
In recent years, ransomware attacks have become a significant security concern. To obtain high returns, cybercriminals have increasingly targeted high-value industries such as healthcare and finance. Although all current ransomware attacks focus on personal computers, recent analyses indicate that industrial control systems (ICS) networks are likely to become the next target for ransomware, with critical infrastructure related to ICS also facing potential ransom threats.
Yesterday’s article on FreeBuf titled “New Threats from Ransomware: If You Don’t Pay the Ransom, I’ll Poison Your Drinking Water” mentioned a ransomware threat to ICS, and the following article provides an in-depth analysis of how ransomware can have such capabilities.
In this study, cybersecurity experts at Georgia Tech developed the first ransomware targeting Programmable Logic Controllers (PLCs), modeling an attack on urban water supply facilities as a target for ransom attacks and impact assessment. (This study was also presented as a special report at the recent RSA Conference; click the link at the end of the article to read the original report.)
Video demonstration of the ransomware attack on water supply facilities:
Research Introduction
ICS attack incidents are rare, but this does not mean that ICS are safe. According to the latest research from Kaspersky, due to various vulnerabilities and insecure protocols, the security of ICS may even be deteriorating. The only explanation for this temporary security situation is that cybercriminals have not yet been able to effectively combine attacks with profit. In today’s environment of rampant ransomware attacks, enterprise data is the target of attackers’ value. Although the valuable data involved in ICS is relatively limited, the stable and safe operation of manufacturing, power plants, water supply, and natural gas facilities is closely related to people’s lives. Previous incidents like the North American blackout and the Stuxnet incident, as well as recent attacks on Ukrainian power plants, have caused significant economic and security losses.
We developed the first ransomware targeting Programmable Logic Controllers (PLCs), named LogicLocker, to explore the possibility of ICS becoming targets for ransomware attacks. LogicLocker utilizes the native API interface of Schneider Modicon M241 devices to scan for known vulnerable devices in the ICS internal network, such as Allen Bradley MicroLogix 1400 PLCs and Schneider Modicon M221 PLCs. It breaches security mechanisms through infection and circumvention, locks legitimate users out of devices, and sets logical bombs in programs that pose threats to physical and personal safety, to extort ransom. Our main research focuses on the following points:
Developed the first ransomware targeting industrial control system Programmable Logic Controllers (PLCs);
Achieved proof of concept for worm infections across vendor PLCs;
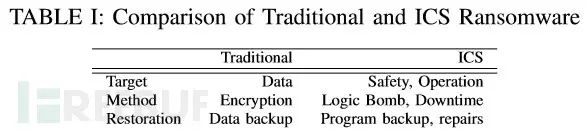
Conducted a detailed economic comparison between traditional ransomware attacks and ICS ransomware attacks;
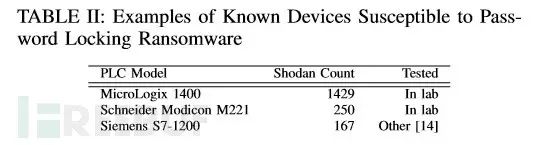
Utilized Shodan for online discovery and investigation of ICS devices susceptible to ransomware;
Established a security framework for ICS ransomware attacks for research and reference.
Threat Modeling
Setting aside attacks from state-sponsored hackers and script kiddies, this study assumes that ransomware attacks are initiated by organized cybercriminal groups for economic purposes. Although these attackers may not have the capability to discover firmware-level vulnerabilities, they can skillfully use application-layer PLC intrusion capabilities to discover and control numerous ICS devices. By modifying PLC code, attackers can achieve physical damage to ICS devices or set program logic bombs to trigger more severe security threats.
Economic Impact Assessment of Ransomware Attacks
The success of ransomware attacks on hospitals is due to their absolute need for control over patient data; similarly, ICS must ensure that their PLCs can safely and stably provide services to the public or downstream manufacturers.
Traditional Ransomware Attacks vs. ICS Ransomware Attacks
The economic losses caused by traditional attacks are determined by the value of the stolen data and the scope of the victims. Attackers evaluate the cost and value of attacks before initiating them. The higher the attack cost, the higher the target’s security, which may also mean a greater ransom value. This relationship can be expressed in the following equation:

