↑ Click the above
“Smart Manufacturing Home”
Follow us
Members can enter the member download area to obtain relevant materials~
Preface
Previously, we discussed PLCs in the era of the Industrial Internet:
In the era of the Industrial Internet, PLCs are no longer the PLCs of the past
We also talked about industrial security in the era of the Industrial Internet. With the deep integration of IT and OT, whether on the OT side or the IT side, industrial control security is crucial:
Siemens, Schneider, Rockwell: The Journey of Password Protection Breakthroughs for PLCs from Three Major Industrial Control Manufacturers
S7-1200+SCADA: A Detailed Explanation of Siemens S7 Protocol and Data Read/Write
Network attacks targeting industrial software and hardware PLCs, HMIs, SCADAs, MESs, IIOT
An Introduction and Practice of Industrial Control System Security – An Analysis of Industrial Control Security
Today, we will discuss industrial control system security: the types and processes of PLC attacks (using Siemens and Schneider PLCs as examples)~

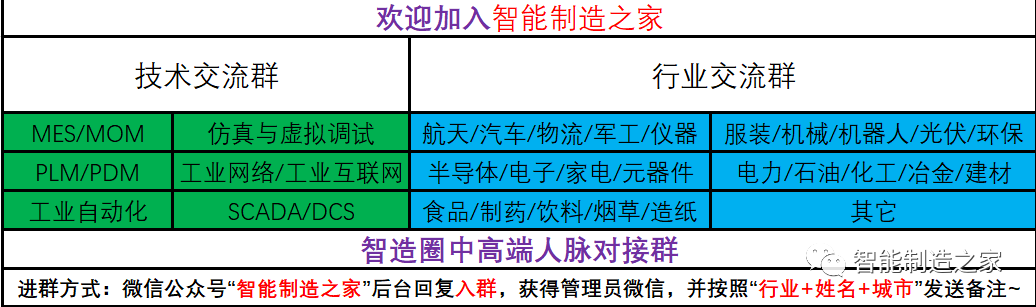
01 Types of PLC Attacks
PLC attacks can be categorized by the difficulty of the attack into disruptive attacks, configuration attacks, and firmware attacks.
The descriptions of the three types of attacks are shown in the table below:
Table 1 Classification, Description, and Harm of Attacks
Disruptive Attacks

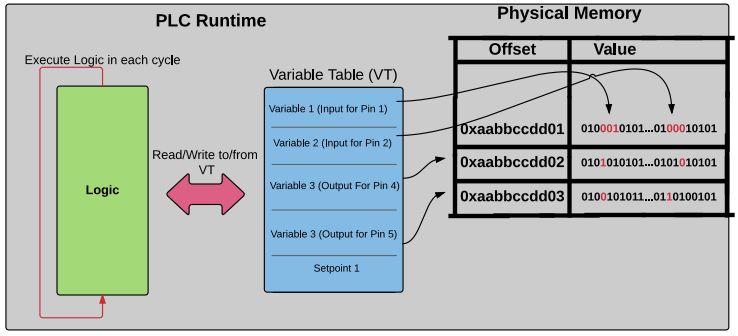
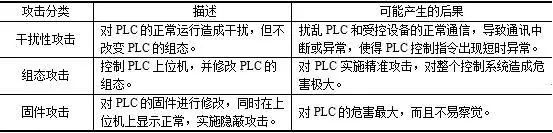
Figure 1 PLC RootKit Attack Process
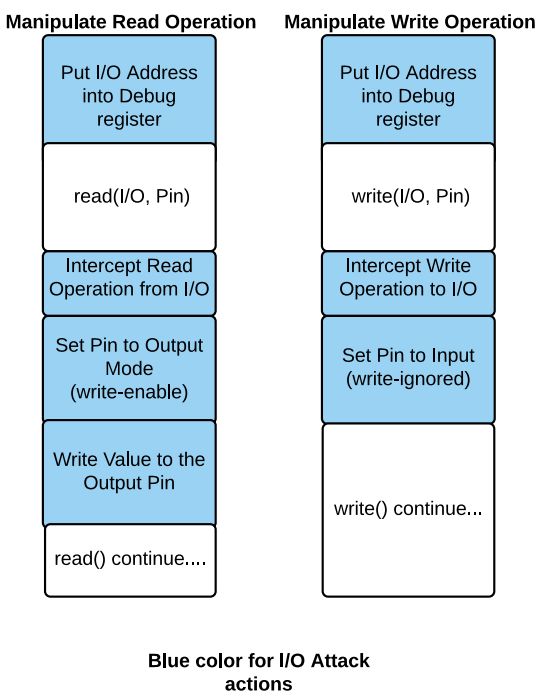
Figure 2 I/O Pin Reuse Attack Schematic

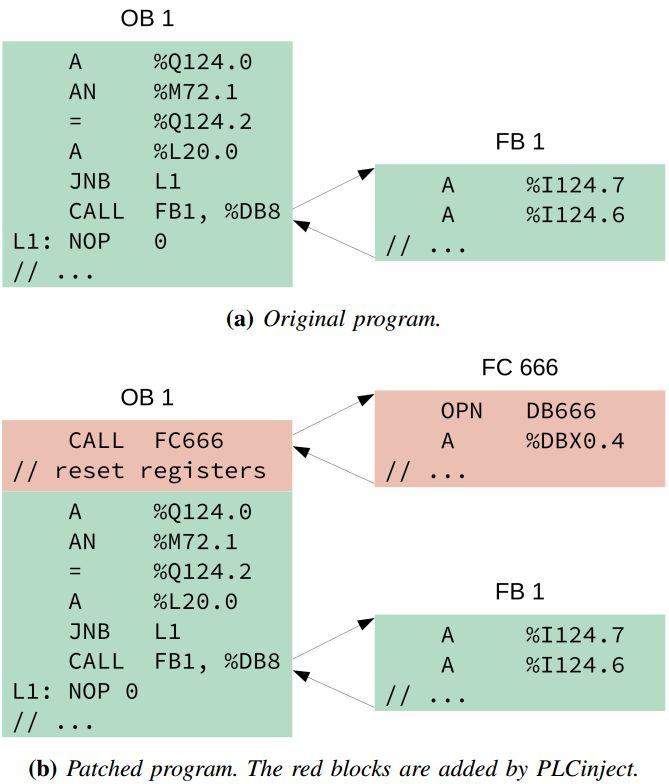
Figure 3 PLC Configuration Injection Process

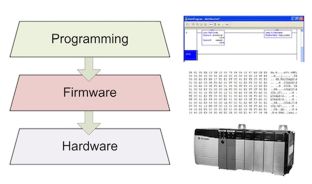
Figure 4 PLC Configuration, Firmware, Hardware Model

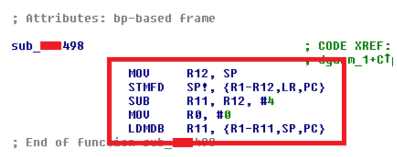
Figure 5 PLC Firmware Diagnostic Routine Modification Process
Beresford et al. [1] implemented firmware attacks against Siemens Simatic S7 PLCs. Garcia et al. [8] provided a detailed account of the entire firmware attack process against PLCs, utilizing embedded firmware upgrade mechanisms, online code injection, etc., to achieve firmware attack objectives. The specific attack process is shown in Figure 6:
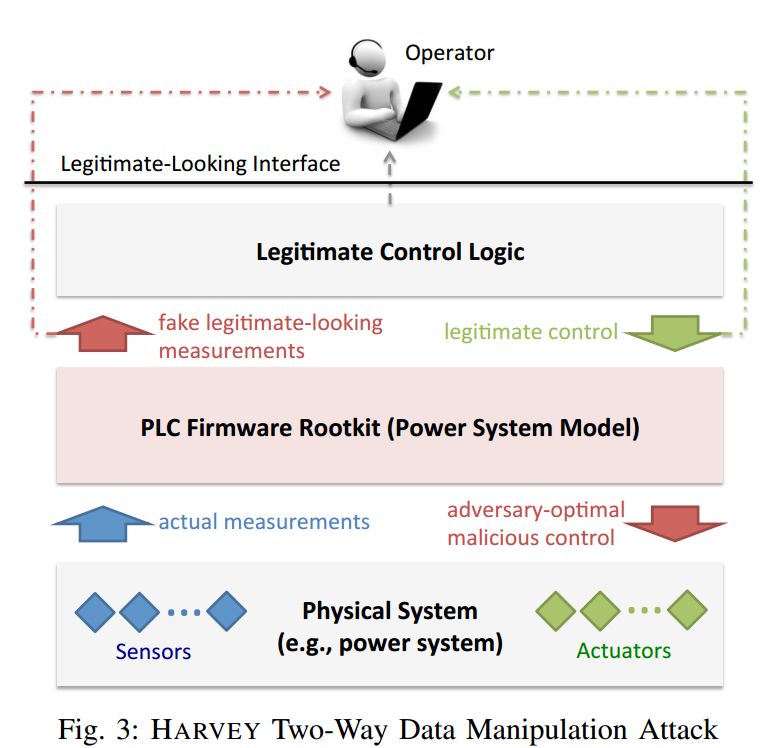
Figure 6 Bidirectional Attack Process on PLC Firmware
The attack process is achieved through bidirectional modification, altering PLC control instructions to destroy the physical world; simultaneously modifying sensor measurements so that operators see “reasonable” values, thereby hiding the attack and avoiding detection.

02 Attack Paths on PLCs
1. Attacks via Embedded System Vulnerabilities

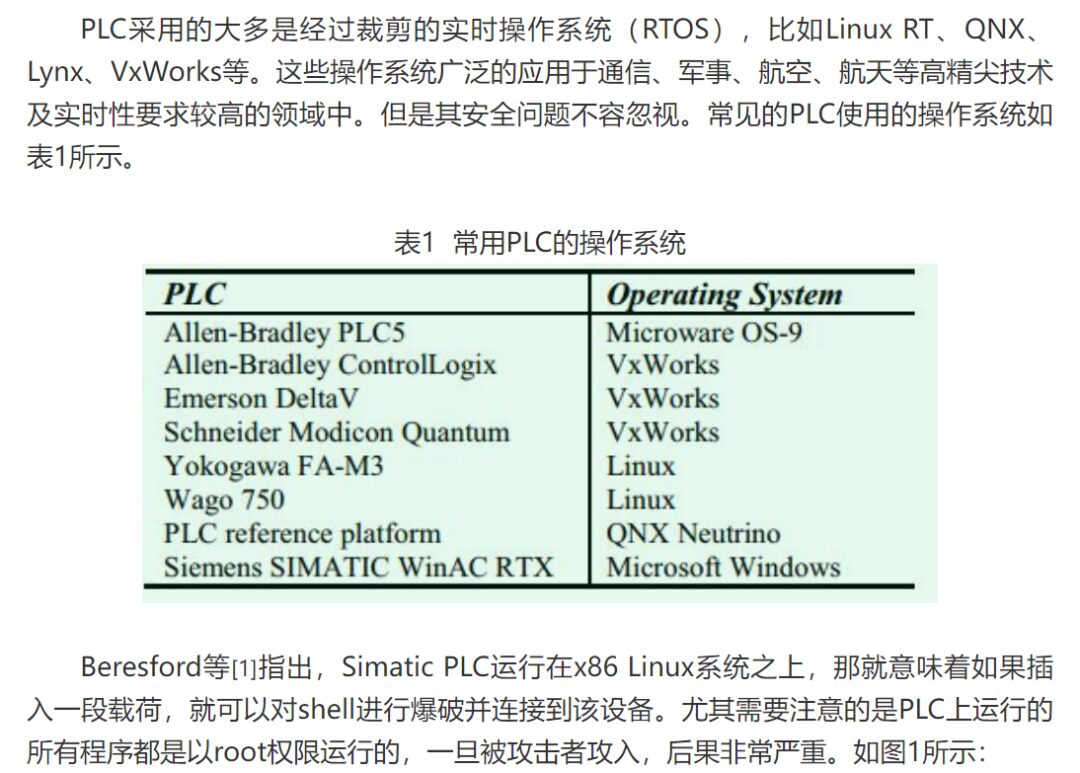
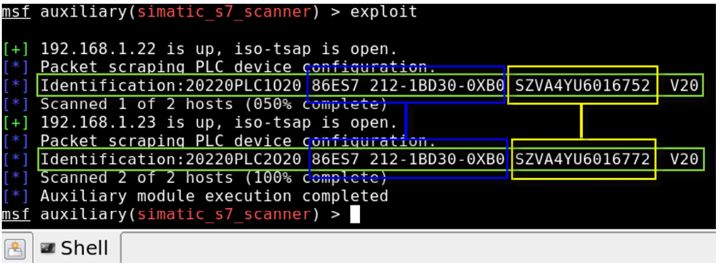
Figure 1 Brute Force Attack on Shell System
Many PLC devices from Siemens and Schneider run software on the VxWorks system. Wdbrpc is the remote debugging port for VxWorks, communicating via UDP with port number 17185. This protocol is based on sun-rpc, and the services it provides mainly support system remote interaction through the integrated development environment Tornado (as shown in Figure 2). According to the information released by Lighthouse Labs [2], hackers can use the wdbrpc protocol to dump all memory space data, find all ftp and telnet login passwords in memory, and further possible attacks include: tampering with bootline to bypass login verification, dumping memory data to capture login passwords, etc. By attacking the embedded real-time operating system, they can control the normal operation of the PLC.
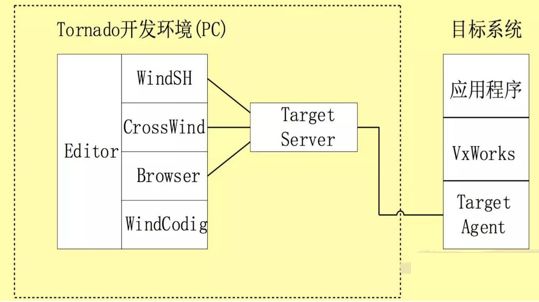
Figure 2 Tornado Development Environment and VxWorks System Diagram
2. Attacks via PLC Communication Protocol Vulnerabilities


3. Attacks via PLC Software Vulnerabilities


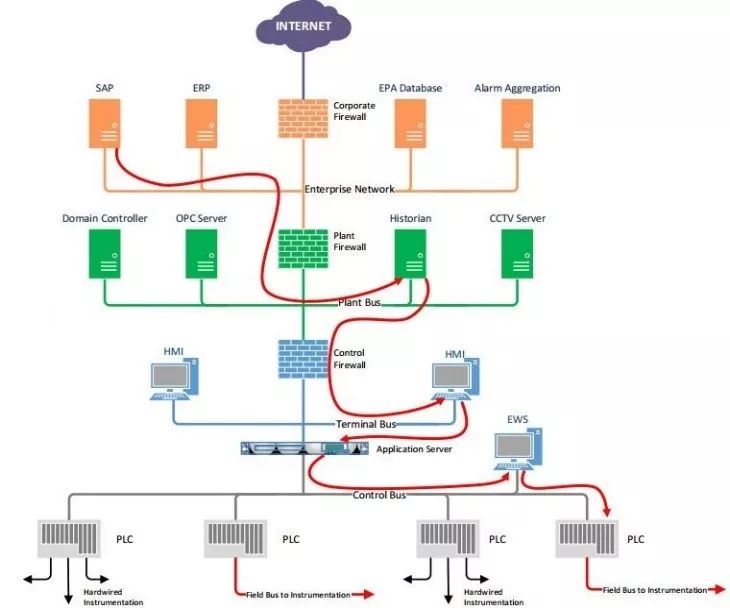
Figure 3 Attacking PLC via Human-Machine Interface Process
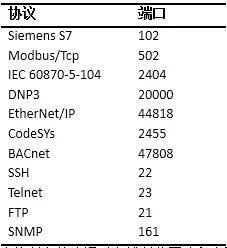
Radvanovsky et al. [9] pointed out that the SHINE (SHodan Intelligence Extraction) project initiated by the United States aims to extract information about SCADA and ICS devices accessible from the internet (especially PLCs and RTUs). The SHODAN search engine works by searching common TCP/UDP ports, as shown in Table 3:
Table 3 Common Protocols and Port Reference Table
Newman [10] noted that control room duty in prisons introduces viruses and worms through online browsing of pictures and movies. Some prisons provide internet services to inmates, and although they are not directly connected to prison control and monitoring systems, they are also a vulnerable point. Additionally, patrol cars in the prison use wireless signals and need to connect to the prison network to upload data, which is also an attack entry point.
Klick [11] pointed out at the 2015 USABlackHat that PLCs lack security mechanisms, and code can often be uploaded to these internet-facing PLCs, using these PLCs as gateways to penetrate production networks and even corporate IT networks. Kclik used the PLC programming language STL to write a port scanner and SOCKS proxy, then used the infected PLC to scan the local network and connect to other PLCs or even penetrate the corporate business network, as shown in Figure 4:
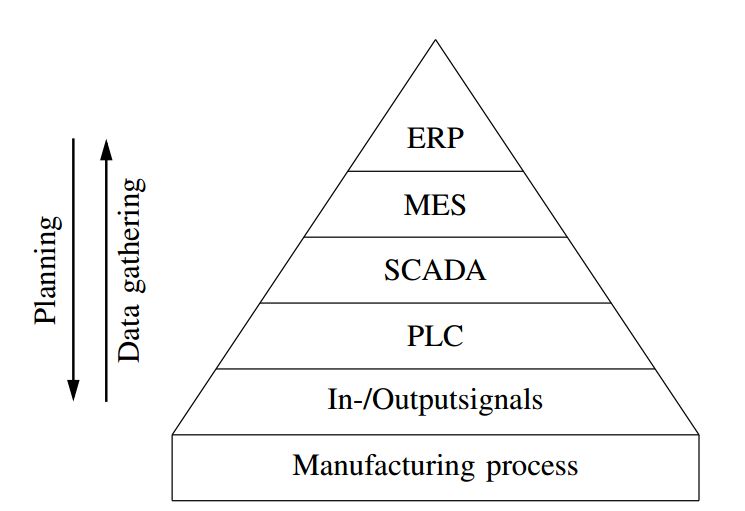
Figure 4 Company System Hierarchy Diagram
McLaughlin [12] designed malware targeting PLCs that can generate dynamic data packet payloads. Attackers can use this tool to implement attacks without prior knowledge of the control system, significantly lowering the threshold for attacking PLCs. First, the generated payload infects one or more hosts, then conducts industrial process analysis, followed by decoding binary files, and finally trimming the generated payload, uploading it to the PLC and running it, as shown in Figure 5:
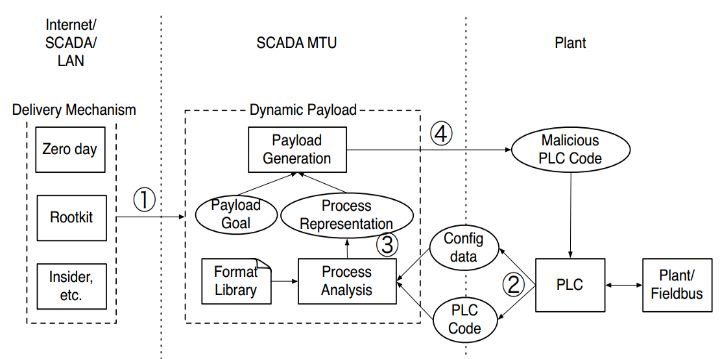
Figure 5 Dynamic Generation of Malicious Payload Process
McLaughlin, in another article [13], developed a tool for automatically generating PLC payloads—Sabot, which automatically identifies PLC logic control and generates malicious PLC code, as shown in Figure 6:
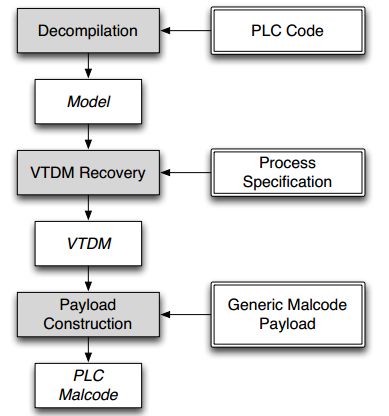
Figure 6 Sabot Attack Process Schematic
Spenneberg [14] et al. demonstrated a worm that survives on PLCs, using Siemens SIMATIC S7-1200 as an example, at the 2016 Asia BlackHat. This worm does not rely on PCs to spread; it remains active and runs on PLCs, discovering new targets (PLCs) through network scanning, then attacking these targets and copying itself to new PLCs without changing the main program of the infected PLC. This allows for target discovery and carrying malicious payloads, among other attack methods. Moreover, removing these worms is very difficult; currently, it can only be done by restoring factory settings or rewriting the functional blocks where the worm resides. The infection process is shown in Figure 7:
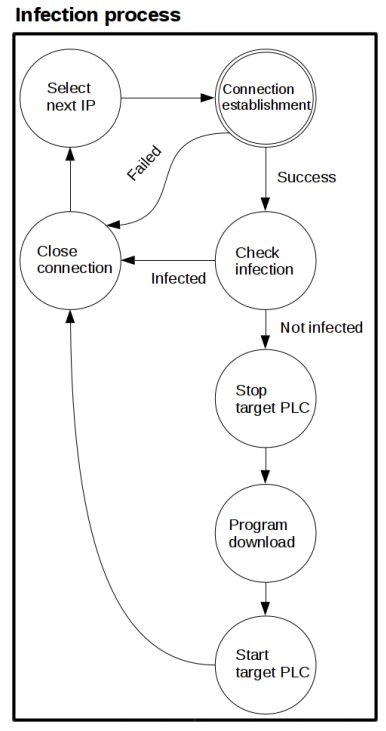
Figure 7 Worm Infection Process on PLC
The code execution process is shown in Figure 8:
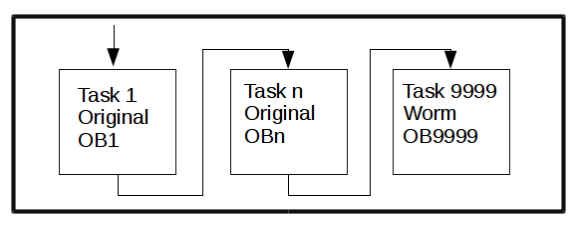
Figure 8 Worm Malicious Code Execution Process
In summary, the security situation of PLCs is not optimistic, with multiple attack paths available and the depth of attacks gradually increasing. There is still a long way to go to ensure the security of PLCs.

References:
[1] Beresford D. Exploiting Siemens Simatic S7 PLCs[J]. Black Hat USA, 2011, 16(2): 723-733.
[2] Kimon. Revealing VxWorks – Directly Targeting IoT Security Vulnerabilities [EB/OL]. http://chuansong.me/n/1864339, 2015-11-01
[3] Langner R. A time bomb with fourteen bytes[J]. Available: hUp: llwww. langner. comlen, 2011.
Members can enter the member download area to obtain relevant materials~

Hardcore Collection
ERP/PLM/MES/SCADA/PLC/Industrial Software Research Report
Information technology, digitalization, smart manufacturing, industrial internet solutions
Automation, information technology, digitalization, industrial networks, simulation and virtual debugging introduction
WinCC technology | Industrial networks | MES technology related | Industrial giants strategic layout | Industrial communication cases
Simulation and virtual debugging | Career insights, cognitive enhancement | Automation control standards collection

Industrial Data Collection (MES\\SCADA\\PLC\\IOT\\Sensors..) Industry Research Report
2021-08-24

Detailed Interpretation of Global Industrial Digital Twin Mainstream Players, Technical Systems, and Industrial Layout
2021-08-19
Siemens, Dassault, PTC, Zhongwang: A Comparative Analysis of Core Product Strengths of Global CAD Players
2021-08-16
In-depth Report on Industrial Software in Production Control (MES+SCADA+DCS+PLC)
2021-08-15
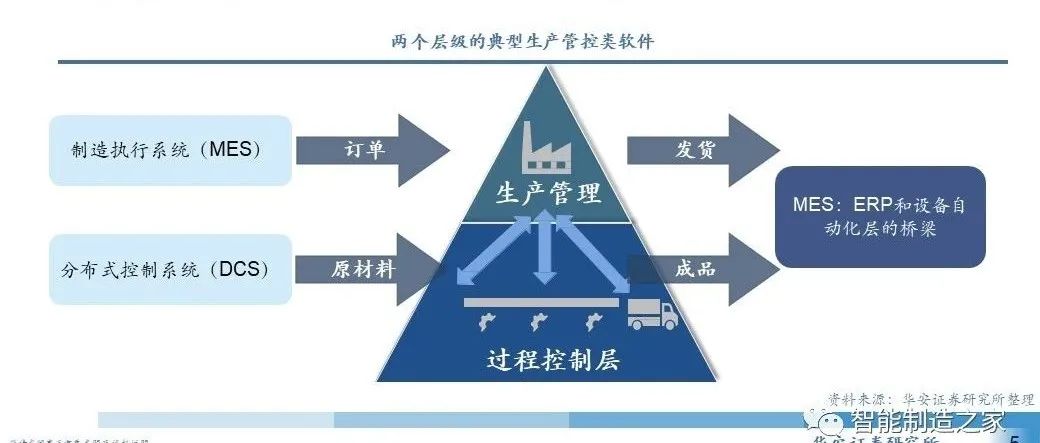
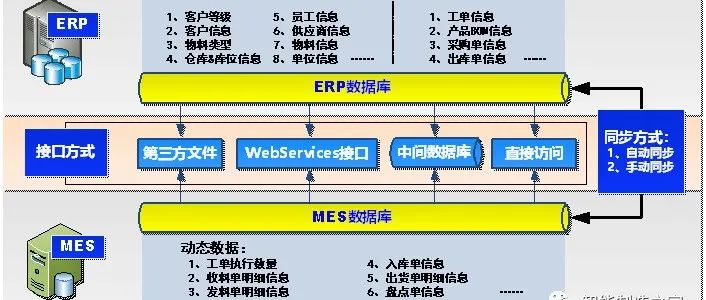
Mainstream Interface Methods and Major Interaction Data Items between MES and ERP
2021-08-13
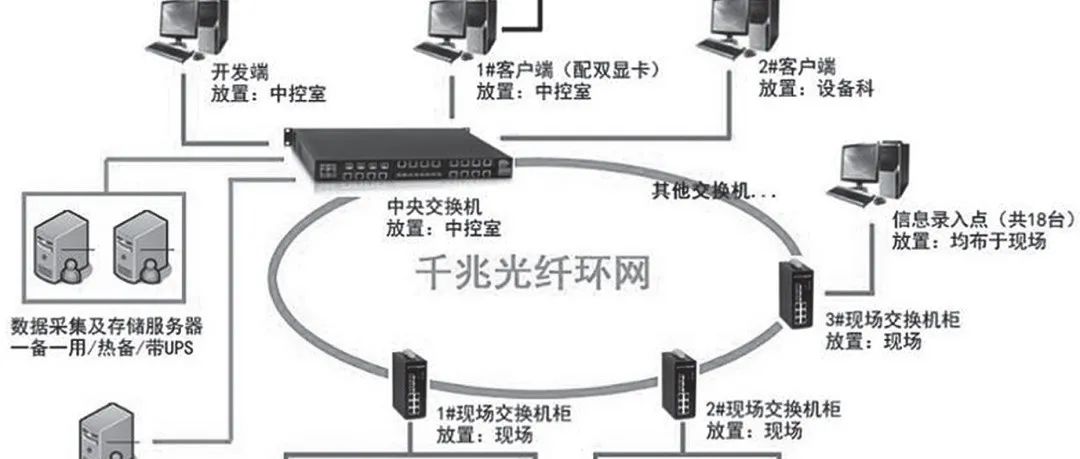
XX Automotive Welding Intelligent Factory Control System and Information System (PLC+SCADA+MES) Planning Design
2021-08-10
Global CAE Market: Siemens, Dassault, ANSYS…, Domestic Industrial Software’s