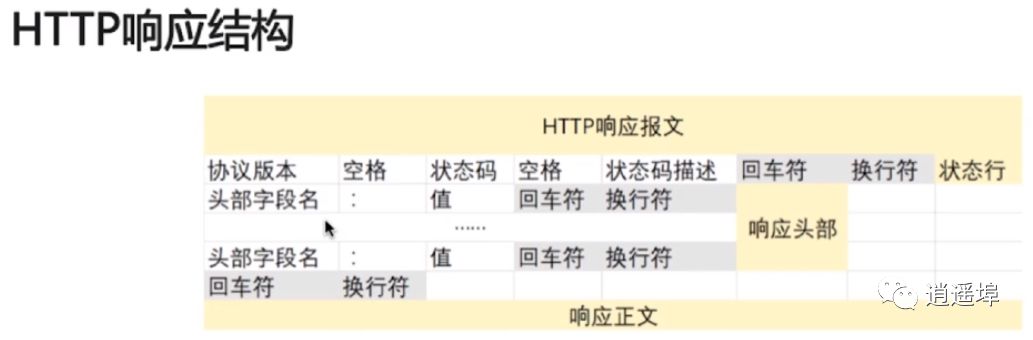
Steps of Request/Response:
1、The client connects to the Web server
2、Send HTTP request
3、The server accepts the request and returns an HTTP response
4、Release TCP connection
5、The client browser parses HTML content
Interview Question: What happens when you type a URL into the browser’s address bar and hit enter?
Answer:
1、DNS resolution (finding the IP address) Browser cache–>System cache–>Router cache–>ISP server cache–>Root domain name server cache–>Top-level domain name server cache
2、TCP connection (establishing a connection with the server IP:Port)
3、Send HTTP request
4、The server processes the request and returns the HTTP message
5、The browser parses and renders the page
6、Connection ends
HTTP Status Codes
Five possible values:
1、1xx: Informational — Indicates that the request has been accepted and is being processed
2、2xx: Success – – Indicates that the request has been successfully received, understood, and accepted
3、3xx: Redirection — Further action is required to complete the request
4、4xx: Client Error — Indicates that there is a syntax error in the request or the request cannot be fulfilled
5、5xx: Server Error — Indicates that the server failed to fulfill a valid request
Common Status Codes:
200 OK : Normal return of information
400 Bad Request: Client request has a syntax error, cannot be understood by the server
401 Unauthorized : Request not authorized, this status code must be used with theWWW-Authenticate header
403 Forbidden: Server received the request but refuses to provide service
404 Not Found: Requested resource does not exist, e.g., incorrect URL
500 Internal Server Error : Unexpected error occurred on the server
503 Server Unavailable : The server cannot currently handle the client’s request, may recover after some time
Differences between Get and Post requests:
Answer:
1、HTTP message level: Get puts request information in the URL, Post puts it in the message body
2、Database level: Get requests are idempotent and safe, Post requests are not
3、Other levels: Get can be cached and stored, while Post cannot
Differences between Cookie and Session:
Cookie:
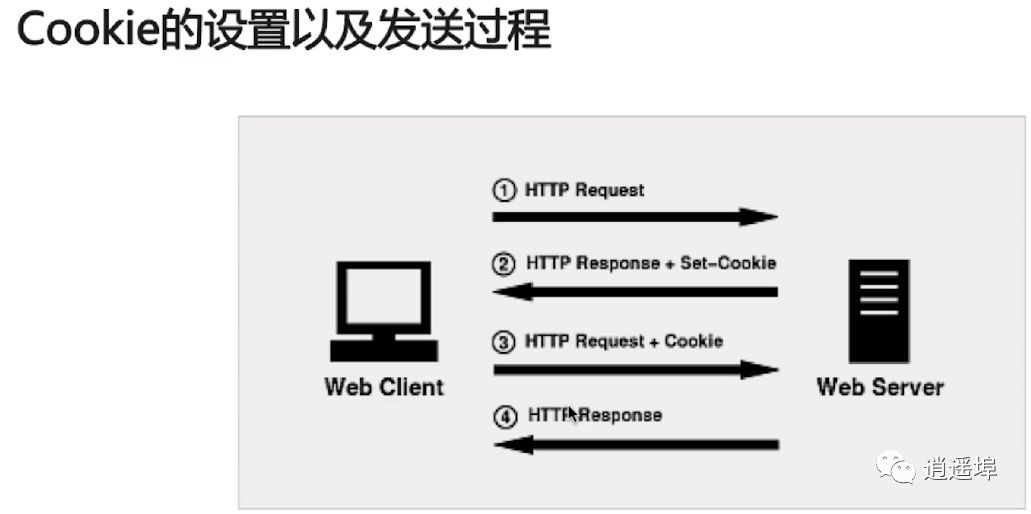
1、Special information sent from the server to the client, stored as text on the client.