For ransomware attacks, ICS are considered low-value and relatively small-scale targets; however, the impact of equipment downtime, security performance, and the safety of operators far exceeds the usual value range, allowing attackers to exploit these critical vulnerabilities to launch ransomware attacks.
Experimental Process
The three PLCs utilized by LogicLocker are Schneider Modicon M221, Allen Bradley MicroLogix 1400, and Schneider Modicon M241, representing some of the more popular and commonly used PLC brands today. However, we must remind readers that most PLC devices, including these brands, lack suitable programmable verification functionality.

Other devices with password verification and PLC programming verification features, such as the MicroLogix 1400, can also be subjected to ransomware attacks if attackers exploit other means to gain control and then set a new password for extortion. We discovered a large number of online ICS devices on Shodan:
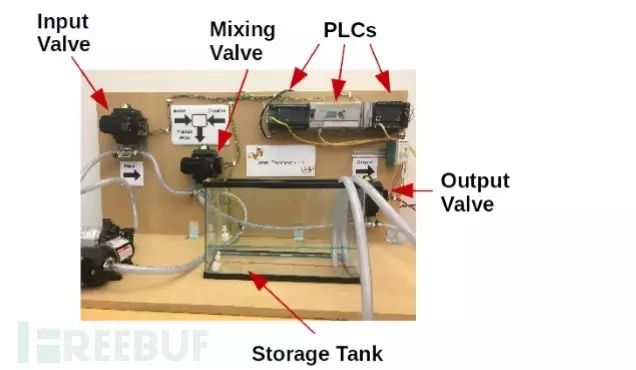
To validate the possibility of ICS ransomware attacks, we constructed a model of a city water supply system and simulated the feasibility of a ransomware attack. During the water quality disinfection phase, the correct proportion of chlorine powder must be added to the tap water, and during the water storage phase, the minimum water usage must be controlled.

Analysis of Ransomware Attacks
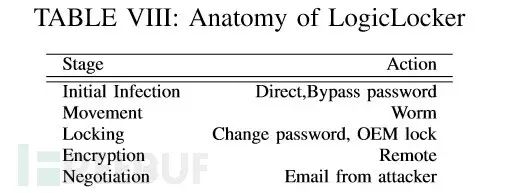
Attacks on ICS can be divided into several steps: initial infection, further attack penetration, device locking and encryption, and ransom negotiation. The entire process is illustrated in the following diagram:
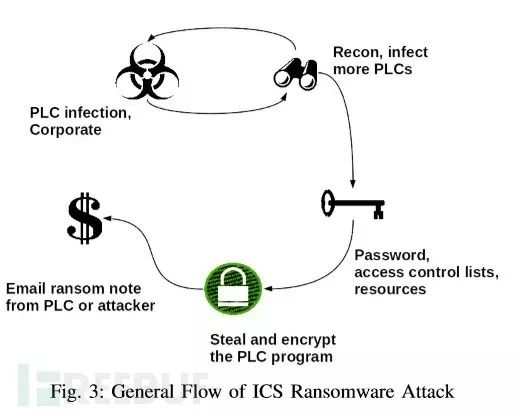
The subsequent list outlines the actions that attackers can execute at each step.
Initial Infection Phase
By infecting directly connected ICS devices or using other attack methods, the attacker infiltrates the target victim’s terminal computer system, ultimately allowing malware or ransomware to reside, preparing for subsequent ransom attacks:
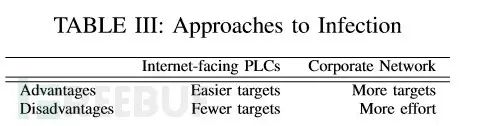
Further Attack Penetration
Through lateral penetration within the internal network and infected devices, the attacker discovers other vulnerable PLC devices and exploitable weaknesses. The attacker performs lateral penetration within the internal network:
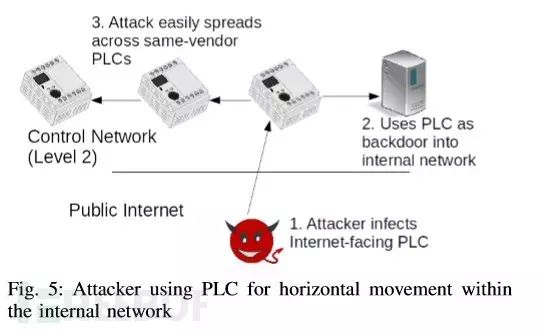
The attacker performs vertical penetration within the internal network:
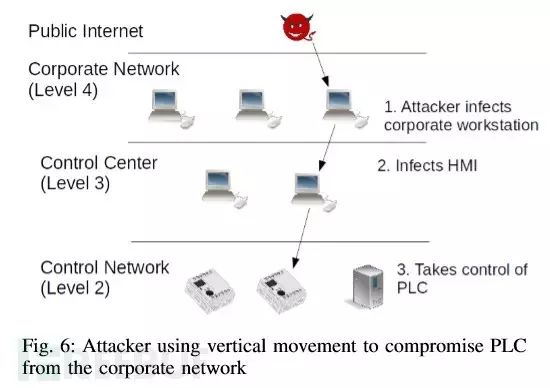
Locking and Encryption
After identifying target PLC devices to attack, the attacker initiates actions to lock and encrypt the target devices:

Ransom Negotiation
Once the PLC device is successfully locked or encrypted, the attacker gains control of the target device and issues warning prompts to the victim to urge payment of the ransom. These warning prompts can be delivered via email or displayed on the PLC page:

LogicLocker
In the attack model, we assume that the attacker can brute-force the connected Modicon M241 device and steal its user credentials. After that, the infected LogicLocker scans the internal network for vulnerable PLC devices. During the locking phase, LogicLocker can perform reprogramming, password resetting, and legitimate user locking functions targeting Modicon M221 and MicroLogix 1400; during the encryption phase, the attacker can use other standard encryption methods to encrypt device passwords and programs at will; during the ransom negotiation phase, the attacker can use LogicLocker to send warning emails to the PLC device managers of the victims.
In this model, if the ransom is paid, the attacker will provide the victim with a device reset program to lift the ransom. If the negotiation fails or the victim refuses to pay the ransom, the attacker will add excessive harmful chemicals to the water supply, and additionally, the attacker can tamper with the water quantity device readings or shut off the water valve through the PLC, causing public panic. Future versions of the LogicLocker software will include a client for sending warning emails, so if the ransom is successful, the attacker can send the victim the program unlock and reset procedures. The following list summarizes the actions LogicLocker can perform for ransomware attacks.
Security Protection
Endpoint Security Protection
Implement deep defense strategies, including changing default passwords, disabling unnecessary protocols, setting access control methods, disabling remote programming features, keeping device firmware updated, and backing up all program documents. For newly purchased devices, careful consideration should be given to product security performance. Additionally, note that PLC password protection features are only used to verify legitimate users in the programmable environment and should be avoided as a means for ransomware attackers to extort.
Network Security Protection
Network segmentation control and suspicious traffic monitoring should be implemented. Additionally, PLC program automatic backup features should be set up to prevent the impact of destructive attacks initiated by attackers in the event of non-payment of ransom. Of course, remote authentication technology can also be introduced for PLC programs to monitor malicious modifications made by attackers.
Security Policies
On the user end, strengthen employee security awareness training to improve defenses against phishing emails and external USB drives; simultaneously, formulate corresponding security emergency response and rapid recovery strategies to quickly assess the impact of attacks and restore device operation in the event of an attack.
*Reference sources: gatech.edu, FB editor clouds compiled, please indicate that it comes from FreeBuf.COM
