In mid-May, “WannaCry” began to sweep the globe, affecting over 300,000 computers in more than 150 countries and regions within just a few days. The impact on key industries such as energy, electricity, transportation, healthcare, education, and manufacturing was shocking. Half a month has passed, and while the attacks seem to have subsided, the reality is that more dangerous ransomware lurks in the shadows, ready to strike at any moment.
The attackers’ greed has expanded; the small ransom they once demanded can no longer satisfy their insatiable desires. Consequently, their targets have shifted from individuals to enterprises, with their claws reaching into the weakly protected industrial control domain, with SCADA and ICS systems being the primary victims.
At the same time, the attackers’ methods have evolved from merely locking and encrypting to completely wiping out the control system’s operational logic and destroying the controllers, causing instantaneous production halts for enterprises, with recovery periods being exceptionally long. This not only leads to significant economic losses for the affected companies but can also damage expensive production equipment or result in casualties.
JiuLue Intelligence has collected, organized, and analyzed the current threats posed by ransomware targeting industrial networks, relevant cases, and protective recommendations.
1. LogicLocker – Locking Logic Programs
At the RSA Conference in San Francisco in February 2017, researchers from Georgia Tech (GIT) demonstrated a newly developed ransomware called LogicLocker, which can infect industrial control facilities and poison water supplies. The targets include infrastructures like power plants or water treatment facilities. LogicLocker infects PLCs and modifies passwords to lock out legitimate users, closing valves that control chlorine levels in the water and displaying erroneous readings on machine panels.

1. Ransom Process
LogicLocker primarily targets three types of PLC systems: Schneider Modicon M221, Allen Bradley MicroLogix 1400, and Schneider Modicon M241. It scans for known vulnerabilities in the industrial control systems through API interfaces, bypasses security mechanisms, locks legitimate users out of devices, modifies PLC code to damage control devices, or sets logic bombs to trigger more severe security threats.
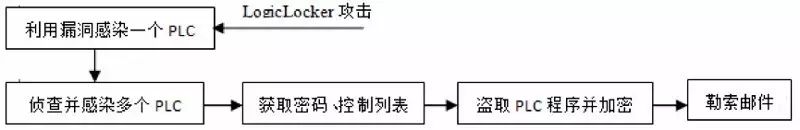
1.1 Initial Infection Stage
Infiltrating networked ICS devices or computer terminals to establish a foothold for malware or ransomware.
1.2 Lateral Penetration Stage
Discovering PLC devices with vulnerabilities and weaknesses through internal networks and infected devices.
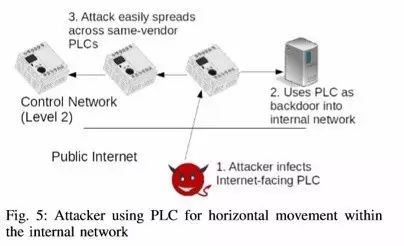
1.3 Vertical Penetration Stage
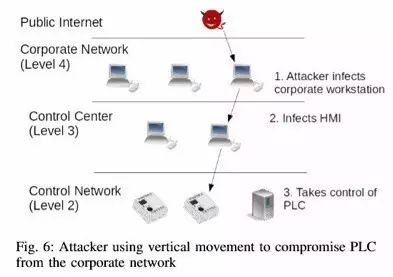
1.4 Locking and Encryption Stage
After locating the target PLC, it locks and encrypts it.
1.5 Ransom Negotiation Stage
Once successfully locked or encrypted, control permissions are obtained, and ransom is demanded via email or PLC page.
2. Logic Bomb
After gaining control of the PLC, it can cause denial of service (DoS), alter PLC behavior, and gather data from sensor and control messages. Since it is written in ladder logic, it can hide within the ladder logic program masquerading as a normal program block, making it difficult to detect. When the trigger conditions for the bomb are met, it immediately “explodes” and executes the payload.

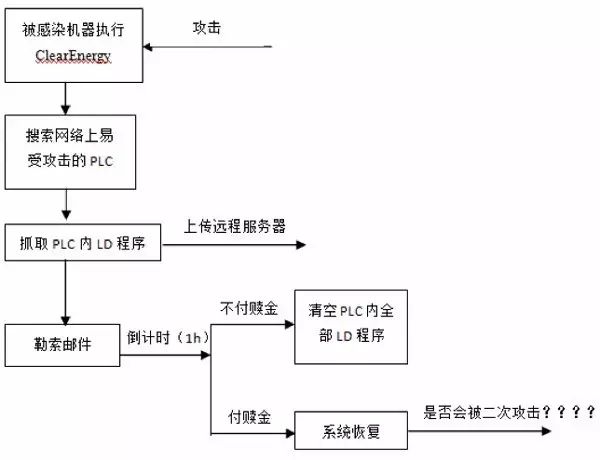
3. ClearEnergy – Clearing All Ladder Logic Programs
In early April 2017, the CRITIFENCE research group on “Critical Infrastructure and SCADA/ICS Network Threats” showcased a proof-of-concept (POC) ransomware called ClearEnergy, targeting SCADA and ICS systems to extort critical assets and infrastructure (which are easy to attack and hard to recover).
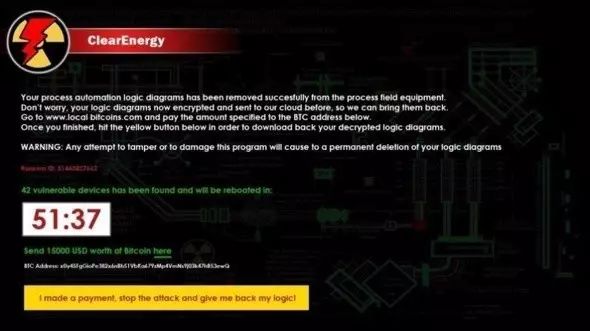
CRITIFENCE researchers found that ClearEnergy attacks are based on vulnerabilities CVE-2017-6032 and CVE-2017-6034, affecting a wide range of devices, including Schneider Electric’s Unity series PLCs and Unity OS version 2.6 and higher.
The UMAS protocol is a kernel-level protocol for Schneider Unity series PLCs and Unity OS version 2.6 and above, relying on the Modbus protocol, and is commonly used in critical infrastructure, SCADA, and industrial control systems for accessing both assigned and unassigned memory. The design of the session key in the UMAS protocol has a “bypass authentication” vulnerability (the fact that it is vulnerable has been confirmed by Schneider). Research has also discovered that products from manufacturers like GE and AB (MicroLogix series) have vulnerabilities that make them highly susceptible to this ransomware.
Schneider issued an important cybersecurity notice (SEVD-2017-065-01):
ICS-CERT released an important notice: Schneider confirmed that the fundamental flaw allows attackers to easily guess a weak (1-byte length) session key (256 possibilities) or even sniff it. With the session key, attackers can fully control the controller, read programs, and rewrite them with malicious code.
The biggest problem is that there may be no way to fully fix this in the coming years, due to the involvement of numerous hardware and vendors. During the repair period, a complete factory shutdown would cause massive losses; for example, energy plants require constant temperatures for chemical reactions, and if the reaction chain is disrupted, it may take weeks to reinitialize. Operationally, OT networks become more complicated, and many factories do not have the latest backups, requiring complete reconfiguration. Therefore, enterprises may be more willing to pay the ransom, but once paid, who can guarantee that they won’t suffer a second attack?
4. Scythe – Replacing Controller Firmware and Locking “Update Firmware”
On April 27, 2017, during Security Week, Applied Risk presented a paper at an ICS conference, indicating that the attack exploits a “firmware verification bypass” vulnerability and locks the “upgrade firmware” function. The targets are I/O systems distributed between SCADA field devices and OPC servers (e.g., remote terminal units or RTUs), which are supported by embedded OS and run web servers. Many public assets can be found via shodan search engines or Google search, making it easy for attackers to find potential targets on the web and replace the victim’s firmware version to achieve extortion.
Ariciu tested four devices from different vendors, most of which lacked authentication, allowing easy access. Hardware debugging determined the operational modes, analyzed ports, and employed various hardware attack techniques, firmware destruction, reverse engineering, etc., to study the target devices’ operating principles and attack methods.
This attack relies on the vulnerability to bypass firmware authentication to replace legitimate firmware. The attacker connects to the target device interface, backs up the target device configuration, and installs firmware that disrupts normal processes. Subsequently, the connection to the affected device is severed, and ransom information is displayed.
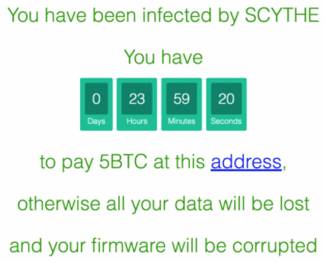
The attacker disables the “firmware and configuration update” function to prevent the victim from restoring the firmware. Although “factory reset” does not mitigate the attack, it has been disabled by the hacker. If the victim pays the ransom, the attacker can restore the device configuration because the “firmware update” function has not been disabled. If the user knows the firmware file name, they can update the firmware; if the attacker specifies a random file name of 32 characters or more, the victim cannot determine and execute the firmware update.
The occurrence of such attacks is because some enterprises have never considered backup configurations or rarely reconfigure devices after deployment. The affected products from four vendors range from $300 to $1000, of which two vendors have acknowledged the seriousness of the “firmware verification bypass” vulnerability and indicated that fixing the security vulnerabilities is not an easy task, and they are still trying to find the best solution.
Although ICS networks have not yet been attacked by malicious ransomware, it is not because they are more secure, but rather that criminals have not found a suitable business model for a long time. Cybercriminals seem to be starting to view the weakly protected ICS networks as the next potential target.
The rapid development of ransomware in industrial control systems deserves our utmost attention. Equipment vendors, users, security vendors, and others must take proactive defense measures to effectively combat this challenging battle in the future.
5. Ransom Events in Control Systems
1. In late January 2017, a luxury hotel in Austria was attacked, preventing the creation of new room key cards for guests, effectively locking them out of their rooms. As each hotel room costs up to several hundred dollars per night, the victim paid approximately $1,600 in ransom to restore the system and continue normal business operations. Although known ransomware was not used to attack the PLC, the control system was attacked in other ways.
2. Affected by WannaCry, hundreds of hospitals and clinics in the UK were infected with the virus on May 12, forcing them to transfer patients elsewhere. On May 13, Renault announced the suspension of production at its factories in Sandouville, France, and Romania to prevent the spread of ransomware within the system. In addition to Renault, other victims included Nissan’s manufacturing plant in Sunderland, northeast England.
Of course, the events we listed are just a portion of the affected cases. Over time, the instances of ransom on control systems will inevitably increase, and the targeting will become increasingly precise.
6. JiuLue Intelligence Security Protection Strategies
From the above analysis, it is clear that only targeted measures can achieve the best preventive effects. JiuLue Intelligence recommends that relevant enterprises take targeted protective measures against attack pathways:
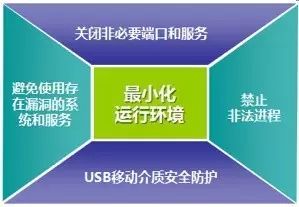
1. Industrial Host Intelligent Protection System – Preventing Initial Infection
Install an industrial host intelligent protection system on ICS engineer stations, operator stations, and other hosts to create a minimized operational environment for the industrial control network.
By intelligently identifying host applications and using a process whitelist management mechanism, illegal processes are prohibited from running, blocking the execution of viruses and other malicious programs in industrial control hosts, as well as the spread of trojans and worms; implementing comprehensive USB mobile storage device permissions and operational management to prohibit illegal USB devices from connecting to industrial control hosts, while auditing and tracing the operational behavior of legitimate USB devices to ensure no illegal devices are connected, no unauthorized operations are conducted, and effectively preventing file leaks.
2. Industrial Network Intelligent Protection System – Preventing Lateral and Vertical Propagation
Build a protective wall between different industrial control functional areas and “threats” using a combination of whitelist mechanisms (intelligent learning active defense) and blacklist mechanisms (industrial network vulnerability library intrusion defense) to effectively respond to various security threat challenges and ensure the safe and stable operation of industrial control systems. When non-secure factors emerge, malicious attacks hidden within control protocols can be discovered and blocked through in-depth analysis of industrial control protocols, and seemingly normal illegal operations can be intercepted outside the wall.
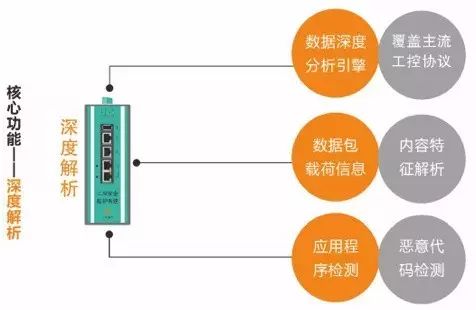
3. Industrial Network Intelligent Monitoring System – Real-time Monitoring of Abnormal Traffic
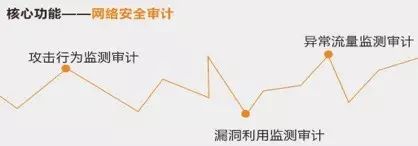
Deployed alongside switches/routers, integrating network monitoring, protocol analysis, and security auditing, it quickly identifies abnormal events and attack behaviors in the industrial control network through specific security policies and advanced intelligent learning technologies, providing real-time alerts to help you accurately perceive the network security situation.
Additionally, enhancing employee security awareness is crucial. Many current security issues stem from weak security defense awareness among staff, who believe their industrial control systems are secure and will not be attacked. It is only after an attack occurs that they realize the severity of the issue. Many infrastructures, once attacked, may be difficult to recover, and the severity is self-evident, making it necessary to raise personnel security awareness.
Overall, vendors in the industrial control field are not highly vigilant regarding ransomware, or even if they realize the seriousness, they have not taken practical measures to prepare in advance. Many vendors even avoid the issue directly, which is detrimental to preventing and resolving ransomware incidents.
With the emergence of new types of ransomware, it is likely that cybercriminals will directly attack critical infrastructure in the near future. Additionally, state-backed attackers may also utilize ransomware to conceal their true intentions. Therefore, personnel involved in critical infrastructure and industrial control systems should begin adopting standard security practices, establishing comprehensive security management systems, and implementing network isolation.