2、When the client requests again, it sends the Cookie back to the server
3、After the server receives it, it parses the Cookie to generate content corresponding to the client
Cookie setting and sending process:
Session
1、Server-side mechanism that saves information on the server
2、Parses client requests and operates on session id, saving state information as needed
Session implementation methods:
1、Using cookies for implementation:
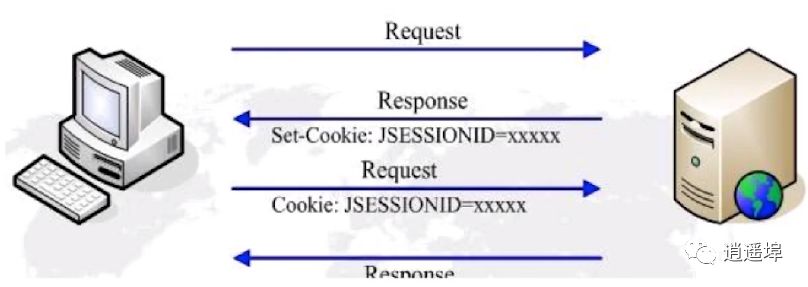
2、Using URL rewriting for implementation
Differences:
1、Cookie data is stored in the client’s browser, while Session data is stored on the server.
2、Session is more secure than Cookie.
3、If considering reducing server load, use Cookie.
8、Differences between Http and Https
HTTPS Introduction:
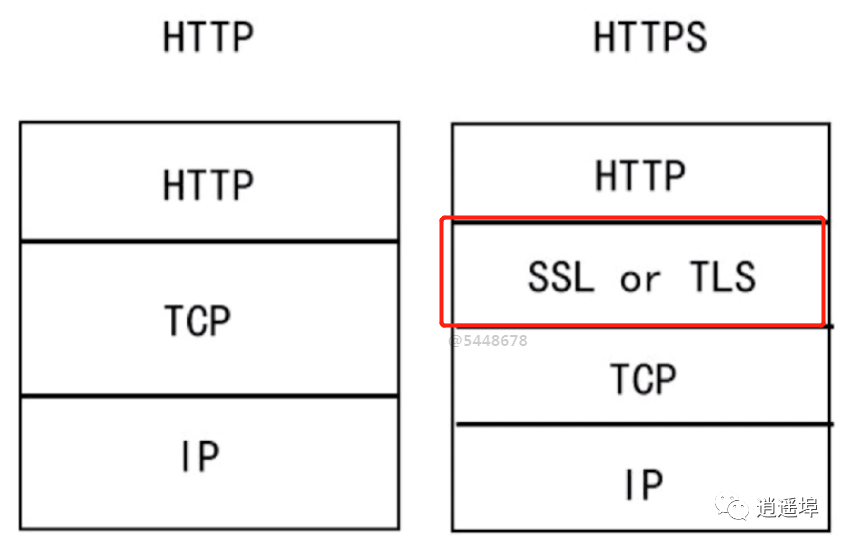
Https adds a layer of SSL or TLS
SSL (Security Sockets Layer)
1、Provides security and data integrity for network communication
2、API provided by the operating system, SSL3.0 was renamed to TLS
3、Uses authentication and data encryption to ensure the security of network communication and data integrity
Encryption methods:
1、Symmetric encryption: the same key is used for both encryption and decryption
2、Asymmetric encryption: different keys are used for encryption and decryption
3、Hash algorithms: converting information of any length into a fixed-length value, the algorithm is irreversible
4、Digital signatures: proving that a message or file is sent/acknowledged by someone
Https Data Transmission Process:
1、The browser sends the supported encryption algorithm information to the server
2、The server selects a set of encryption algorithms supported by the browser and sends it back to the browser in the form of a certificate
3、The browser verifies the legitimacy of the certificate and encrypts information to send to the server using the certificate’s public key
4、The server uses its private key to decrypt the information, verifies the hash, and encrypts the response message back to the browser
5、The browser decrypts the response message, verifies the message, and then encrypts the interactive data
Differences:
1、HTTPS requires applying for a certificate from a CA, while HTTP does not
2、Https transmits encrypted data, while http transmits plain text
3、Different connection methods, https defaults to using port 443, while http uses 80 port
4、https = http + encryption + authentication + integrity protection, making it more secure than http
Is Https really secure?
Not necessarily;
Because browsers default to filling in http://, requests need to be redirected, which poses a risk of interception
HSTS (HTTP Strict Transport Security) can be used for optimization
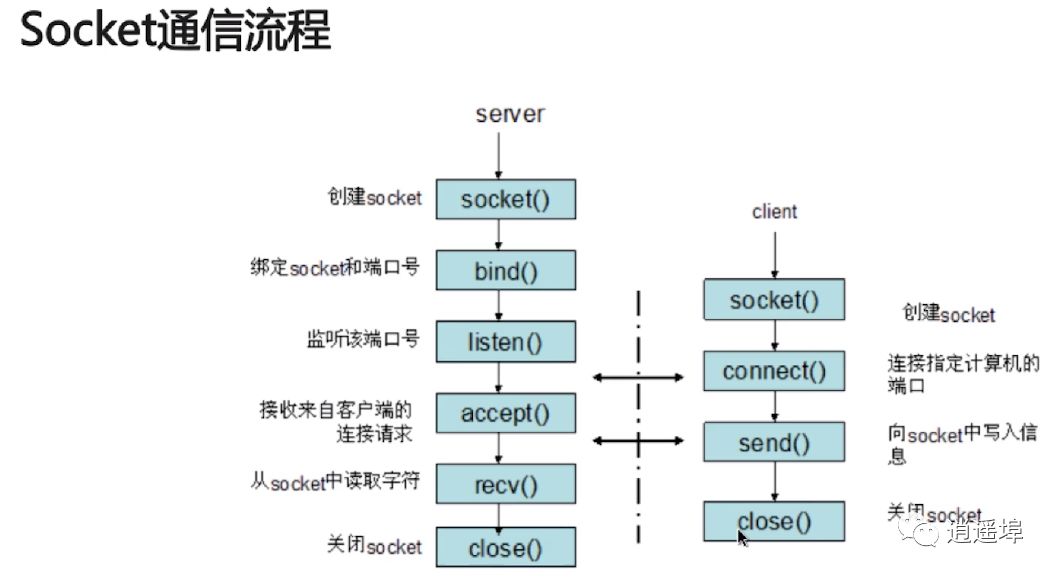
9、Socket
Socket is an abstraction of the TCP/IP protocol, an interface provided by the operating system
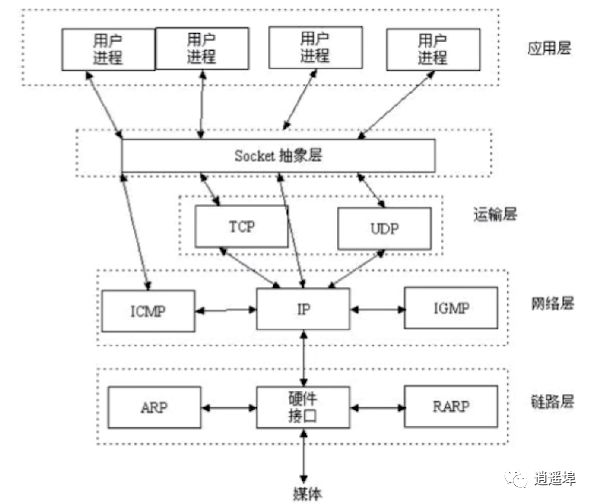
Socket communication process: